China’s cybersecurity consultants over the previous decade have advanced from hesitant individuals in international capture-the-flag competitions, exploit contests, and bug bounty applications to dominant gamers in these arenas — and the Chinese language authorities is making use of these spoils towards stronger cyber-offensive capabilities for the nation.
In 2014, for instance, Eager Crew was the only Chinese language hacking group to take residence a prize — scoring 13% of the purse — from the Pwn2Own exploit contest. However by 2017, seven China-based groups collected 79% of the prize cash from the competition, in line with knowledge from the report, “From Vegas to Chengdu Hacking Contests, Bug Bounties, and China’s Offensive Cyber Ecosystem,” printed final week. The next 12 months, China banned participation in Western contests, gauging the vulnerability info too essential to nationwide safety.
Its civilian hackers have instantly benefited China’s cyber-offensive applications and are one instance of the success of China’s cybersecurity pipeline, which the federal government created by way of its requirement that every one vulnerabilities be instantly reported to authorities authorities, says Eugenio Benincasa, senior researcher on the Middle for Safety Research (CSS) at ETH Zurich, and the writer of the report.
“By strategically positioning itself as the final recipient in the vulnerability disclosure processes of civilian researchers, the Chinese government leverages its civilian vulnerability researchers, among the best globally, on a large scale and at no cost,” he says.
The open supply intelligence report comes as the US, Australia, Japan, South Korea, and different nations within the Asia-Pacific area have struggled to enhance cyber defenses in opposition to Chinese language advance persistent risk (APT) teams. Earlier this 12 months, high-profile US authorities officers warned that China was compromising important infrastructure to pre-position its army hackers for future conflicts. And, within the just lately uncovered “Operation Crimson Palace,” three totally different risk groups in China performed coordinated assaults in opposition to a Southeast Asia authorities company.
A Strong Cyber Pipeline
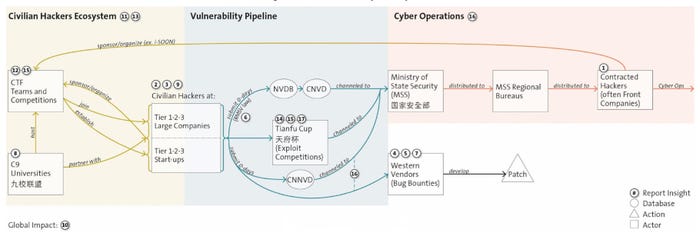
Beginning with college capture-the-flag competitions and ending with exploits that allow army cyber operations, China’s pipeline for coaching civilian hackers highlights the advantages of the nation’s deal with sensible cybersecurity. China’s cyber-offensive functionality has additionally considerably benefited from the enforcement of its vulnerability disclosure rule, the Laws on the Administration of Safety Vulnerabilities in Community Merchandise (RMSV). Each applications are a part of China’s general Army-Civil Fusion (MCF) initiative.
Stream chart displaying the pipeline for cybersecurity experience and vulnerability info. Supply: ETH Zurich’s “From Vegas to Chengdu Hacking Contests, Bug Bounties, and China’s Offensive Cyber Ecosystem” paper
Focusing its burgeoning numbers of technical graduates on discovering vulnerabilities helps amplify its offensive capabilities, says Chris Wysopal, chief expertise officer at software program safety agency Veracode.
“There is a scale difference there. … They have a large number of technical graduates, and that is being harnessed to find vulnerabilities in [Western products, such as] Google Android,” he says. “This shows that the incentives are working in their favor, and there’s evidence of that.”
Two teams of hackers exist inside China’s cyber-offensive ecosystems. The primary group consists of vulnerability researchers and offensive safety specialists who’ve distinguished themselves by competing in bug bounty applications and hacking contests, such because the Pwn2Own contest and the Tianfu Cup, which was established as a China-based different to Pwn2Own.
The second group consists of the contracted or skilled hackers who weaponize vulnerabilities to be used in assaults on particular targets. Exploits developed by the primary group have typically been utilized by the second, a truth mentioned within the iSoon leak earlier this 12 months.
Up to now, vulnerability analysis groups have been sometimes related to technical teams at giant corporations, resembling Qihoo 360, which has at the very least 19 groups; the Ant Group, which hosts 9 groups; and Tencent, which has at the very least seven analysis teams. At the moment, the researchers typically are a part of boutique cybersecurity corporations.
China’s civilian hackers initially obtained coaching by collaborating in Western capture-the-flag contests and exploit-development competitions, resembling Pwn2Own, in addition to bug bounty applications. China now has home variations of most of those initiatives and applications, typically with the monetary backing of top-tier nationwide technical universities.
Cybersecurity Superstars
A handful of researchers have made vital contributions to China’s applications, highlighting China’s reliance on a small group of researchers, in line with the report.
Greater than 50% of Google Android vulnerabilities, for instance, are credited to Qihoo 360’s Safety Response Middle (360 SRC), naming Han Zinuo as one of many contributors. When Zinuo moved to cybersecurity agency Oppo, 360 SRC’s submissions dropped and Oppo’s elevated, the analysis paper acknowledged. Equally, one other researcher, Yuki Chen, accounted for 68% of Qihoo 360’s Vulcan researcher group’s submissions to Microsoft, and when he moved to boutique agency Cyber Kunlun in 2020, the previous agency noticed a big drop in vulnerabilities to Microsoft’s bug bounty program, whereas the latter noticed a surge.
General, the variety of vulnerabilities reported by Chinese language corporations to the massive three US software program corporations — Apple, Google, and Microsoft — declined beginning in 2020. Whereas this might recommend that Chinese language corporations have been not reporting the vulnerabilities they found, it additionally coincided with growing sanctions from the US, such because the blacklisting of Qihoo 360 in Might 2020 attributable to its hyperlinks to the Chinese language army, the report acknowledged.
“This decrease [in vulnerability reports has] raised concerns about the potential loss of a significant channel for vulnerability reporting within the global ecosystem,” the report mentioned.
Downsides for Protection
As a result of Chinese language groups have curtailed their participation in Western hacking competitions, they’ve arguably made the competitions much less efficient as a defensive technique. In 2022 and 2023, for instance, no groups tried to hack both Apple’s iPhone or Google’s Pixel on the Pwn2Own competitors — that was the primary time in 15 years for Apple’s iPhone — indicating that China now considers any exploits its consultants discover as too beneficial to exhibit publicly.
“The notable absence of Chinese hacking teams that specialized in targeting these devices explains this break far better than assuming that the iPhone and Pixel have become unbreachable,” the analysis paper acknowledged. “Concurrently, these vulnerabilities are highly likely evaluated by China’s security agencies for potential use in cyber malicious operations.”
Even displaying such exploits with none accompanying particulars runs the chance of directing attackers to rediscover vulnerabilities, says Dustin Childs, head of risk consciousness for the Zero Day Initiative at Pattern Micro, which runs the Pwn2Own competitors.
“They have already been demonstrated onstage, so threat actors know they aren’t wasting their time reversing a patch for some that may end up non-exploitable,” he says. “This is why we invite vendors to participate in the contest.”
Personal organizations that deal in exploits act as a bellwether for the vulnerability market. Exploit vendor Zerodium at the moment presents a $2.5 million payday for any hacker that finds a zero-click exploit chain for Google Android and $2 million for the same assault on iOS.
China’s Personal Hacking Competitions
In the meantime, China is additional divorcing itself from the worldwide info infrastructure, transferring its infrastructure to domestically developed expertise. Unsurprisingly, its cybersecurity pipeline is following swimsuit, with some main exploit competitions focusing more and more on Chinese language merchandise.
In the long run, China must comply with two paths, Benincasa says.
“We are observing an interesting shift in China’s hacking competitions toward focusing more on their own products, while at the same time maintaining a strong interest in Western ones,” he says, including, “China’s strategic intent [is] to maintain a presence in international products for offensive purposes, given the expertise of its hackers in targeting Western products, while simultaneously focusing on domestic products for defensive purposes as it gradually reduces reliance on US vendors.”