Censys uncovers the hidden infrastructure of Fox Kitten, an Iranian cyberespionage group. It reveals distinctive patterns, potential new IOCs, and actionable suggestions to guard your group from Fox Kitten assaults.
Censys, a risk looking and assault floor administration platform has launched new particulars relating to the infrastructure of the Iranian cyberespionage group known as Fox Kitten utilizing knowledge from a joint Cybersecurity Advisory (CSA) by the FBI, CISA, and DC3. Censys recognized a major variety of further hosts that possible belong to the Fox Kitten infrastructure, increasing the scope of the risk.
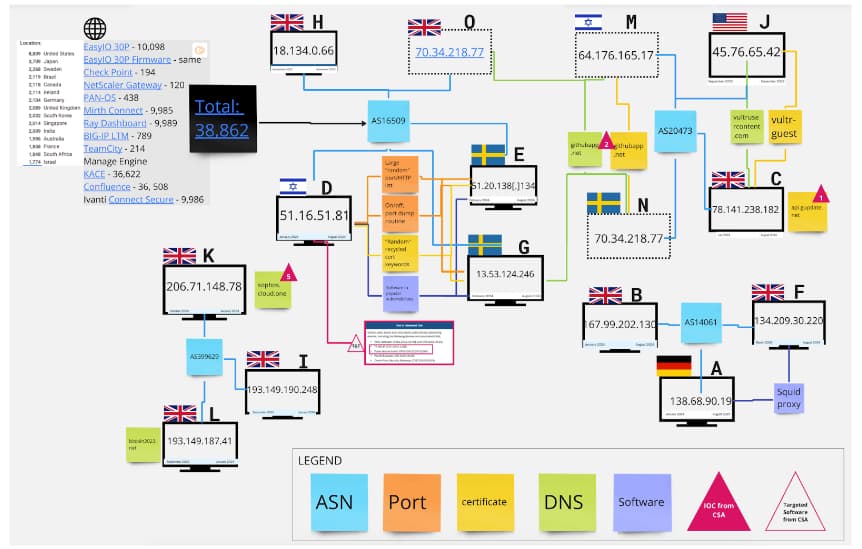
In its report, shared with Hackread.com forward of its publication on Wednesday, Censys illuminated the distinctive patterns and probably new indicators of compromise utilized by Fox Kitten, which is understood for focusing on organizations worldwide.
Utilizing these patterns, Censys might discover beforehand undiscovered energetic hosts that boasted matching patterns and Autonomous Techniques (ASs) reminiscent of Hosts D, E, and G, which may very well be a part of the identical infrastructure and could also be utilized in future assaults. Matching area IOCs had been used to establish Host G, and matching ASs had been used to establish Hosts J & C.
The information was analyzed utilizing strategies like Host Profiling, Sample Recognition, Hyperlink Evaluation, and Historic Evaluation. Host profiling includes analyzing particular person hosts’ traits, sample recognition identifies recurring patterns, hyperlink evaluation examines relationships between infrastructure components, and historic evaluation compares present knowledge with historic information to establish developments.
Additional probing revealed that the attackers used numerous strategies to obfuscate their infrastructure, reminiscent of utilizing dynamic IP addresses, distributing infrastructure throughout a number of Autonomous Techniques (ASNs), and utilizing deceptive certificates names to disguise malicious exercise.
Censys discovered two area IOCs (api.gupdate.web and githubapp.web) on energetic IPs not listed within the CSA. Some area IOCs had been discovered on Fox Kitten IPs earlier than or after the CSA timeframe. All area IOCs had been present in 64 legitimate certificates, requiring additional monitoring.
Additional analysis revealed commonalities reminiscent of geolocation in London, Stockholm, Frankfurt, Tel Aviv, and Los Angeles, shared Autonomous Techniques (AS) numbers, distinctive patterns in Hosts D, E, and G, timeframe discrepancies on some hosts outdoors the CSA timeframe, and 38,862 further probably malicious hosts with related traits. These findings counsel a honeypot-like design and a possible connection between the hosts.
By delving deeper into the Fox Kitten infrastructure, Censys has offered helpful insights into the group’s operations and ways. These patterns and commonalities can be utilized to establish different energetic hosts and certificates which may be a part of the identical Fox Kitten infrastructure.
Defenders can use IOCs and identified intervals of nefarious exercise to check host and certificates profiles earlier than, throughout, and after reported assaults, conduct dynamic searches throughout public scan datasets like Censys to look at how threats might arrange new infrastructure, and keep forward of risk actors.
RELATED TOPICS
- Iranian State Hackers Associate Up for Giant-Scale Assaults, Report
- Iran’s MuddyWater Hits Saudis and Israelis with BugSleep Backdoor
- Iranian Hackers Staff Up with Ransomware Gangs in Assaults on US
- Iran’s Peach Sandstorm Deploy FalseFont Backdoor in Protection Sector
- Iran’s Mint Sandstorm APT Hits Universities with Hamas-Israel Phishing