By means of an integration with Sysdig, Checkmarx One customers can now leverage runtime container insights to prioritize vulnerabilities related to working container packages that pose probably the most threat.
Favor to not learn? You possibly can watch a replay of our joint webinar the place we go into extra depth concerning the capabilities and display stay throughout the Checkmarx One and Sysdig Safe merchandise. Watch now ->
Previously a number of years containers have emerged as a good alternative for deploying functions, as a result of their structure they permit builders to miss considerations about dependencies and environments. The whole lot important for working an utility is neatly encapsulated throughout the container, encompassing code, runtime, system instruments, libraries, and dependencies.
In cloud-native environments, containers, when coupled with finest practices and the suitable instruments, provide seamless scalability, guaranteeing optimum utility efficiency and availability. This flexibility not solely caters to peak calls for but in addition frees processing energy for numerous utility elements.
Nonetheless, the problem arises when cloud and utility safety features function in silos, creating fragmentation. This situation leaves AppSec groups with out the correlation or context to grasp which container packages are working, which aren’t and prioritize related dangers successfully.
Think about a situation the place builders, prompted by safety alerts and new work objects, make investments their priceless time in remediation efforts, solely to find that the recognized low-priority vulnerability pertains to an unused container package deal. With out the correlation between vulnerability and runtime information, frustration units in for builders, and will trigger alert fatigue, whereas AppSec groups discover themselves handicapped with no complete view of the crucial vulnerabilities that actually matter.
The problem for AppSec groups is just not merely figuring out vulnerabilities however prioritizing, and remediating those that pose probably the most threat. Establishing a connection between vulnerabilities and the working containers turns into essential, enabling groups to prioritize crucial vulnerabilities and remediating them successfully. This correlation goes past technical nuances; it varieties the spine for fostering belief and collaboration between builders and AppSec groups.
Checkmarx & Sysdig; connecting the dots between pre-production and runtime
Sysdig enhances Checkmarx Container Safety by offering very important runtime insights into container Open-Supply Software program (OSS) working inside cloud-native environments. Whereas Checkmarx excels in securing container pictures by detecting vulnerabilities throughout improvement, Sysdig’s real-time profiling enriches this course of by analyzing containerized functions throughout runtime. Checkmarx crossmatches the checklist of OSS packages used at runtime with recognized susceptible packages, enhancing the identification of safety dangers. By integrating with Sysdig, Checkmarx extends its container safety capabilities past static picture evaluation, guaranteeing a complete method all through the container lifecycle.
The collaboration between Sysdig and Checkmarx streamlines total safety administration by providing steady runtime monitoring and evaluation. Sysdig’s integration enhances Checkmarx’ means to prioritize and tackle vulnerabilities successfully, delivering a unified answer overlaying static evaluation and real-time package deal insights. This partnership strengthens the aptitude to establish and remediate safety threats, fostering a resilient cloud-native atmosphere whereas empowering safety groups and builders with a extra proactive safety posture.
See the combination in motion
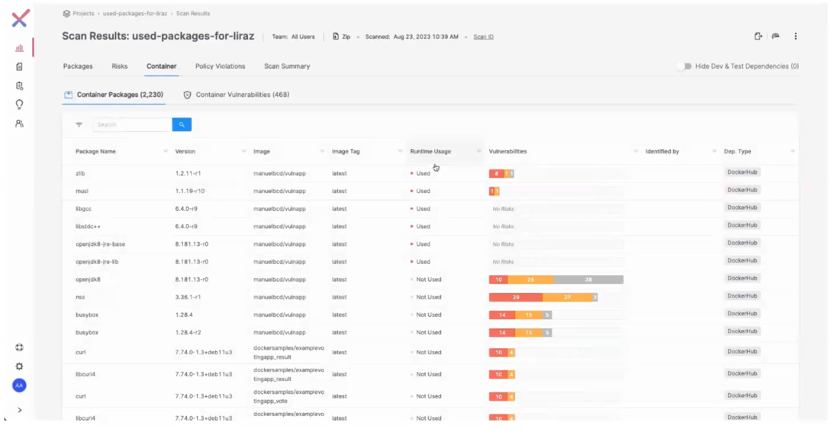
Starting in Checkmarx Container safety, we take a look at the finished scans beneath the “Container” tab.
Runtime insights for container packages can be found on the container degree and on the vulnerability degree.
Throughout the container degree beneath the “Container Packages” tab, container scan outcomes are sorted by default by the packages used at runtime, and by the packages with probably the most vulnerabilities.
On this view, you’ll be able to simply see how simple it’s to shortly soar in and deal with the container packages with probably the most vulnerabilities. However when customers shortly cross reference the “Runtime Usage” column alongside the variety of vulnerabilities discovered, it turns into clear which vulnerabilities must be prioritized.
Customers also can filter this view to solely see the packages used at runtime.
Runtime insights are additionally obtainable on the vulnerability degree. The ‘Container Vulnerabilities’ view shows vulnerabilities related to containers and their criticality, effervescent up these vulnerabilities related to containers present in runtime on the high of the checklist.
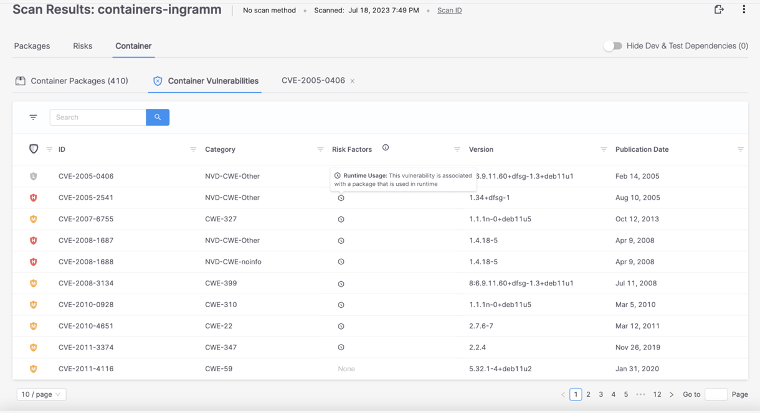
On this view, you’ll see that the “Risk Factor” column highlights whether or not the vulnerability is related to a package deal that’s used at runtime. The outcomes present 9 CVEs which can be related to a package deal utilized in runtime, and the final CVE was not inside a package deal utilized in runtime. The chance issue of whether or not the vulnerability was related to a package deal present in runtime is simply the beginning; further threat components are coming quickly.
When customers need to higher perceive a given vulnerability discovered, they’ll click on into the CVE for extra info, together with the severity, CVSS Rating, and assault vector.
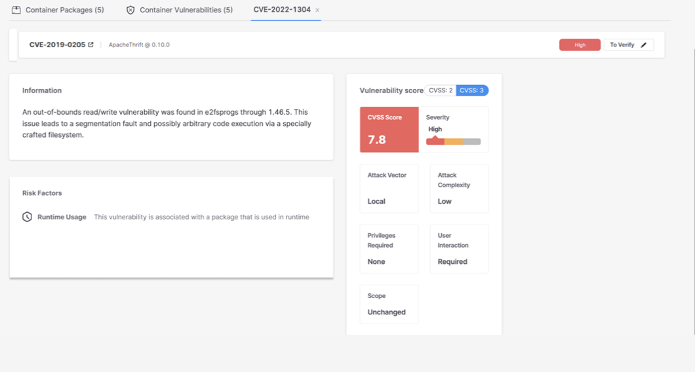
When customers click on right into a given CVE, they’ll now see a brand new “Risk Factors” field, the place they’ll shortly see that the vulnerability is related to a package deal utilized in runtime.
Prioritize what’s working and scale back noise by as much as 90%
Utilizing runtime insights from Sysdig Safe, Checkmarx One or SCA standalone prospects acquire a number of advantages.
- They will successfully prioritize remediation. Correlating pre-production and runtime surfaces probably the most impactful threat, dramatically decreasing the time to detect and prioritize vulnerabilities related to in-use packages first.
- Construct #DevSecTrust. Staff alignment and belief are essential for the success of an enterprise-scale AppSec program. Focusing their improvement group on probably the most crucial vulnerabilities and filtering out the remaining whereas decreasing alert fatigue, builds belief with builders.
- Enhance your safety posture. Runtime insights help organizations in rising their total safety posture, by offering the context your group must prioritize probably the most impactful vulnerabilities.
- Cut back noise. AppSec groups can prioritize vulnerabilities based mostly on in-use context, and remove 90%
Whether or not you’re a CISO (Chief Data Safety Officer) centered in your complete utility safety posture, or a part of an AppSec group centered on figuring out and prioritizing vulnerabilities, or a developer centered on remediation and supporting the enterprise the place it issues most, Checkmarx and Sysdig show you how to higher establish, prioritize, and remediate vulnerability threat.
The mixing is obtainable for customers of each Checkmarx One or Checkmarx SCA standalone and Sysdig Safe. For present prospects of each Checkmarx and Sysdig, otherwise you want to begin gathering runtime insights Request a Demo, to get began.
You may also watch a replay of our joint demonstration https://data.checkmarx.com/tech-partner/sysdig/bridging-code-and-cloud-security