The Black Basta ransomware operation is suspected of exploiting a Home windows privilege escalation vulnerability (CVE-2024-26169) as a zero-day earlier than a repair was made accessible.
The flaw is a high-severity subject (CVSS v3.1: 7.8) within the Home windows Error Reporting Service, permitting attackers to raise their privileges to SYSTEM.
Microsoft mounted the flaw on March 12, 2024, by way of its month-to-month Patch Tuesday updates, whereas its standing on the vendor’s web page exhibits no energetic exploitation.
A report by Symantec says that CVE-2024-26169 has been actively exploited by the Cardinal cybercrime group (Storm-1811, UNC4394), the operators of the Black Basta gang, noting that there is a good probability it was leveraged as a zero-day.
Exploiting CVE-2024-26169
Symantec investigated an tried ransomware assault the place an exploit instrument for CVE-2024-26169 was deployed following an preliminary an infection by the DarkGate loader, which Black Basta has been utilizing for the reason that QakBot takedown.
The analysts consider the attackers are linked to Black Basta as a result of they used batch scripts that masquerade as software program updates designed to run malicious instructions and set up persistence on compromised programs, a standard tactic for this group.
The noticed exploit instrument leveraged the truth that the Home windows file werkernel.sys makes use of a null safety descriptor when creating registry keys.
The instrument exploits this to create a registry key (HKLMSoftwareMicrosoftWindows NTCurrentVersionImage File Execution OptionsWerFault.exe) and units the “Debugger” worth to its personal executable pathname, permitting it to launch a shell with SYSTEM privileges.
Beneath is an indication of BleepingComputer testing the exploit on a Home windows 11 machine that solely has the Home windows safety updates from February put in, earlier than Microsoft mounted the flaw in March.
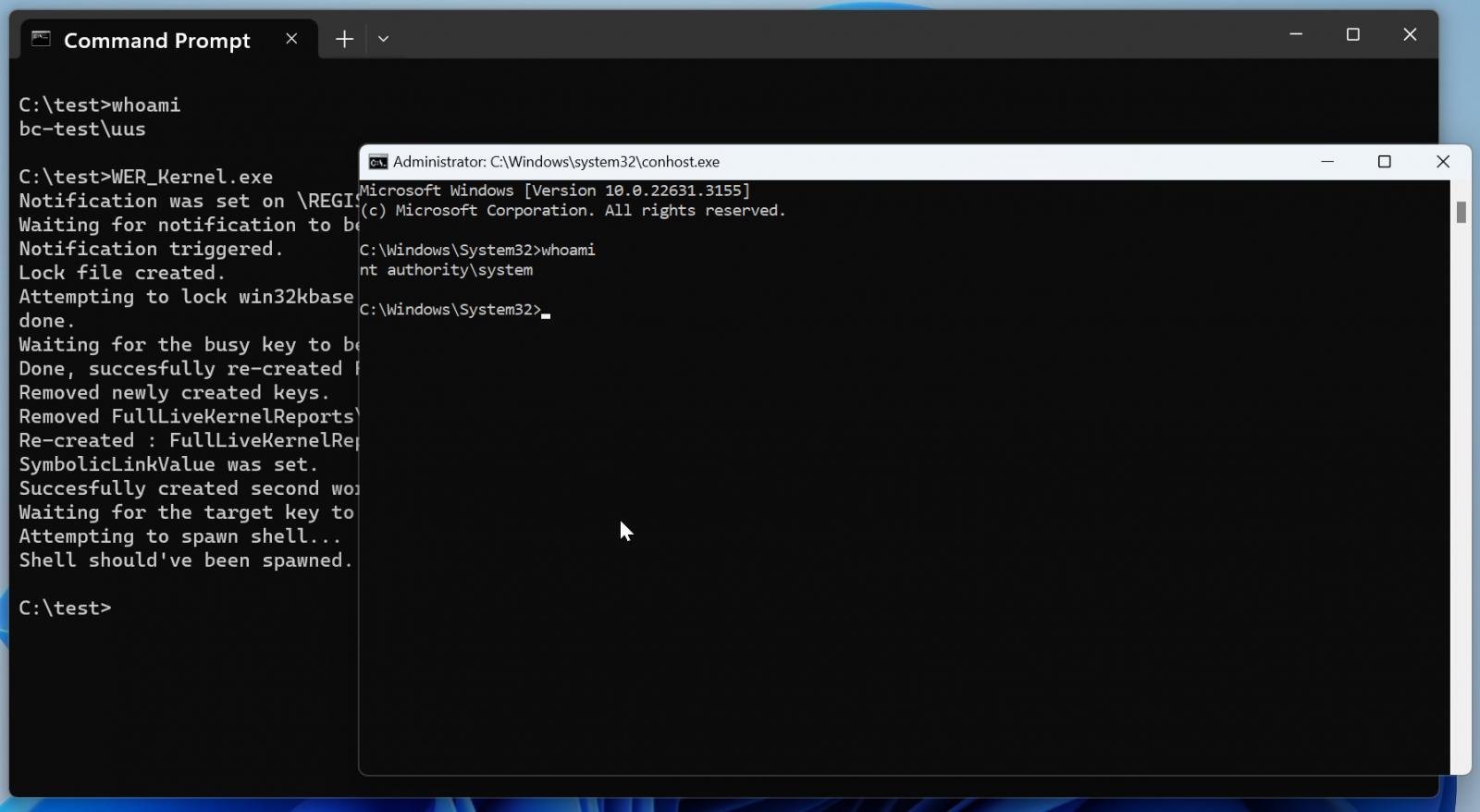
Supply: BleepingComputer
An enchanting facet of Symantec’s findings is that one variant of the exploit instrument has a compilation timestamp dated February 27, 2024, whereas a second pattern was constructed even earlier, on December 18, 2023.
Which means that Black Basta had a working exploit instrument between 14 and 85 days earlier than Microsoft finally pushed a repair for the privilege elevation subject.
Whereas timestamps in moveable executables could be modified, as Symantec admits, making the discovering inconclusive relating to whether or not zero-day exploitation occurred, there seems to be little motivation for the attackers to falsify the timestamps, so this situation is unlikely.
Black Basta, a ransomware operation believed to be linked to the now-defunct Conti cybercrime syndicate, has beforehand demonstrated experience in abusing Home windows instruments and an in-depth understanding of the platform.
A Might 2024 advisory from CISA and the FBI highlighted Black Basta’s high-volume exercise, holding its associates answerable for 500 breaches since April 2022, the time of its launch.
Blockchain analytics agency Elliptic reported in November 2023 that the ransomware operation had remodeled $100 million in ransom funds.
To mitigate Black Basta’s use of this vulnerability, it’s important to use the newest Home windows safety replace and comply with the pointers shared by CISA.
