This text is written by Varonis Safety Specialist Tom Barnea.
Take into consideration your most up-to-date safety consciousness coaching regarding phishing assaults. It possible included tips about avoiding clicking on suspicious hyperlinks and workout routines to determine refined character variations, akin to distinguishing between the letter “O” and a zero.
Sadly, the time when even essentially the most novice know-how consumer might simply acknowledge a phishing e mail has ended.
In the previous couple of years, attackers have change into extra refined and inventive. Typo errors and grammar points are now not a priority for non-English-speaking menace actors, because the fast evolution of AI has considerably contributed to the standard of those assaults.
Lately, the Varonis Managed Knowledge Detection and Response (MDDR) forensics crew investigated a intelligent phishing marketing campaign wherein a malicious e mail enabled a menace actor to entry the group.
This weblog submit will reveal the techniques the menace actor used to keep away from detection and share the IoCs found throughout our investigation.
Technical overview
A U.Ok.-based insurance coverage buyer confronted a novel phishing assault. It started when a deletion rule created from a U.S. IP tackle was present in an govt supervisor’s mailbox. This rule, named “a,” completely deleted emails containing a particular key phrase within the e mail tackle.
After the client was alerted to the assault, the Varonis MDDR crew recognized the phishing e mail titled “ML Payment #05323” and its sender. We mapped out all e mail recipients, those that responded, those that reported it, and different communications with the menace actor’s area. This complete spreadsheet was essential for incident containment.
Initially, our solely indicators of compromise have been the recipient’s e mail tackle and the supply IP of the deletion rule creation occasion, which turned out to be a basic Microsoft IP and, subsequently, not very helpful in that case.
Nevertheless, the investigation took an fascinating flip once we found that the phishing e mail appeared to come back from a trusted sender: the CEO of a significant worldwide delivery firm, who had beforehand communicated with our buyer’s staff. The menace actor in all probability compromised the CEO’s e mail account, utilizing it to wreck extra organizations.
The precise key phrase within the deletion rule was a part of the sender’s area. It was designed to erase all emails to or from this area, leaving no hint. The subsequent step was to investigate the unique EML file to grasp the phishing methodology.
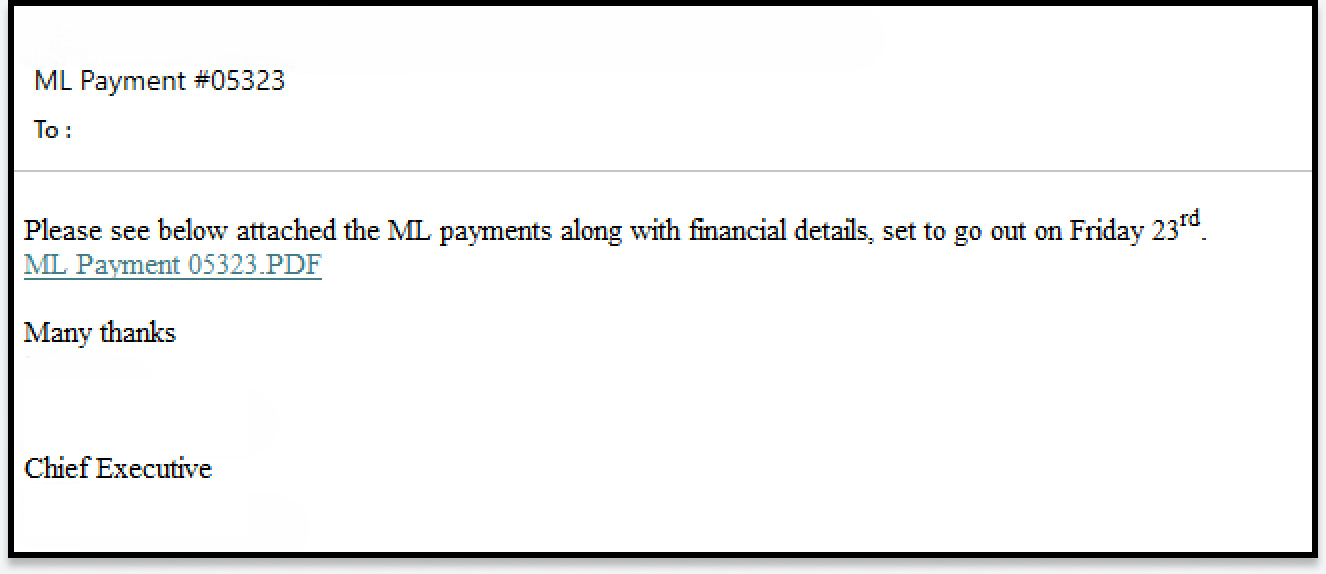
The unique phishing e mail was despatched to 26 recipients within the group. As an alternative of attaching a PDF file, the e-mail included a hyperlink to a PDF hosted on an AWS server.
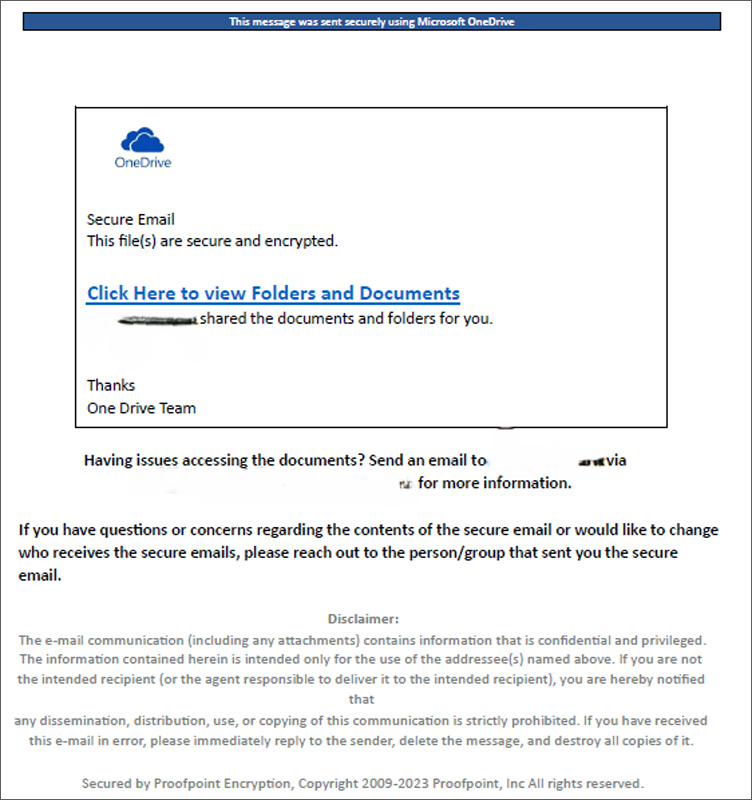
The PDF seemed to be an official OneDrive message, indicating that the sender had shared a file. Whereas a cybersecurity skilled may determine the e-mail as a phishing try, the high-quality message might simply deceive the typical consumer.
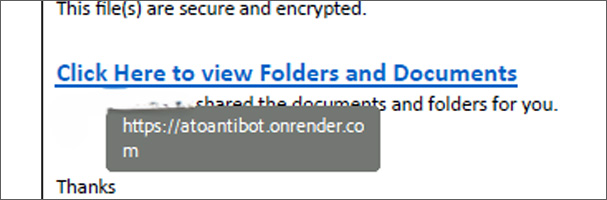
Apparently, the PDF hyperlink contained the phrase “atoantibot.” ATO stands for account takeover. At first look, the hyperlink appeared to guard in opposition to ATO assaults, however the phishing try was finally the precise reverse. This little bit of “hacker humor” will probably be revisited later within the article.
To develop a part of the assault, the menace actor used the general public platform Render, a unified cloud platform that enables builders to construct, deploy, and scale functions and web sites simply. By leveraging a official platform, the attacker ensured their malicious actions blended in seamlessly, making it tough for e mail safety programs to detect the menace.
After clicking to “view the shared document,” the consumer was redirected to “login.siffinance[.]com”, a faux Microsoft authentication web page. At this level, when the sufferer entered his credentials, the attacker achieved his objective. The consumer was then redirected to the official Microsoft Workplace website, making the incident look like a glitch.
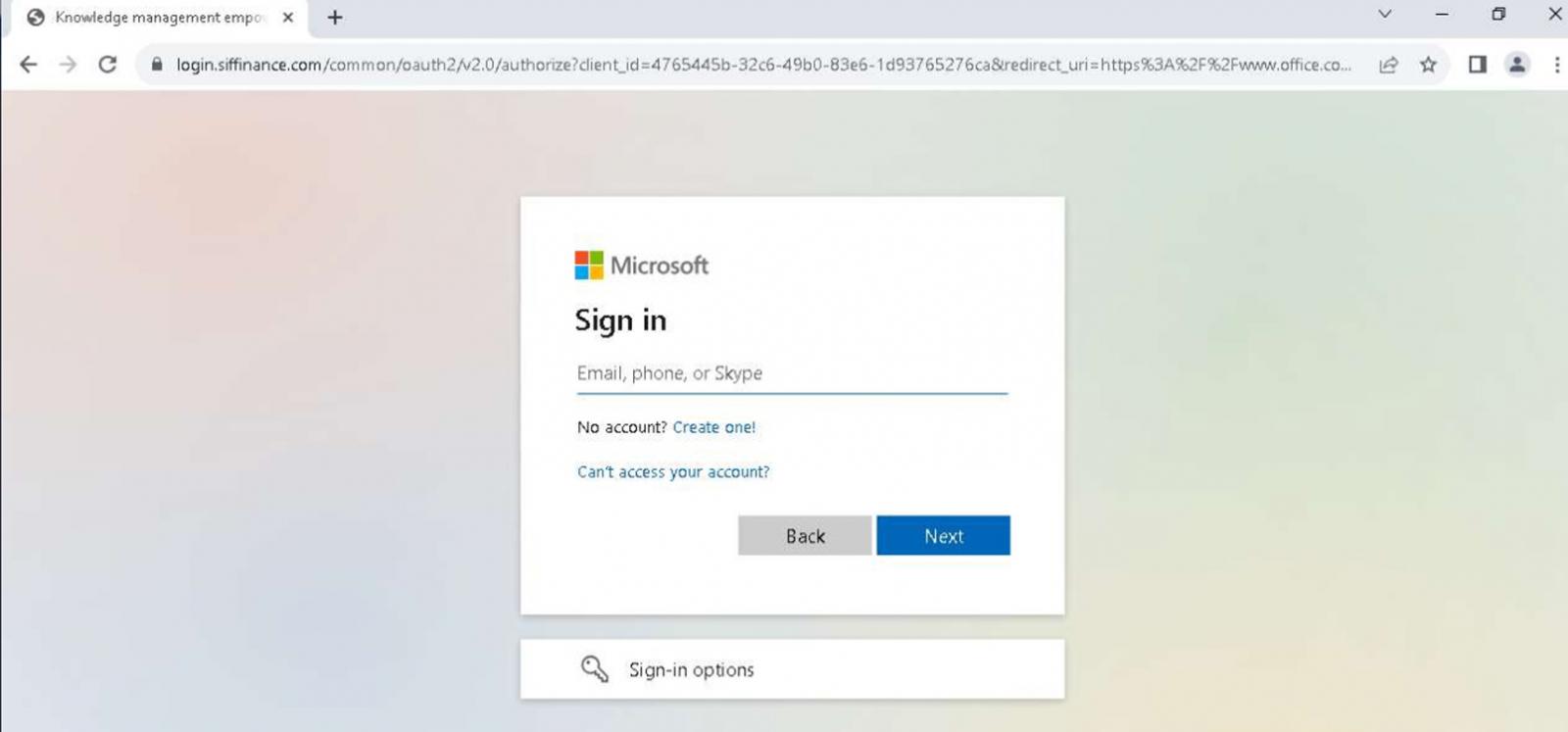
Circling again to the “hacker humor” talked about above, the attacker has disabled (or deactivated) the malicious area, however when you attempt to entry it at this time, it redirects to a well-liked web prank often called Rickrolling.
After coming into credentials on the phishing web page, the sufferer inexplicably responded to the attacker’s e mail. Nevertheless, as a result of the client couldn’t retrieve the despatched e mail, the content material of the message is a thriller. Two minutes later, a profitable login from a U.S. IP tackle (138.199.52[.]3) was detected, regardless of the sufferer being within the U.Ok. This “impossible travel” confirmed the attacker’s entry.
Fortuitously, our buyer’s safety crew acted swiftly, disabling the account, ending the session, and resetting the consumer’s credentials inside half-hour. The one motion the attacker efficiently achieved was making a deletion rule.
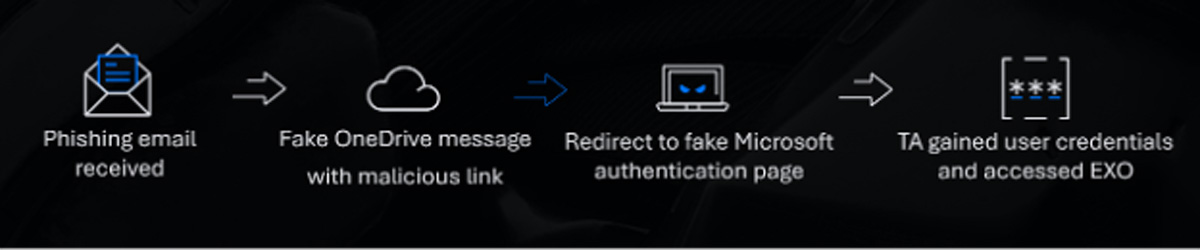
Our investigation revealed that this incident was a part of a broader phishing marketing campaign focusing on a number of corporations. The attacker employed a number of refined techniques that made detection and investigation difficult:
- Overlaying their tracks: After having access to the sufferer’s M365 atmosphere, the primary motion was to create a deletion rule.
- Utilizing a trusted sender tackle: The attacker used a well-known e mail tackle, decreasing suspicion amongst staff.
- Leveraging official platforms: AWS hosted the malicious PDF, and Render was used to construct part of the assault web site. These platforms helped the attacker evade e mail safety software program.
- The Russian nesting dolls methodology: Just like nesting dolls, the attacker embedded a number of hyperlinks inside each other, creating a fancy chain that obscured the ultimate phishing website. Every hyperlink led to a different legitimate-looking web page, utilizing credible platforms to bypass e mail safety filters. This made the phishing e mail seem innocent and tough to detect. By the point the consumer reached the faux authentication web page, they have been weary from navigating a number of websites, making them much less attentive and extra prone to fall for the rip-off.
Suggestions
Consumer security awareness
As is usually the case in cybersecurity, the method begins and ends with customers’ safety consciousness. Whereas it may be difficult for the typical consumer to acknowledge refined phishing emails, there are a number of greatest practices you possibly can educate your customers on to assist them keep away from falling into these traps:
- E mail habits: Encourage customers to open messages or shared information immediately from the related platform as a substitute of clicking on e mail hyperlinks.
- Hyperlink verification: Hover over e mail hyperlinks to verify the URL. Guarantee it logically matches the e-mail content material.
- Credential safety: Confirm the URL of the authentication web page earlier than coming into credentials.
- Phishing recognition: Educate customers on figuring out phishing emails and understanding the related dangers.
Technical measures
Beneath are a couple of technical steps that can enable you shield in opposition to phishing and account take-over assaults:
- Password coverage: Implement complicated passwords and require adjustments each 90 days.
- Multifactor authentication (MFA): Implement MFA for all customers.
- E mail safety: Undertake a strong e mail safety resolution.
- Reporting mechanism: Present a simple method for customers to report suspicious emails.
- Exterior e mail warnings: Add default warnings for emails obtained from exterior sources.
IoCs
138.199.52[.]3
siffinance[.]com
login.siffinance[.]com
www.siffinance[.]com
ywnjb.siffinance[.]com
atoantibot.onrender[.]com
file365-cloud.s3.eu-west-2.amazonaws[.]com
How Varonis may help
Varonis displays real-time e mail and looking actions and consumer and knowledge actions, offering a complete device for cyber forensics investigations. This allows you to rapidly decide the influence and potential dangers of a phishing marketing campaign focusing on your group.
The Varonis MDDR crew provides 24/7/365 knowledge safety experience and incident response, making certain steady assist for nearly any safety concern.
Need to see Varonis in motion? Schedule a demo at this time.
This text initially appeared on the Varonis weblog.
Sponsored and written by Varonis.