Shield your self from the ClickFix assault! Learn the way cybercriminals are utilizing pretend Google Meet pages to trick customers into downloading malware. Uncover the newest ways employed by these malicious actors and keep secure on-line.
Cybersecurity researchers at Sekoia have detected an uptick in cyberattacks concentrating on customers of the favored video conferencing platform, Google Meet, using a infamous tactic, dubbed “ClickFix.” This tactic emerged in Could 2024 and includes mimicking legit providers like Google Chrome, Fb, or Google Meet, to trick customers into downloading malware.
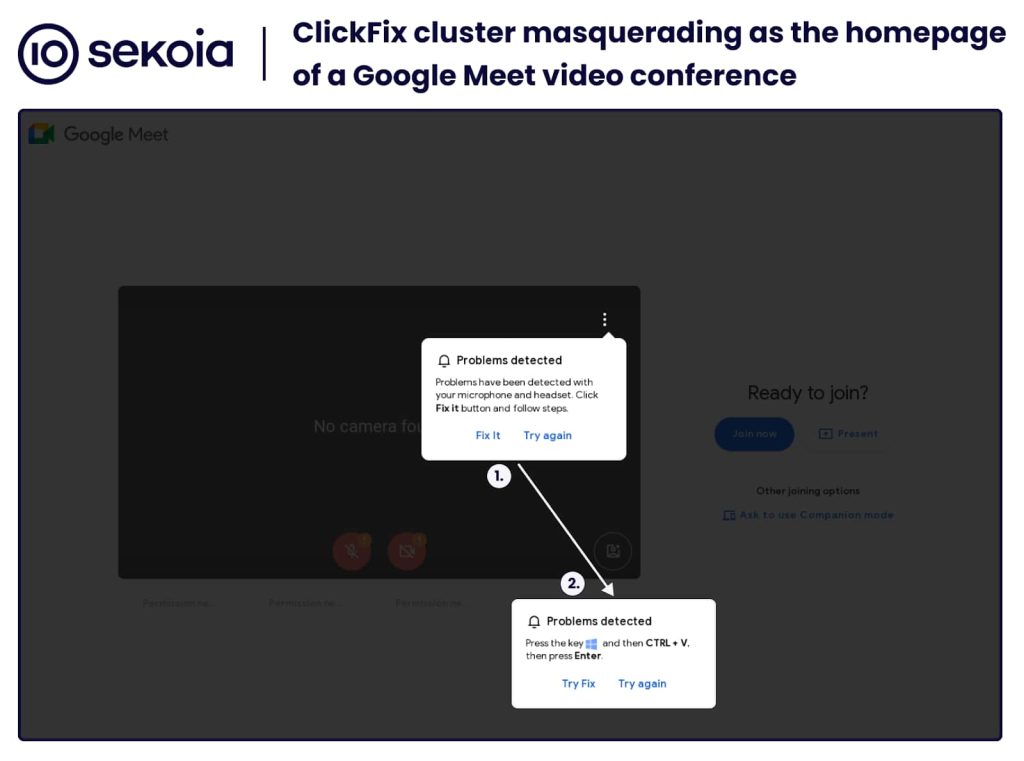
Based on Sekoia’s report, attackers are displaying pretend error messages mimicking legit alerts from Google Meet, prompting customers to click on a “Fix It” button or carry out different actions. Nonetheless, these actions unknowingly execute malicious code that installs malware on the sufferer’s system.
The ClickFix marketing campaign leverages a number of malware distribution campaigns. Sekoia researchers analyzed a ClickFix cluster impersonating Google Meet video conferences, which focused each Home windows and macOS customers.
For Home windows customers, the pretend error message claimed microphone or headset points, prompting them to repeat a script that downloaded Stealc and Rhadamanthys infostealers. macOS customers have been tricked into downloading the AMOS Stealer malware.
“Given the variety of initial malicious websites redirecting to this infrastructure, we assess with high confidence that it is shared among multiple threat actors. They collaborate within a centralized Traffers team to share certain resources, including this infrastructure and the AMOS Stealer, which is also sold as Malware-as-a-Service.”
Sekoia
Potential Perpetrators
The investigation revealed that two cybercrime teams, “Slavic Nation Empire” (linked with cryptocurrency rip-off staff Marko Polo) and “Scamquerteo Team” (a subgroup of cryptocurrency rip-off staff CryptoLove), have been doubtless behind this ClickFix cluster. These teams focus on concentrating on customers concerned in cryptocurrency belongings, Web3 purposes, and decentralized finance (DeFi).
Each groups use the identical ClickFix template to impersonate Google Meet, suggesting they share supplies and infrastructure. Sekoia analysts estimate that each groups use the identical cybercrime service to produce the pretend Google Meet cluster, and it’s doubtless {that a} third occasion manages their infrastructure or registers their domains.
The malware delivered by these assaults consists of infostealers, botnets, and distant entry instruments. These malicious packages can steal delicate information, compromise methods, and allow additional assaults.
ClickFix Scope
The ClickFix tactic is especially harmful as a result of it bypasses conventional safety measures. By not requiring customers to obtain a file immediately, it avoids detection by internet browser security measures. This makes it extra prone to ensnare unsuspecting victims.
To guard your self from ClickFix assaults, be cautious of surprising error messages, confirm scripts earlier than copying and pasting them from unknown sources, use sturdy safety software program like antivirus and anti-malware, be cautious with hyperlinks, and allow two-factor authentication so as to add an additional layer of safety to your on-line accounts.
RELATED TOPICS
- Konni RAT Exploiting Phrase Docs to Steal Information from Home windows
- Faux Chrome Browser Replace Installs NetSupport Supervisor RAT
- Bifrost RAT Variant Targets Linux Units, Mimics VMware Area
- AsyncRAT Infiltrates Key US Infrastructure By GIFs and SVGs
- Fashionable Android Display screen Recorder iRecorder App Revealed as Trojan