The newly found CVE-2022-42889 made some headlines not too long ago. On this quick weblog we are going to talk about what the vulnerability is, its affect, and mitigation.
The package deal affected by the CVE is Apache Commons Textual content, an open-source Apache library that’s “focused on algorithms that are applied to strings” (string substitution, lookups, matching and different algorithms). The found vulnerability exists all through variations 1.5 to 1.9 and should result in arbitrary code execution when untrusted information is processed and interpolated.
Government Abstract
A brand new vulnerability, CVE-2022-42889, generally referred to ‘text4shell’, is a vital severity vulnerability affecting the favored Apache Commons Textual content. It’s reminiscent, at its technical core, of the now notorious Log4Shell vulnerability – by processing values in a method that may permit invoking inside functionalities, which might, in flip, lead to execution of arbitrary malicious code.
Fortuitously, not all customers of this library can be affected by this vulnerability – in contrast to Log4J within the Log4Shell vulnerability, which was weak even in its most elementary use-cases. Apache Commons Textual content should be utilized in a sure method to expose the assault floor and make the vulnerability exploitable.
Regardless, this vulnerability is extreme, and customers ought to take the time to replace this library to its newest model as quickly as doable.
Technical particulars
Within the Apache Commons Textual content, there’s a function that expands the textual content with lookups. Features like changing a string will name the weak lookup operate. This performance is an implementation of a really primary expression language, which permits invoking a number of strategies from inside the interpolated string.
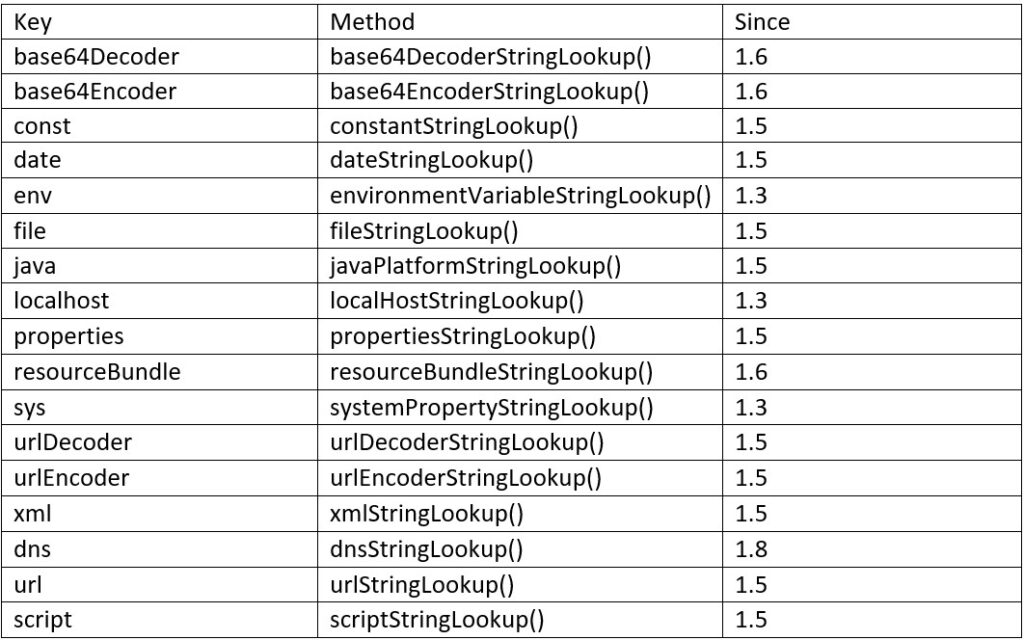
The lookup has variety of fields which it tries to determine as proven beneath:
The fields that introduce safety threats are the dns, url, and script − the worst one being script which opens the door for Arbitrary Code Execution. Utilizing the ‘replace’ operate, we will invoke a lookup with the expression language string ‘${<lookup field>:<lookup string>}’
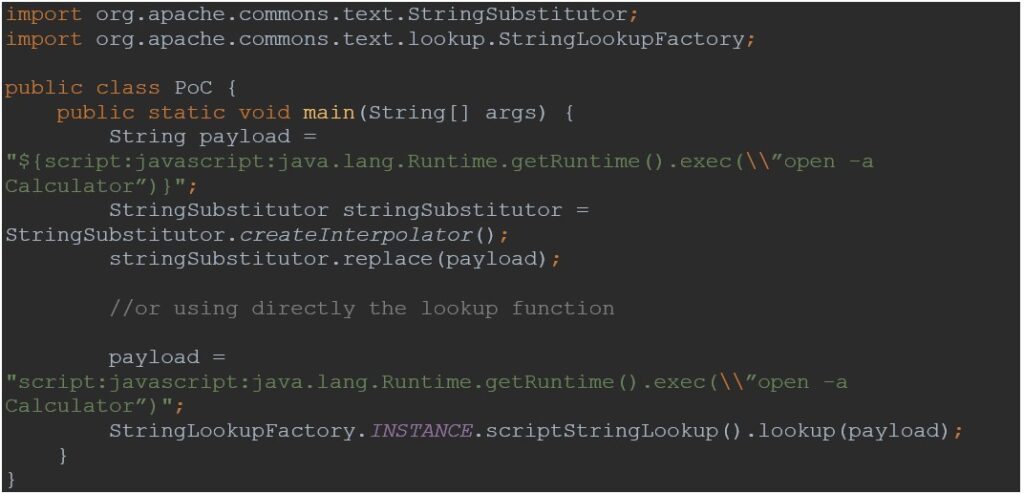
The next PoC makes use of the change operate with the payload containing the symbols “${}” for the lookup to execute. The second a part of the code demonstrates invoking the lookup instantly.
Log4Shell vs. CVE-2022-42889
When first seeing this vulnerability, we instantly affiliate it with Log4shell, therefore the same title, Text4shell (regardless of having nothing to do with the quantity 4). String interpolation of primary EL invoking code, with related file names in (e.g. StringSubstitutor.java), invoking probably harmful strategies are all very a lot paying homage to Log4Shell. Regardless of the numerous resemblances to the notorious CVE-2021-44228, nonetheless, we should level out that the weak package deal and features just isn’t as extensively used within the wild. One other main distinction is in implementation. Whereas essentially the most elementary use-cases of Log4j have been weak in Log4Shell, this vulnerability requires an implementation sample that won’t have an effect on all of its customers.
Regardless, this vulnerability is critical, and the potential affect stays the identical as unauthenticated RCE (distant code execution) is essentially the most impactful assault one can have.
Remediation
The repair utilized by the Apache group was the removing of the dns, script, and url lookups from the default interpolator conduct. Within the StringLookupFactory.createDefaultStringLookups() technique the DefaultStringLookup.DNS, DefaultStringLookup.URL and DefaultStringLookup.SCRIPT at the moment are not added by default. Within the earlier variations, all of the DefaultStringLookup situations have been added by default.
The advisable motion is to improve the package deal to the fastened model (1.10.0).
In case an improve just isn’t doable, the StringSubstitutor may be initialized with secure StringLookup configurations.
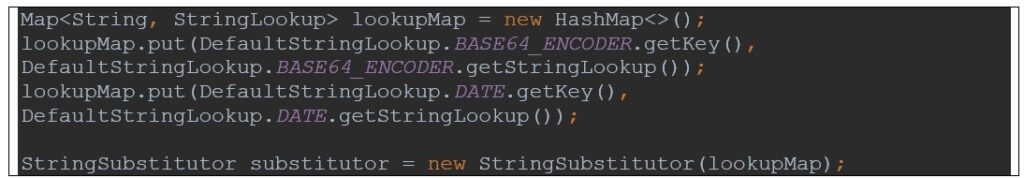
If the harmful lookups are vital within the software, all consumer enter needs to be sanitized earlier than being interpolated. A doable resolution may be the usage of a whitelist within the enter validation part.
Conclusion
In conclusion, the vulnerability could trigger some panic within the wake of Log4shell. Regardless of it being much less used within the wild, and regardless of requiring particular implementation for exploitation to be viable, it’s nonetheless an essential vulnerability since it’s simple to use the place weak, it’s extensively used, and has important affect. Checking in case your code is weak is very essential.
Checkmarx SCA prospects can scan their code for related varieties of vulnerabilities and get the most recent remediation steerage.
Timeline
- 2022-03-09: Situation reported to [email protected]
- 2022-03-25: Apache Commons safety group acknowledged receiving the report
- 2022-05-27: GHSL requested a standing replace
- 2022-05-27: Apache Commons safety group notifies they’re engaged on disabling the script interpolation by default
- 2022-06-29: Apache Commons safety group states that “Commons Text” will likely be up to date, in an effort to make the programmer’s intention utterly express on utilizing a “dangerous” function
- 2022-08-11: GHSL requested a standing replace
- 2022-10-12: Apache Commons Textual content releases model 1.10.0 the place script interpolation is disabled by default