Cybercriminals are focusing on folks working in Web3 with pretend enterprise conferences utilizing a fraudulent video conferencing platform that infects Home windows and Macs with crypto-stealing malware.
The marketing campaign is dubbed “Meeten” after the title generally utilized by the assembly software program and has been underway since September 2024.
The malware, which has each a Home windows and a macOS model, targets victims’ cryptocurrency property, banking data, data saved on net browsers, and Keychain credentials (on Mac).
Meeten was found by Cado Safety Labs, which warns that menace actors continuously change names and branding for the pretend assembly software program and have beforehand used names like “Clusee,” “Cuesee,” “Meetone,” and “Meetio.”
Supply: Cado
These pretend manufacturers are backed by seemingly official web sites and social media accounts populated with AI-generated content material so as to add legitimacy.
Guests find yourself on the location by phishing or social engineering and are prompted to obtain what’s supposedly a gathering software however, in actuality, it’s Realst stealer.
“Based mostly on studies from targets, the rip-off is performed in a number of methods. In a single reported occasion, a person was contacted on Telegram by somebody they knew who wished to debate a enterprise alternative and to schedule a name. Nonetheless, the Telegram account was created to impersonate a contact of the goal. Much more apparently, the scammer despatched an funding presentation from the goal’s firm to him, indicating a classy and focused rip-off. Different studies of focused customers report being on calls associated to Web3 work, downloading the software program and having their cryptocurrency stolen.
After preliminary contact, the goal can be directed to the Meeten web site to obtain the product. Along with internet hosting data stealers, the Meeten web sites comprise Javascript to steal cryptocurrency that’s saved in net browsers, even earlier than putting in any malware.”
❖ Cado Safety
Along with the Realst malware, Cado says the “Meeten” web sites host JavaScript that makes an attempt to empty wallets that hook up with the location.
Concentrating on Macs and Home windows
Folks selecting to obtain the macOS model of the assembly software program get a bundle named ‘CallCSSetup.pkg,’ however different filenames have additionally been used prior to now.
When executed, it makes use of the macOS command-line instrument ‘osascript’ to ask the person to enter their system password, resulting in privilege escalation.
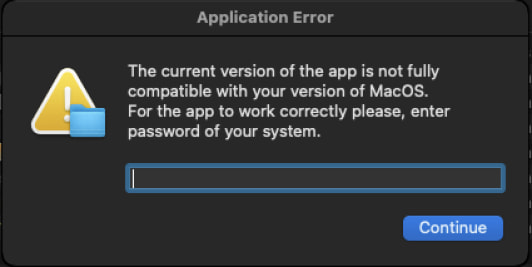
Supply: Cado
After coming into the password, the malware will show a decoy message stating, “Cannot connect to the server. Please reinstall or use a VPN.”
Nonetheless, within the background, the Realst malware steals knowledge hosted on the pc, together with:
- Telegram credentials
- Banking card particulars
- Keychain credentials
- Browser cookies and autofill credentials from Google Chrome, Opera, Courageous, Microsoft Edge, Arc, CocCoc, and Vivaldi
- Ledger and Trezor wallets
The info is first saved domestically in a folder, zipped, and finally exfiltrated to a distant tackle together with machine particulars like construct title, model, and system data.
The Home windows variant of Realst is distributed as a Nullsoft Scriptable Installer System (NSIS) file, named ‘MeetenApp.exe,’ and it is also digitally signed utilizing a stolen certificates from Brys Software program.
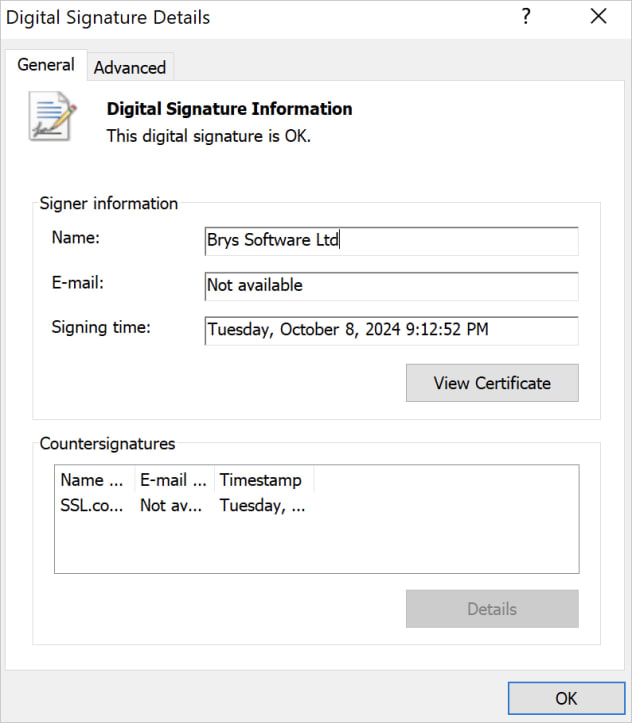
Supply: Cado
The installer incorporates a 7zip archive (“app-64”) and the core of an Electron software (“app.asar”) that incorporates JavaScript and sources, compiled utilizing Bytenode into V8 bytecode to evade detection.
The Electron app connects to a distant server at “deliverynetwork[.]observer” and downloads a password-protected archive (“AdditionalFilesForMeet.zip) containing a system profiler (“MicrosoftRuntimeComponentsX86.exe”) and the main malware payload (“UpdateMC.exe”).
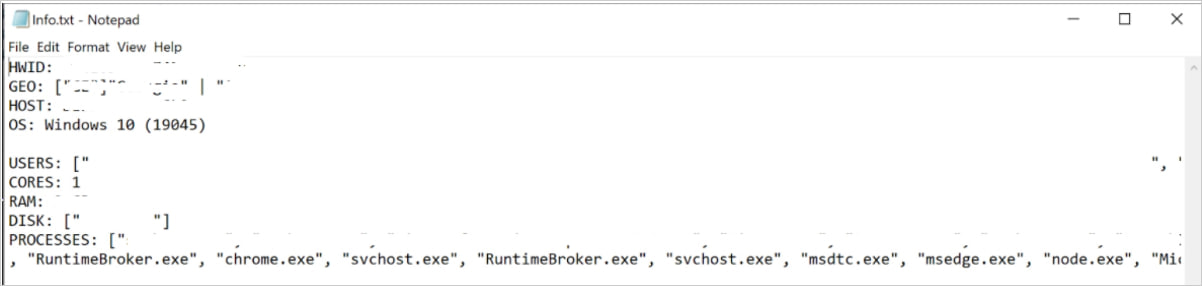
Supply: Cado
The Rust-based executable makes an attempt to gather the next data, add it to a ZIP file, and exfiltrate it:
- Telegram credentials
- Banking card particulars
- Browser cookies, historical past, and autofill credentials from Google Chrome, Opera, Courageous, Microsoft Edge, Arc, CocCoc, and Vivaldi
- Ledger, Trezor, Phantom, and Binance wallets
In comparison with macOS, the Home windows model contains a extra elaborate and versatile payload supply mechanism, higher evasion, and the power to persist between reboots by registry modification.
General, customers ought to by no means set up software program really helpful by customers by social media with out first verifying if the software program is respectable after which scanning it on a multi-engine antivirus instrument like VirusTotal.
These working in Web3 are significantly weak, as social engineering is a standard tactic used to construct a rapport with targets on this house, after which in the end trick targets into putting in malware to steal cryptocurrency.
