The open supply ecosystem, as a result of its widespread adoption, has develop into a main goal for provide chain assaults. Malicious actors usually exploit built-in options of open supply packages to mechanically distribute and execute dangerous code. They notably favor two methods: Computerized, preinstall scripts that execute upon package deal set up, and seemingly harmless packages that import malicious dependencies.
As these techniques have develop into extra recognizable, present safety instruments and vigilant builders have improved at detecting them shortly. Nevertheless, an usually missed but doubtlessly harmful characteristic stays: Entry factors.
This weblog put up explores how attackers can leverage entry factors throughout a number of programming ecosystems with an emphasis on Pypi to trick victims into operating malicious code. Whereas this technique doesn’t enable for instant system compromise like computerized scripts or malicious dependencies, it provides a subtler strategy for affected person attackers to infiltrate techniques, doubtlessly evading customary safety measures.
By understanding this lesser-known vector, we will higher defend towards the evolving panorama of Open supply provide chain assaults.
Key Factors
- Entry factors, a robust characteristic for exposing package deal performance, are weak to exploitation throughout varied ecosystems together with PyPI (Python), npm (JavaScript), Ruby Gems, NuGet (.NET), Dart Pub, and Rust Crates.
- Attackers can leverage these entry factors to execute malicious code when particular instructions are run, posing a widespread danger within the open-source panorama.
- Assault strategies embody command-jacking—impersonating widespread third-party instruments and system instructions—and focusing on varied levels of the event course of via malicious plugins and extensions. Every strategy carries various ranges of potential success and detection danger.
- Entry level assaults, whereas requiring consumer interplay, supply attackers a extra stealthy and chronic technique of compromising techniques, doubtlessly bypassing conventional safety checks.
- This assault vector poses dangers to each particular person builders and enterprises, highlighting the necessity for extra complete Python package deal safety measures.
Understanding Python Entry Factors
Entry factors are a robust characteristic of the packaging system that permits builders to show particular performance as a cli command with out requiring customers to know the precise import path or construction of the package deal.
Entry factors serve a number of functions which embody:
- Creating command-line scripts that customers can run after putting in a package deal.
- Defining plugin techniques the place third-party packages can lengthen the performance of a core package deal.
The most well-liked form of entry level is console_scripts, which factors to a perform that you simply wish to be made out there as a command-line instrument to whoever installs your package deal.
Whereas primarily designed to reinforce modularity and plugin techniques, entry factors can, if misused, develop into a vector for malicious actors to embed and execute dangerous code. To grasp how attackers can leverage Python entry factors of their favor, let’s first perceive how entry factors have been initially meant to work.
How Entry Factors are Outlined in Package deal Metadata
The placement and format of entry level definitions can differ relying on the package deal format (wheel or supply distribution).
Supply Distributions (.tar.gz)
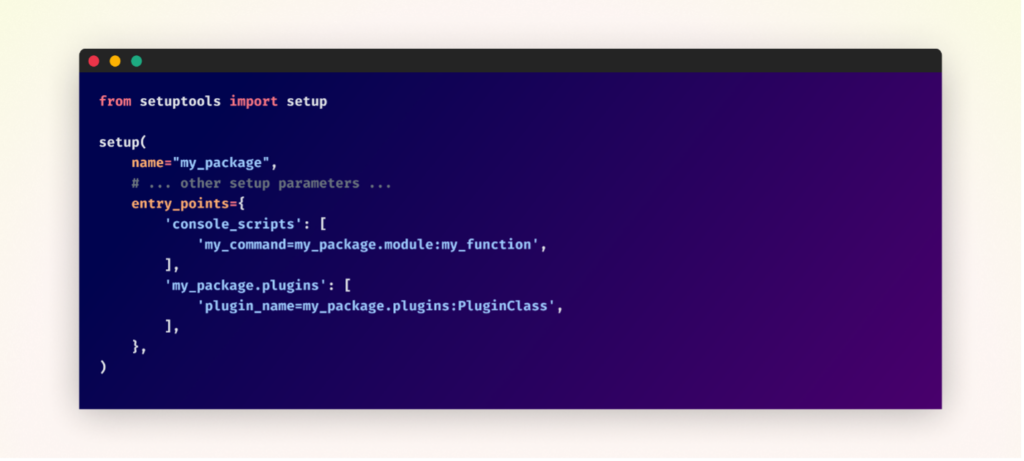
For supply distributions, entry factors are sometimes outlined in a package deal’s setup configuration. This may be in setup.py, setup.cfg for conventional setups, or pyproject.toml for extra fashionable packaging approaches.
Right here’s an instance of how entry factors may be outlined in setup.py:
Wheel Recordsdata (.whl)
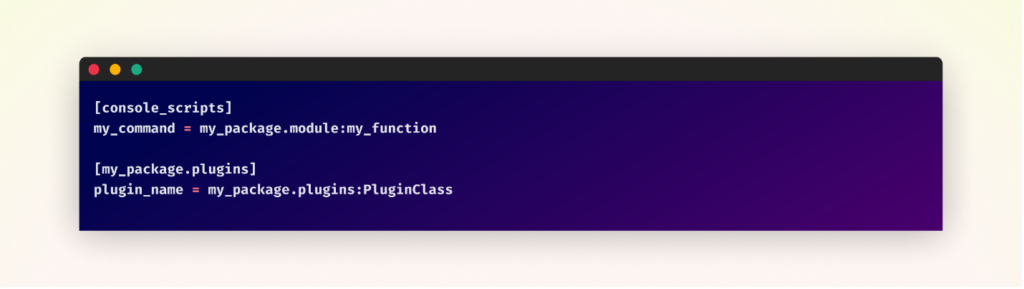
In a wheel file, which is a constructed package deal format, entry factors are outlined within the entry_points.txt file throughout the .dist-info listing.
Right here’s how the entry_points.txt file would possibly search for the above instance:
The syntax for entry factors follows this sample:

- title: The title of the entry level (e.g., the command title for console scripts)
- package deal.module: The Python module path
- object: The article (perform, class, and so forth.) throughout the module for use
Within the above examples, my_command is a console script that might be created throughout set up. Anytime after the package deal set up, when a consumer varieties my_command of their terminal, it’ll execute the my_function from mypackage.module.
The plugin_name is a customized entry level that may very well be utilized by my_package to find plugins. It factors to PluginClass in my_package.plugins.
When a package deal is put in, these entry factors are recorded within the package deal’s metadata. Different packages or instruments can then question this metadata to find and use the outlined entry factors.
If an attacker can manipulate a official package deal’s metadata or persuade a consumer to put in a malicious package deal, they’ll doubtlessly execute arbitrary code on the consumer’s system at any time when the outlined command or plugin is invoked. Within the following part, I’ll present a number of strategies an attacker might use to trick somebody into executing their malicious code via entry factors.
Understanding CLI Instructions in Working Techniques
Command-line interface (CLI) instructions are the first means by which customers work together with an working system via a text-based interface. These instructions are interpreted and executed by the shell, which acts as an middleman between the consumer and the working system.
When a consumer enters a command, the shell follows a selected decision mechanism to find and execute the corresponding program. The precise order can differ barely between totally different shells. Nevertheless, the method sometimes begins by checking so as the directories listed within the PATH atmosphere variable and runs the primary matching executable it finds. Customers can view their present PATH by coming into the command “echo $PATH” of their terminal (the precise command will differ between working techniques), which shows the listing of directories the shell searches for executables.
This decision course of ensures that when a consumer varieties a command, the suitable motion is taken. Understanding this course of is essential when contemplating how Python entry factors, which might create new CLI instructions, would possibly work together with or doubtlessly intrude with present system instructions.
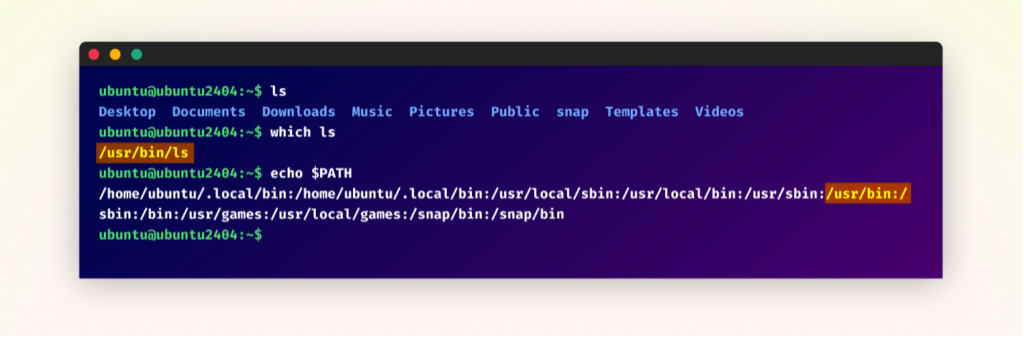
Terminal output on an Ubuntu system displaying the ‘ls’ command execution, its PATH location utilizing ‘which ls’, and the system’s PATH atmosphere variable, displaying the ‘ls’ PATH precedence.
How Attackers Can Abuse Entry Factors to Execute Malicious Code
Malicious actors can exploit Python entry factors in a number of methods to trick customers into executing dangerous code. We’ll discover a variety of techniques, together with Command-Jacking, Malicious Plugins and Malicious Extensions.
Command-Jacking
Impersonating Widespread Third-Get together Instructions
Malicious packages can use entry factors to masquerade as widely-used third-party instruments. This tactic is especially efficient towards builders who continuously use these instruments of their workflows.
As an illustration, an attacker would possibly create a package deal with a malicious ‘aws’ entry level. When unsuspecting builders who recurrently use AWS companies set up this package deal and later execute the aws command, the pretend ‘aws’ command might exfiltrate their AWS entry keys and secrets and techniques. This assault may very well be devastating in CI/CD environments, the place AWS credentials are sometimes saved for automated deployments—doubtlessly giving the attacker entry to whole cloud infrastructures.
One other instance may very well be a malicious package deal impersonating the ‘docker’ command, focusing on builders working with containerized purposes. The pretend ‘docker’ command would possibly secretly ship photographs or container specs to the attacker’s server throughout builds or deployments. In a microservices structure, this might expose delicate service configurations and even result in the exfiltration of proprietary container photographs.
Different widespread third-party instructions that may very well be potential targets for impersonation embody however not restricted to:
- npm (Node.js package deal supervisor)
- pip (Python package deal installer)
- git (Model management system)
- kubectl (Kubernetes command-line instrument)
- terraform (Infrastructure as Code instrument)
- gcloud (Google Cloud command-line interface)
- heroku (Heroku command-line interface)
- dotnet (Command-line interface for .NET Core)
Every of those instructions is broadly utilized in varied growth environments, making them enticing targets for attackers trying to maximize the affect of their malicious packages.
Impersonating System Instructions
Through the use of widespread system command names as entry factors, attackers can impersonate elementary system utilities. Instructions like ‘touch,’ ‘curl,’ ‘cd’, ‘ls’, and ‘mkdir’ simply to call just a few, may very well be hijacked, resulting in extreme safety breaches when customers try to make use of these elementary instruments.
Whereas this technique doubtlessly gives the best probabilities of the sufferer by chance executing the malicious code, it additionally carries the best danger of failure for the attacker. The success of this strategy primarily depends upon the PATH order. If the listing containing the malicious entry factors seems earlier within the PATH than the system directories, the malicious command might be executed as an alternative of the system command. That is extra more likely to happen in growth environments the place native package deal directories are prioritized.
One other factor to remember is that globally put in packages (requiring root/admin privileges) would possibly override system instructions for all customers, whereas user-installed packages would solely have an effect on that particular consumer’s atmosphere.
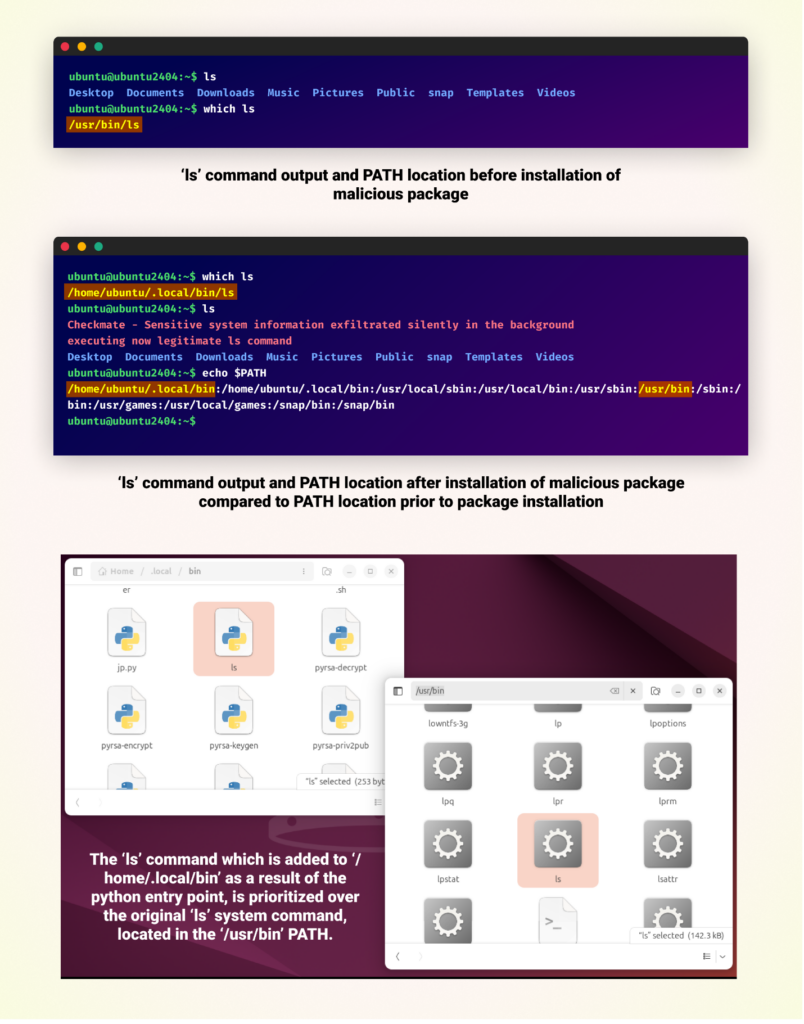
Comparability of Ubuntu terminal outputs earlier than and after set up of a malicious package deal. An ‘ls’ command is added to the PATH /residence/ubuntu/.native/bin/ls, which takes precedence over the PATH of the official ls command.
Enhancing Assaults with Command Wrapping
In every of those Command-Jacking techniques, whereas it’s easier for an attacker to merely override CLI instructions, the probabilities of remaining undetected are fairly low. The second victims can’t execute a command, they’ll doubtless develop into suspicious instantly. Nevertheless, these assaults may be made way more efficient and stealthy via a way known as “command wrapping.” As a substitute of merely changing a command, wrapping includes creating an entry level that acts as a wrapper across the authentic command. Right here’s the way it works:
- The malicious entry level is triggered when the consumer calls the command (whether or not it’s an impersonated third-party instrument or an try to impersonate a system command).
- Along with silently executing the attacker’s malicious code, it calls the unique, official command with all of the consumer’s arguments.
- Lastly, it returns the output and exit code of the official command to the consumer.
This technique of command wrapping is especially harmful because it executes malicious code with out the consumer’s data whereas sustaining the looks of regular operation. Because the official command nonetheless runs and its output and habits are preserved, there’s no instant signal of compromise, making the assault extraordinarily troublesome to detect via regular use. This stealthy strategy permits attackers to keep up long-term entry and doubtlessly exfiltrate delicate info with out elevating suspicion.
Nevertheless, implementing command wrapping requires further analysis by the attacker. They should perceive the right paths for the focused instructions on totally different working techniques and account for potential errors of their code. This complexity will increase with the range of techniques the assault targets.
Another strategy, relying on the command being hijacked, is for the malicious package deal to not solely carry out its covert operations but in addition replicate some or all the performance of the unique command. As a substitute of calling the true command, the wrapper simulates its habits. This technique might additional lower suspicion, particularly for easier instructions, nevertheless it requires extra effort from the attacker to precisely mimic the unique command’s habits throughout varied eventualities.
The success of those assaults finally depends upon the malicious package deal being put in and its scripts listing being prioritized within the system’s PATH.
Malicious Plugins & Extensions
One other highly effective method for abusing entry factors is thru the creation of malicious plugins for widespread Python instruments and frameworks. This strategy may be notably harmful because it targets the event and testing course of itself.
Manipulating pytest
For example, let’s contemplate how an attacker would possibly goal pytest, a widely-used testing framework within the Python ecosystem. By making a malicious pytest plugin, an attacker might doubtlessly compromise the integrity of all the testing course of.
Right here’s how such an assault might work:
- The attacker creates a plugin that makes use of pytest’s entry level system to inject malicious code.
- This plugin is distributed as a seemingly useful testing utility.
- As soon as put in, the plugin can manipulate varied facets of the testing course of corresponding to assertion dealing with.
The malicious plugin might then stealthily run malicious code within the background throughout testing. The malicious plugin might additionally override pytest’s assertion comparability, inflicting, for instance, all equality checks to go no matter their precise values, resulting in false positives in check outcomes, permitting buggy or weak code to go high quality checks unnoticed.
Within the following video demonstration, we showcase how such a malicious plugin can goal pytest’s assertion dealing with, permitting an attacker to control check outcomes with out alerting the builders. On this instance, a developer was trying a easy check scan of a primary calculator package deal.
Manipulating Flake8
Attackers may goal widespread growth instruments, manipulating them to run malicious extensions. Flake8, a widely-used linting instrument within the Python ecosystem, is one such instance. Since Flake8 makes use of entry factors to find and cargo extensions, it turns into a possible goal for malicious actors.
An attacker would possibly exploit Flake8 by making a malicious extension disguised as useful linting guidelines. This extension could be outlined as an entry level within the package deal’s setup configuration. For instance, the setup file would possibly specify an entry level named ‘MCH’, pointing to a malicious checker class throughout the package deal.
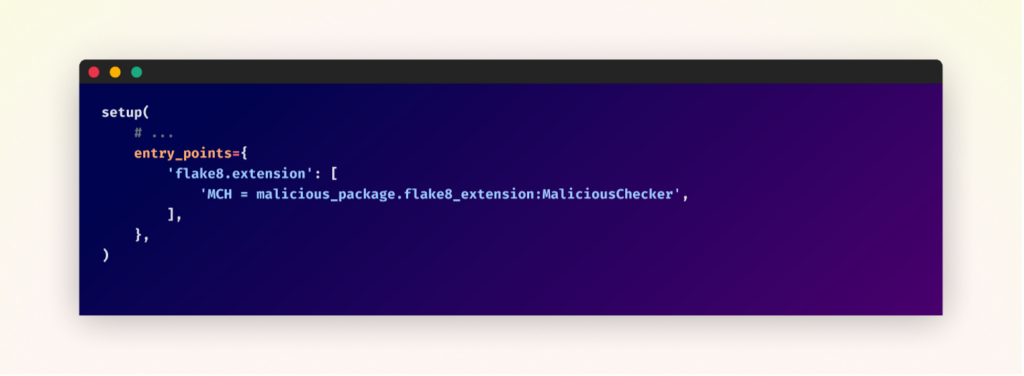
The malicious checker’s implementation might embody performance to carry out dangerous actions on the sufferer’s system, inject malicious “fixes” into the code, or manipulate linting outcomes to cover or create points. When a consumer runs Flake8 on their codebase, this malicious extension would activate, permitting the attacker to execute their dangerous code.
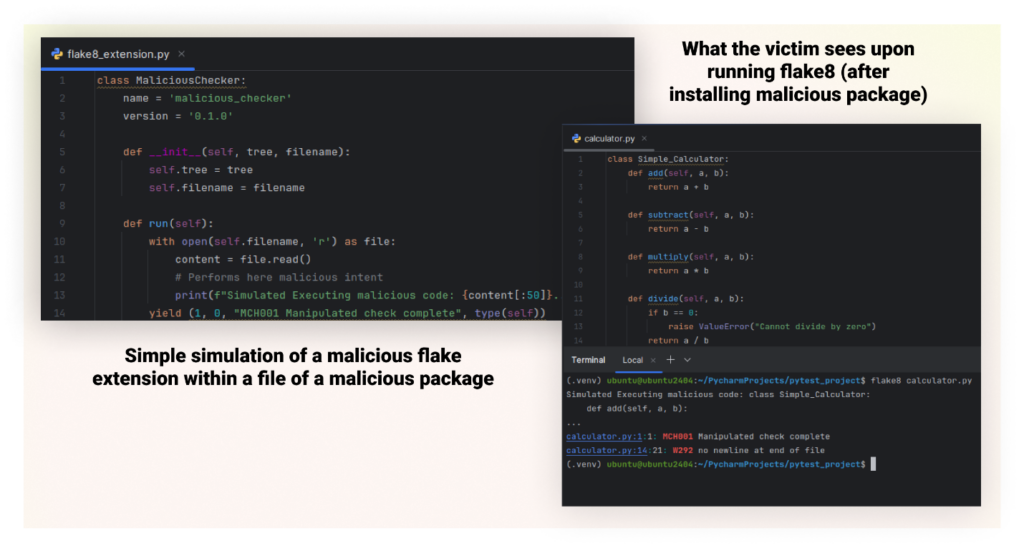
This assault is especially harmful as a result of linting instruments usually run on whole codebases, giving the attacker broad entry to the supply code. Furthermore, the assault may be perpetrated via seemingly useful linting guidelines, making it much less more likely to elevate suspicion. It might function half of a bigger provide chain assault to assemble intelligence or introduce vulnerabilities into the goal’s codebase.
Working round .whl File Limitations
Python wheels (.whl information) have develop into more and more prevalent as a result of their efficiency advantages in package deal set up. Nevertheless, they current a novel problem for attackers
Whereas each .tar.gz and .whl information might comprise a setup.py file, .whl information don’t execute setup.py throughout set up. This attribute has historically made it harder for attackers to attain arbitrary code execution throughout the set up course of when utilizing .whl information.
Nevertheless, the entry level assault technique we’ve mentioned gives a workaround for this limitation. By manipulating entry factors, attackers can guarantee their code is executed when particular instructions are run, even when the package deal is distributed as a .whl file. That is notably vital as a result of when builders construct a Python package deal utilizing instructions like “pip -m build”, newer pip variations mechanically create each .tar.gz and .whl information. Moreover, pip prioritizes delivering the .whl file to customers throughout set up
This shift in package deal format and set up habits presents a brand new alternative for attackers. Many safety instruments deal with analyzing execution of preinstall scripts throughout set up, that are sometimes related to .tar.gz information. Because of this, they could miss malicious code in packages distributed as .whl information, particularly when the malicious habits is triggered via entry factors moderately than instant execution.
Entry Factors in Different Ecosystems
Whereas this weblog primarily focuses on Python, the exploitation of entry factors for malicious functions extends past the Python ecosystem. By way of our analysis, we’ve got confirmed that any such assault vector exists in a number of different main ecosystems, together with:
npm (JavaScript), Ruby Gems, NuGet (.NET), Dart Pub, and Rust Crates, although the vulnerability might not be restricted to those alone.
Understanding how entry factors perform throughout varied programming languages and package deal managers is essential for greedy the widespread nature of this potential safety danger and for creating complete defensive methods.
Conclusion
Entry factors, whereas a robust and helpful characteristic for official package deal growth, will also be manipulated to ship malicious code throughout a number of programming ecosystems
Attackers might exploit this mechanism via varied strategies, together with Command-Jacking and the creation of malicious plugins and extensions for widespread growth instruments.
Transferring ahead, it’s essential to develop complete safety measures that account for entry level exploitation. By understanding and addressing these dangers, we will work in direction of a safer Python packaging atmosphere, safeguarding each particular person builders and enterprise techniques towards subtle provide chain assaults.
As a part of the Checkmarx Provide Chain Safety answer, our analysis crew constantly displays suspicious actions within the open-source software program ecosystem. We monitor and flag “signals” which will point out foul play, together with suspicious entry factors, and promptly alert our clients to assist shield them from potential threats.