Below sure situations, attackers can chain a set of vulnerabilities in a number of elements of the CUPS open-source printing system to execute arbitrary code remotely on susceptible machines.
Tracked as CVE-2024-47076 (libcupsfilters), CVE-2024-47175 (libppd), CVE-2024-47176 (cups-browsed) and CVE-2024-47177 (cups-filters) and found by Simone Margaritelli, these safety flaws do not have an effect on programs of their default configuration.
CUPS (brief for Frequent UNIX Printing System) is probably the most broadly used printing system on Linux programs, and additionally it is usually supported on gadgets working Unix-like working programs resembling FreeBSD, NetBSD, and OpenBSD and their derivates.
One in all its elements is the cups-browsed daemon, which searches the native community for marketed community or shared printers and makes them obtainable for printing on the machine. That is much like how Home windows and Macs can search the community for distant community printers to print to.
Margaritelli discovered that if the cups-browsed daemon is enabled, which isn’t on most programs, it can pay attention on UDP port 631. It is going to additionally, by default, enable distant connections from any machine on the community to create a brand new printer.
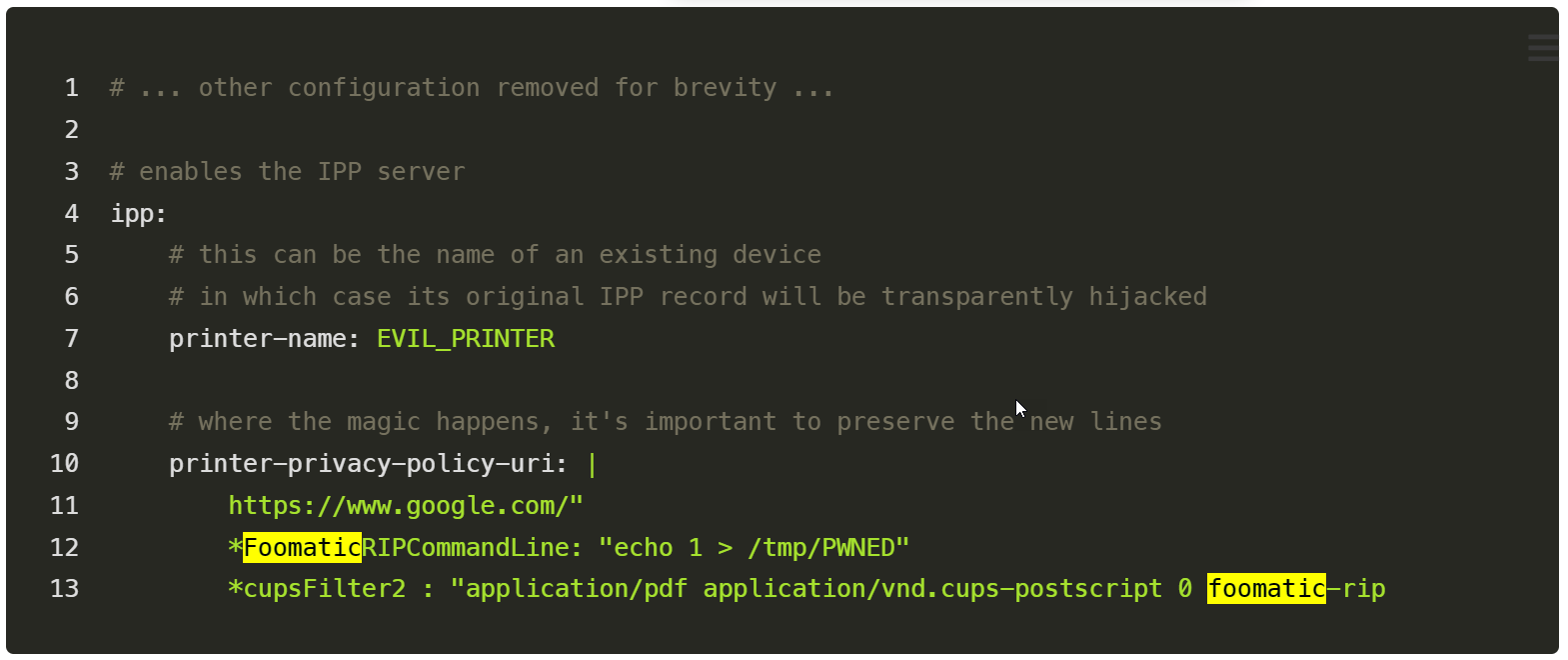
He found he might create a malicious PostScript Printer Description (PPD) printer that may very well be manually marketed to an uncovered cups-browsed service working on UDP port 631.
This causes the distant machine to routinely set up the malicious printer and make it obtainable for printing. If the consumer on that uncovered server prints to the brand new printer, the malicious command within the PPD might be executed regionally on the pc.
The command to execute when printing is added via a foomatic-rip filter, which executes instructions on a tool so {that a} print job is rendered appropriately.
Restricted world affect
Whereas it is a distant code execution chain, it needs to be famous from the beginning that attackers should overcome some obstacles to take advantage of the vulnerabilities and really obtain distant code execution.
The primary is that the focused programs will need to have the cups-browsed daemon enabled, which is often not enabled by default, to reveal their UDP ports on a community. Then, the attacker has to trick a consumer into printing from a malicious printer server on their native community that abruptly seems on their machine.
“It is a chain of bugs that rely on spoofing a printer in your local network that is automatically added via network discovery if it is turned on at all – usually not in its default configuration. Then an unverified variable that is used to exploit other vulnerabilities in the CUPS system to execute code, but only when a print job is triggered,” mentioned Ilkka Turunen, Discipline CTO at Sonatype.
“Good news then – it’s an RCE but with several mitigations, including the fact the attacker needs to be able to connect to a computer via UDP which is widely disabled on network ingress and the service is usually not on by default. It seems like the real world impact is low.”
For these causes, Purple Hat has rated the failings as having an “Important” severity affect as an alternative of important.
Whereas BleepingComputer’s exams confirmed that almost all of our Linux servers didn’t have the service enabled by default, considered one of our Ubuntu VMs did. Others have additionally famous on Twitter that cups-browsed was enabled by default on their Linux gadgets.
No patches, however mitigation measures can be found
Whereas patches are nonetheless in improvement, Purple Hat shared mitigation measures requiring admins to cease the cups-browsed service from working and stop it from being began on reboot utilizing the next instructions to interrupt the exploit chain:
sudo systemctl cease cups-browsed
sudo systemctl disable cups-browsed
Purple Hat customers can even use the next command to seek out out if cups-browsed is working on their programs:
sudo systemctl standing cups-browsed
If the outcome shows “Active: inactive (dead),” then the exploit chain is halted, and the system is just not susceptible. If the outcome reveals “running” or “enabled,” and the “BrowseRemoteProtocols” directive accommodates the worth “cups” within the configuration file /and so on/cups/cups-browsed.conf, then the system is susceptible.
