The adoption of Cloud Native Software Safety Platforms (CNAPPs) has surged, reflecting a rising recognition of the necessity for complete safety throughout cloud environments. In accordance with business studies, the worldwide CNAPP market is projected to develop at a CAGR of over 25% from 2023 to 2028 – and 40% of enterprises have already got one. This spike is fueled by the rising complexity of cloud infrastructures and the ever-evolving menace panorama.
CNAPP Brings a New Degree of Visibility
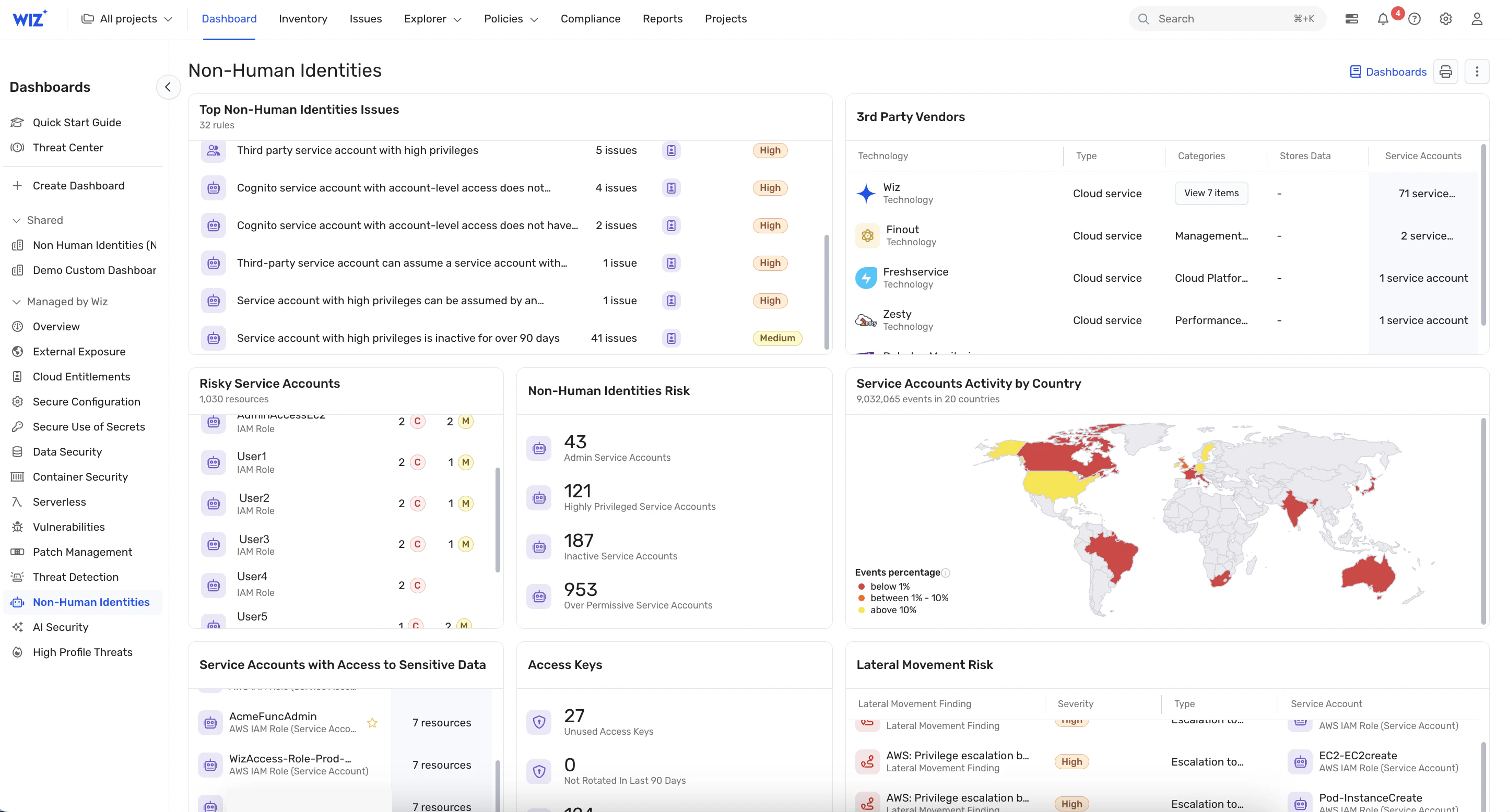
CNAPPs have confirmed to be highly effective instruments for figuring out a big selection of cloud-specific safety gaps, and are reporting a whole lot of findings within the realm of cloud id and permissions. These platforms excel at revealing over-permissioned identities, misconfigured entry insurance policies, and potential factors of exploitation. Nevertheless, whereas CNAPPs present precious visibility, they typically fall quick in the case of remediation, requiring findings to be handled separately, or not offering remediation paths in any respect. And whenever you issue within the sheer quantity of alerts (I don’t have to go over the statistics about “alert fatigue” from SIEM / XDR / CNAPP / insert-acronym-here), you’ll be able to think about how giant this backlog of unresolved points is.
Addressing id and permissions points at scale is a major problem. Many CNAPP options supply detailed insights, prioritize the problems and a few even supply automated remediation bots, however all of them lack the capabilities to resolve these points effectively throughout giant cloud environments. It’s not for lack of talent or effort: it’s a problem of quantity and coordination.
CNAPPs are discovering hundreds of permissions points, significantly in machine identities. Most are struggling to scrub them up. (Picture courtesy Wiz weblog)
Lots of Findings, A Lack of Motion
Right here’s what I imply: take one thing so simple as an unused id. CNAPP ought to be capable to discover this simply. As soon as discovered, are you able to safely delete it? Are you certain it’s not there for a purpose? Who owns the id? What workload will (finally) break if it’s eliminated? Answering these questions requires discovering the precise particular person – as in, who owns that account / OU / a part of the cloud. If it’s a machine id (it normally is), it’s not overtly tied to a given particular person or workforce. Now you’re on a hunt for an individual, including the complication of human coordination, scheduling, and communication to a problem that needs to be between you and the cloud console. Because the common cloud has 11k identities, and 61% have been unused for 90 days, multiply this course of by oh, 6,000 or so. Good luck getting these cleaned up on this decade.
Together with unused identities, overpermissioned identities, lateral motion dangers, and privilege escalation situations make for a bundle of enjoyable that cloud groups are lastly seeing, however not appearing on. They merely can’t: CNAPP shines a lightweight on the massive set of issues of the trendy cloud, however it doesn’t offer you a machete to chop by way of the jungle. And for those who’re not within the Dev org, you’re afraid of breaking one thing that’ll decelerate code deployment. We’ve obtained bulk visibility, however not bulk motion. So that you’re selection is certainly one of two choices: One, tackle the Sisyphean process of manually remediating a whole bunch, if not hundreds, of permissions and identity-related dangers; or Two, settle for the danger and hope you’re reaching actual threat discount with the 1% of remediations you will get to. Choice one means your intel is old-fashioned even earlier than you end, Choice two is playing your job on a hunch that which unused principals and permissions are extra enticing vessels for lateral motion.

Enabling the ‘Bulk Fix’ within the Identification World
Sonrai Safety’s Cloud Permissions Firewall is the important thing to bridging the hole left by CNAPP’s intense concentrate on figuring out points. As an alternative of simply highlighting issues, this answer empowers organizations to take motion, enabling bulk resolutions that deal with the vast majority of id and permissions points all of sudden. What units it aside is its ‘default deny’ method, which ensures a least-privilege state is constantly maintained, whilst your cloud atmosphere grows and evolves. This functionality is crucial for maintaining your cloud operations safe and compliant, significantly as your group scales.
The Sonrai Cloud Permissions Firewall takes automated “bulk fixes” to the subsequent stage by combining detailed permissions evaluation with a laser concentrate on essentially the most important dangers. With centralized management over permissions and entry, it allows swift, complete actions to eradicate unused delicate permissions, identities, providers, and areas throughout your cloud atmosphere. What makes this method so efficient is its capacity to revive permissions on demand inside seconds, guaranteeing that your improvement groups keep productive with out compromising safety or disrupting operations.
Take into account the instance of imposing least privilege for each human and machine identities. A typical least privilege software scans audit logs, compares the permissions really used with these assigned to a principal, and identifies which privileges might be safely eliminated as “unused.” Sounds easy, proper? However challenges come up: Which unused privileges are literally important? Who’s accountable, and who must approve the brand new coverage? What might change or break if we implement it? Does this permission even pose an actual safety threat? And what if these permissions are wanted later? The Cloud Permissions Firewall addresses these considerations by:
- Robotically figuring out possession: Shortly determines who’s liable for every permission.
- Preserving underlying permissions: Retains the unique permissions and credential grants intact.
- Specializing in dangerous permissions: Controls solely the unused delicate permissions that could possibly be exploited in an assault.
- Implementing centralized restrictions: Makes use of a centralized coverage to limit entry to unused permissions with out altering current grants. Restrictions are utilized to:
- Unused delicate permissions
- Unused identities
- Unused providers
- Unused areas
- Restoring permissions as wanted: Grants entry again to permissions when essential, with approval, guaranteeing seamless operations.
The Cloud Permissions Firewall automates your complete course of, from assigning possession to identities and analyzing logs to establish unused permissions, to writing centralized insurance policies and producing the mandatory infrastructure as code templates. It even handles exceptions and updates the related insurance policies mechanically. This centralized management and automation take the burden off the event groups, inserting it within the arms of cloud safety operations groups—with out the time-consuming trouble of deploying particular person insurance policies.
Working along with your CNAPP
The Cloud Permissions Firewall enhances any CNAPP answer to deal with id points, decreasing alerts, alarms, and general threat in your cloud atmosphere. Clients have reported that it cuts the time wanted to resolve id points by 97%, making the aim of reaching least privilege in your cloud a actuality. As an alternative of endlessly hacking away at a giant stack of issues, Sonrai resets the paradigm: delicate permissions and providers use is regulated like community site visitors was. Specific grants govern all principal’s permissions – however current site visitors patterns are allowed to stream as they had been, maintaining productiveness up.
Like all safety innovation, cloud permissions threat follows the identical sample: step one is figuring out it, the second is designing a remediation, the third step is operationalizing the repair in a productive method. Step one will get all of the hype. The third step is commonly ignored as unsexy, however it’s a very powerful. In any case, what’s consciousness of threat price for those who can’t repair it in a well timed vogue, earlier than it will get exploited?
If you happen to’re fascinated about operationalizing CNAPP’s findings and making actual impression to your cloud permissions threat, take a look at the Cloud Permissions Firewall.