Safety flaws in Telit Cinterion mobile modems, broadly utilized in sectors together with industrial, healthcare, and telecommunications, may enable distant attackers to execute arbitrary code by way of SMS.
A set of eight separate points, seven of them with identifiers CVE-2023-47610 by way of CVE-2023-47616 and one other that has but to be registered, have been disclosed final November by safety researchers at Kaspersky’s ICS CERT division.
Earlier than publishing the safety points, the safety firm had reported them to the seller in February 2023.
On Saturday, on the OffensiveCon convention in Berlin, Alexander Kozlov and Sergey Anufrienko shall be offering low stage technical particulars concerning the safety points and the way a risk actor may exploit them to take management of susceptible Telit Cinterion units.
SMS to machine takeover
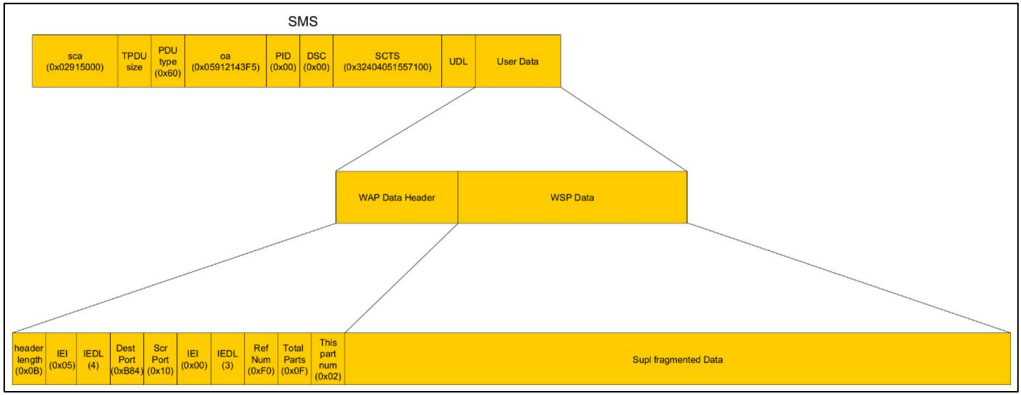
Probably the most extreme of the vulnerabilities is CVE-2023-47610, a heap overflow drawback that impacts the modem’s Consumer Airplane Location (SUPL) message handlers.
Kaspersky, in collaboration with Telit and primarily based on a radical evaluation of the technical particulars, assigned it a severity rating of 8.8 out of the utmost 10. Nonetheless, NIST’s evaluation is that the difficulty has vital affect and acquired a severity rating of 9.8.
Attackers exploiting the flaw by way of specifically crafted SMS messages may set off the vulnerability and execute arbitrary code remotely on the modem with out requiring authentication.
In a report shared with BleepingComputer, the researchers say that the SMS messaging interface is current on all modems and that accessing it’s potential if the subscriber variety of the goal modem within the mobile operator’s community is thought.
They clarify that operator restrictions could generally forestall sending binary SMS however a pretend base station ought to bypass this limitation.
“According to the transmission protocol, the ULPSizeFromPacket and wapTpduLen variables are calculated independently,” the researchers word within the technical report.
“These variables are interrelated only in the part of WAP messages reception algorithm: the sum of the sizes of all received WAP messages in a UPL message must not exceed ULPSizeFromPacket.”
“But the algorithm used to receive WAP messages does not check it. Therefore, a received WAP packet of size wapTpduLen will be copied to a buffer of size ULPSizeFromPacket.”
Supply: Kaspersky
By exploiting CVE-2023-47610 to execute arbitrary code by way of SMS, an attacker can get deep-level entry to the modem’s working system.
“This access also facilitates the manipulation of RAM and flash memory, increasing the potential to seize complete control over the modem’s functionalities—all without authentication or requiring physical access to the device” – Kaspersky
Though the remainder of the vulnerabilities that Kaspersky researchers found acquired a decrease severity rating, they can be utilized to compromise the integrity of MIDlets – Java-based purposes with varied capabilities.
In response to Kaspersky, an attacker may obtain code execution with elevated privileges (producer stage) by circumventing digital signature checks (CVE-2023-47611). This could pose a risk not simply to information confidentiality and integrity but in addition to broader community safety and machine integrity.
Though the analysis focused the Cinterion EHS5-E collection modem, as a result of different merchandise from the seller have comparable software program and {hardware} structure further variants are additionally impacted:
- Cinterion BGS5
- Cinterion EHS5/6/7
- Cinterion PDS5/6/8
- Cinterion ELS61/81
- Cinterion PLS62
Telit fastened among the disclosed vulnerabilities however some stay unpatched, Kaspersky informed BleepingComputer.
“The vulnerabilities we found, coupled with the widespread deployment of these devices in various sectors, highlight the potential for extensive global disruption,” says Evgeny Goncharov, head of Kaspersky ICS CERT.
Goncharov notes that as a result of the modems are embedded in different options, it’s a problem to find out which merchandise are impacted.
The safety firm has some suggestions to mitigate the threats, which is a lot of the occasions potential by working with the telecom operator. One technique is to disable SMS sending to impacted units and utilizing a securely configured non-public APN.
Kaspersky additionally recommends imposing utility signature verification to stop the set up of untrusted MIDIets on the modem and take measures to stop unauthorized bodily entry to the units.
