Securing purposes and cloud environments has turn into paramount for enterprises worldwide. Checkmarx has built-in with Wiz to handle this vital want. This partnership brings collectively Checkmarx’s experience in utility safety with Wiz’s CNAPP resolution, providing mutual prospects a complete method to safety from the primary line of code to deployment and runtime within the cloud.
Embracing Code to Cloud is now a lot simpler
There are three pillars main this method:
- Streamlined safety posture administration – Integrating safety into each stage of the event lifecycle, providing a unified view, automated danger evaluation, and remediation steering, enhancing total safety efficacy.
- Enhanced collaboration and effectivity for growth, safety, and operations groups – Attaining clear communication by built-in workflows, and streamlined processes, by feeding developer groups proper the place they work with the knowledge they want, once they want it most.
- Combining AppSec and runtime for actionable insights and prioritized vulnerability remediation – Figuring out Kubernetes clusters, container photos, code repositories and mapping them to Checkmarx One purposes and tasks with runtime information to raised danger administration and prioritize vital vulnerabilities successfully.
Understanding the Integration
The combination between Checkmarx and Wiz helps ship extra actionable insights and prioritizes vulnerability remediation to our mutual prospects. Checkmarx One correlates Wiz’s cloud asset stock and community publicity findings, with utility safety outcomes similar to code repositories, and vulnerabilities. This gives organizations with the context wanted to prioritize vulnerability remediation, based mostly on what is definitely exploitable within the operating utility. This method reduces the noise generated by non-critical vulnerabilities by as much as 90% and permits prospects to focus their sources on addressing high-impact safety points.
This integration implements a “Shift Left, Shield Right” technique, extending the Checkmarx One providing by including runtime info to safe each stage of the Software program Improvement Life Cycle (SDLC), facilitating collaboration between growth and safety groups. Builders can achieve entry to actionable safety insights straight inside their growth environments (IDE), enabling them to handle vulnerabilities early within the growth course of, and safety groups can leverage runtime context and cloud asset stock to offer builders with related safety info and steering. In the end, it accelerates the supply of safe purposes in a cloud-native setting.
How Checkmarx enriches AppSec findings with Wiz runtime insights
Let’s see this integration in motion.
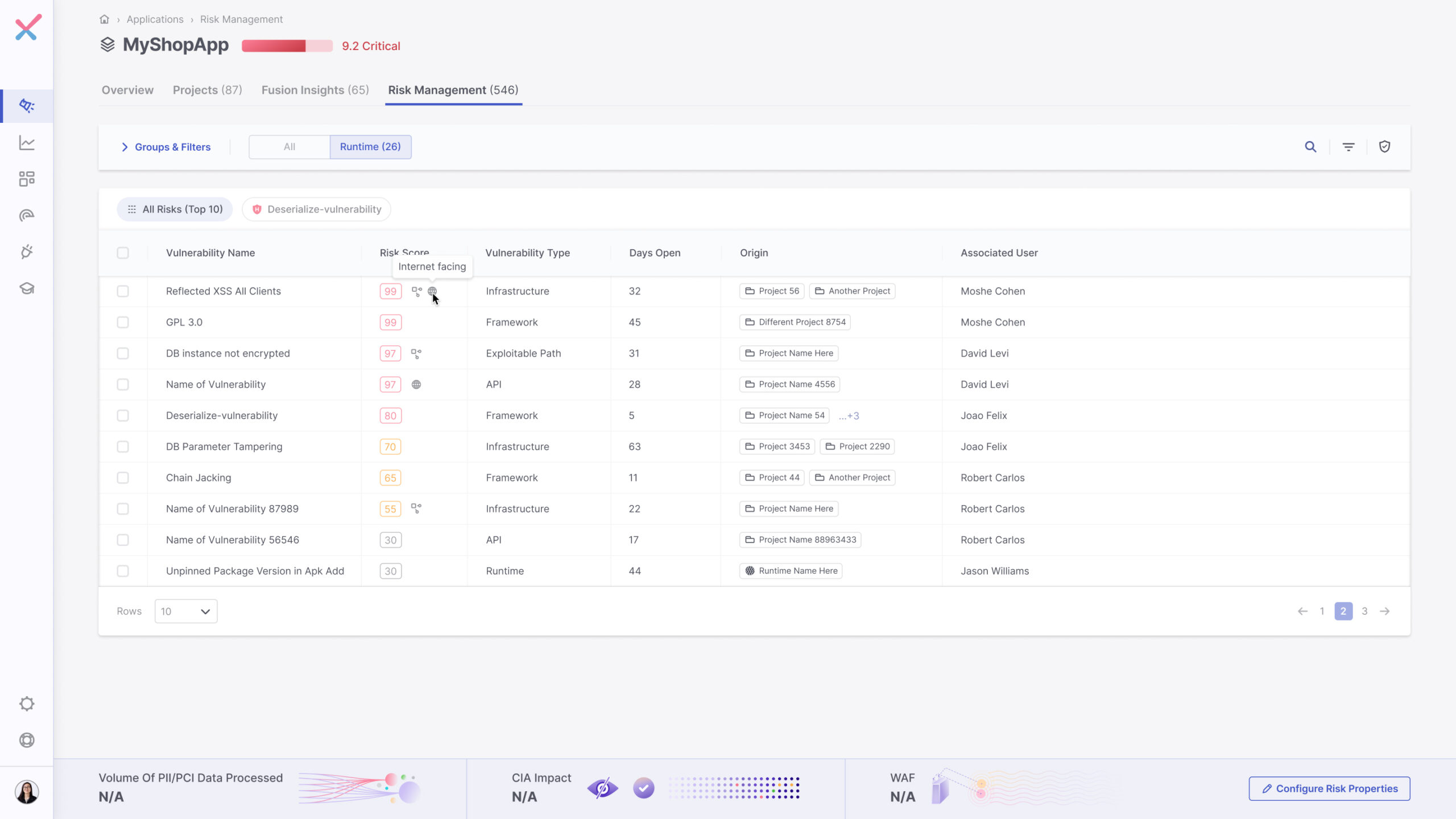
Within the Threat Administration tab, we’re capable of correlate the entire Checkmarx scanner info and see all of the vulnerabilities and their sorts. We are able to straight tie them again to their mission, and their related person. Including the runtime context, and internet-facing info from the Wiz integration permits us so as to add one other piece of the puzzle and modify the chance stage to mirror web going through vulnerabilities as riskier and prioritize them extra successfully.
Runtime context permits us to grasp whether or not vulnerabilities are uncovered to the web, which will increase the chance of exploitation. Vulnerabilities which are uncovered to the web are prioritized attributable to their elevated danger stage.
Let’s now take a look at the mission stage, the place Checkmarx One connects all of the dots. We’re capable of see all of the constructing blocks of the mission, code repos, and packages used throughout the mission, together with: once they have been scanned, what number of vulnerabilities they’ve, the chance stage and the runtime context. This permits us to raised prioritize the chance and escalate it as wanted.
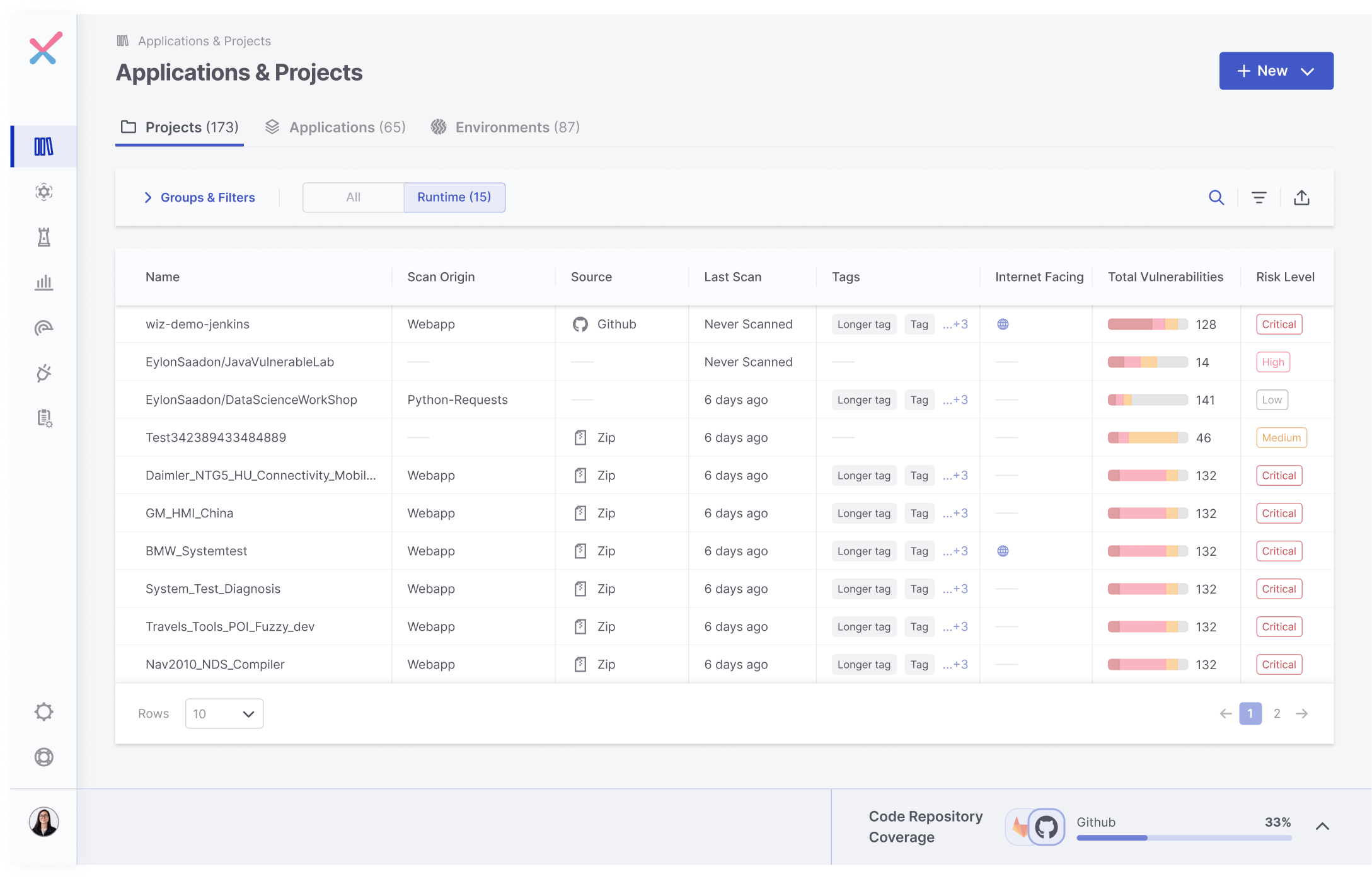
The combination between Checkmarx and Wiz permits organizations to attach all of the shifting elements within the growth life cycle from code to deployment, gaining visibility into vulnerabilities which are web going through, and prioritize them effectively. Organizations then can navigate the complexities of recent cloud environments securely, with streamlined safety posture administration, actionable insights, and enhanced collaboration, mutual prospects can successfully mitigate dangers and speed up their cloud journey with confidence.
If you happen to want to begin gathering runtime insights and see the magic occur Request a Demo, to get began.