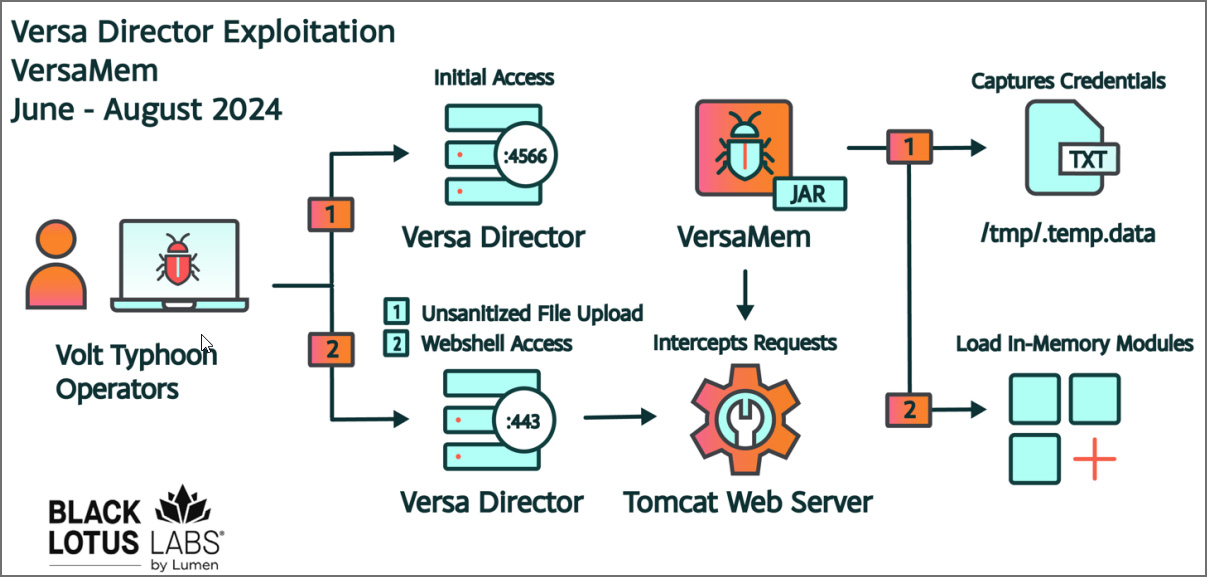
The Chinese language state-backed hacking group Volt Hurricane is behind assaults that exploited a zero-day flaw in Versa Director to add a customized webshell to steal credentials and breach company networks.
Versa Director is a administration platform ISPs and MSPs use to handle digital WAN connections created utilizing SD-WAN providers.
The vulnerability is tracked as CVE-2024-39717 and resides in a function permitting admins to add customized icons to customise the Versa Director GUI. Nevertheless, the flaw allowed menace actors with administrator privileges to add malicious Java recordsdata disguised as PNG photos, which may then be executed remotely.
In an advisory revealed yesterday, Versa says that Director variations 21.2.3, 22.1.2, and 22.1.3 are impacted by the flaw. Upgrading to the newest model, 22.1.4, will repair the vulnerability, and admins ought to evaluate the seller’s system hardening necessities and firewall tips.
Versa advised BleepingComputer that they classify this vulnerability as a privilege elevation flaw because it was used to reap credentials from customers who logged into the system. Nevertheless, different forms of malware may have been used to carry out several types of malicious exercise on the system.
Exploited to breach networks
Researchers at Lumen’s Black Lotus Labs found the Versa zero-day vulnerability on June 17 after discovering a malicious Java binary named ‘VersaTest.png’ uploaded from Singapore to VirusTotal.
Evaluation of the file decided it was a customized Java internet shell named internally as “Director_tomcat_memShell,” however dubbed by the researchers as “VersaMem”. The malware at the moment has 0 detections on VirusTotal and is designed particularly for Versa Administrators.
After analyzing world telemetry, Black Lotus Labs detected site visitors from SOHO routers exploiting a Versa vulnerability as a zero-day to deploy this internet shell since June 12, 2024.
“We recognized compromised SOHO gadgets with TCP periods over port 4566 which had been instantly adopted by giant HTTPS connections over port 443 for a number of hours. Provided that port 4566 is mostly reserved for Versa Director node pairing and the pairing nodes usually talk with this port for prolonged intervals of time, there shouldn’t be any legit communications to that port from SOHO gadgets over quick timeframes.
We assess the quick timeframe of TCP site visitors to port 4566 instantly adopted by moderate-to-large periods of HTTPS site visitors over port 443 from a non-Versa node IP deal with (e.g. SOHO system) as a probable signature of profitable exploitation.”
❖ Black Lotus Labs
Whereas the vulnerability requires administrator privileges, the researchers say that the menace actors had been in a position to achieve elevated privileges by an uncovered Versa Director port used for excessive availability (HA) pairing of nodes.
Versa confirmed this to BleepingComputer, explaining that the menace actors exploited the vulnerability to steal credentials utilizing these steps:
- Entry the uncovered HA port utilizing an NCS shopper and create an account with Supplier-Information-Heart-Admin or Supplier-Information-Heart-System-Admin privileges.
- Exploit the zero-day vulnerability utilizing the account created in Step #1 to plant the malicious JAR internet shell used to steal credentials.
- (Optionally available) Delete the account created in Step #1.
- Harvest credentials of legit customers who logged in subsequent to Step #2.
Versa says that the menace actors couldn’t have exploited the flaw if the HA port was protected based on the corporate’s firewall tips. When requested why the port was open by default, Versa stated it was required for the excessive availability function.
Black Lotus Labs reported the flaw to Versa on July 20, who then privately alerted prospects on July 26.
The customized VersaMem internet shell is primarily used to steal the credentials of legit customers to breach the focused inner community. These stolen passwords are encrypted and saved to the /tmp/.temp.information file for later retrieval by the menace actors.
The customized internet shell can even stealthily load in-memory Java byte code despatched by the attackers, which is then executed within the Tomcat webserver operating on the compromised Versa Director system.
Supply: Lumen’s Black Lotus Labs
Black Lotus Labs advised BleepingComputer that they know of 4 organizations within the US and one in India impacted by the zero-day, with the menace actors breaching the community in at the very least one of many assaults.
“Analysis of our global telemetry identified actor-controlled small-office/home-office (SOHO) devices exploiting this zero-day vulnerability at four U.S. victims and one non-U.S. victim in the Internet service provider (ISP), managed service provider (MSP) and information technology (IT) sectors as early as June 12, 2024,” defined Black Lotus Labs.
Clients can verify if their gadgets had been compromised by inspecting the /var/versa/vnms/internet/custom_logo/ folder for suspicious recordsdata. Lumen’s Black Lotus Labs recommends admins verify gadgets for newly created accounts and limit entry to the HA port on ports 4566 and 4570.
The researchers have shared a whole listing of IoCs associated to this marketing campaign and additional steps to mitigate assaults within the report.
After publication of this story, cybersecurity agency Censys advised BleepingComputer that they had seen 163 Versa Director servers uncovered on the Web.
Of those servers, BleepingComputer decided that eight could also be susceptible as they expose their excessive availability port, which can be utilized to achieve the elevated privileges required to use the vulnerability.
Of those eight servers, 5 are within the US, one is in China, one is in Hong Kong, and the final is the Czech Republic.
Volt Hurricane
The researchers linked these assaults to Volt Hurricane, aka Bronze Silhouette, primarily based on recognized techniques, strategies, and procedures.
Volt Hurricane is a Chinese language state-sponsored hacking group recognized to hijack SOHO routers and VPN gadgets and use them to launch stealthy assaults on focused organizations.
The menace actors use compromised routers, firewalls, and VPN gadgets to mix their malicious site visitors with legit site visitors so assaults stay undetected.
In December 2023, Black Lotus Labs disclosed that Volt Hurricane was compromising SOHO routers, VPN gadgets, and IP cameras to construct the ‘KV-botnet,’ used to launch assaults on focused networks. Gadgets compromised to host the malware on this marketing campaign included Netgear ProSAFE firewalls, Cisco RV320s, DrayTek Vigor routers, and Axis IP cameras.
A month later, CISA and the FBI issued a joint advisory calling on producers of small workplace/dwelling workplace (SOHO) routers to make sure their gadgets’ safety towards assaults by Volt Hurricane.
That very same day, the FBI disclosed that they disrupted Volt Hurricane’s KV-botnet, which the menace actors had used to assault essential infrastructure within the US.
In February, Volt Hurricane exploited a distant code execution vulnerability in FortiOS SSL VPN to put in customized malware, with over 20,000 Fortinet gadgets impacted by the assaults.
Replace 8/27/24: Added details about uncovered servers from Censys.
