A brand new joint cybersecurity advisory from the Federal Bureau of Investigation, Cyber Nationwide Mission Pressure, and Nationwide Safety Company exposes new exercise from the Flax Hurricane menace actor.
The cyberattackers have compromised greater than 260,000 Small Workplace/House Workplace (SOHO) routers, firewalls, Community-attached Storage, and Web of Issues gadgets to create a botnet able to launching Distributed Denial of Service assaults or focused assaults geared toward U.S. networks.
Who’s Flax Hurricane?
Flax Hurricane, often known as RedJuliett and Ethereal Panda, is a China-based menace actor energetic since not less than mid-2021, in response to Microsoft. The tech big reported that Flax Hurricane has focused Taiwan-based organizations in addition to different victims in Southeast Asia, North America, and Africa for cyberespionage functions.
In accordance with the FBI’s joint advisory, the group stands behind a China-based firm referred to as Integrity Tech, which has ties to the Chinese language authorities.
Flax Hurricane has used a number of totally different IP addresses from Chinese language supplier China Unicom Beijing Province to manage and handle the botnet. The group has additionally leveraged these addresses to entry different operational infrastructures utilized in laptop intrusion operations geared toward U.S. entities.
Additional studies present that Chinese language-based menace actors have focused companies and governments throughout the globe lately.
SEE: Why Your Enterprise Wants Cybersecurity Consciousness Coaching (TechRepublic Premium)
‘Raptor Train’ botnet
Black Lotus Labs, the menace intelligence workforce from cybersecurity firm Lumen, revealed a report about Flax Hurricane’s compromising of SOHO routers and different gadgets. They referred to as the botnet ensuing from that exercise “Raptor Train” and have been monitoring it for 4 years.
Affected gadgets have been compromised by a variant of the notorious Mirai malware household, making it a weapon of alternative for any cybercriminal aiming to compromise IoT gadgets, as they might simply modify the code for his or her goal.
Within the variant noticed by the FBI, the malware automates the compromise of varied gadgets by exploiting identified vulnerabilities. The oldest exploited vulnerabilities date again to 2015, whereas the newest occurred in July 2024. As soon as compromised, the system sends system and community data to an attacker-controlled C2 server.
As of September 2024, greater than 80 subdomains of a w8510.com area have been related to the botnet.
Almost half of affected gadgets situated within the US
In June 2024, the administration servers working a front-end software program referred to as “Sparrow,” which enabled the attackers to manage compromised gadgets, contained over 1.2 million data. This contains over 385,000 distinctive gadgets within the U.S.
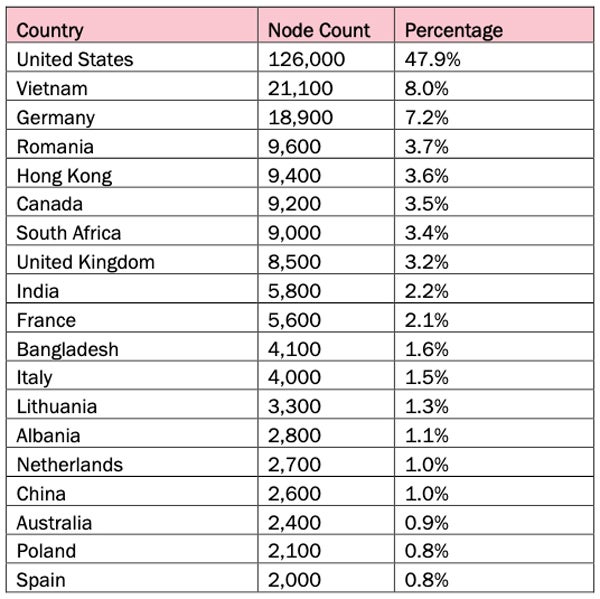
A depend of contaminated gadgets achieved in June 2024 revealed that just about half (47.9%) of the contaminated gadgets have been situated within the U.S., adopted by Vietnam (8%) and Germany (7.2%).
Greater than 50 Linux techniques have been compromised, starting from unsupported, outdated variations to presently supported ones, working Linux Kernel variations from 2.6 to five.4.
The Sparrow interface allowed the menace actor not solely to checklist compromised gadgets but in addition to handle vulnerabilities and exploits, add or obtain recordsdata, execute distant instructions, and tailor IoT-based DDoS assaults at scale.
Gadgets compromised by the botnet cowl many manufacturers, together with ASUS,TP-LINK or Zyxel routers. Additionally impacted have been IP cameras, reminiscent of D-LINK DCS, Hikvision, Mobotix, NUUO, AXIS, and Panasonic cameras. NAS from QNAP, Synology, Fujitsu, and Zyxel have been additionally focused.
FBI Director Christopher Wray introduced in a keynote on the 2024 Aspen Cyber Summit {that a} court docket authorization allowed the FBI to challenge instructions to take away the malware from the contaminated gadgets.
How companies can defend from Flax Hurricane
The FBI recommends the next actions be taken promptly:
- Disable unused providers and ports at routers and IoT gadgets. Companies reminiscent of Common Plug And Play or file sharing providers is perhaps abused by attackers, so all providers must be disabled if not wanted.
- Community segmentation should be carried out to make sure IoT gadgets don’t pose the next danger of compromise. The precept of least privilege should be utilized in order that the gadgets can solely carry out their meant operate.
- Monitor for prime volumes of community visitors. Organizations ought to put together for irregular visitors volumes that is perhaps DDoS assaults.
- Deploy patches and updates for all working techniques, software program, and firmware. Common patching mitigates the exploitation of vulnerabilities.
- Change default gadgets’ passwords with stronger ones in order that an attacker can’t merely log in by way of default credentials.
The federal company additionally instructed that companies plan for system reboots — to take away fileless malware which may run within the reminiscence — and change end-of-life tools with supported ones.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.