A risk actor has been utilizing a content material supply community cache to retailer information-stealing malware in an ongoing marketing campaign focusing on methods U.S., the U.Okay., Germany, and Japan.
Researchers imagine that behind the marketing campaign is CoralRaider, a financially motivated risk actor centered on stealing credentials, monetary knowledge, and social media accounts.
The hackers ship LummaC2, Rhadamanthys, and Cryptbot data stealers which are obtainable on underground boards from malware-as-a-service platforms for a subscription charge.
Cisco Talos assesses with average confidence that the marketing campaign is a CoralRaider operation, based mostly on similarities in ways, strategies, and procedures (TTPs) with previous assaults attributed to the risk actor.
Hints pointing to CoralRaider embody the preliminary assault vectors, the usage of intermediate PowerShell scripts for decryption and payload supply, and particular strategies to bypass Person Entry Controls (UAC) on sufferer machines.
Cisco Talos
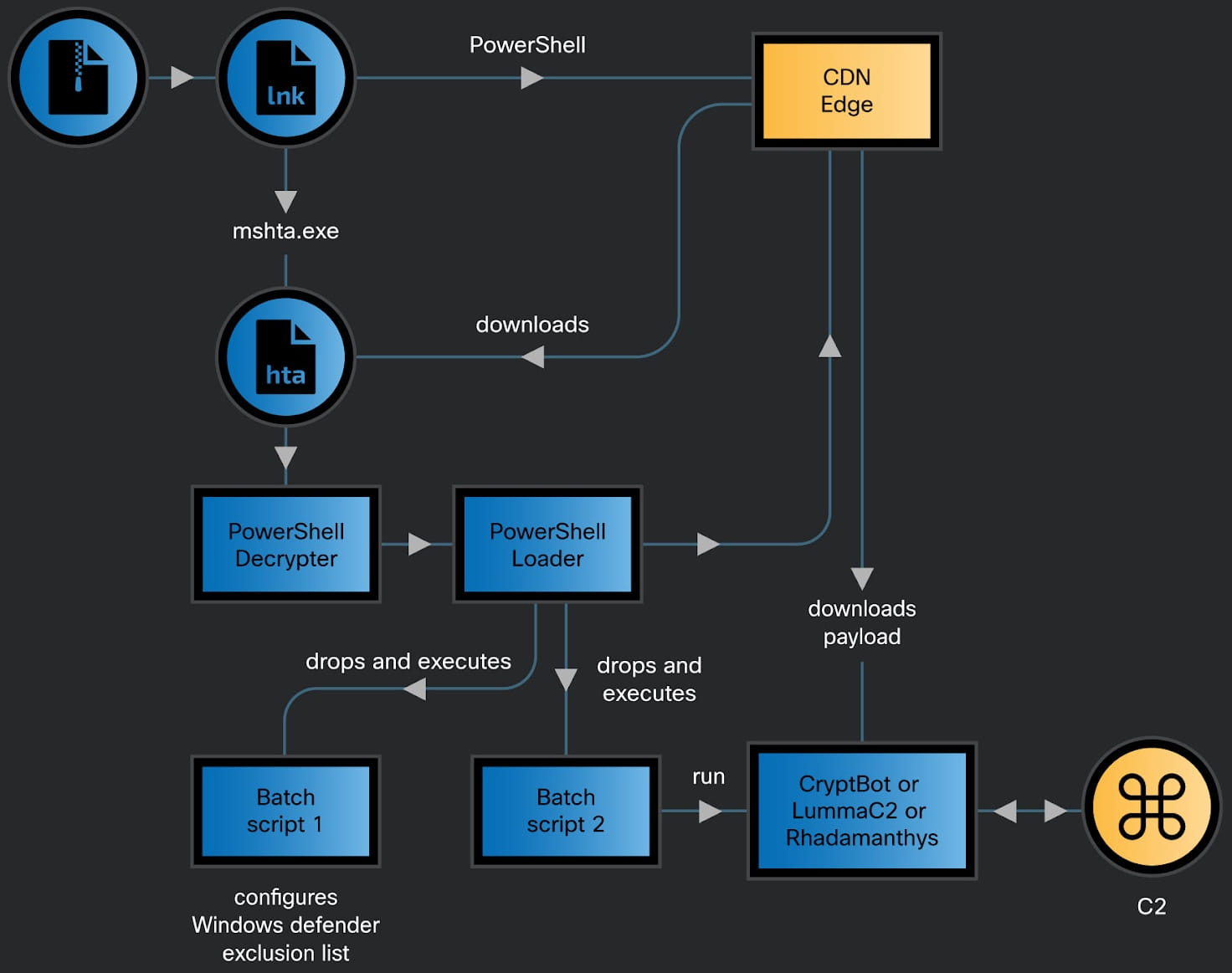
CoralRaider an infection chain
Cisco Talos stories that the most recent CoralRaider assaults begin with the sufferer opening an archive containing a malicious Home windows shortcut file (.LNK).
It’s unclear how the archive is delivered nevertheless it could possibly be as an attachment to a malicious electronic mail, as a obtain from an untrusted location, or promoted by means of malvertising.
The LNK comprises PowerShell instructions that obtain and execute a closely obfuscated HTML Utility (HTA) file from an attacker-controlled subdomain on the Bynny content material supply community (CDN) platform.
Through the use of the CDN cache as a malware supply server, the risk actor avoids request delays and in addition deceives community defenses.
The HTA file comprises JavaScript that decodes and runs a PowerShell decrypter script, which unpacks a second script that writes a batch script in a brief folder. The purpose is to stay undetected by modifying Home windows Defender exclusions.
A local Home windows binary, the FoDHelper.exe LoLBin, is used to edit registry keys and bypass the Person Entry Management (UAC) safety characteristic.
After this step, the PowerShell script downloads and executes one of many three data stealers (Cryptbot, LummaC2, or Rhadamanthys) that had been added in a location excluded from Defender’s scanning.
Cisco Talos
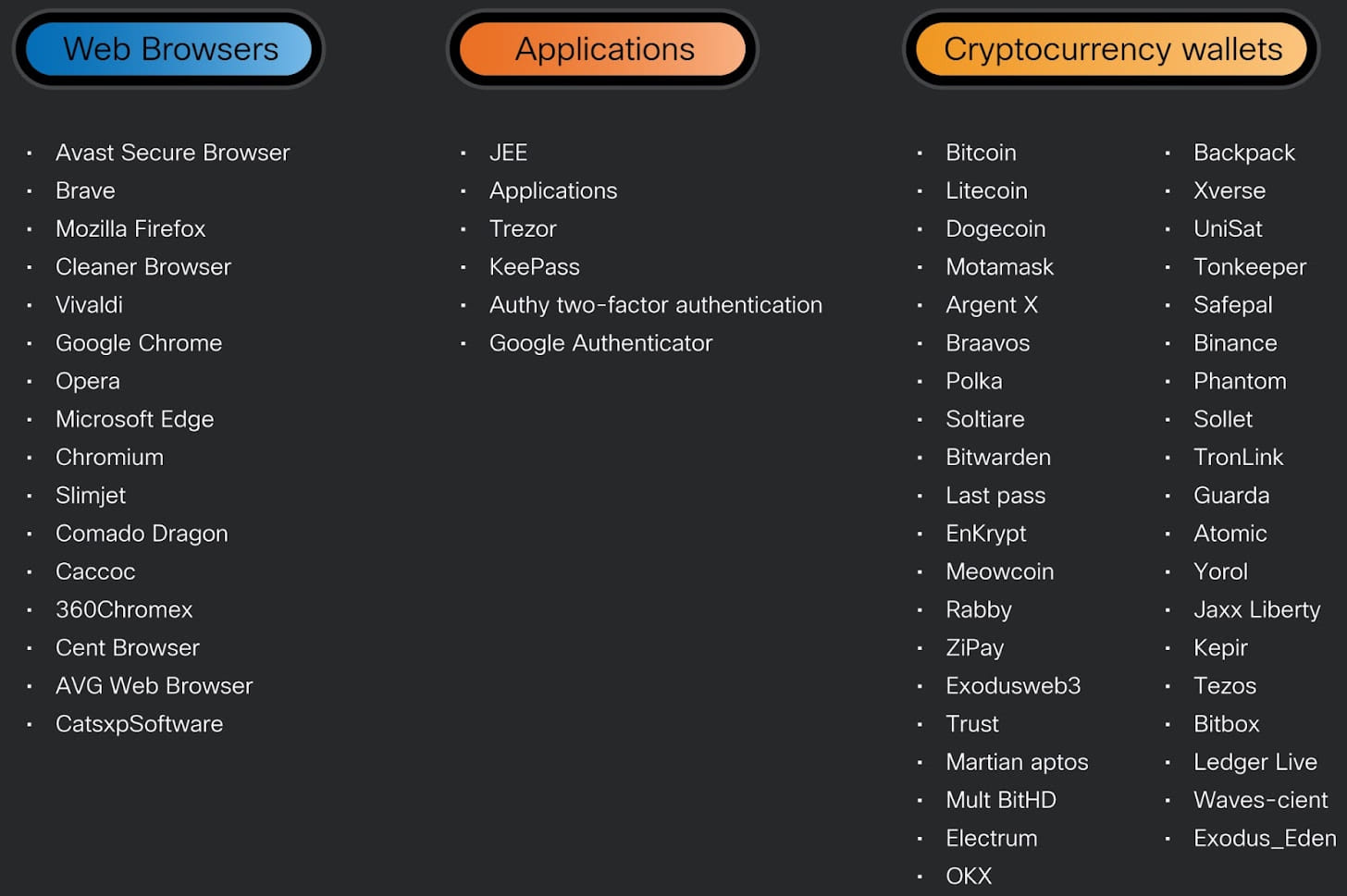
Data-stealing payloads
Cisco Talos says CoralRaider makes use of pretty current variations of LummaC2 and Rhadamanthys, which in late 2023 added highly effective options like capturing RDP logins and reviving expired Google account cookies [1, 2].
Though Cryptbot is much less fashionable, it’s a notable risk that contaminated 670,000 computer systems in a yr.
Cisco Talos says that the variant seen in CoralRaider’s current assaults was launched in January and has higher obfuscation and anti-analysis mechanisms, and an expanded checklist of focused purposes.
Cisco Talos
Cisco Talos additionally notes that Cryptbot can also be focusing on databases for password managers in addition to authenticator apps knowledge to steal cryptocurrency wallets protected with two-factor authentication.
CoralRaider has been energetic since a minimum of 2023 and researchers imagine it’s based mostly in Vietnam. In a earlier marketing campaign, the risk actor relied on a Telegram bot for command-and-control (C2) and to exfiltrate sufferer knowledge.
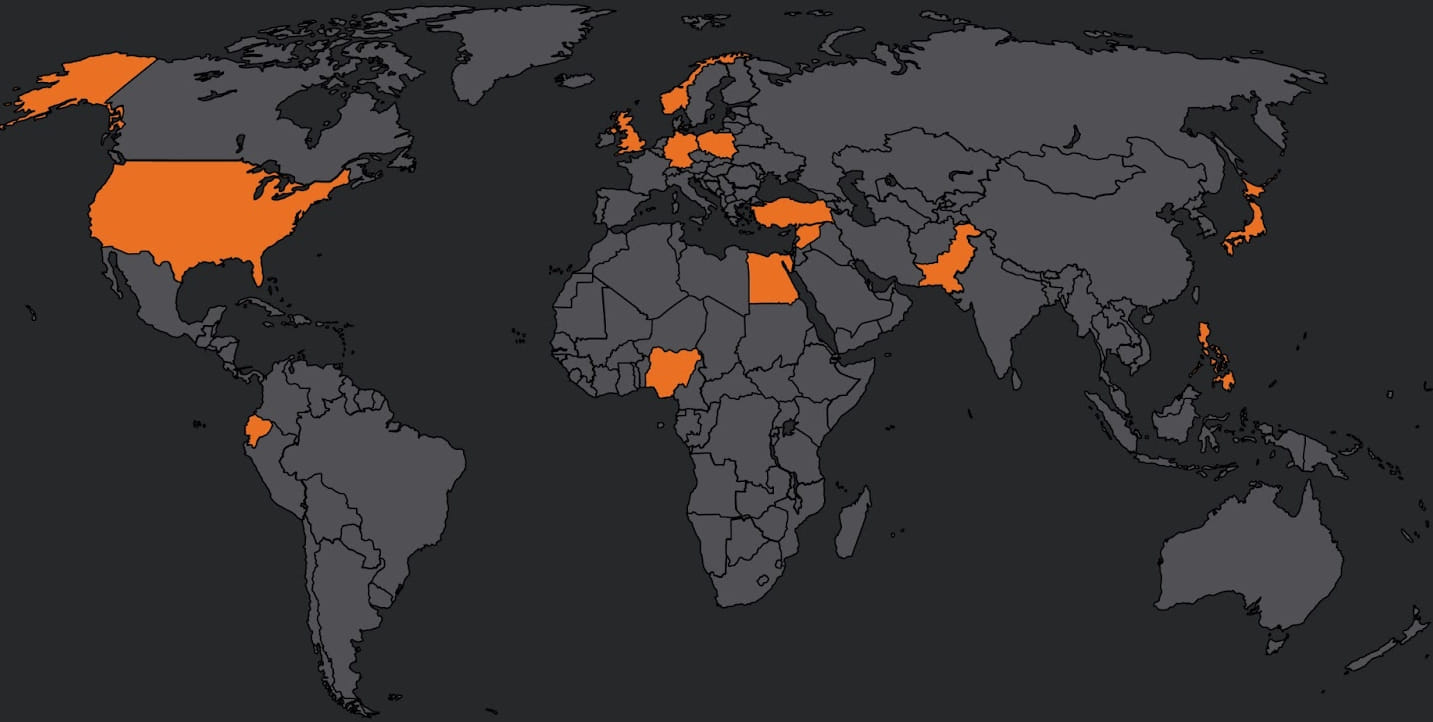
Its victims are usually in Asian and Southeast Asian international locations. Nevertheless, the most recent operation has prolonged focusing on to the U.S., Nigeria, Pakistan, Ecuador, Germany, Egypt, the U.Okay., Poland, the Philippines, Norway, Japan, Syria and Turkey.
