Tens of hundreds of uncovered D-Hyperlink routers which have reached their end-of-life are weak to a essential safety concern that permits an unauthenticated distant attacker to alter any consumer’s password and take full management of the machine.
The vulnerability was found within the D-Hyperlink DSL6740C modem by safety researcher Chaio-Lin Yu (Steven Meow), who reported it to Taiwan’s pc and response heart (TWCERTCC).
It’s value noting that the machine was not out there within the U.S. and reached end-of-service (EoS) section initially of the yr.
In an advisory immediately, D-Hyperlink introduced that it will not repair the problem and recommends “retiring and replacing D-Link devices that have reached EOL/EOS.”
Chaio-Lin Yu reported to TWCERTCC two different vulnerabilities, an OS command injection and a path traversal concern:
The three flaws points are summarized as follows:
- CVE-2024-11068: Flaw that permits unauthenticated attackers to switch any consumer’s password by means of privileged API entry, granting them entry to the modem’s Internet, SSH, and Telnet providers. (CVSS v3 rating: 9.8 “critical”).
- CVE-2024-11067: Path traversal vulnerability permitting unauthenticated attackers to learn arbitrary system recordsdata, retrieve the machine’s MAC tackle, and try login utilizing the default credentials. (CVSS v3 rating: 7.5 “high”)
- CVE-2024-11066: Bug enabling attackers with admin privileges to execute arbitrary instructions on the host working system by means of a particular internet web page. (CVSS v3 rating: 7.2 “high”)
A fast search on the FOFA search engine for publicly uncovered gadgets and software program exhibits that there are near 60,000 D-Hyperlink DSL6740C modems reachable over the web, most of them in Taiwan.
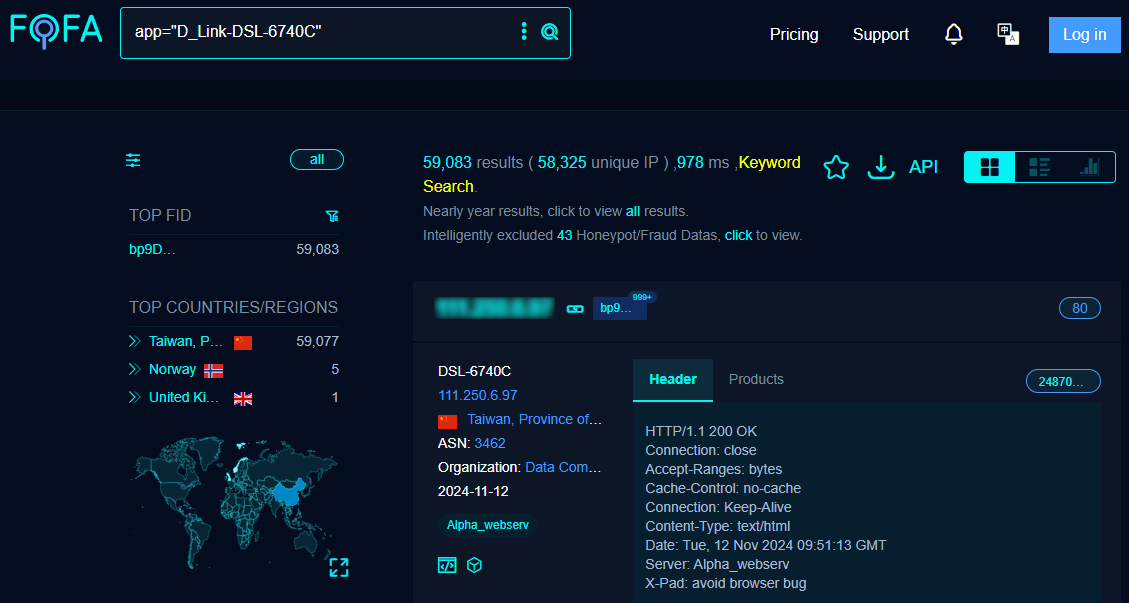
Supply: BleepingComputer
TWCERTCC has revealed advisories for 4 extra high-severity OS command injection vulnerabilities that impression the identical D-Hyperlink machine. The bugs are tracked as CVE-2024-11062, CVE-2024-11063, CVE-2024-11064, and CVE-2024-11065.
Though the variety of weak gadgets uncovered on the general public internet is critical, D-Hyperlink has made it clear prior to now [1, 2] that end-of-life (EoL) gadgets usually are not coated by updates, even when essential bugs are involved.
If customers cannot change the affected machine with a variant that the seller nonetheless helps, they need to no less than prohibit distant entry and set safe entry passwords.
