CrushFTP warned prospects immediately in a non-public memo of an actively exploited zero-day vulnerability fastened in new variations launched immediately, urging them to patch their servers instantly.
As the corporate additionally explains in a public safety advisory revealed on Friday, this zero-day bug allows unauthenticated attackers to flee the person’s digital file system (VFS) and obtain system information.
Nevertheless, these utilizing a DMZ (demilitarized zone) perimeter community in entrance of their important CrushFTP occasion are protected towards assaults.
“Please take immediate action to patch ASAP. A vulnerability was reported today (April 19th, 2024), and we patched it immediately. [..] This vulnerability exists in the wild,” the corporate warned prospects through electronic mail.
“The bottom line of this vulnerability is that any unauthenticated or authenticated user via the WebInterface could retrieve system files that are not part of their VFS. This could lead to escalation as they learn more, etc.”
The corporate additionally warned prospects with servers nonetheless working CrushFTP v9 to right away improve to v11 or replace their occasion through the dashboard.
“There is a simple rollback in case you have an issue or regression with some functionality. Update immediately,” CrushFTP warned.
The safety flaw was reported by Simon Garrelou of Airbus CERT and is now fastened in CrushFTP variations 10.7.1 and 11.1.0.
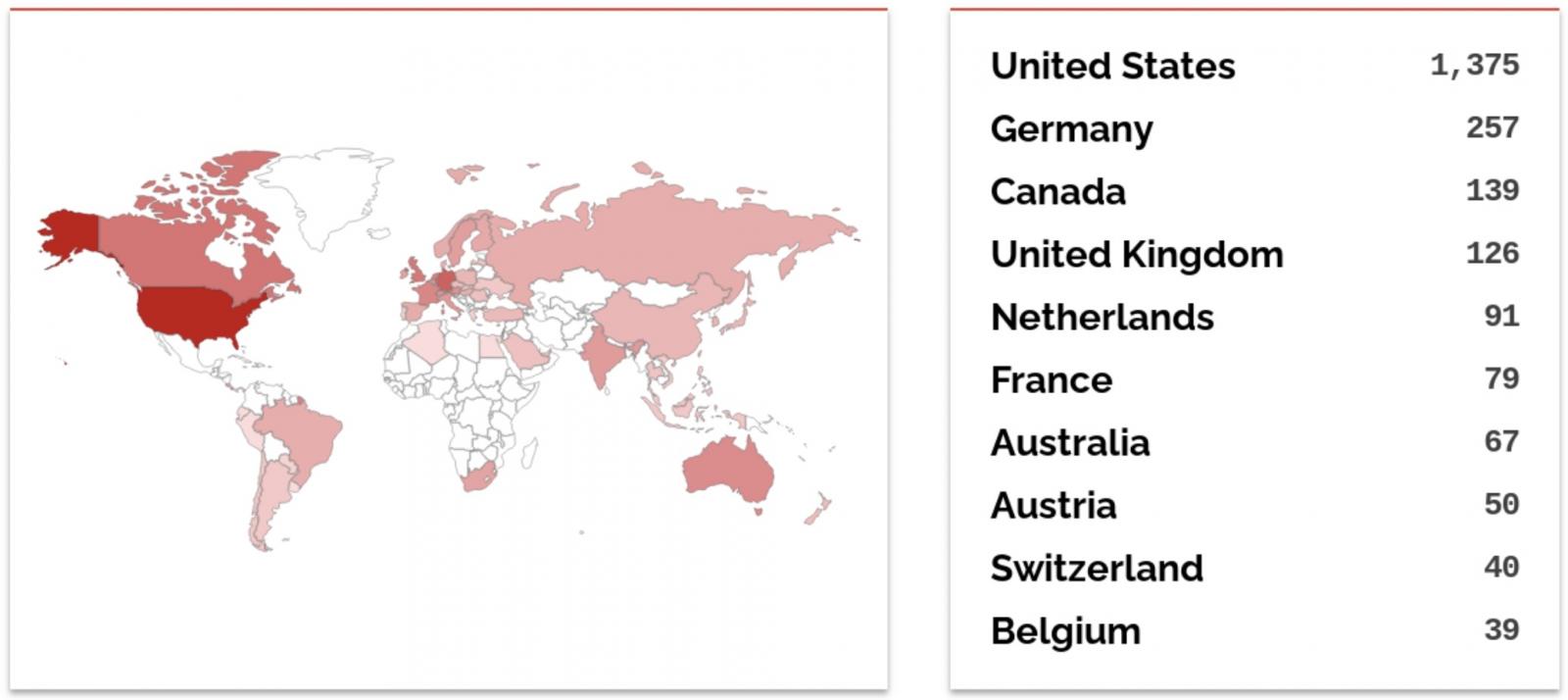
In keeping with Shodan, a minimum of 2,700 CrushFTP situations have their net interface uncovered on-line to assaults, though it is unimaginable to find out what number of have but to be patched.
Exploited in focused assaults
Cybersecurity firm CrowdStrike additionally confirmed the vulnerability (which has but to get a CVE ID assigned) in an intelligence report with extra data on the attackers’ ways, methods, and targets (TTPs).
CrowdStrike says its Falcon OverWatch and Falcon Intelligence groups have seen the CrushFTP zero-days being exploited in focused assaults.
The menace actors are focusing on CrushFTP servers at a number of U.S. organizations, and proof factors to an intelligence-gathering marketing campaign, possible politically motivated.
“Falcon OverWatch and Falcon Intelligence have observed this exploit being used in the wild in a targeted fashion,” CrowdStrike says.
“CrushFTP users should continue to follow the vendor’s website for the most up-to-date instructions and prioritize patching.”
In November, CrushFTP prospects had been additionally warned to patch a crucial distant code execution vulnerability (CVE-2023-43177) after Converge safety researchers who reported the flaw additionally launched a proof-of-concept exploit.
