Cybersecurity researchers have shed extra gentle on a distant entry trojan (RAT) referred to as Deuterbear utilized by the China-linked BlackTech hacking group as a part of a cyber espionage marketing campaign focusing on the Asia-Pacific area this yr.
“Deuterbear, while similar to Waterbear in many ways, shows advancements in capabilities such as including support for shellcode plugins, avoiding handshakes for RAT operation, and using HTTPS for C&C communication,” Development Micro researchers Pierre Lee and Cyris Tseng stated in a brand new evaluation.
“Comparing the two malware variants, Deuterbear uses a shellcode format, possesses anti-memory scanning, and shares a traffic key with its downloader unlike Waterbear.”
BlackTech, energetic since no less than 2007, can also be tracked by the broader cybersecurity group below the monikers Circuit Panda, Earth Hundun, HUAPI, Manga Taurus, Palmerworm, Pink Djinn, and Temp.Overboard.
Cyber assaults orchestrated by the group have lengthy concerned the deployment of a malware referred to as Waterbear (aka DBGPRINT) for almost 15 years, though campaigns noticed since October 2022 have additionally utilized an up to date model referred to as Deuterbear.
Waterbear is delivered by way of a patched reliable executable, which leverages DLL side-loading to launch a loader that then decrypts and executes a downloader, which contacts a command-and-control (C&C) server to retrieve the RAT module.
Curiously, the RAT module is fetched twice from the attacker-controlled infrastructure, the primary of which is simply used to load the Waterbear plugin that subsequently launches a distinct model of the Waterbear downloader to retrieve the RAT module from one other C&C server.
Put in a different way, the primary Waterbear RAT serves as a downloader whereas the second Waterbear RAT features as a backdoor, harvesting delicate data from the compromised host by means of a set of 60 instructions.
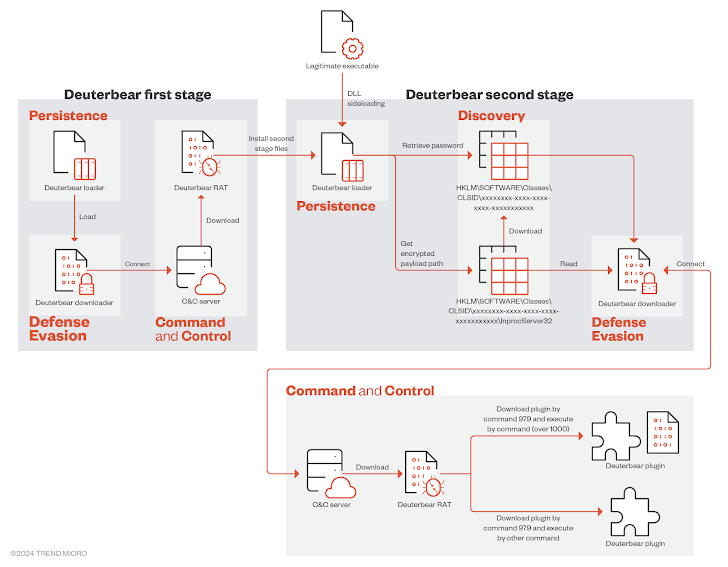
The an infection pathway for Deuterbear is loads much like that of Waterbear in that it additionally implements two levels to put in the RAT backdoor part, but additionally tweaks it to some extent.
The primary stage, on this case, employs the loader to launch a downloader, which connects to the C&C server to fetch Deuterbear RAT with the intention to set up persistence by way of a second-stage loader through DLL side-loading.
This loader is in the end accountable for executing a downloader, which once more downloads the Deuterbear RAT from a C&C server for data theft.
“In most of the infected systems, only the second stage Deuterbear is available,” the researchers stated. “All components of the first stage Deuterbear are totally removed after the ‘persistence installation’ is completed.”
“This strategy effectively protects their tracks and prevents the malware from easily being analyzed by threat researchers, particularly in simulated environments rather than real victim systems.”
Deuterbear RAT can also be a extra streamlined model of its predecessor, retaining solely a subset of the instructions in favor of a plugin-based method to include extra performance.
“Waterbear has gone through continuous evolution, eventually giving rise to the emergence of a new malware, Deuterbear,” Development Micro stated. “Interestingly, both Waterbear and Deuterbear continue to evolve independently, rather than one simply replacing the other.”
Focused Marketing campaign Delivers SugarGh0st RAT
The disclosure comes as Proofpoint detailed an “extremely targeted” cyber marketing campaign focusing on organizations within the U.S. which might be concerned in synthetic intelligence efforts, together with academia, personal business, and authorities, to ship a malware referred to as SugarGh0st RAT.
The enterprise safety firm is monitoring the rising exercise cluster below the identify UNK_SweetSpecter.
“SugarGh0st RAT is a remote access trojan, and is a customized variant of Gh0st RAT, an older commodity trojan typically used by Chinese-speaking threat actors,” the corporate stated. “SugarGh0st RAT has been historically used to target users in Central and East Asia.”
SugarGh0st RAT was first documented late final yr by Cisco Talos in reference to a marketing campaign focusing on the Uzbekistan Ministry of International Affairs and South Korean customers since August 2023. The intrusions had been attributed to a suspected Chinese language-speaking menace actor.
The assault chains entail sending AI-themed phishing messages containing a ZIP archive that, in flip, packs a Home windows shortcut file to deploy a JavaScript dropper accountable for launching the SugarGh0st payload.
“The May 2024 campaign appeared to target less than 10 individuals, all of whom appear to have a direct connection to a single leading U.S.-based artificial intelligence organization according to open source research,” the corporate stated.
The top aim of the assaults isn’t clear, though it is suspected that it might be an try and steal private details about generative synthetic intelligence (GenAI).
What’s extra, the focusing on of U.S. entities additionally coincides with information studies that the U.S. authorities is seeking to curtail China’s entry to GenAI instruments from firms like OpenAI, Google DeepMind, and Anthropic, providing potential motives.
Earlier this yr, the U.S. Division of Justice (DoJ) additionally indicted a former Google software program engineer for stealing proprietary data from the corporate and trying to make use of it at two AI-affiliated know-how firms in China, together with one which he based round Might 2023.
“It is possible that if Chinese entities are restricted from accessing technologies underpinning AI development, then Chinese-aligned cyber actors may target those with access to that information to further Chinese development goals,” the corporate stated.