CISA warned right now that attackers are actively exploiting a maximum-severity GitLab vulnerability that permits them to take over accounts through password resets.
GitLab hosts delicate information, together with proprietary code and API keys, and account hijacking can have a big affect. Profitable exploitation also can result in provide chain assaults that may compromise repositories by inserting malicious code in CI/CD (Steady Integration/Steady Deployment) environments.
Tracked as CVE-2023-7028, the safety flaw is because of an improper entry management weak spot that may enable distant unauthenticated menace actors to ship password reset emails to electronic mail accounts below their management to alter the password and hijack focused accounts with out consumer interplay.
Though attackers cannot exploit this vulnerability to hijack accounts the place two-factor authentication (2FA) is enabled, it’s vital to patch techniques the place accounts aren’t protected with this extra safety measure.
The CVE-2023-7028 bug impacts GitLab Neighborhood and Enterprise editions, and GitLab mounted it in 16.7.2, 16.5.6, and 16.6.4 and backported patches to variations 16.1.6, 16.2.9, and 16.3.7.
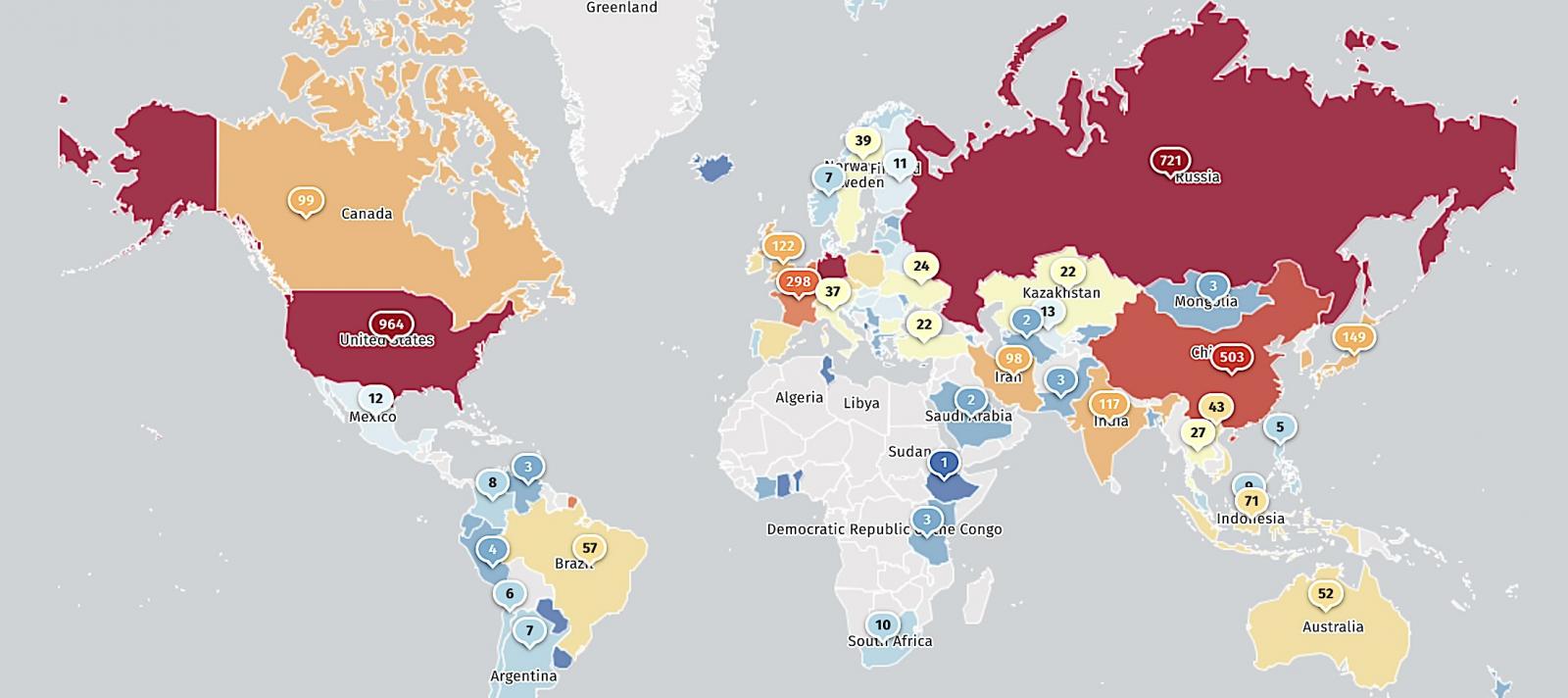
Whereas menace monitoring service Shadowserver discovered 5,379 weak GitLab cases uncovered on-line in January (the week safety patches had been launched), lower than half (2,394) are nonetheless reachable in the intervening time.
CISA added CVE-2023-7028 to its Identified Exploited Vulnerabilities Catalog on Wednesday, confirming it is now actively exploited in assaults and ordering U.S. federal companies to safe their techniques inside three weeks by Could 22.
The U.S. cybersecurity company hasn’t shared any data relating to ongoing assaults exploiting this most severity GitLab safety bug, nevertheless it did affirm it has no proof that it is being utilized in ransomware assaults.
“These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise,” CISA stated right now.
Though the company’s KEV catalog primarily targets federal companies, non-public organizations utilizing the GitLab DevOps platform must also prioritize patching this vulnerability to forestall assaults.
Those that have not already patched could have been compromised already, so they need to comply with GitLab’s incident response information and test for indicators of compromise as quickly as doable.
