Sticking to container safety finest practices is vital for efficiently delivering verified software program, in addition to stopping extreme safety breaches and its penalties. These finest practices are an necessary a part of implementing a strong Cloud Native Software Safety Platform (CNAPP).
In accordance with the 2023 CNCF Survey, over 90 p.c of corporations are utilizing containers, whereas 84 p.c of corporations have been utilizing or evaluating Kubernetes. Container applied sciences have develop into mainstream and are current all over the place.
However aren’t containers meant to be protected and remoted? Nicely, form of.
For instance, an exploitable vulnerability inside a container, mixed with uncovered metadata and a flawed credentials configuration, can compromise your complete cloud infrastructure. As described in our Cloud lateral motion put up, a hacker can use this chain of exploits and flawed configurations to run crypto mining purposes in your cloud account.
Containers have been designed as a distribution mechanism for self-contained purposes, permitting them to execute processes in an remoted surroundings. For isolation functions, they make use of a light-weight mechanism utilizing kernel namespaces, eradicating the requirement of a number of extra layers in VMs, like a full working system, CPU and {hardware} virtualization, and so forth.
The lack of those extra abstraction layers, in addition to tightly coupling with the kernel, working system, and container runtime, make it simpler to make use of exploits to leap from contained in the container to the skin and vice versa.
Container safety finest practices don’t simply embody the delivered purposes and the securing containers picture itself, but additionally the complete element stack used for constructing, distributing, and specifically executing the container.
This consists of:
The host or VM
- The container runtime
- Cluster know-how
- Cloud supplier configuration
- And extra.
Safety may be utilized at every of the totally different phases: growth, distribution, execution, detection and response to threats.
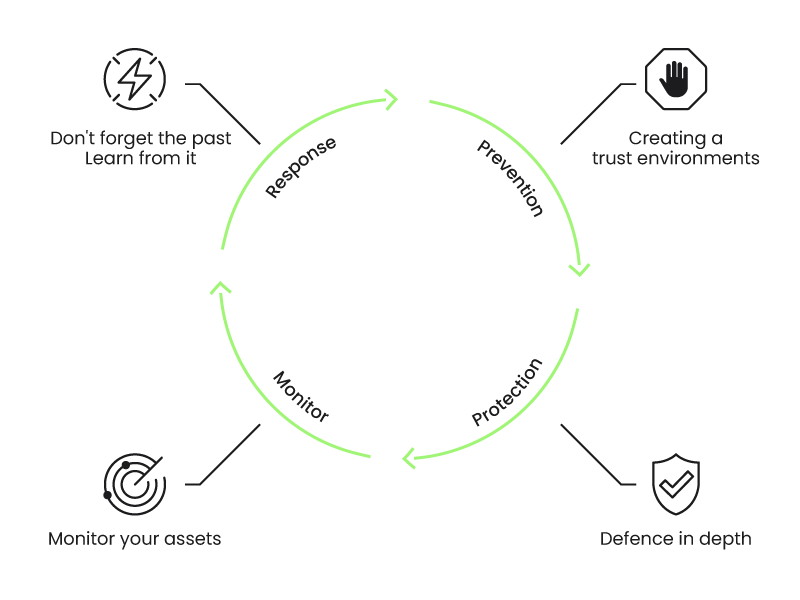
Let’s dive into the fascinating particulars, breaking down the overall concepts into 17 concrete container safety finest practices you could apply in your DevOps workflows.
A posh stack
Containers’ success is commonly fueled by two actually helpful options:
- They’re a actually handy option to distribute and execute software program, as a self-contained executable picture which incorporates all libraries and dependencies, whereas being a lot lighter than classical VM pictures.
- They provide a good stage of safety and isolation by utilizing kernel namespaces to execute processes in their very own “jail”, together with mounts, PID, community, IPC, and so forth., and likewise useful resource limiting CPU utilization and reminiscence by way of kernel cgroups. Reminiscence safety, permission enforcement, and so forth. are nonetheless supplied by way of the usual kernel safety mechanisms.
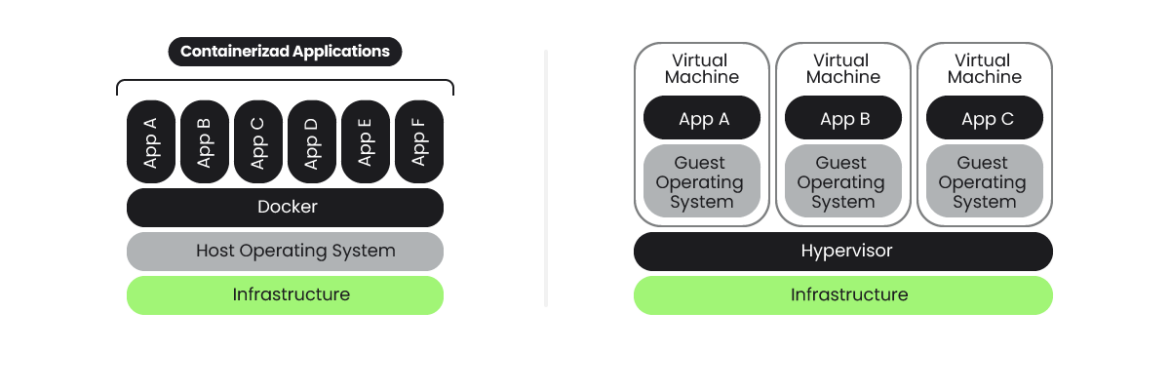
The container safety mannequin could be sufficient most often, however for instance, AWS provides extra safety for his or her serverless resolution. It does so by operating containers inside Firecracker, a micro digital machine that provides one other stage of virtualization to stop cross-customer breaches.
Does this imply containers usually are not protected?
You’ll be able to see it as a double-edged sword.
An software operating inside a container is not any totally different than an software operating immediately in a machine, sharing a file-system and processes with many different purposes. In a way, they’re simply purposes that might comprise exploitable vulnerabilities.
Working inside a container gained’t stop this, however will make it a lot more durable to leap from the appliance exploit to the host system, or entry information from different purposes.
Alternatively, containers depend upon one other set of kernel options, a container runtime, and often a cluster or orchestrator that could be exploited too.
So, we have to take the entire stack under consideration, and we will apply container safety finest practices on the totally different phases of the container lifecycle. Let’s replicate these two dimensions within the following diagram and give attention to the practices that may be utilized in every block:
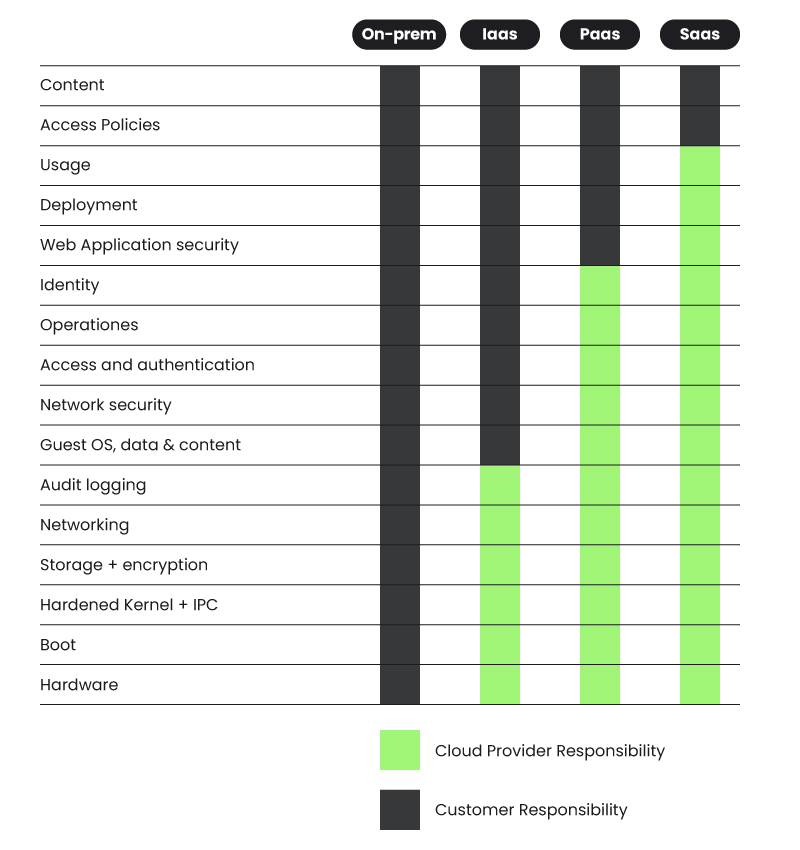
There will probably be instances just like the serverless compute engine ECS Fargate, Google Cloud Run, and so forth., the place a few of these items are out of our management, so we work on a shared duty mannequin.
- The supplier is answerable for protecting the bottom items working and secured
- And you can give attention to the higher layers.
Prevention: 8 steps for shift left safety
Earlier than your software inside a container is executed, there are a number of locations the place you can begin making use of totally different strategies to stop threats from taking place.
The software program provide chain has develop into a high entry level for cyber threats lately. Trendy companies routinely depend upon third-party purposes, dependencies, and packages, and there have been various main safety incidents the place risk actors exploited the provision chain.
Prevention and making use of container safety as early as potential is essential and can prevent loads of bother, time, and cash with minimal effort should you apply some good practices through the growth and distribution of the container pictures.
1. Combine Code Scanning on the CI/CD Course of
Safety scanning is the method of analyzing your software program, configuration or infrastructure, and detecting potential points or recognized vulnerabilities. Scanning may be completed at totally different levels:
- Code
- Dependencies
- Infrastructure as code
- Container Photos
- Hosts
- Cloud configuration
- … and extra
Let’s give attention to the primary stage: code. Earlier than you ship the appliance and even construct your software, you may scan your code to detect bugs or doubtlessly exploitable code (a brand new vulnerability).
For software code, you should use a device like Snyk Code or Checkmarx One for SAST (static software safety testing) to scan for vulnerabilities and different points. There are additionally open supply SAST instruments like sonarqube, which give vulnerability scanners for various languages, gosec for analyzing go code and detecting points primarily based on guidelines, linters, and so forth.
You’ll be able to run them on the developer machine, however integrating code scanning instruments on the CI/CD course of can make it possible for a minimal stage of code high quality is assured. For instance, you may block pull requests by default if some checks are failing.
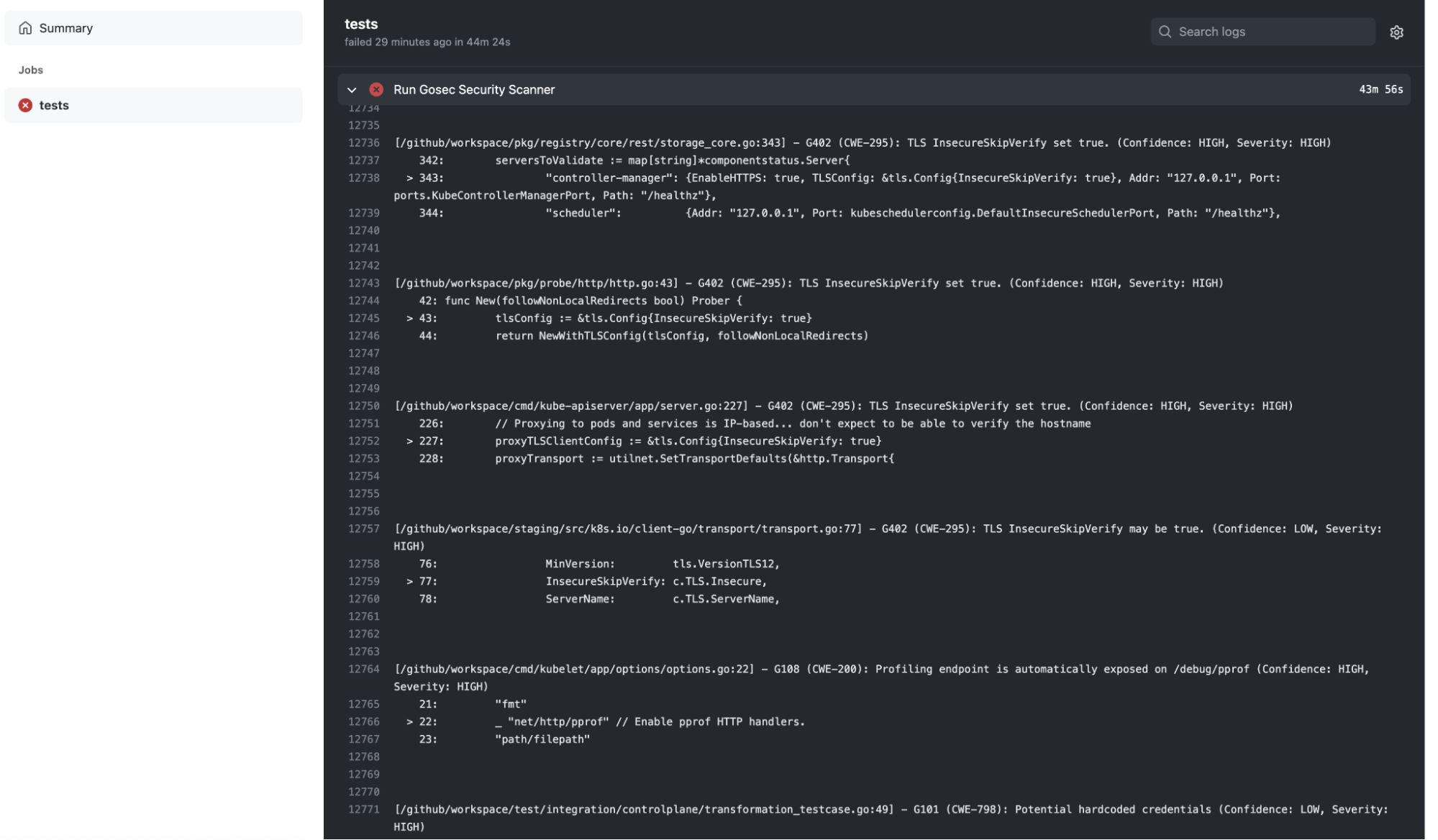
A Github Motion operating gosec:
identify: "Security Scan"
on:
push:
jobs:
exams:
runs-on: ubuntu-latest
env:
GO111MODULE: on
steps:
- identify: Checkout Supply
makes use of: actions/checkout@v2
- identify: Run Gosec Safety Scanner
makes use of: securego/gosec@grasp
with:
args: ./...
Code language: Perl (perl)And the corresponding output:
2. Cut back exterior vulnerabilities by way of dependency scanning
Solely very minimal and toy purposes are freed from third-party libraries or frameworks. However reusing code from exterior dependencies means you may be together with bugs and vulnerabilities from these dependencies as a part of your software. Dependency scanning ought to be included as a finest follow in any software construct course of.
Instruments like Snyk that supply SCA (software program composition evaluation) capabilities can be utilized to establish third-party dependencies. Bundle administration instruments, like npm, maven, go, and so forth., can match vulnerability databases along with your software dependencies and supply helpful warning.
For instance, enabling the dependency-check plugin in Maven requires simply including a plugin to the pom.xml:
<mission>
...
<construct>
...
<plugins>
...
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<model>6.2.2</model>
<executions>
<execution>
<targets>
<purpose>examine</purpose>
</targets>
</execution>
</executions>
</plugin>
...
</plugins>
...
</construct>
...
</mission>
Code language: Perl (perl)And each time maven is executed, it is going to generate a vulnerability report:
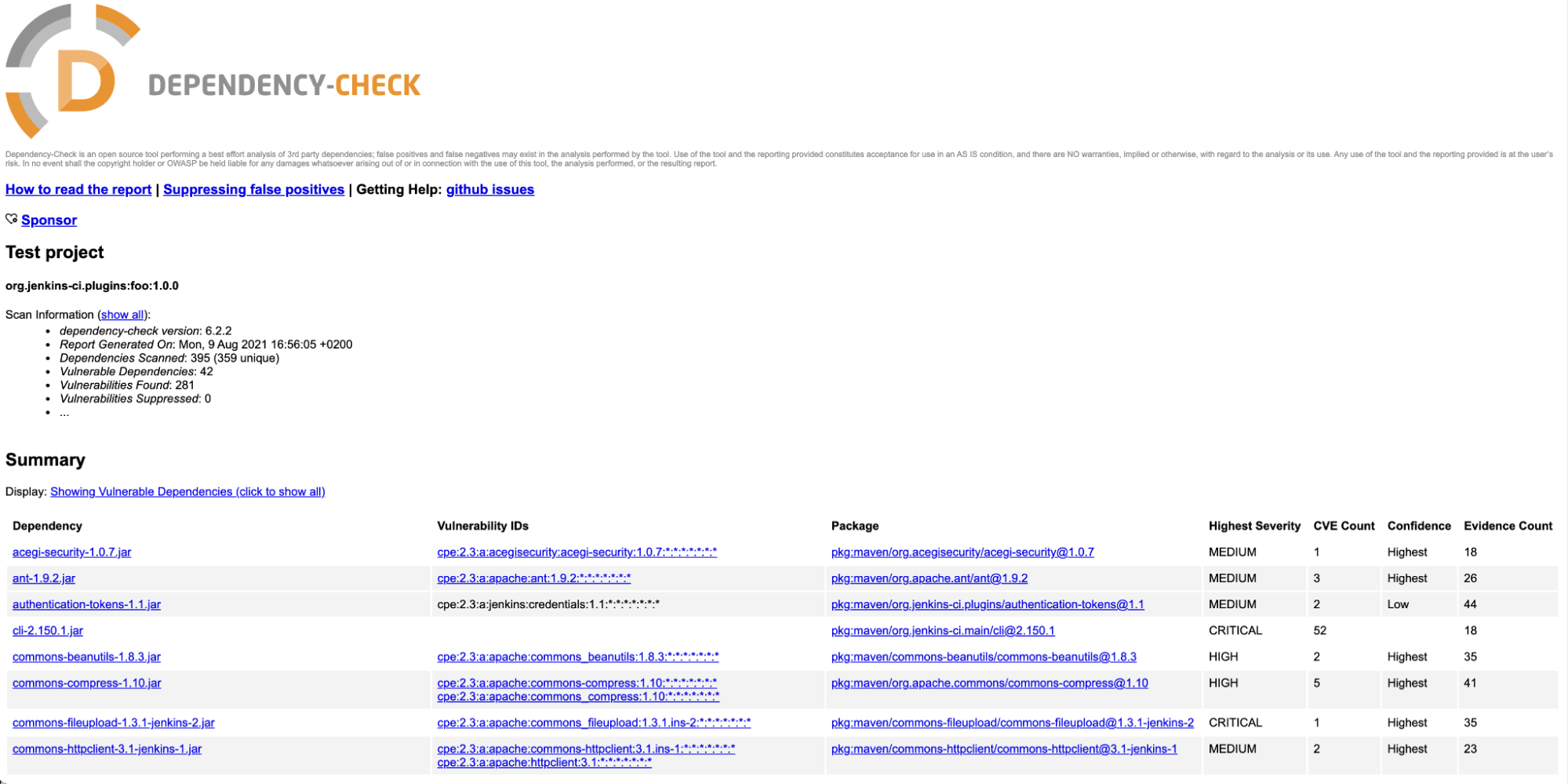
Keep away from introducing vulnerabilities by dependencies by updating them to newer variations with fixes.
In some instances, this won’t be potential as a result of the repair shouldn’t be out there, or bumping the model would require loads of refactoring attributable to breaking adjustments. Analyze the vulnerabilities revealed by dependency scanning to guage the influence and exploitability, and introduce extra measures like checks in your code or safety mechanisms to stop the vulnerability from being exploited.
Word that though it’s potential to additionally scan dependencies later, as soon as the appliance is constructed, dependency scanning will probably be much less correct as some metadata data shouldn’t be out there, and it could be unattainable for statically linked purposes like Go or Rust.
3. Use picture scanning to investigate container pictures
As soon as your software is constructed and packaged, it’s common to repeat it inside a container with a minimal set of libraries, dependent frameworks (like Python, Node, and so forth.), and configuration information. You’ll be able to learn our High 20 Dockerfile finest practices to study the perfect practices centered in securing containers constructing and runtime.
Use a picture scanner to investigate your container pictures. The picture scanning device will uncover vulnerabilities within the working system packages (rpm, dpkg, apk, and so forth.) supplied by the container picture base distribution. It would additionally reveal vulnerabilities in package deal dependencies for Java, Node, Python, and others, even should you didn’t apply dependency scanning within the earlier levels.
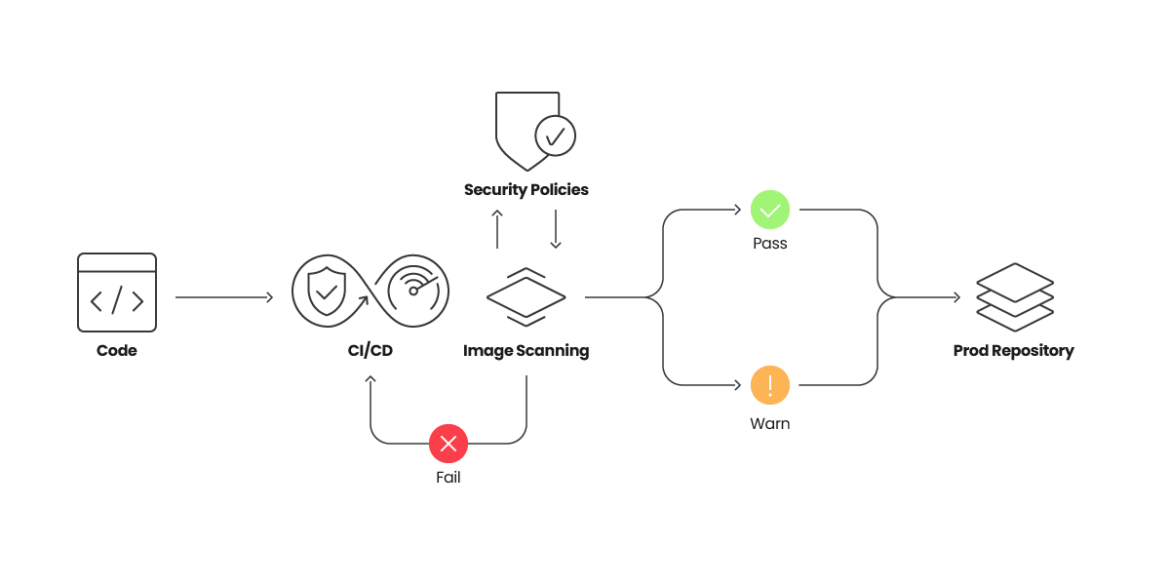
Picture Scanning is simple to automate and implement. It may be included as a part of your CI/CD pipelines, triggered when new pictures are pushed to a registry, or verified in a cluster admission controller to make it possible for non-compliant pictures are actually allowed to run. Another choice is utilizing Sysdig to scan pictures as quickly as they begin operating within the hosts the place they’re operating.
An instance is Github Motion integration with the Sysdig Safe Inline Scan Motion:
identify: "Security Scan"
on:
push:
jobs:
build-and-scan:
runs-on: ubuntu-latest
steps:
- identify: Construct the Docker picture
run: docker construct . --file Dockerfile --tag my-image:newest
- identify: Scan picture
id: scan
makes use of: sysdiglabs/scan-action@v3
with:
image-tag: my-image:newest
sysdig-secure-token: ${{ secrets and techniques.SYSDIG_SECURE_TOKEN }}
input-type: docker-daemon
run-as-user: root
Code language: Perl (perl)The earlier instance builds a Docker picture after which scans it domestically, from the Docker daemon.
Scan outcomes are supplied immediately as a part of the motion output, and pull-request may be blocked from merging relying on the examine standing:
4. Implement picture content material belief
Container picture integrity may be enforced by including digital signatures by way of Notary or related, which then may be verified within the Admission Controller or the container runtime.
Let’s see a fast instance:
$ docker belief key generate example1
Producing key for example1...
Enter passphrase for new example1 key with ID 7d7b320:
Repeat passphrase for new example1 key with ID 7d7b320:
Efficiently generated and loaded non-public key. Corresponding public key out there: /Customers/airadier/example1.pub
Code language: Perl (perl)Now, we have now a signing key referred to as “example1”. The general public half is positioned in:
$HOME/example1.pub
Code language: Perl (perl)and the non-public counterpart will probably be positioned in:
$HOME/.docker/belief/non-public/<key ID>.key
Code language: Perl (perl)Different builders may also generate their keys and share the general public half.
Now, we allow a signed repository by including the keys of the allowed signers to the repository (airadier/alpine within the instance):
$ docker belief signer add --key example1.pub example1 airadier/alpine
Including signer "example1" to airadier/alpine...
Initializing signed repository for airadier/alpine...
...
Enter passphrase for new repository key with ID 16db658:
Repeat passphrase for new repository key with ID 16db658:
Efficiently initialized "airadier/alpine"
Efficiently added signer: example1 to airadier/alpine
Code language: Perl (perl)And we will signal a picture within the repository with:
$ docker belief signal airadier/alpine:newest
Signing and pushing belief information for native picture airadier/alpine:newest, might overwrite distant belief information
The push refers to repository [docker.io/airadier/alpine]
bc276c40b172: Layer already exists
newest: digest: sha256:be9bdc0ef8e96dbc428dc189b31e2e3b05523d96d12ed627c37aa2936653258c dimension: 528
Signing and pushing belief metadata
Enter passphrase for example1 key with ID 7d7b320:
Efficiently signed docker.io/airadier/alpine:newest
Code language: Perl (perl)If the DOCKER_CONTENT_TRUST surroundings variable is about to 1, then pushed pictures will probably be mechanically signed:
$ export DOCKER_CONTENT_TRUST=1
$ docker push airadier/alpine:3.11
The push refers to repository [docker.io/airadier/alpine]
3e207b409db3: Layer already exists
3.11: digest: sha256:39eda93d15866957feaee28f8fc5adb545276a64147445c64992ef69804dbf01 dimension: 528
Signing and pushing belief metadata
Enter passphrase for example1 key with ID 7d7b320:
Efficiently signed docker.io/airadier/alpine:3.11
Code language: Perl (perl)We will examine the signers of a picture with:
$ docker belief examine --pretty airadier/alpine:newest
Signatures for airadier/alpine:newest
SIGNED TAG DIGEST SIGNERS
newest be9bdc0ef8e96dbc428dc189b31e2e3b05523d9... example1
Checklist of signers and their keys for airadier/alpine:newest
SIGNER KEYS
example1 7d7b320791b7
Administrative keys for airadier/alpine:newest
Repository Key: 16db658159255bf0196...
Root Key: 2308d2a487a1f2d499f184ba...
Code language: Perl (perl)When the surroundings variable DOCKER_CONTENT_TRUST is about to 1, the Docker CLI will refuse to drag pictures with out belief data:
$ export DOCKER_CONTENT_TRUST=1
$ docker pull airadier/alpine-ro:newest
Error: distant belief information does not exist for docker.io/airadier/alpine-ro: notary.docker.io does not have belief information for docker.io/airadier/alpine-ro
Code language: Perl (perl)You’ll be able to implement content material belief in a Kubernetes cluster by utilizing an Admission controller.
5. Frequent safety misconfigurations and remediations
Wrongly configured hosts, container runtimes, clusters, or cloud assets can go away a door open to an assault, or create a straightforward option to escalate privileges and carry out lateral motion.
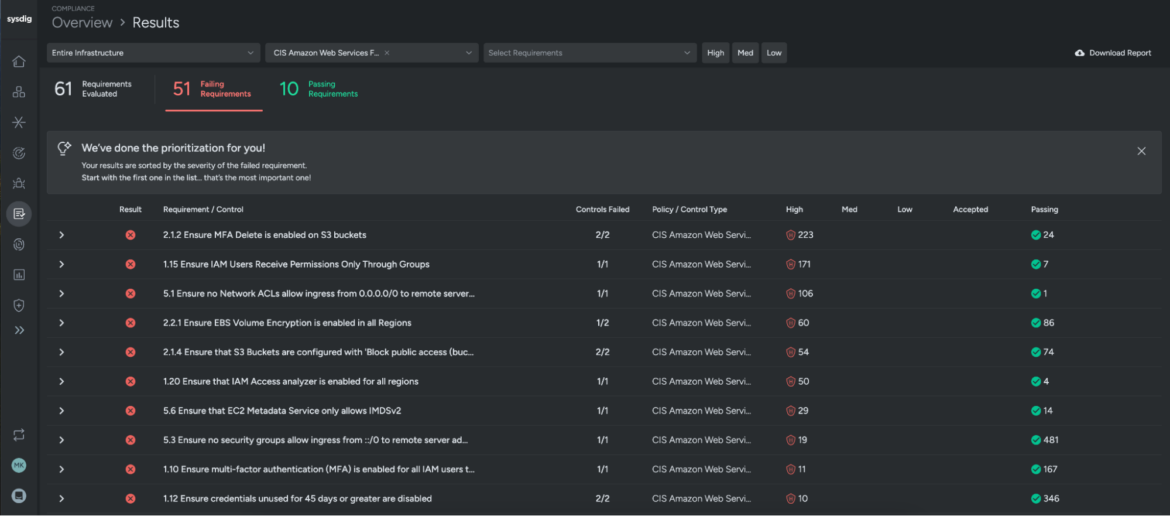
Benchmarks, finest practices, and hardening guides give you details about tips on how to spot these misconfigurations, why they’re an issue, and tips on how to remediate them. Amongst totally different sources of data, the Middle for Web Safety (CIS) is paramount. It’s a non-profit group that publishes free benchmarks for a lot of totally different environments, the place any particular person and firm can contribute with their information. It has develop into a de facto customary for safety benchmarking.
One of the best ways to be sure you can examine this sort of setting for container safety is to automate it as a lot as potential. A number of instruments exist for this, primarily primarily based on static configuration evaluation, permitting you to examine configuration parameters at totally different ranges and supply steering in fixing them. Sysdig Safe features a Compliance function which may help you schedule, execute, and analyze your entire infrastructure (Linux hosts, Docker, Kubernetes, EKS, GKE, AKS, MKE, OpenShift clusters, and so forth.) primarily based on CIS Benchmarks, in addition to compliance requirements, like PCI DSS, SOC 2, NIST 800-53, NIST 800-190, HIPAA, ISO 27001, GDPR and others, all in a single centralized dashboard.
Different instruments you should use are linux-bench, docker-bench, kube-bench, kube-hunter, kube-striker, Cloud Custodian, OVAL, and OS Question.
Instance host benchmark management
A bodily machine the place you simply put in Linux, a digital machine provisioned on a cloud supplier, or on-prem might comprise a number of insecure out-of-the-box configurations that you’re not conscious of. If you happen to plan to make use of it for a chronic interval, with a manufacturing workload or publicity to the web, it’s a must to take particular care of them. That is additionally true for Kubernetes or OpenShift nodes. In any case, they’re digital machines; don’t assume that if you’re utilizing a cluster provisioned by your cloud supplier that they arrive completely secured.
CIS has a benchmark for Distribution Independant Linux, and one particularly for Debian, CentOs, Pink Hat, and lots of different distributions.
Examples of misconfigurations you may detect:
Instance linux distribution
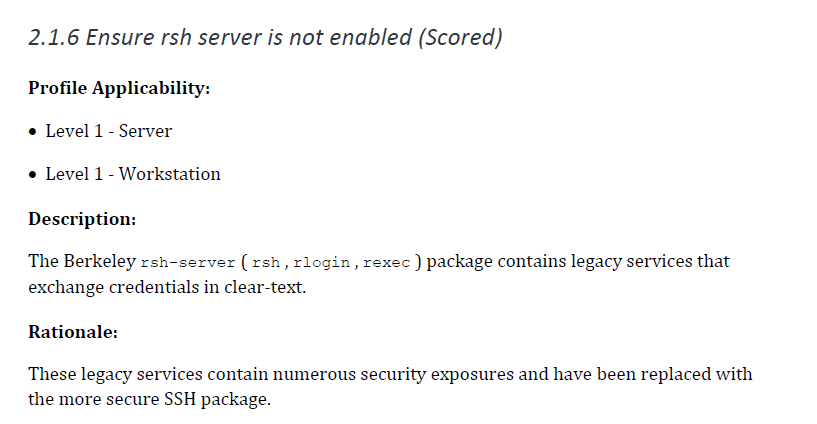
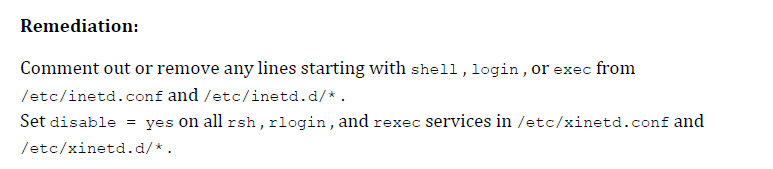
The next determine is supplied by CIS Benchmark for Distribution Unbiased Linux, the configuration is to make sure rsh server shouldn’t be enabled.
Instance securing containers runtime benchmark management
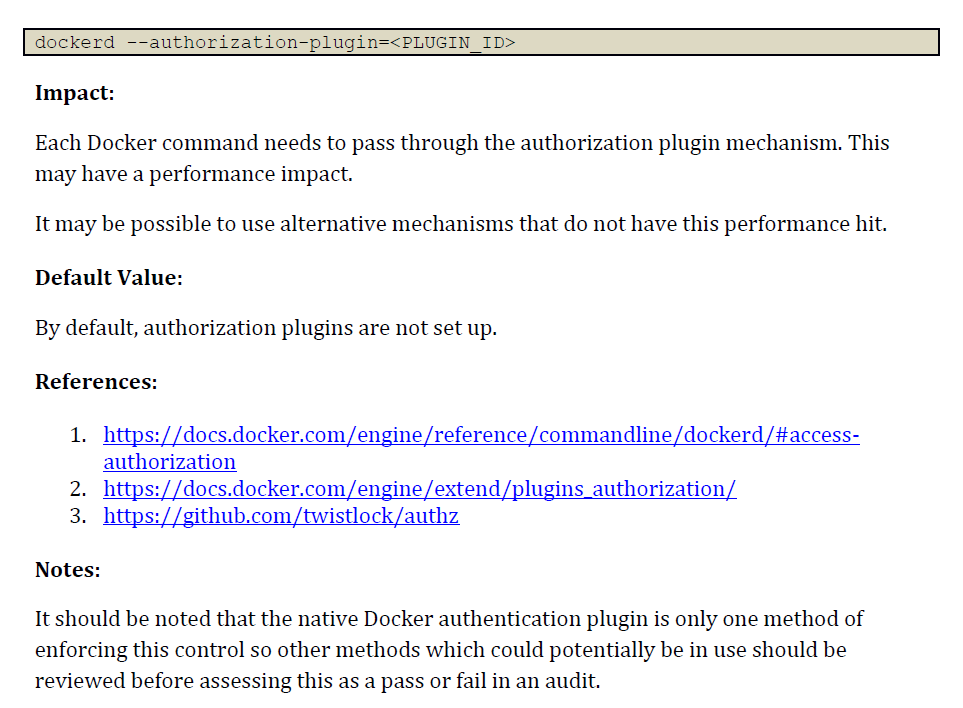
If you happen to set up a container runtime like Docker by your self in a server you personal, it’s important you utilize a benchmark to ensure any default insecure configuration is remediated. The subsequent determine exhibits the configuration to make sure that authorization for Docker shopper instructions is enabled.

Instance orchestrator benchmark management
Kubernetes, by default, leaves many authentication mechanisms to be managed by third-party integrations. A benchmark will guarantee all potential insecurities are handled. The picture beneath exhibits us the configuration to make sure that the –anonymous-auth argument is about to false.
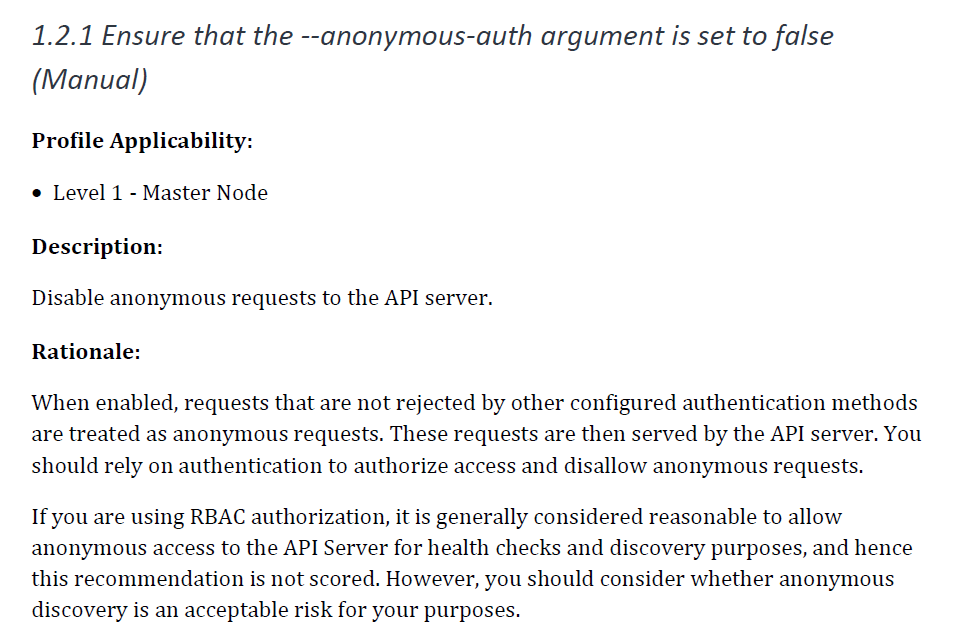
Instance cloud benchmark management
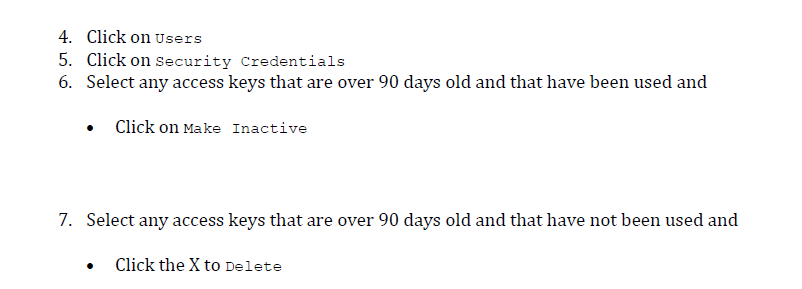
Benchmarks on cloud supplier accounts, additionally referred to as Cloud Security Posture Administration (CSPM), are important, as they’ll examine the safety on each single asset on the account. All settings that might result in an assault, assets that ought to be non-public however are made public (e.g., S3 buckets), or storage that lacks encryption are outlined in this sort of benchmark. It is a benchmark that’s important to automate, because the belongings within the cloud account change on a regular basis, and it’s a must to continually watch that all the pieces is as safe as potential. The next picture is an instance of configuration examine that ensures credentials unused for 90 days or better are disabled.
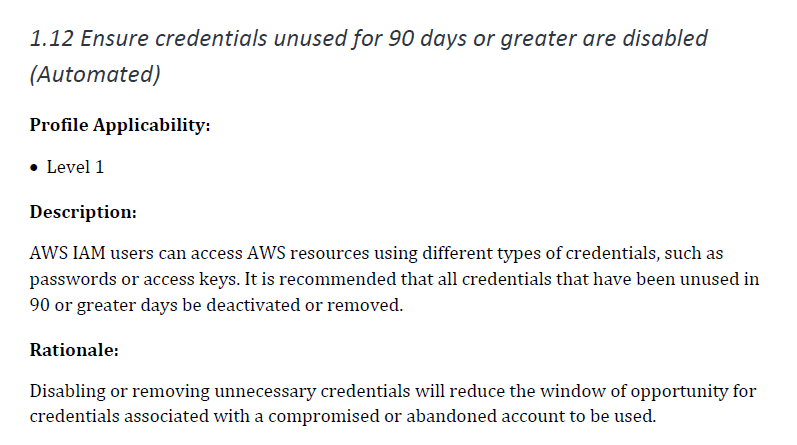
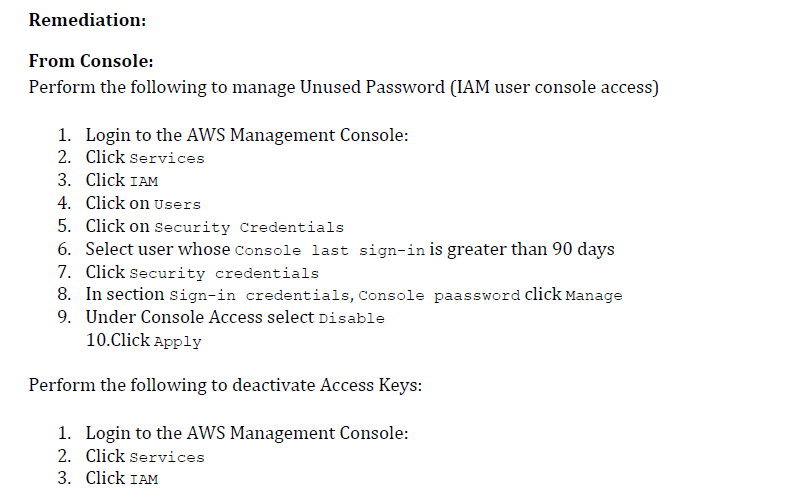
6. Incorporate IaC scanning and coverage as code
Cloud useful resource administration is a posh activity, and instruments like Terraform or CloudFormation may help leverage this burden. Infrastructure is declared as code – aka “Infrastructure as Code” – saved and versioned in a repository, and automation takes care of making use of the adjustments within the definition to maintain the present infrastructure updated with the declaration.
In case you are utilizing infrastructure as code, incorporate instruments with IaC scanning capabilities to validate the configuration of your infrastructure earlier than it’s created or up to date. Just like different linting instruments, apply IaC scanning instruments domestically and in your pipeline, and take into account blocking adjustments that introduce safety points.
Coverage as code is a associated strategy during which the insurance policies governing safety, infrastructure, and extra are outlined and managed by code. This strategy may be leveraged to automate compliance and governance throughout IaC and Kubernetes environments to make sure scalability and consistency throughout a corporation.
Sysdig consists of IaC safety capabilities, scanning for misconfigurations throughout IaC instruments together with Terraform, Helm, or YAML information and mapping them again to the supply, in addition to leveraging OPA, the OSS customary for coverage administration, to implement constant insurance policies throughout a number of IaC sources and Kubernetes clusters.
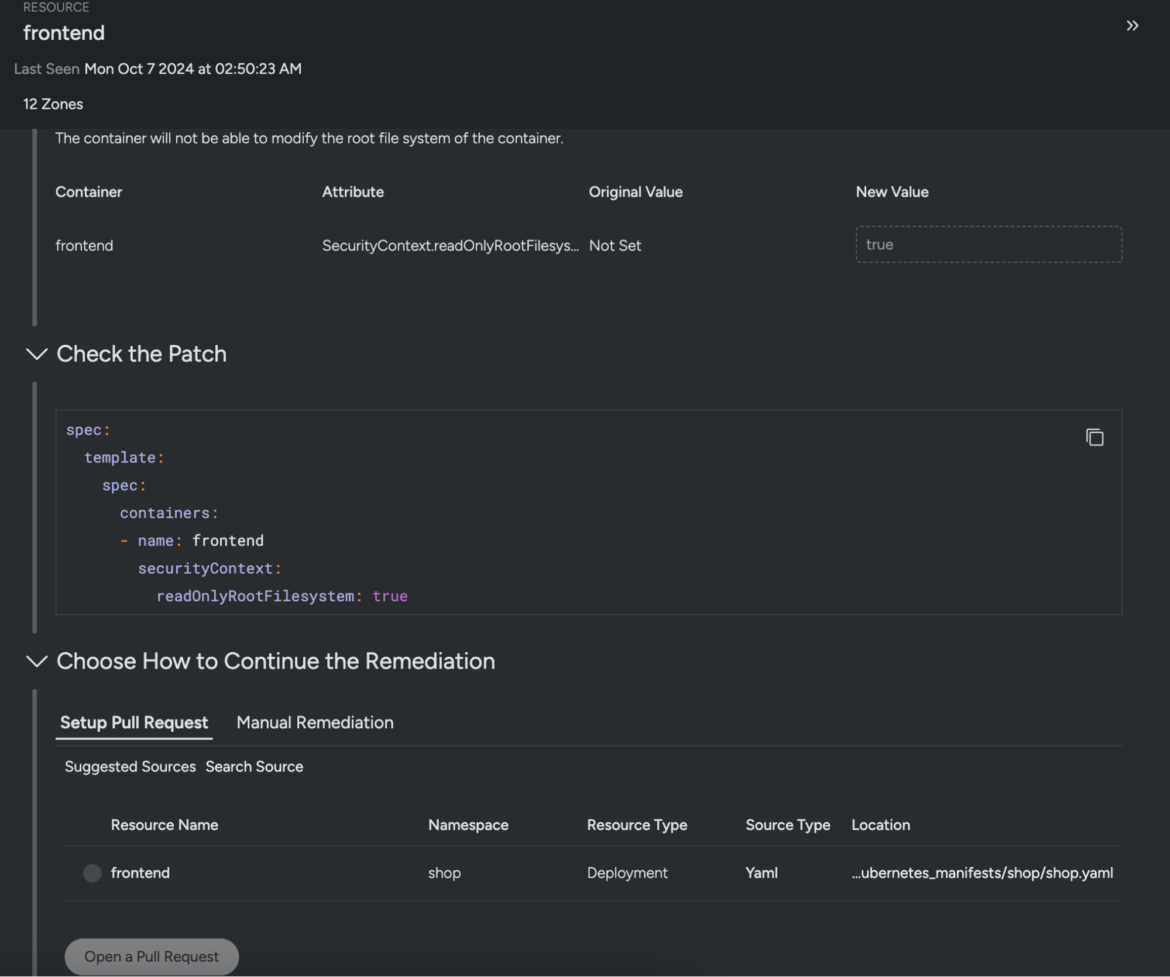
7. Safe your host with host scanning
Securing your host is simply as necessary as securing containers. The host the place the containers are operating is often composed of an working system with a Linux kernel, a set of libraries, a container runtime, and different frequent providers and helpers operating within the background. Any of those elements may be weak or misconfigured, and might be used because the entry level to entry the operating containers or trigger a denial of service assault.
For instance, points within the container runtime itself may cause an influence in your operating containers, like this DoS assault that forestalls creating new containers in a bunch.
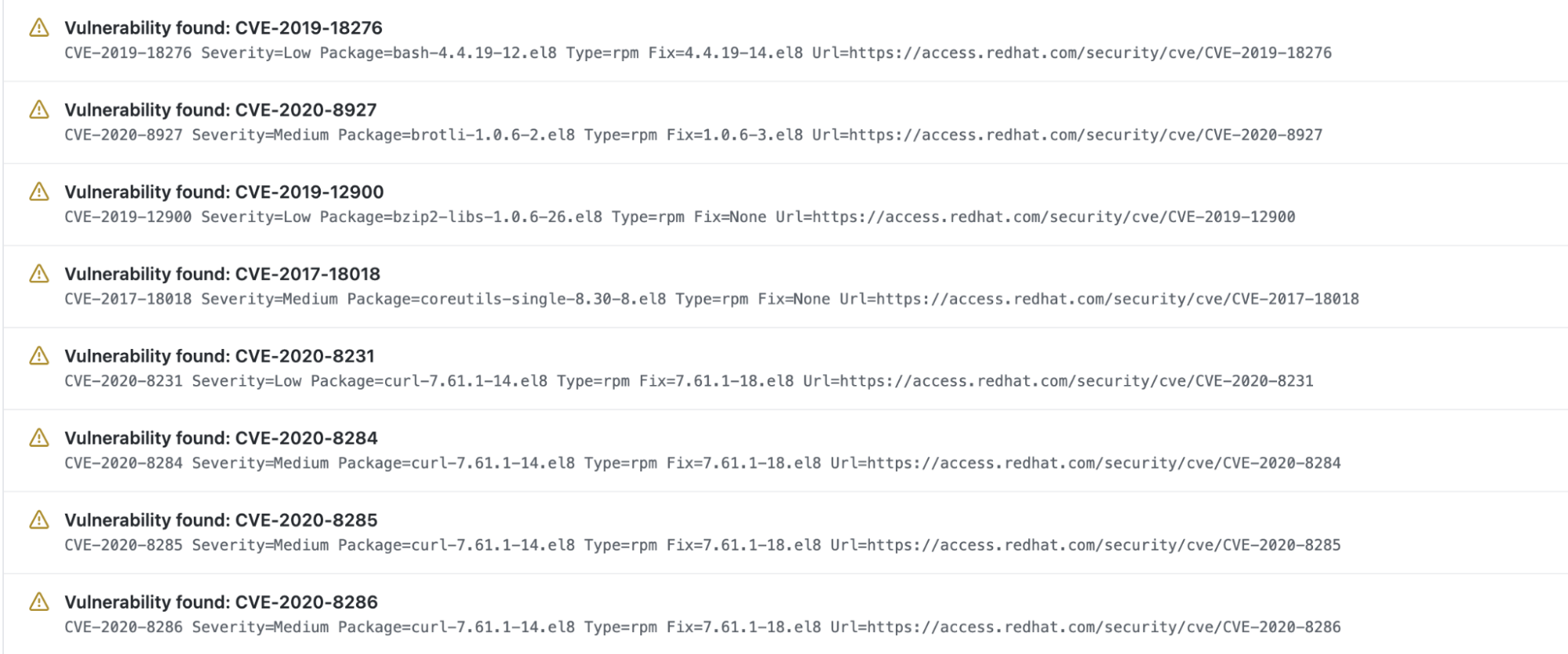
We already talked about hardening host configuration within the “Unsafe configuration” part. However how can we detect weak elements? A host scanning device can detect recognized vulnerabilities within the kernel, customary libraries like glibc, providers, and even the container runtime residing within the host (fairly much like what picture scanning does for a container picture).
Sysdig will transparently scan your hosts and report discovered vulnerabilities. The next determine exhibits how simple it’s to detect dangers at a look on the dashboard.
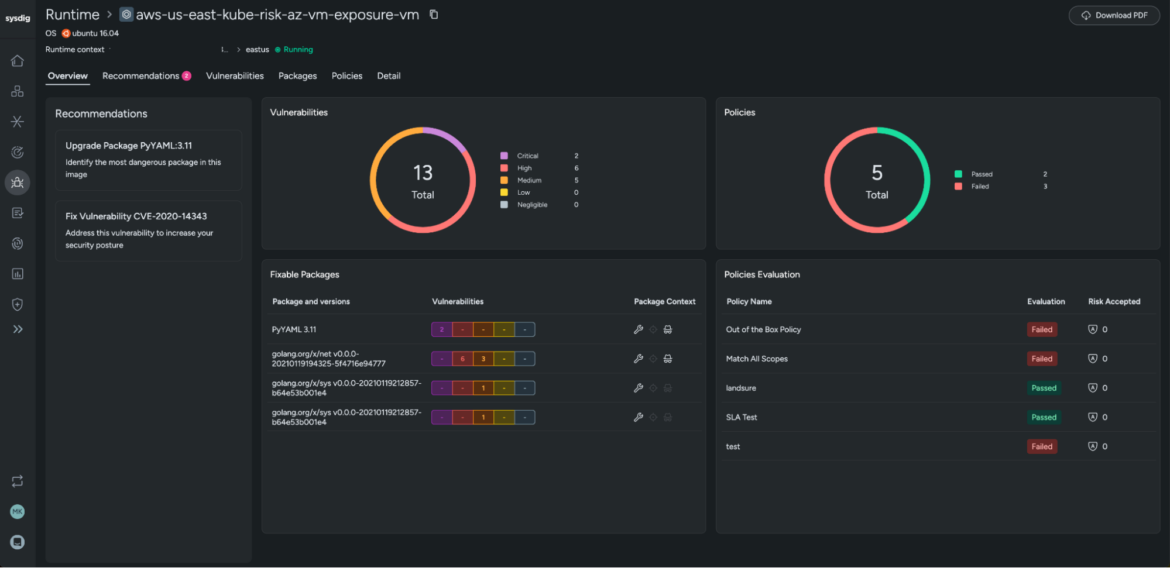
Use this data to replace the working system, kernel, packages, and so forth. Do away with probably the most vital and exploitable vulnerabilities, or at the least pay attention to them, and apply different safety mechanisms like firewalls, limiting person entry to the host, stopping unused providers, and so forth.
8. Stop unsafe containers from operating
As a final line of protection, Kubernetes Admission Controllers can block unsafe containers from operating within the cluster. Whereas the picture scanning finest practices described earlier can mitigate this concern, not all the pieces you deploy will undergo your CI/CD pipeline or recognized registries. There are additionally third-party pictures and handbook deployments. For instance, you could skip protocol to carry out a handbook deploy in a rush, or an attacker with entry to your cluster might deploy pictures skipping your picture scanner.
With an admission controller, you may outline insurance policies to simply accept or block containers primarily based on the pod specification (e.g., implement annotations, detect privileged pods, or utilizing host paths) and the standing of the cluster (e.g. require all ingress hosts to be distinctive inside the cluster).
Safety – Working your containers safely
Adhering to construct time and configuration container safety finest practices proper earlier than runtime nonetheless gained’t make your container 100% protected. New container vulnerabilities are found day by day, so your precise container, fairly protected at the moment, can develop into a possible sufferer of recent disclosed exploits tomorrow.
On this part, we are going to introduce container safety finest practices for together with container vulnerability administration and safety measures in your workload.
9. Defend your assets
Your containers and host may comprise vulnerabilities, and new ones are found regularly. Nevertheless, the hazard shouldn’t be within the host or container vulnerability itself, however moderately the assault vector and exploitability.
For instance, you may defend from a community exploitable vulnerability by impeding connections to the operating container or the weak service. And if the assault vector requires native entry to the host (being logged within the host), you may prohibit the entry to that host.
So, restrict the variety of customers which have entry to your hosts, cloud accounts, and assets, and block pointless community site visitors by utilizing totally different mechanisms:
- VPCs, Safety teams, community guidelines, firewall guidelines, and so forth. in cloud suppliers to limit communication between VMs, VPCs, and the Web.
- Firewalls at hosts ranges to show solely the minimal set of required providers.
- Kubernetes Community Insurance policies for clusters, and extra instruments, like Service Mesh or API Gateways, can add a further safety layer for filtering community requests.
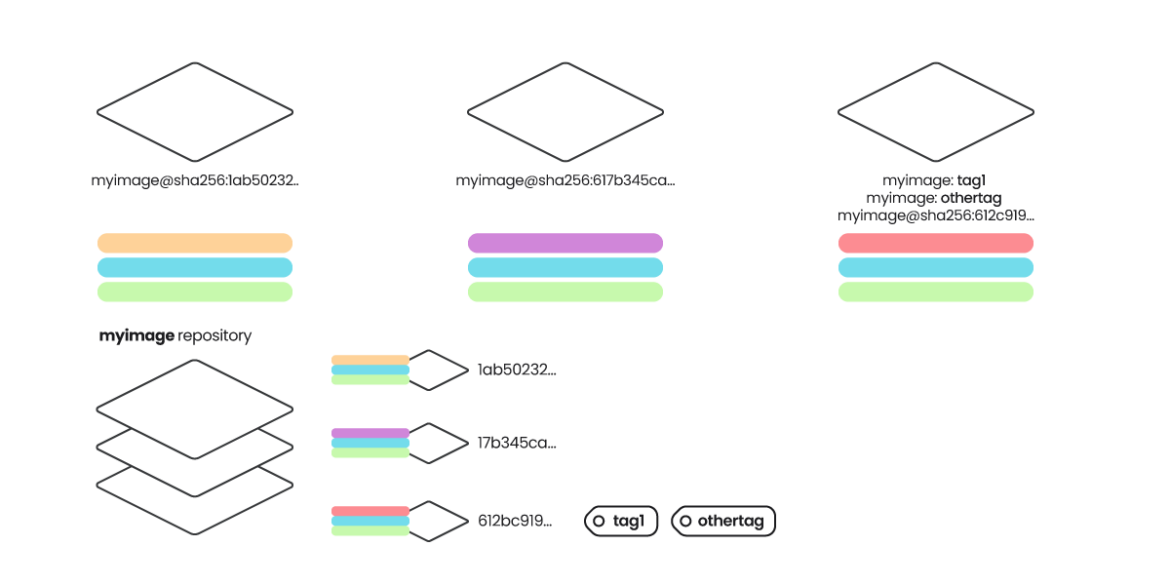
10. Confirm picture signatures
As described in “Image content trust”, picture signatures are a safety mechanism to ensure that the picture has not been tampered. Verifying picture signatures may also stop some assaults with tag mutability, assuring that the tag corresponds to a selected digest that has been signed by the writer. The determine beneath exhibits an instance of this assault.
11. Prohibit container privileges at runtime
The scope or “blast radius” of an exploited vulnerability inside a container largely is dependent upon the privileges of the container, and the extent of isolation from the host and different assets. Runtime configuration can mitigate the influence of current and future vulnerabilities within the following methods:
- Efficient person: Don’t run the container as root. Even higher, use randomized UIDs (like Openshift) that don’t map to actual customers within the host, or use the person namespace function in Docker and in Kubernetes when prepared (not out there at time of publish).
- Prohibit container privileges: Docker and Kubernetes supply methods to drop capabilities and don’t permit privileged containers. Seccomp and AppArmor can add extra restrictions to the vary of actions a container can carry out.
- Add useful resource limits: Keep away from container consuming all of the reminiscence or CPUs and starve different purposes.
- Watch out with shared storage or volumes: Particularly, issues like hostPath, and sharing the filesystem from the host.
- Different choices like hostNetwork, hostPID or hostIPC: Kubernetes will make the container share a namespace with the host, decreasing isolation.
- Outline Pod Safety Insurance policies (PSPs) and Safety Context Constraints (SCCs for Openshift): Set guardrails in your cluster and stop misconfigured containers. PSPs and SCCs are Admission Controllers that may reject pods in case their safety context doesn’t adjust to the outlined insurance policies.
12. Handle container vulnerabilities correctly
Handle and assess your vulnerabilities correctly. Not all vulnerabilities have fixes out there, or might now be capable to be utilized simply.
Nevertheless, not all of them could be simply exploitable, or they might require native and even bodily entry to the hosts to be exploited.
You could have a superb technique, together with:
- Prioritize what must be mounted: It’s best to give attention to host and container vulnerabilities which might be in use at runtime. Addressing vulnerabilities that aren’t in your manufacturing surroundings wastes treasured time that might be spent on those who really put your group in danger, and vulnerabilities with out an energetic exploit are much less dangerous than these which might be being exploited by malicious actors. Solely 1% of vital or excessive severity vulnerabilities have an out there repair, have an energetic exploit, and are in use in manufacturing. Prioritizing these riskiest vulnerabilities will prevent vital time whereas addressing threat that issues.
- Plan making use of fixes as countermeasures to guard your containers and hosts: Create and observe tickets, making vulnerability administration a part of your customary growth workflows.
- Create exceptions for vulnerabilities whenever you conclude that you’re not impacted: It will cut back the noise. Take into account snoozing as an alternative of completely including an exception, so you may reevaluate later.
Your technique ought to translate in insurance policies {that a} container vulnerability scanner can use to set off alerts for detected vulnerabilities based on some standards, and to use prevention and safety at totally different ranges, like:
- Ticketing: Notify builders of detected vulnerabilities to allow them to apply the fixes.
- Picture registry: Stop weak pictures from being pulled in any respect.
- Host / kernel / container: Block operating containers, add extra safety measures or reply by killing, quarantine or shut down hosts or containers for vital points.
It’s also necessary to carry out steady vulnerability scanning and reevaluation to just be sure you get alerts when new vulnerabilities that apply to operating containers are found. Sysdig Safe may help right here, as it is going to reevaluate your scanning insurance policies each time the vulnerability feeds are up to date.
Detection – Alerts for irregular habits
Up to now, we put the give attention to prevention and safety, getting your containers up and operating in the absolute best form, and anticipating potential and recognized assaults. Making use of prevention strategies when constructing, distributing, and operating your container with the right privileges and protections, in addition to guaranteeing the underlying stack, will restrict the vary of motion that an attacker can take. However that doesn’t imply you may simply overlook about operating containers and belief the utilized safety measures. As soon as the safety measures are operating, they are often attacked. We have to detect irregular and sudden habits in our purposes to be able to take corrective motion and stop safety incidents from taking place once more.
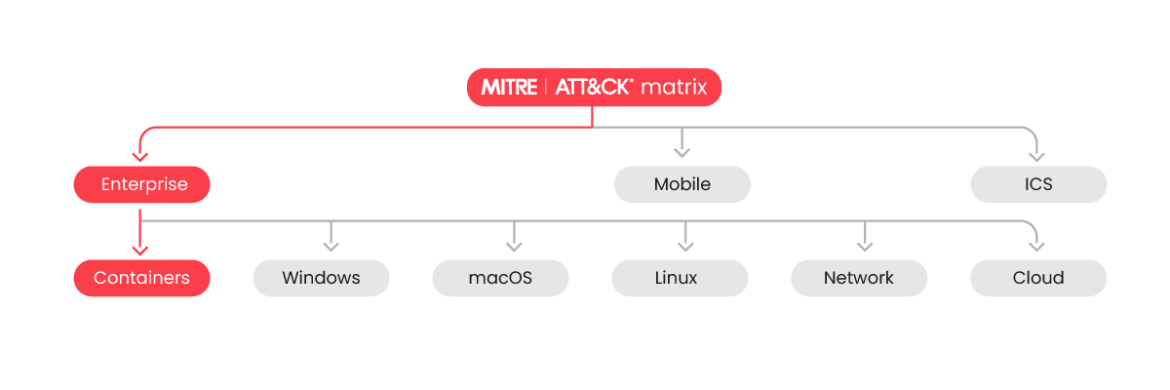
Many alternative assault vectors exist. For instance MITRE ATT&CK gives an intensive checklist of ways and strategies “based on real world observations”, which can be utilized each to use prevention measures and to investigate the exercise to detect irregular behaviors, which might imply an assault or intrusion is being carried out. The MITRE ATT&CK Matrix for Containers covers strategies particularly focused in opposition to container applied sciences.
13. Arrange real-time occasion and log auditing
Threats to container safety may be detected by auditing totally different sources of logs and occasions, and analyzing irregular exercise. Sources of occasions embody:
- Host and Kubernetes logs
- Cloud logs (CloudTrail in AWS, Exercise Audit in GCP, and so forth.)
- System calls in containers
Falco is able to monitoring the executed system calls and producing alerts for suspicious exercise. It features a community-contributed library of guidelines, and you may create your individual by utilizing a easy syntax. Kubernetes audit log can also be supported.
You’ll be able to see good examples of Falco in motion in our Detecting MITRE ATT&CK articles:
Sysdig Safe extends the capabilities of Falco and may also ingest occasions from totally different cloud suppliers.
For example, the next rule would set off an alert each time a brand new ECS Activity is executed within the account:
rule: ECS Activity Run or Began
situation: aws.eventSource="ecs.amazonaws.com" and (aws.eventName="RunTask" or aws.eventName="StartTask") and not aws.errorCode exists
output: A brand new activity has been began in ECS (requesting person=%aws.person, requesting IP=%aws.sourceIP, AWS area=%aws.area, cluster=%jevt.worth[/requestParameters/cluster], activity definition=%aws.ecs.taskDefinition)
supply: aws_cloudtrail
description: Detect a brand new activity is began in ECS.
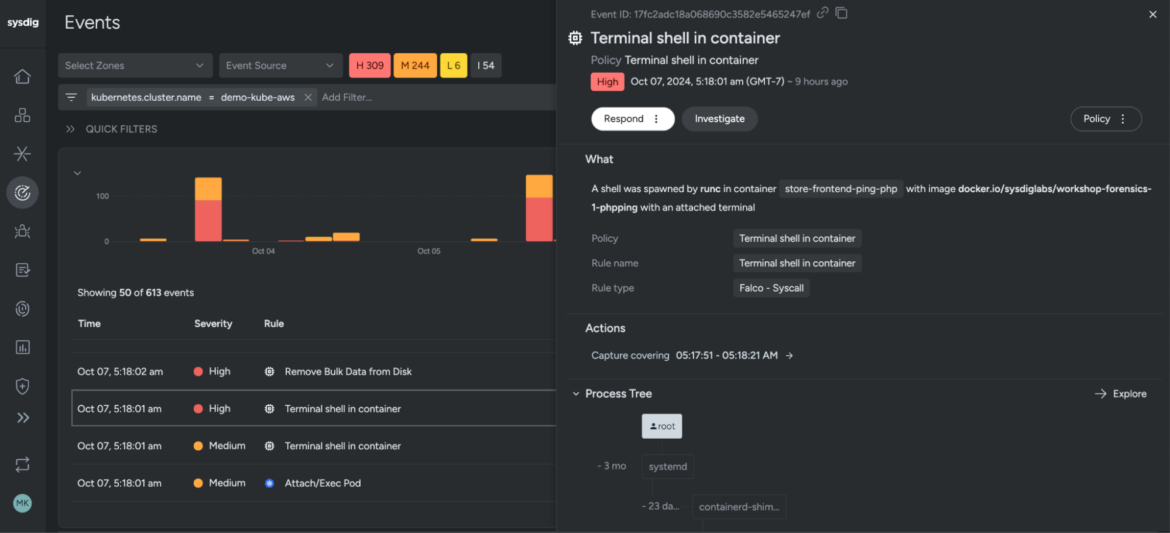
Code language: Perl (perl)Sysdig additionally consists of an ever rising algorithm tagged with the corresponding compliance requirements and controls, and gives a centralized dashboard for exploring all safety occasions in your infrastructure:
Incident response and forensics
When you detect a safety incident is going on in your system, take motion to cease the risk and restrict any extra hurt. As an alternative of simply killing the container or shutting down a bunch, take into account isolating it, pausing it, or taking a snapshot. An excellent forensics evaluation will present many clues and reveal what, when, and the way it occurred. It’s vital to establish:
- If the safety incident was an actual assault or only a element malfunction.
- What precisely occurred, the place did it happen, and are some other doubtlessly impacted elements?
- How will you stop the safety incident from taking place once more?
14. Isolate and examine
When a safety incident is detected, you need to rapidly cease it first to restrict any additional injury.
- Cease and snapshot: When potential, isolate the host or container. Container runtimes’ supply was to “pause” the container (i.e., “docker pause” command) or take a snapshot after which cease it. For hosts, you may take a snapshot on the filesystem stage, then shut it down. For EC2 or VM situations, it’s also possible to take a snapshot of the occasion. Then, proceed to isolation. You’ll be able to copy the snapshot to a protected sandbox surroundings, with out networking, and resume the host or container.
- Discover and forensics: As soon as remoted, you may ideally discover the stay container or host, and examine operating processes. If the host or container shouldn’t be alive, then you may simply give attention to the snapshot of the filesystem. Discover the logs and modified information. There are instruments like, Sysdig Safe captures, that significantly improve forensics capabilities by recording all of the system calls round an occasion and permitting you to discover even after the container or host is lifeless.
- Kill the compromised container and/or host as a final useful resource: Merely destroying the suspicious exercise will stop any extra hurt within the quick time period. However lacking particulars about what occurred will make it unattainable to stop it from taking place once more, and you may find yourself in a by no means ending whack-a-mole state of affairs, repeatedly ready for the following assault to occur simply to kill it once more.
15. Repair misconfigurations
Investigation ought to reveal what made the assault potential. After getting found the assault supply, take safety measures to stop it from taking place once more. The reason for a bunch, container, or software being compromised generally is a dangerous configuration, like extreme permissions, uncovered ports or providers, or an exploited vulnerability.
Within the case of the previous, repair the misconfigurations to maintain it from taking place once more. Within the latter case, it could be potential to stop a vulnerability from being exploited (or at the least restrict its scope) by making adjustments in configurations, like firewalls, utilizing a extra restrictive person, and defending information or directories with extra permissions or ACLs, and so forth.
If the difficulty applies to different belongings in your surroundings, apply the repair in all of them. It’s particularly necessary to take action in those who could be uncovered, like purposes which might be reachable from the web if the exploit may be executed over a distant community connection.
16. Patch vulnerabilities
When potential, repair the vulnerability itself:
- For working system packages (dpkg, rpm, and so forth.): First examine if the distribution vendor is providing an up to date model of the package deal containing a repair. Simply replace the package deal or the container base picture.
- Older distribution variations: The seller will cease offering up to date variations and safety fixes. Maintain your hosts and pictures utilizing supported variations earlier than it’s too late.
- For language packages, like NodeJS, Go, Java, and so forth.: Examine for up to date variations of the dependencies. Seek for minor updates or patch variations that merely repair safety points should you can’t spend extra time planning and testing for breaking adjustments that may occur on greater model updates. However plan forward: outdated variations gained’t be maintained perpetually.
- In case the distribution doesn’t supply a patched model or there isn’t any repair for unmaintained packages: It’s nonetheless potential {that a} repair exists and may be manually utilized or backported. It will require some extra work however it may be crucial for packages which might be vital in your system and when there isn’t any official mounted model but. Examine the vulnerability hyperlinks in databases like NVD, vendor feeds and sources, public data in bug studies, and so forth. If a repair is obtainable, you need to be capable to find it.
If there isn’t any repair out there you could apply on the impacted package deal, it would nonetheless be potential to stop exploiting the vulnerability with configuration or safety measures (e.g., firewalls, isolation, and so forth.). Additionally, it could be advanced and require a deep information of the vulnerability, however you may add extra checks in your individual code. For instance, a vulnerability brought on by an overflow in a JSON processing library that’s utilized by an internet API server might be prevented by including some checks on the HTTP request stage, blocking requests that comprise strings that might doubtlessly result in the overflow.
17. Shut the loop
Sadly, host and container safety shouldn’t be a a technique journey the place you simply apply a set of safety containers good practices as soon as and might overlook perpetually. Software program and infrastructure are evolving on a regular basis, and so complexity will increase and new errors are launched. This results in vulnerabilities and configuration points. New assaults and exploits are found repeatedly.
Begin by together with prevention and safety finest practices. Then, apply safety measures to your assets, principally hosts and workloads, but additionally cloud providers. Proceed monitoring and detecting anomalous habits to take motion, reply, examine and report the found incidents. Forensics proof will shut the loop: repair found vulnerabilities and enhance safety to start out over once more, rebuilding your pictures, updating packages, reconfiguring your assets, and create incident studies to the longer term safety incidents.
Within the center, it’s worthwhile to assess threat and handle vulnerabilities. The variety of inputs to handle in a posh and massive surroundings may be overwhelming, so classify and prioritize to give attention to the best dangers first.

Conclusion
We’ve reviewed how container safety finest practices may be simply utilized to your DevOps workflows. Particularly, bear in mind to:
- Shift left safety, step one is prevention.
- Defend all of your belongings.
- Know all the pieces that occurs in your group, monitoring and detecting points as quick as potential.
- Plan for incident response, as a result of assaults are inevitable.
Do not forget that container safety finest practices don’t simply embody the delivered purposes and container pictures themselves. You additionally want to incorporate the complete element stack used for constructing, distributing, and particularly executing the container.
70 p.c of containers stay for 5 minutes or much less, which makes investigating anomalous habits and breaches extraordinarily difficult.
One of many key factors of cloud-native safety is addressing container safety dangers as quickly as potential. Doing it later within the growth life cycle slows down the tempo of cloud adoption, whereas elevating safety and compliance dangers.
Sysdig Safe will aid you observe these container safety finest practices. Strive it at the moment!