Cybersecurity agency Fortinet alerts customers of a phishing rip-off marketing campaign distributing the Byakugan malware. This malware steals delicate info and grants attackers distant entry to contaminated Home windows units.
Malware Present in PDF File:
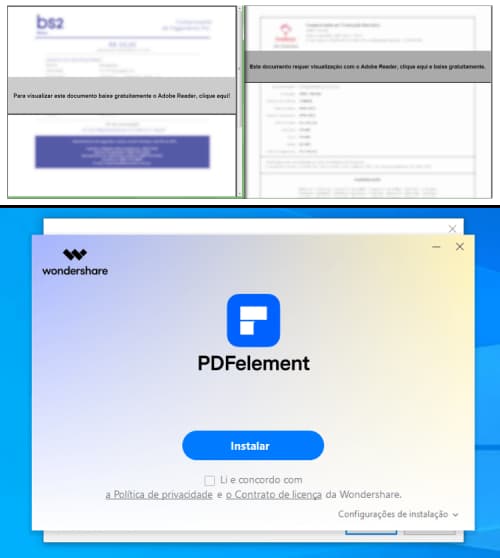
In January 2024, FortiGuard Labs found a PDF file in Portuguese language distributing Byakugan, a multi-functional malware. Researchers discovered a blurred desk within the PDF and directions for the victims to click on a malicious hyperlink to view the content material.
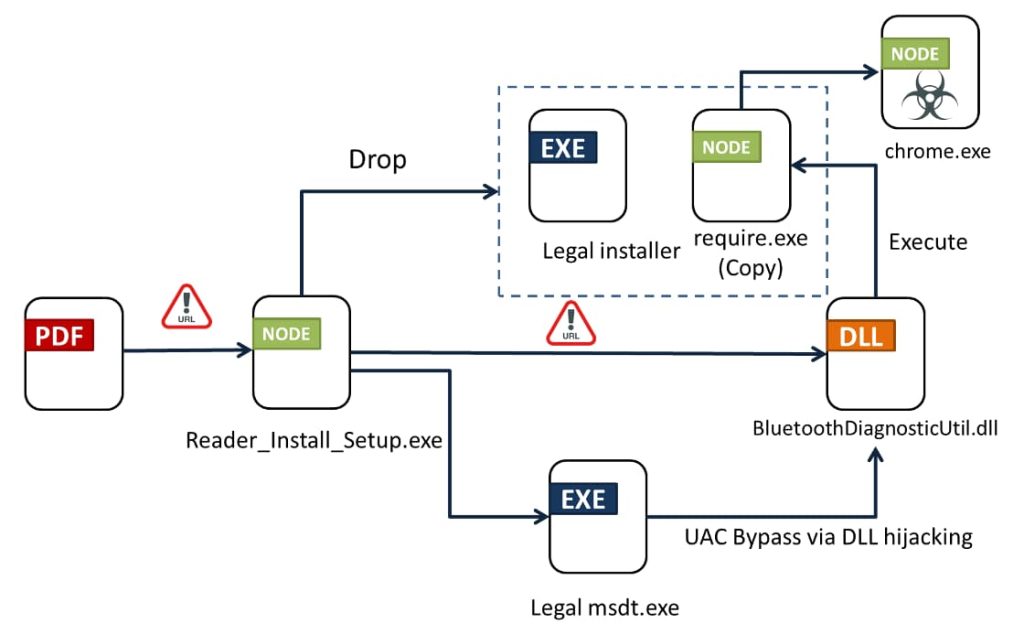
As soon as clicked, the downloader drops a file titled require.exe, which is its copy. Then a clear installer is downloaded to the temp folder adopted by a DLL, which is executed through DLL-hijacking to run require.exe to obtain the primary module.
The downloader, named “require.exe” and positioned within the temp folder, executes the copy and never the Reader_Install_Setup.exe, and displays completely different behaviour in each information. Byakugan’s predominant module is downloaded from thinkforce.com, a C2 server which will additionally function an attacker’s management panel, with a login web page on port 8080.
AhnLab SEcurity Intelligence Middle (ASEC) additionally found an Infostealer disguised as an Adobe Reader installer by a faux PDF file in Portuguese, urging customers to obtain Adobe Reader, which led to the execution of a malicious file Reader_Install_Setup.exe.
It additional creates two malicious information and runs a Home windows system file, msdt.exe as an administrator, loading the malicious BluetoothDiagnosticUtil.dll and loading the malicious DLL file. The menace actor can bypass Person Account Management (UAC) through DLL hijacking.
Byakugan Malware Key Options
Byakugan is a node.js-based malware that makes use of OBS Studio to watch the goal’s desktop and carry out varied features. It has a number of libraries, together with a display screen monitor, miner, keylogger, file manipulation, and browser info stealer.
Furthermore, Byakugan can select between mining with CPU or GPU to stop system overloading and downloads from standard miners like Xmrig, t-rex, and NBMiner. It additionally shops knowledge within the kl folder and may steal details about “cookies, credit cards, downloads, and auto-filled profiles,” researchers wrote.
Byakugan additionally has anti-analysis options, equivalent to pretending to be a reminiscence supervisor and setting the trail to the Home windows Defender’s exclusion path. Moreover, it drops a process scheduler configuration file into the Defender folder, enabling it to execute robotically when beginning up. Nonetheless, this newer variant doesn’t obtain the software program from its area.
The best way to Keep Secure?
Menace actors are utilizing each clear and malicious elements in malware, equivalent to Byakugan, making detection troublesome, FortiGuard researchers famous, Subsequently, to remain shielded from phishing assaults and such misleading malware, customers should be cautious with emails, and confirm sender legitimacy.
Moreover, use robust passwords and two-factor authentication, preserve software program up to date, and like putting in safety software program that may detect and block phishing emails/malware. Keep away from clicking on hyperlinks or downloading attachments from suspicious emails, and contacting the sender straight.