GraphQL is an API normal stated to be a extra environment friendly and versatile various to REST and SOAP. One of many primary functions of a GraphQL server is to course of incoming knowledge.
One of the crucial difficult duties for builders who work with GraphQL servers is Denial-of-Service (DoS) safety. Directive overloading (submitting a number of directives) is without doubt one of the DoS vectors to be involved about.
Directives are used to dynamically change queries’ construction and form utilizing variables. If the context of utilizing the directive shouldn’t be clear – don’t fear; that’s not essential within the present vulnerability. To study extra details about directives and directive overloading examine our weblog publish: https://checkmarx.com/weblog/alias-and-directive-overloading-in-graphql/
Weak software program
graphql-java is the most well-liked GraphQL server written in Java. It was discovered to be susceptible to DoS assaults by way of the directive overload.
Furthermore, the spring-graphql by Spring and dgs-framework by Netflix libraries use it as a core element. Due to this fact, they’re additionally susceptible if the core element is outdated. To know the dimensions of the issue, it’s value mentioning that graphql-java is the #1 library in Maven’s prime GraphQL servers and is utilized by 355 libraries.
The vulnerability was fastened in two phases. The primary repair launched a safety management, whereas the second focused the foundation trigger. The primary repair is offered within the variations of graphql-java 19.0 and later, 18.3, and 17.4.
The second repair has been utilized in the model 20.1 with the pull-request.
Exploitation and Impression
The vulnerability will be exploited by sending a crafted GraphQL request. The request comprises an enormous variety of non-existing directives.
The instance demonstrated beneath relies on the spring-graphql GraphQL server that makes use of the unpatched graphql-java model.
Request instance:
@aa is a non-existent directive. The processing time of this request is barely about 100 ms; whereas, including a lot of directives drastically will increase the execution time. The screenshot beneath exhibits the request with 1000 directives which is executed in 189 ms, 3000 in 447 ms, 5000 in 963 ms, 7000 in 1,7 second, 10000 in 3 seconds, and 15000 in 5.4 seconds:
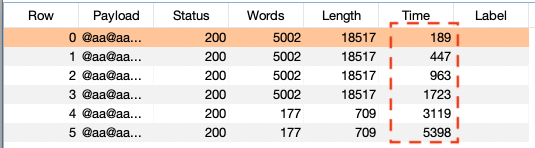
The time of execution will increase primarily based on the variety of directives. By launching 50 concurrent malicious requests with 30.000 directives, the server turns into unavailable:
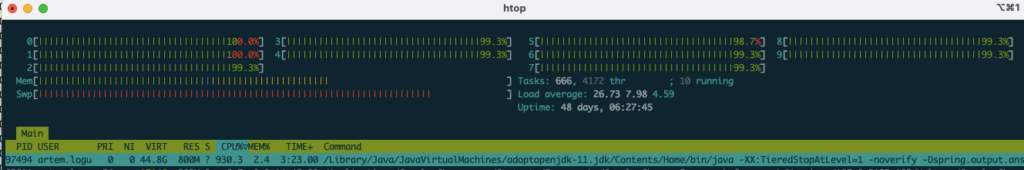
Because of this assault, the server grew to become unavailable. All of the CPU assets have been exhausted.
An attacker can exhaust all of the server’s CPU assets by sending 50 concurrent requests utilizing just one attacking machine.
Root trigger
Two Denial-of-Service protections have been added earlier than the invention of the vulnerability within the following pull requests:
These safety mechanisms are triggered when an attacker submits a giant question; they restrict the variety of parsed tokens and validation errors.
And the restrict works. After submitting greater than 15000 tokens, the next error happens:
{
"errors": [
{
"message": "Invalid Syntax : More than 15000 parse tokens have been presented.
To prevent Denial Of Service attacks, parsing has been cancelled. offending token '@' at line 2 column 22511"
}
],
...
}
Nevertheless, as seen within the instance above, the execution time will increase even when greater than 15000 tokens are offered. It signifies that the DoS happens earlier than the code reaches the token limits.
The issue resides in question recognition by the ANTLR4 lexer. The graphql-java developer bbakerman mentions:
Testing confirmed that the max token code was certainly being hit, however the ANTLR lexing and parsing code was taking proportionally longer to get to the max token state because the enter dimension elevated
That is trigger by the grasping nature of the ANTLR Lexer – it would look forward and retailer tokens in reminiscence below sure grammar circumstances..
Graphql-java makes use of ANTLR4 for decomposing GraphQL queries to lexical tokens. The code line that raises the DoS vulnerability is situated within the file graphql/parser/Parser.java:
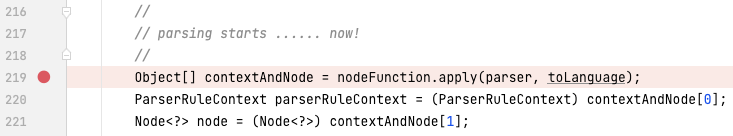
The decision chain goes to the file graphql/parser/antlr/GraphqlParser.java.
This file is generated routinely by ANTLR and relies on the grammar file Graphql.g4. The file with the .g4 extension comprises the grammar for the ANTLR parser. The file imports different g4 recordsdata, and so they all describe how ANTLR ought to parse GraphQL queries.
Additional investigation of ANTRL recordsdata revealed the susceptible sample. The sample inflicting the DoS vulnerability in GraphQL grammar is a basic “don’t.” The next rule is situated in the GraphqlSDL.g4 file:
...
schemaExtension :
EXTEND SCHEMA directives? '{' operationTypeDefinition+ '}' |
EXTEND SCHEMA directives+
;
And the directives rule isdescribed within the file GraphqlCommon.g4:
directives : directive+;
directive :'@' title arguments?;
The rule known as directives is repetitive and, moreover, applies repetition to the directive sub-rule. Nested repetition results in DoS threat. This difficulty will be in contrast with an “evil” regex.
It’s value mentioning that the schemaExtension rule shouldn’t be even used to acknowledge the question. It occurs as a result of the directives rule makes use of the adaptivePredict methodology within the ANTLR-generated code.
adaptivePredict algorithm is context-free by default – however, in case of ambiguity, it falls again to a context-sensitive evaluation to proceed with the popularity. This appears particularly related when a rule has a repetition operator since ANTLR can solely resolve which state to transit to after wanting forward till the top of the repetition. This lookup wouldn’t be an issue for a single repetition since ANTLR solely performs this evaluation as soon as per loop. Nevertheless, the code comprises nested repetition, which causes ambiguity inside each repetitions.
Repair #1
The diff for fastened code: https://github.com/graphql-java/graphql-java/pull/2892/recordsdata#diff-f9fc01d56c3bffa9c70fee9c9b3ad888d6890b84d774c20a99b2526b31500ab8
The thought behind the repair is similar because the DoS safety simply talked about—cease parsing question if it comprises greater than 15,000 (a default configurable worth) directives. This time, the examine is carried out earlier than passing the question to ANTLR processing.
The principle adjustments within the graphql/parser/Parser.java file:
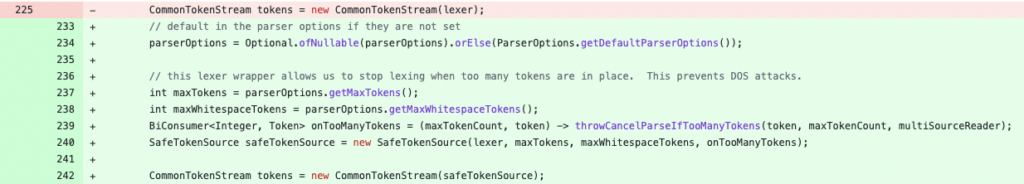
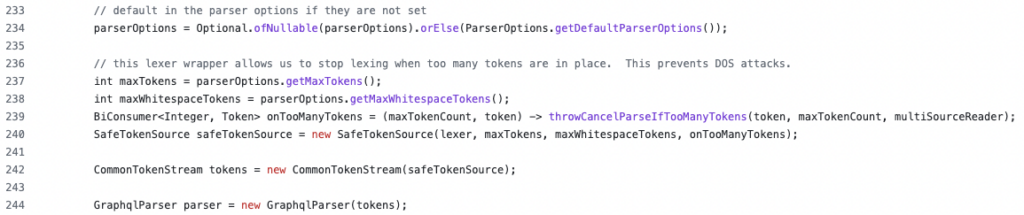
SafeTokenSource class is launched to confirm that the variety of tokens within the question doesn’t exceed a threshold. It prevents a malicious question from being caught by throwing an exception when a threshold is reached.
Further analysis of the fastened model confirmed that the repair protects graphql-java server solely in opposition to a single-threaded assault. An attacker can’t ship a single question with a considerable amount of “evil” directives; nevertheless, sending a number of requests concurrently (> 50-100 threads) containing a big, however allowed quantity, if directives nonetheless results in DoS, because the root explanation for the vulnerability was nonetheless there.
Repair #2
The second repair targets the foundation trigger. These adjustments repair the nested repetition of directives within the rule schemaExtension.
That is the modified code within the file src/primary/antlr/GraphqlSDL.g4:
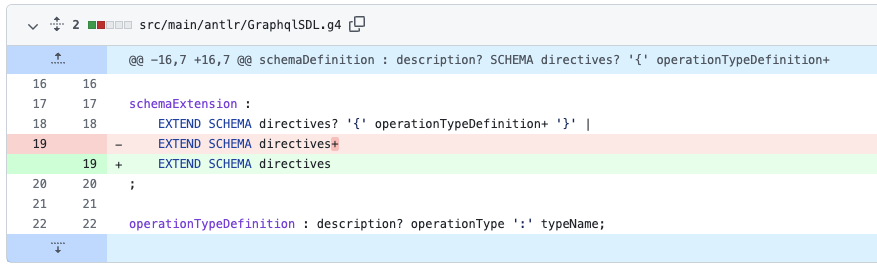
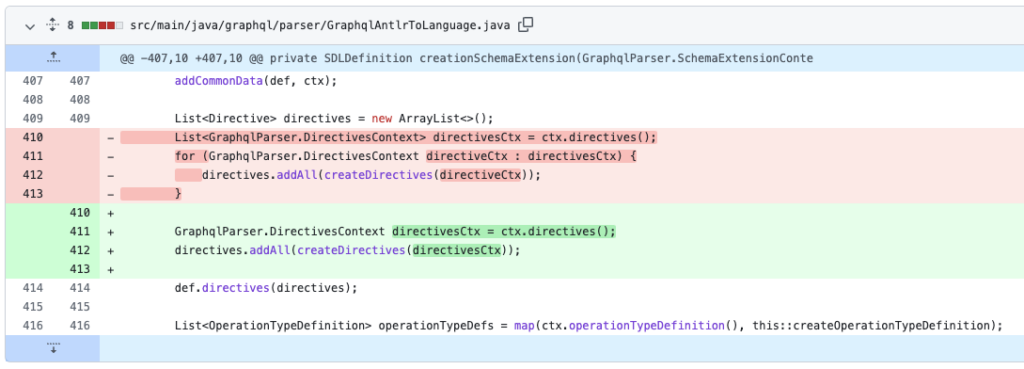
For fixing the nested repetition, it’s sufficient to delete the + (plus) signal for the directives. Additionally, it requires altering the parsing of the schema within the file src/primary/java/graphql/parser/GraphqlAntlrToLanguage.java.
After making use of the repair, a major distinction in execution time between the primary and the second fixes will be noticed:
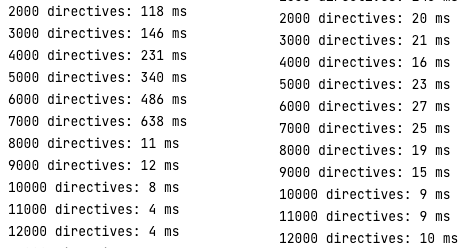
The utilized payload @aa is 2 characters lengthy. As proven within the screenshot above, 7000 directives, two chars lengthy every, don’t hit the 15000 chars restrict and eat far more assets when the second repair shouldn’t be utilized. The execution time turns into comparable after 8000 directives as a result of the primary repair blocks greater than 15000 characters and doesn’t parse them. The second repair eradicates the foundation trigger and prevents a DoS whatever the payload dimension.
The adjustments above have been utilized within the pull-request: https://github.com/graphql-java/graphql-java/pull/3071