A safety researcher found a flaw in Cloudflare’s content material supply community (CDN), which might expose an individual’s normal location by merely sending them a picture on platforms like Sign and Discord.
Whereas the geo-locating functionality of the assault isn’t exact sufficient for street-level monitoring, it will probably present sufficient information to deduce what geographic area an individual lives in and monitor their actions.
Daniel’s discovering is especially regarding for people who find themselves extremely involved about their privateness, like journalists, activists, dissidents, and even cybercriminals.
Nonetheless, for legislation enforcement, this flaw may very well be a boon to investigations, permitting them to study extra concerning the nation or state the place a suspect could also be positioned.
Stealthy 0-click monitoring
Three months in the past, a safety researcher named Daniel found that Cloudflare caches media assets on the information middle nearest to the person to enhance load instances.
“3 months ago, I discovered a unique 0-click deanonymization attack that allows an attacker to grab the location of any target within a 250 mile radius,” defined Daniel.
“With a weak app put in on a goal’s cellphone (or as a background utility on their laptop computer), an attacker can ship a malicious payload and deanonymize you inside seconds–and you would not even know.
To conduct the information-disclosure assault, the researcher would ship a message to somebody with a singular picture, whether or not that be a screenshot or perhaps a profile avatar, hosted on Cloudflare’s CDN.
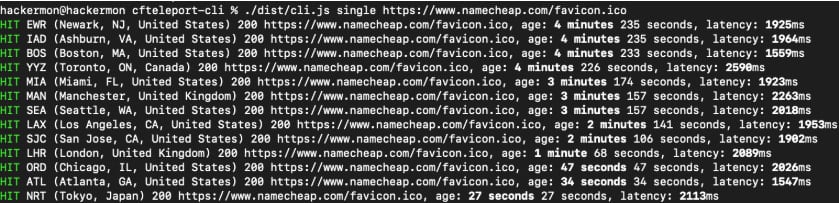
Subsequent, he leveraged a bug in Cloudflare Employees that permits forcing requests by particular information facilities utilizing a customized instrument known as Cloudflare Teleport.
This arbitrary routing is generally disallowed by Cloudflare’s default safety restrictions, which dictate that every request is routed from the closest information middle.
By enumerating cached responses from totally different Cloudflare information facilities for the despatched picture, the researcher might map the overall location of customers primarily based on the CDN returning the closest airport code close to their information middle.
Supply: hackermondev | GitHub
Moreover, since many apps routinely obtain photographs for push notifications, together with Sign and Discord, an attacker can monitor a goal with out person interplay, making this a zero-click assault.
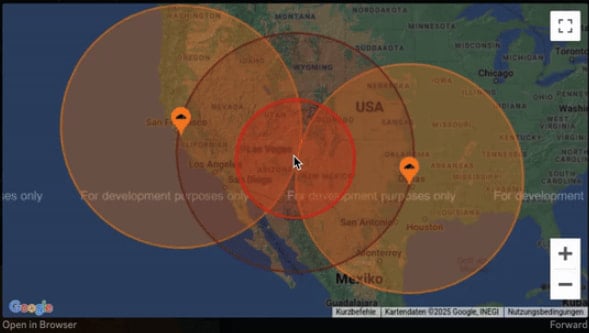
The monitoring accuracy ranges between 50 and 300 miles, relying on the area and what number of Cloudflare datacenters are close by. Precision round main cities must be higher than in rural or much less populated areas.
Whereas experimenting with geo-locating Discord’s CTO, Stanislav Vishnevskiy, the researcher discovered that Cloudflare makes use of anycast routing with a number of close by information facilities dealing with a request for higher load balancing, permitting even higher accuracy.
Supply: hackermondev | GitHub
Response from affected platforms
As first reported by 404 Media, the researcher disclosed his findings to Cloudflare, Sign, and Discord, and the previous marked it as resolved and awarded him a $200 bounty.
Daniel confirmed that the Employees bug was patched, however by reprogramming Teleport to make use of a VPN to check totally different CDN areas, the geo-locating assaults are nonetheless potential, if a bit extra cumbersome now.
“I chose a VPN provider with over 3,000 servers located in various locations across 31 different countries worldwide,” explains the researcher in his writeup.
“Using this new method, I’m able to reach about 54% of all Cloudflare datacenters again. While this doesn’t sound like a lot, this covers most places in the world with significant population.”
Responding to a subsequent request, Cloudflare instructed the researcher that it’s in the end the customers’ duty to disable caching.
Discord rejected the report as a Cloudflare subject, as did Sign, noting that it is exterior their mission’s scope to implement network-layer anonymity options.
BleepingComputer has reached out to Sign, Discord, and Cloudflare for a touch upon the researcher’s findings, however we’re nonetheless ready for his or her responses.
