CocoaPods is THE dependency supervisor for iOS and Mac initiatives. It helps software program builders simply add pre-made items of code (known as “libraries” or “dependencies”) to their iOS or Mac initiatives. These code libraries will help builders add further options or performance to their apps with out having to write down all the code themselves. Consider it like including pre-made Lego items to a Lego creation to make it higher or extra fascinating.
Subdomain Hijacking
Subdomain hijacking is a sort of cyber assault the place an attacker takes management of a subdomain of a official area, and makes use of it to host malicious content material or launch additional assaults.
In a subdomain hijacking assault, the attacker can discover forgotten settings on free internet hosting web sites akin to GitHub Pages, which aren’t mapped anymore. The weak validation grants attackers permission to make use of these subdomains.
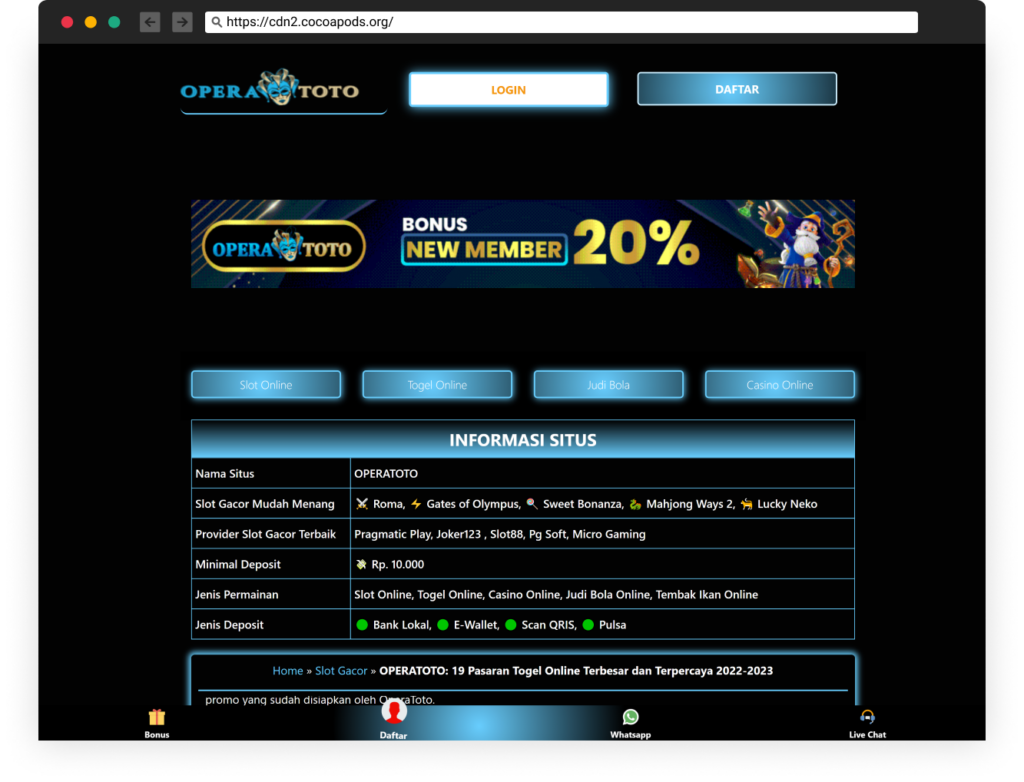
CocoaPods On line casino
Man Nachshon, a superb safety researcher in my workforce, discovered the subdomain cdn2.cocoapods.org was used years in the past and deserted. Nonetheless, the DNS data nonetheless pointed to the GitHub Pages internet hosting service, and attackers hijacked it to host a fishy on line casino web site.
Whereas we have been investigating this, the subdomain bought freed on GitHub Pages (in all probability on account of an replace/mistake of the attackers).
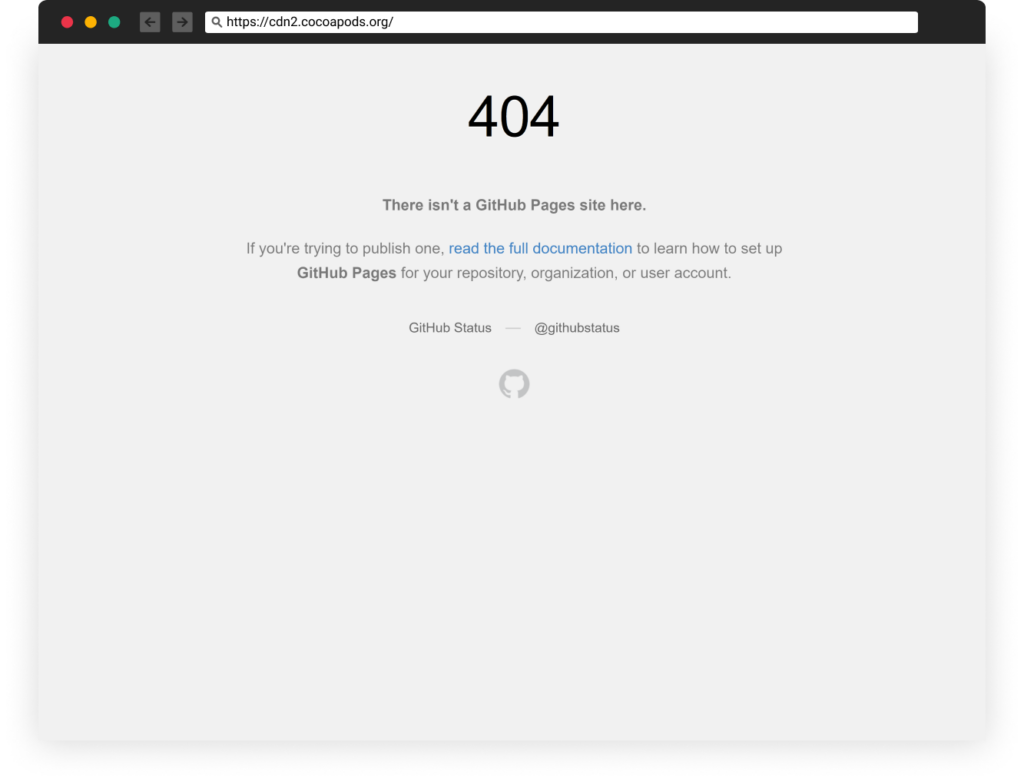
We jumped on the chance and created a easy repository to carry this subdomain and stop one other takeover by these on line casino attackers.
This works so long as the subdomain is unoccupied by one other GitHub Pages undertaking and is tremendous easy to arrange -> settings, allow GitHub Pages, sort the subdomain “cdn2.cocoapods.org”:
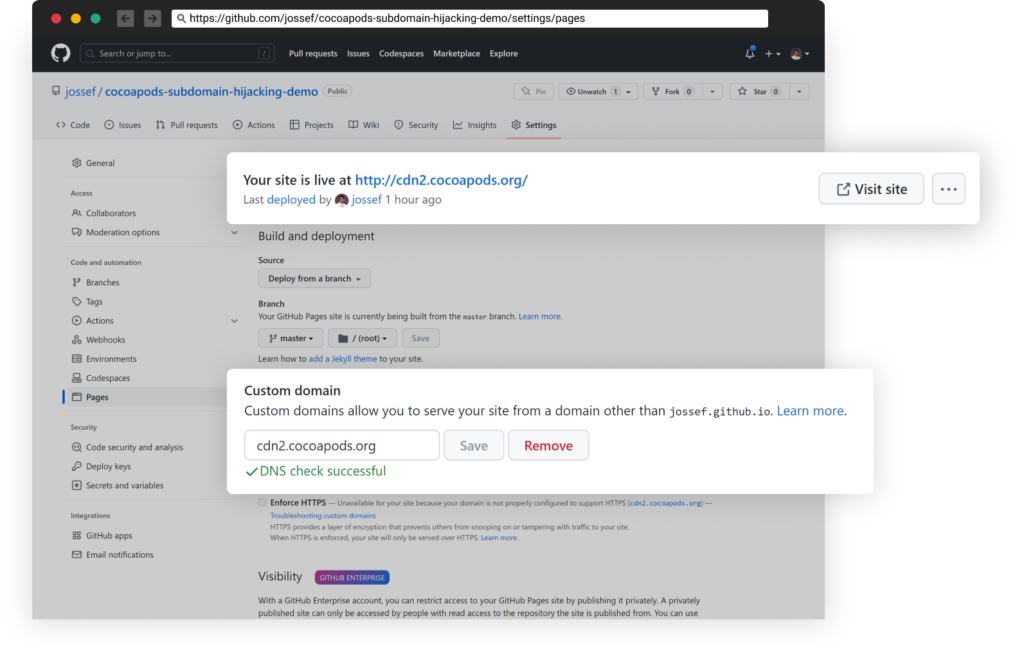
Watch this brief demo video to see it in motion:
Influence
Typically talking, the influence of hijacking a subdomain of a recognized web site can trick customers into considering the content material they’re seeing is official and created by the recognized model.
Moreover, organizations normally enable community visitors to such dev-related official assets from delicate networks to help the engineering course of.
Final 12 months, we noticed instances wherein attackers hosted malicious exe file on GitHub and one other instance the place an picture hosted on imgur.com contained malicious python code. Therefore, it’s fairly clear what’s the potential of hijacking a subdomain of a well-liked and bonafide model.
Conclusion
I disclosed the findings to CocoaPods in this GitHub difficulty, and large respect for the quick response and eradicating the subdomain file.
It’s ridiculous how straightforward it’s to take over an deserted subdomain. This made me marvel – ought to this be that straightforward? Ought to GitHub implement 2-way validation when linking a site to a GitHub Pages undertaking? Like validating the precise repository URL? IMHO – sure.
See this case as a warning when you’ve got created subdomain data for side-projects that over time grew to become out of date, like cdn2.cocoapods.org. I counsel eradicating them, as somebody would possibly hijack your subdomain.