The FBI and cybersecurity researchers have disrupted an enormous Chinese language botnet referred to as “Raptor Train” that contaminated over 260,000 networking gadgets to focus on important infrastructure within the US and in different nations.
The botnet has been used to focus on entities within the navy, authorities, larger schooling, telecommunications, protection industrial base (DIB), and IT sectors, primarily within the US and Taiwan.
Over 4 years, Raptor Practice has grown into a posh, multi-tiered community with an enterprise-grade management system for dealing with tens of servers and a lot of contaminated SOHO and client gadgets: routers and modems, NVRs and DVRs, IP cameras, and network-attached storage (NAS) servers.
Multi-tiered botnet
Raptor Practice began in Could 2020 and seems to have remained below the radar till final 12 months when it was found by researchers at Black Lotus Labs, the risk analysis and operations arm at Lumen Applied sciences, whereas investigating compromised routers.
Whereas the first payload is a variant of the Mirai malware for distributed denial-of-service (DDoS) assaults, which the researchers name Nosedive, the botnet has not been seen deploying such assaults.
In a report immediately, the researchers describe three tiers of exercise inside Raptor Practice, every for particular operations, e.g. sending out duties, managing exploitation or payload servers, and command and management (C2) methods.
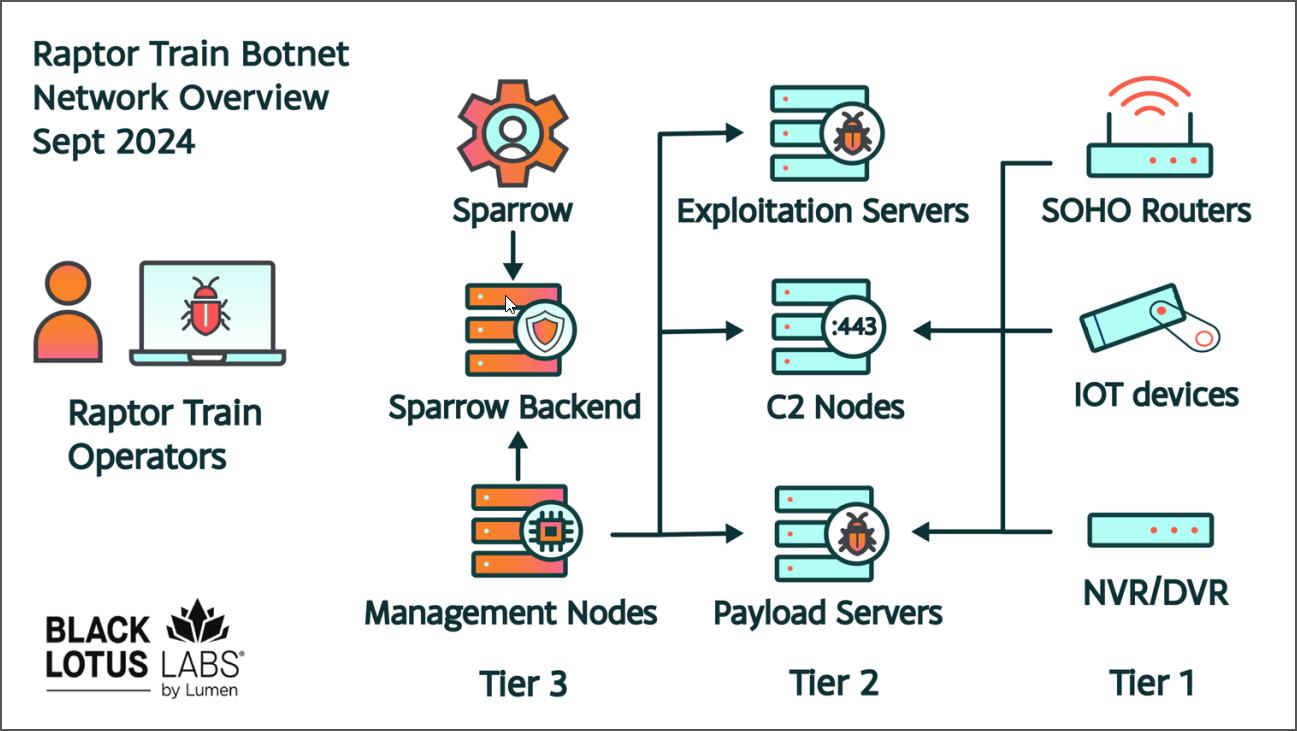
supply: Black Lotus Labs
The variety of lively compromised gadgets within the botnet fluctuates however researchers imagine that greater than 200,000 methods have been contaminated by Raptor Practice because it began in Could 2020, and it managed over 60,000 gadgets at its peak in June final 12 months.
In the meanwhile, Black Lotus Labs is monitoring across the identical variety of lively contaminated gadgets, fluctuating by just a few thousand since August.
In an alert immediately about the identical botnet, the FBI notes that Raptor Practice contaminated greater than 260,000 gadgets.
supply: FBI
Talking at the Aspen Cyber Summit earlier this month, FBI Director Christopher Wray mentioned that Flax Storm labored on the course of the Chinese language authorities.
To take away the risk, the FBI executed Courtroom approved operations that led to taking management of the botnet infrastructure. In response, Flax Storm tried emigrate contaminated gadgets to new servers “and even conducted a DDOS attack against us,” Wray mentioned.
“Ultimately as part of this operation we were able to identify thousands of infected devices, and then with court authorization, issued commands to remove malware from them, prying them from China’s grip” – Christopher Wray
In a MySQL database retrieved from an upstream administration server (Tier 3), the FBI discovered that in June this 12 months, there have been greater than 1.2 million data of compromised gadgets (lively and beforehand compromised), with 385,000 distinctive methods within the U.S.
The FBI additionally related the botnet to the Flax Storm state-sponsored hackers, saying that the management of Raptor Practice was performed by way of the Chinese language firm Integrity Know-how Group (Integrity Tech) utilizing China Unicom Beijing Province Community IP addresses.
With an structure that may deal with greater than 60 C2s and the bots they handle, Raptor Practice sometimes has tens of 1000’s of lively Tier 1 gadgets when engaged in campaigns:
| Modems/Routers | |
| ActionTec PK5000 | ASUS RT-*/GT-*/ZenWifi |
| TP-LINK | DrayTek Vigor |
| Tenda Wi-fi | Ruijie |
| Zyxel USG* | Ruckus Wi-fi |
| VNPT iGate | Mikrotik |
| TOTOLINK | |
| IP Cameras | |
| D-LINK DCS-* | Hikvision |
| Mobotix | NUUO |
| AXIS | Panasonic |
| NVR/DVR | Shenzhen TVT NVRs/DVRs |
| NAS gadgets | |
| QNAP (TS Sequence) | Fujitsu |
| Synology | Zyxel |
The researchers say that Raptor Practice operators add gadgets in Tier 1 doubtless by exploiting “exploiting more than 20 different device types with both 0-day and n-day (known) vulnerabilities.”
As a result of Nosedive payloads wouldn’t have a persistence mechanism, these gadgets keep within the botnet for about 17 days and the operators recruit new ones as wanted.
The Tier 2 community is for command and management, exploitation, and payload servers for Tier 1 gadgets.
Black Lotus Labs distinguishes between first-stage and second-stage payload servers, with the previous delivering a extra generic payload and the latter partaking in additional focused assaults on particular system sorts.
The researchers imagine that this can be a part of an effort to higher cover the zero-day vulnerabilities used within the assaults.
Over time, Raptor Practice has elevated the variety of C2 servers, from as much as 5 between 2020 and 2022, to 11 final 12 months, and greater than 60 this 12 months between June and August.
The administration of the whole botnet is finished manually over SSH or TLS from Tier 3 methods (referred to as Sparrow nodes by the attacker), which ship instructions and acquire information reminiscent of bot info and logs.
For simpler operation, Raptor Practice’s Sparrow nodes present an internet interface (Javascript front-end), backend, and auxiliary capabilities to generate payloads and exploits.
Raptor Practice campaigns
Black Lotus Labs has tracked 4 Raptor Practice campaigns since 2020 and found dozens of Tier 2 and Tier 3 domains and IP addresses used within the assaults.
Beginning Could 2023, in a marketing campaign that researchers name Canaray, the botnet operators confirmed a extra focused method and added to Raptor Practice largely ActionTec PK5000 modems, Hikvision IP cameras, Shenzhen TVT NVRs and ASUS RT- and GT- routers.
For the almost two months throughout the Canary marketing campaign, one Tier 2 second-stage server contaminated not less than 16,000 gadgets.
The fourth recruitment effort (Oriole marketing campaign) that the researchers noticed started in June 2023 and lasted till this September. Final month, the botnet had not less than 30,000 gadgets in Tier 1.
The researchers say that the C2 area w8510[.]com used within the Oriole marketing campaign “became so prominent amongst compromised IoT devices, that by June 3, 2024, it was included in the Cisco Umbrella domain rankings” and that by August it was additionally in Cloudflare’s Radar high a million domains.
“This is a concerning feat because domains that are in these popularity lists often circumvent security tools via domain whitelisting, enabling them to grow and maintain access and further avoid detection” – Black Lotus Labs
In keeping with the researchers, the botnet was used final December in scanning actions that focused the U.S. navy, U.S. authorities, IT suppliers, and protection industrial bases.
Nonetheless, it seems that the focusing on efforts are world, because the Raptor Practice was additionally used to focus on a authorities company in Kazakhstan.
Moreover, Black Lotus Labs notes that the botnet was additionally concerned in exploitation makes an attempt towards Atlassian Confluence servers and Ivanti Join Safe home equipment (doubtless by way of CVE-2024-21887) at organizations in the identical exercise sectors.
At the moment, the Raptor Practice botnet is not less than partially disrupted as Black Lotus Labs is null-routing visitors to the recognized infrastructure factors, “including their distributed botnet management, C2, payload and exploitation infrastructure.”
Linked to Chinese language state hackers
In keeping with the symptoms discovered throughout the investigation, Black Lotus Labs assesses with medium to excessive confidence that the operators of Raptor Practice are doubtless state-sponsored Chinese language hackers, particularly the Flax Storm group.
In assist of the idea shouldn’t be solely the selection of targets, which aligns with Chinese language pursuits but in addition the language used within the codebase and infrastructure, in addition to the overlapping of assorted ways, methods, and procedures.
The researchers seen that Tier 3 administration node connections to Tier 2 methods over SSH occurred “almost exclusively” throughout China’s regular workweek hours.
Moreover, the outline of the capabilities and interface menus, feedback, and references within the codebase have been in Chinese language.
Regardless of being a complicated botnet, there are steps that customers and community defenders can take to guard towards Raptor Practice. As an illustration, community directors ought to test for giant outbound information transfers, even when the vacation spot IP is from the identical space.
Customers are really helpful to reboot their routers repeatedly and set up the newest updates from the seller. Additionally, they need to substitute gadgets which are not supported and do not obtain updates (end-of-life methods).
