The Bumblebee malware loader has been noticed in new assaults just lately, greater than 4 months after Europol disrupted it throughout ‘Operation Endgame’ in Could.
Believed to be the creation of TrickBot builders, the malware emerged in 2022 as a alternative for the BazarLoader backdoor to supply ransomware menace actors entry to sufferer networks.
Bumblebee sometimes achieves an infection through phishing, malvertising, and web optimization poisoning that promoted numerous software program (e.g. Zooom, Cisco AnyConnect, ChatGPT, and Citrix Workspace).
Among the many payloads sometimes delivered by Bumblebee are Cobalt Strike beacons, information-stealing malware, and numerous ransomware strains.
In Could, a world regulation enforcement operation codenamed ‘Operation Endgame’ seized over 100 servers supporting the a number of malware loader operations, together with IcedID, Pikabot, Trickbot, Bumblebee, Smokeloader, and SystemBC.
Ever since, Bumblebee went silent. Nevertheless, researchers at cybersecurity firm Netskope noticed new Bumblebee exercise tied to the malware, which might point out a resurgence.
Newest Bumblebee assault chain
The newest Bumblebee assault chain begins with a phishing e-mail that lures the sufferer to obtain a malicious ZIP archive.
The compressed file comprises a .LNK shortcut named Report-41952.lnk, which triggers PowerShell to obtain a malicious .MSI file (y.msi) disguised as a professional NVIDIA driver replace or Midjourney installer from a distant server.
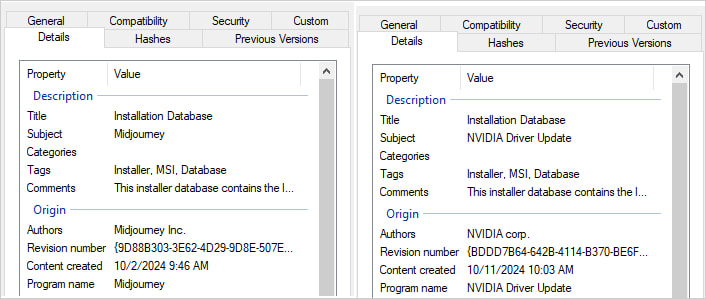
Supply: Netskope
The MSI file is then executed silently utilizing msiexec.exe with the /qn possibility, which ensures that the method runs with none consumer interplay.
To keep away from spawning new processes, which is noisier, the malware makes use of the SelfReg desk throughout the MSI construction, which instructs msiexec.exe to load the DLL into its personal handle house and to invoke its DllRegisterServer perform.
As soon as the DLL is loaded and executed, the malware’s unpacking course of begins, resulting in the deployment of Bumblebee in reminiscence.
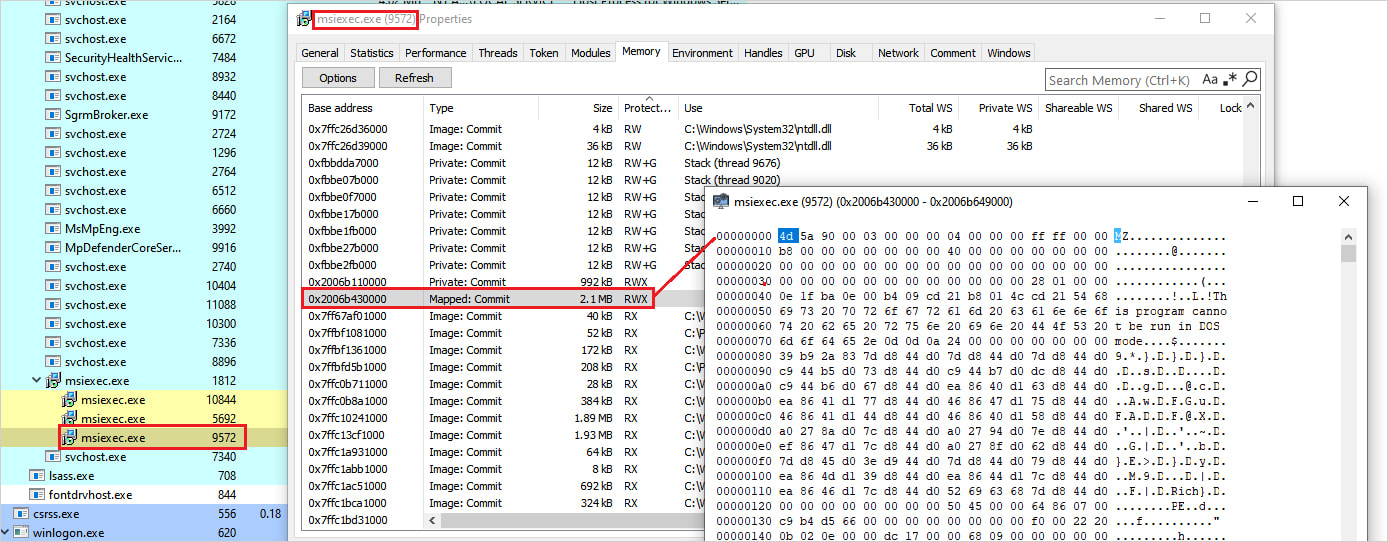
Supply: Netskope
Netskope feedback that the Bumblebee payload carries its signature inner DLL and exported features naming scheme, in addition to configuration extraction mechanisms seen in previous variants.
The RC4 key that decrypts its configuration in the latest assaults makes use of the “NEW_BLACK” string, whereas there are two marketing campaign IDs, particularly “msi” and “lnk001.”
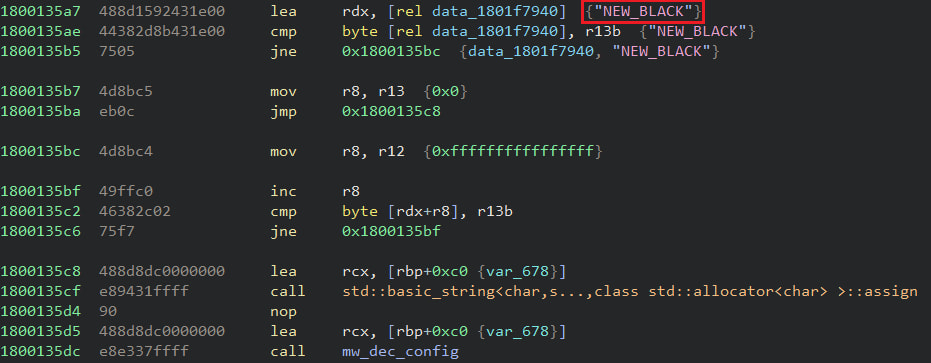
Supply: Netskope
Netskope did not present any information on the payloads that Bumblebee dropped or the dimensions of the marketing campaign however the report serves as a warning of early indicators of a doable resurgence.
The entire lists of the symptoms of compromise is accessible on this GitHub repository.
