Throughout a distributed denial-of-service marketing campaign focusing on organizations within the monetary providers, web, and telecommunications sectors, volumetric assaults peaked at 3.8 terabits per second, the biggest publicly recorded to this point. The assault consisted of a “month-long” barrage of greater than 100 hyper-volumetric DDoS assaults flooding the community infrastructure with rubbish information.
In a volumetric DDoS assault, the goal is overwhelmed with giant quantities of information to the purpose that they eat the bandwidth or exhaust the assets of functions and gadgets, leaving respectable customers with no entry.
Asus routers, MikroTik gadgets, DVRs, and internet servers
Most of the assaults aimed on the goal’s community infrastructure (community and transport layers L3/4) exceeded two billion packets per second (pps) and three terabits per second (Tbps).
In keeping with researchers at web infrastructure firm Cloudflare, the contaminated gadgets had been unfold throughout the globe however a lot of them had been situated in Russia, Vietnam, the U.S., Brazil, and Spain.
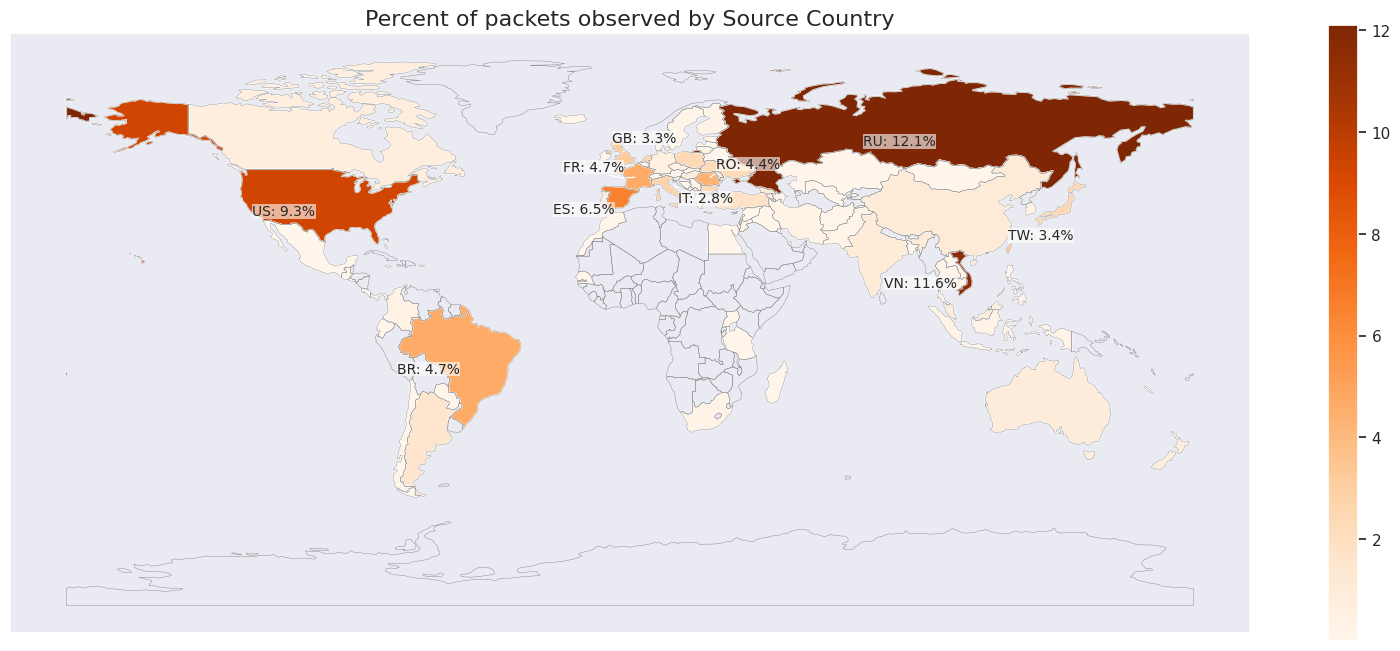
supply: Cloudflare
The menace actor behind the marketing campaign leveraged a number of varieties of compromised gadgets, which included numerous Asus house routers, Mikrotik methods, DVRs, and internet servers.
Cloudflare mitigated all of the DDoS assaults autonomously and famous that the one peaking at 3.8 Tbps lasted 65 seconds.
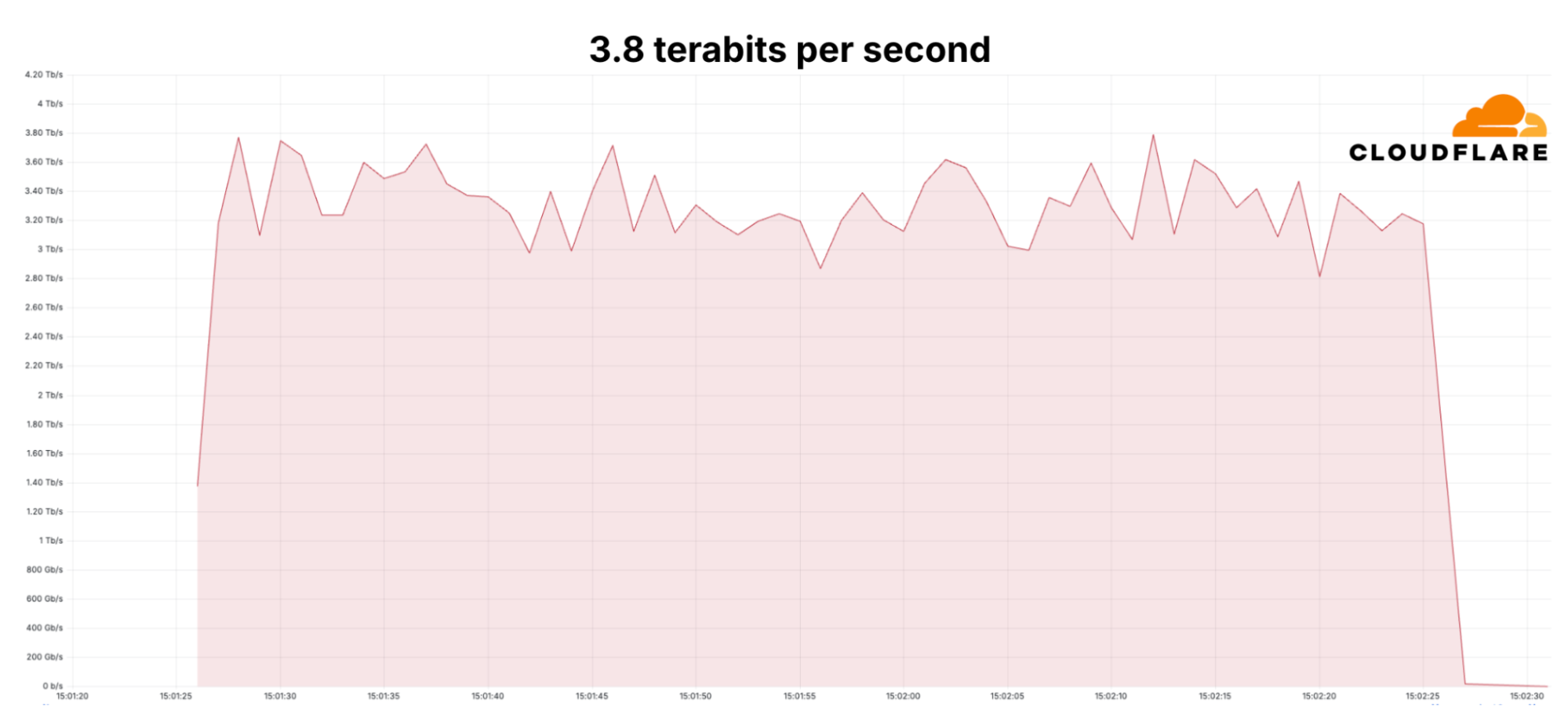
The researchers say that the community of malicious gadgets used primarily the Person Datagram Protocol (UDP) on a hard and fast port, a protocol with quick information transfers however which doesn’t require establishing a proper connection.
Beforehand, Microsoft held the file for defending towards the biggest volumetric DDoS assault of three.47 Tbps, which focused an Azure buyer in Asia.
Usually, menace actors launching DDoS assaults depend on giant networks of contaminated gadgets (botnets) or search for methods to amplify the delivered information on the goal, which requires a smaller variety of methods.
In a report this week, cloud computing firm Akamai confirmed that the not too long ago disclosed CUPS vulnerabilities in Linux could possibly be a viable vector for DDoS assaults.
After scanning the general public web for methods susceptible to CUPS, Akamai discovered that greater than 58,000 had been uncovered to DDoS assaults from exploiting the Linux safety problem.
Extra testing revealed that a whole lot of susceptible “CUPS servers will beacon back repeatedly after receiving the initial requests, with some of them appearing to do it endlessly in response to HTTP/404 responses.”
These servers despatched 1000’s of requests to Akamai’s testing methods, displaying vital potential for amplification from exploiting the CUPS flaws.
