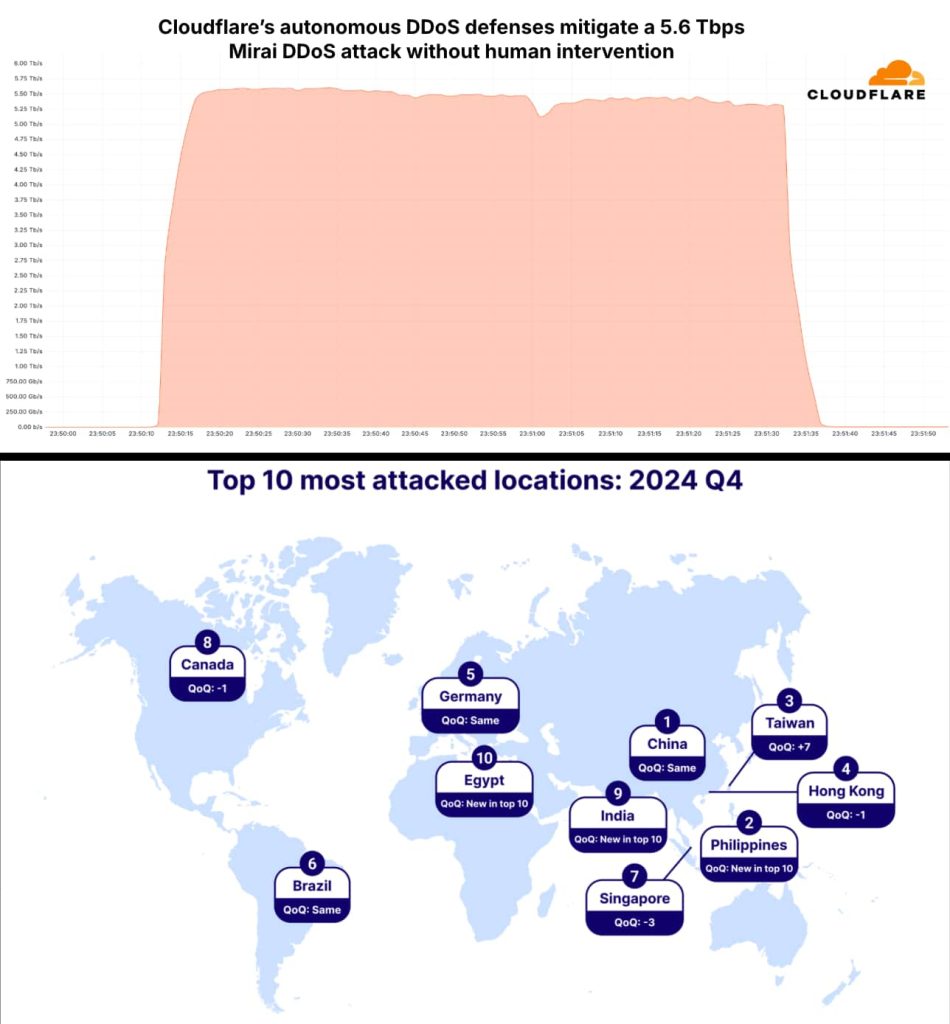
Cloudflare mitigates a record-breaking 5.6 Tbps DDoS assault, highlighting the rising menace of hyper-volumetric assaults. Be taught in regards to the newest DDoS developments and the rising have to strengthen the safety posture of your group.
In its newest analysis report, Cloudflare reveals Distributed Denial-of-Service assault (DDoS assault) developments noticed within the fourth quarter of 2024, drawing comparisons to earlier quarters and the complete yr.
The Cloudflare DDoS Risk Report for This autumn 2024 highlights a major surge in each the amount and depth of DDoS assaults noticed all year long. Cloudflare revealed that it efficiently mitigated a record-breaking 5.6 terabits per second (Tbps) DDoS assault launched by a Mirai-variant botnet within the fourth quarter of 2024 comprising 13,000 IoT gadgets. The assault focused an East Asian Web Service Supplier (ISP) on October twenty ninth.
Beforehand, Cloudflare mitigated a 3.8 Tbps DDoS assault in October 2024. The most recent unprecedented assault, which lasted solely 80 seconds and was promptly mitigated by Cloudflare’s autonomous defence techniques, highlights the escalating sophistication and scale of DDoS threats.
Moreover, the report reveals a dramatic improve in hyper-volumetric assaults exceeding 1 Tbps. Cloudflare’s report revealed a whopping 53% improve within the frequency of DDoS assaults all through 2024, with the corporate blocking roughly 21.3 million assaults – a median of 4,870 assaults per hour. Assaults exceeding 1Tbps surged by a staggering 1,885% quarter-over-quarter, whereas these exceeding 100 million packets per second (pps) elevated by 175%. These high-bandwidth assaults overwhelm typical defences.
The fourth quarter additionally witnessed a disturbing development: a 78% quarter-over-quarter improve in Ransom DDoS assaults. Cybercriminals are more and more leveraging DDoS assaults as a software for extortion, concentrating on companies throughout peak seasons.
Cloudflare recognized the prevalence of varied assault sorts, together with Layer 3/Layer 4 assaults (similar to SYN floods, DNS floods, and UDP floods) and HTTP DDoS assaults. Whereas recognized botnets have been the first supply of HTTP assaults, Cloudflare documented assaults using methods similar to spoofing official browsers and using uncommon HTTP attributes.
Relating to the geographical distribution of assaults, Indonesia emerged because the main supply, adopted by Hong Kong Singapore and China being essentially the most attacked nation. The evaluation additional recognized essentially the most impacted industries, mentioning the Telecommunications, Service Suppliers, and Carriers sectors as the first goal in This autumn.
Whereas nearly all of assaults remained comparatively small, with 63% of HTTP DDoS assaults not exceeding 50,000 requests per second and 93% of network-layer assaults not exceeding 500 Mbps, the emergence of latest assault vectors presents a major concern. Cloudflare noticed a considerable improve in Memcached (314%) and BitTorrent (304%) DDoS assaults, highlighting the adaptability of menace actors in exploiting new vulnerabilities.
Cloudflare’s report emphasises the need of proactive DDoS safety methods and the necessity for organizations to know the evolving nature of DDoS threats and put money into options to successfully mitigate unprecedented scale and complexity assaults.
RELATED TOPICS
- The Mirai Botnet: what it’s and What it has accomplished
- Matrix Hackers Deploy New IoT Botnet for DDoS Assaults
- Mirai-Impressed Gorilla Botnet Hits Targets in 100 International locations
- Mirai-based NoaBot Botnet Hits Linux Programs with Cryptominer
- Panamorfi DDoS Assault Exploits Misconfigured Jupyter Notebooks