New assaults attributed to China-based cyber espionage group Mustang Panda present that the risk actor switched to new methods and malware referred to as FDMTP and PTSOCKET to obtain payloads and steal data from breached networks.
Researchers discovered that the hackers are utilizing a variant of the HIUPAN worm to ship the PUBLOAD malware stager by means of detachable drives on the community.
Mustang Panda, (also referred to as HoneyMyte/Broze President/Earth Preta/Polaris/Stately Taurus) is a Chinese language state-backed hacker group that focuses on cyberespionage operations in opposition to authorities and non-government entities largely in Asia-Pacific, however organizations in different areas are additionally inside its goal scope.
Worm-based assault chain
Mustang Panda usually makes use of spear-phishing emails because the preliminary entry vector however in a report printed at present, researchers at cybersecurity firm Pattern Micro say that new assaults from the risk actor unfold PUBLOAD on the community by means of detachable drives contaminated with a variant of the HIUPAN worm.

Supply: Pattern Micro
HIUPAN hides its presence by transferring all its recordsdata right into a hidden listing and leaving solely a seemingly official file (“USBConfig.exe”) seen on the drive to trick the consumer into executing it.
PUBLOAD is the primary management software within the assaults. It is executed on the system by means of DLL side-loading, establishes persistence by modifying the Home windows Registry, after which executes reconnaissance-specific instructions to map the community.
Aside from PUBLOAD, the risk actor used a brand new piece of malware named FDMTP, which acts as a secondary management software. The researchers say that FDMTP is embedded within the information part of a DLL and it may also be deployed by means of DLL-sideloading.
In accordance with the researchers, information assortment in more moderen Mustang Panda assaults is finished in RAR archives and targets .DOC, .DOCX, .XLS, .XLSX, .PDF, .PPT, and .PPTX recordsdata from specified cutoff dates.
The risk actor exfiltrates the knowledge by means of PUBLOAD utilizing the cURL software. Nevertheless, an alternate exists within the customized PTSOCKET file switch software, an applied based mostly on TouchSocket over DMTP.

Supply: Pattern Micro
Spear-phishing marketing campaign in June
In June, researchers noticed a “fast-paced spear-phishing campaign” from Mustang Panda to ship the DOWNBAIT downloader that retrieved a decoy doc in addition to the PULLBAIT malware, which is executed in reminiscence.
Subsequent, the attacker fetches and execute the first-stage backdoor referred to as CBROVER that’s digitally signed to keep away from triggering the alarm.
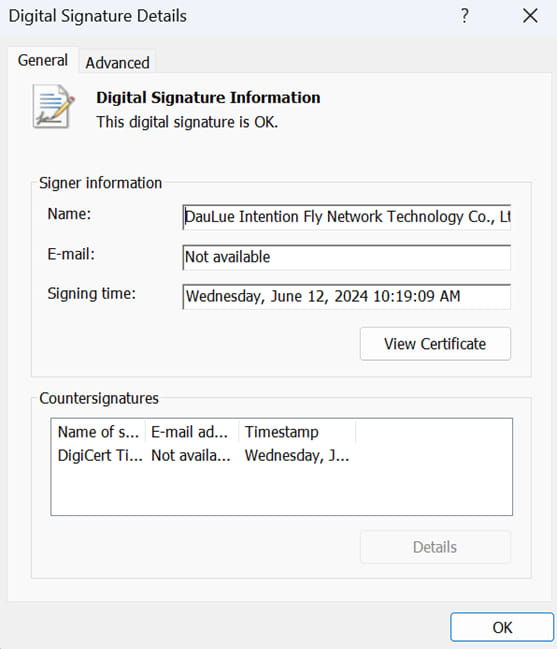
Supply: Pattern Micro
Mustang Panda was noticed utilizing PLUGX to introduce different instruments like ‘FILESAC,’ a software that collects doc recordsdata like .DOC, .XLS, .PDF, .DWG, .PPTX, .DOCX, and exfiltrates them.
Pattern Micro notes there may be one other exfiltration technique seemingly involving the abuse of Microsoft OneDrive, however the researchers could not discover the software used for the duty. The risk group has been seen abusing Google Drive beforehand to introduce malware onto authorities networks.
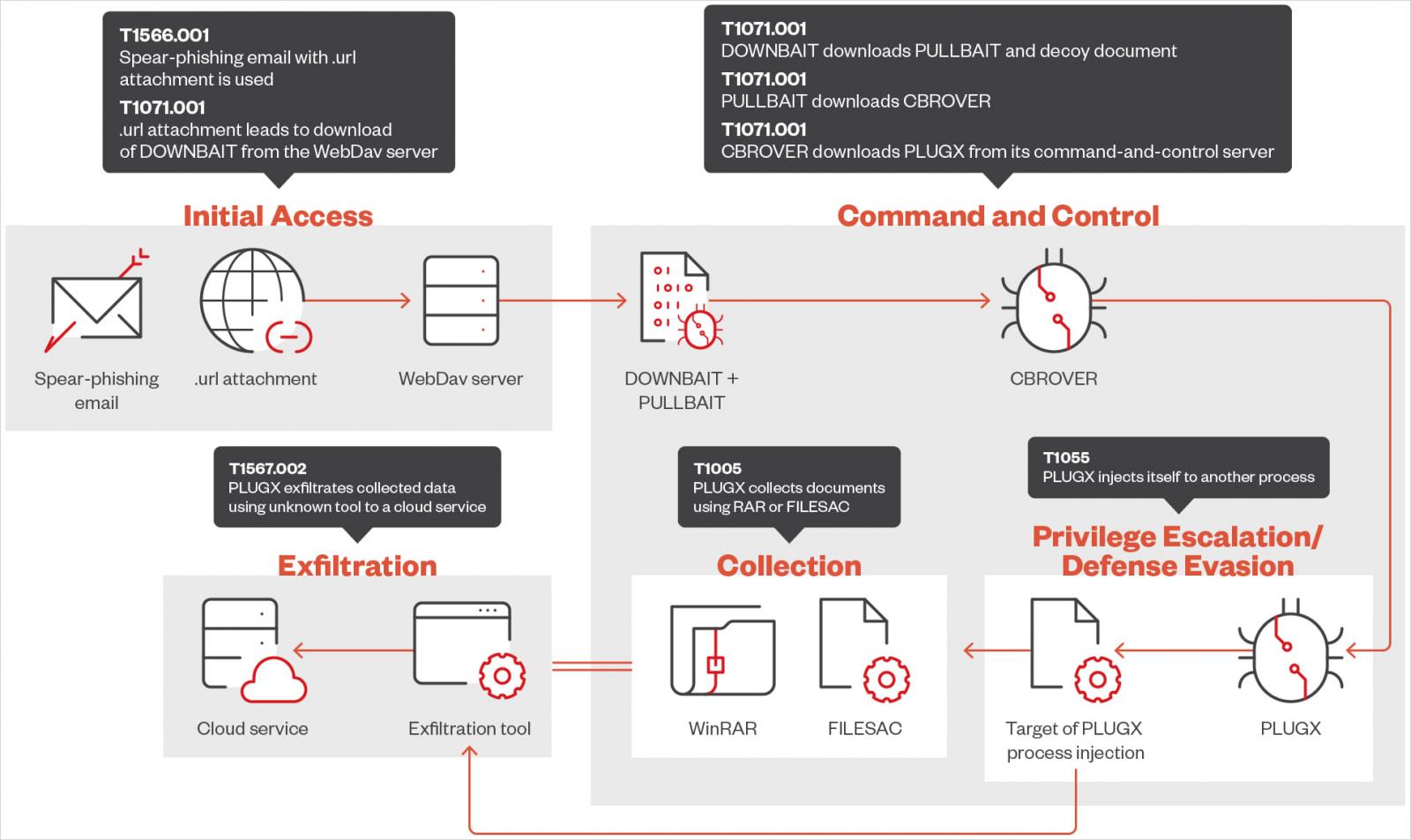
Supply: Pattern Micro
Pattern Micro researchers say that Mustang Panda, which the corporate tracks as Earth Preta, has made important strides in “malware deployment and strategies, particularly in their campaigns targeting government entities” (e.g. army, police, overseas affair companies, welfare, the chief department, and schooling within the APAC area).
They notice that the risk actor continues to be extremely energetic within the space and the brand new ways point out that it’s specializing in “highly targeted and time-sensitive operations.”
A full record of indicators of compromise (IoCs) related to Mustang Panda’s newest campaigns is accessible right here.
