One of many main targets of data safety is to shield information, which in fact entails defending the sources that retailer and supply entry to that information.
Based on the NIST Cybersecurity Framework, organizations must develop and implement the essential protections to limit or mitigate the impact of a doable cybersecurity incident.
Safety must be built-in proper from the supply of the cloud structure design course of. In the present day, menace prevention and steady safety evaluation are important components of enterprise cloud technique. This text will deal with these safety mechanisms.
AWS Shared Duty Mannequin
The trendy cloud structure technique requires a shared safety mannequin, which implies that although cloud suppliers, comparable to AWS, provide appreciable benefits for safety and compliance efforts, they don’t absolve the shopper from defending their customers, purposes, information, and repair providing(s).
It’s important to grasp the shared accountability mannequin, together with which safety duties are dealt with by the cloud supplier and which duties are dealt with by you, the shopper. The workload tasks range relying on whether or not the workload is hosted on Software program as a Service (SaaS), Platform-as-a-Service (PaaS), Infrastructure-as-a-service (IaaS), or in on-premises information facilities.
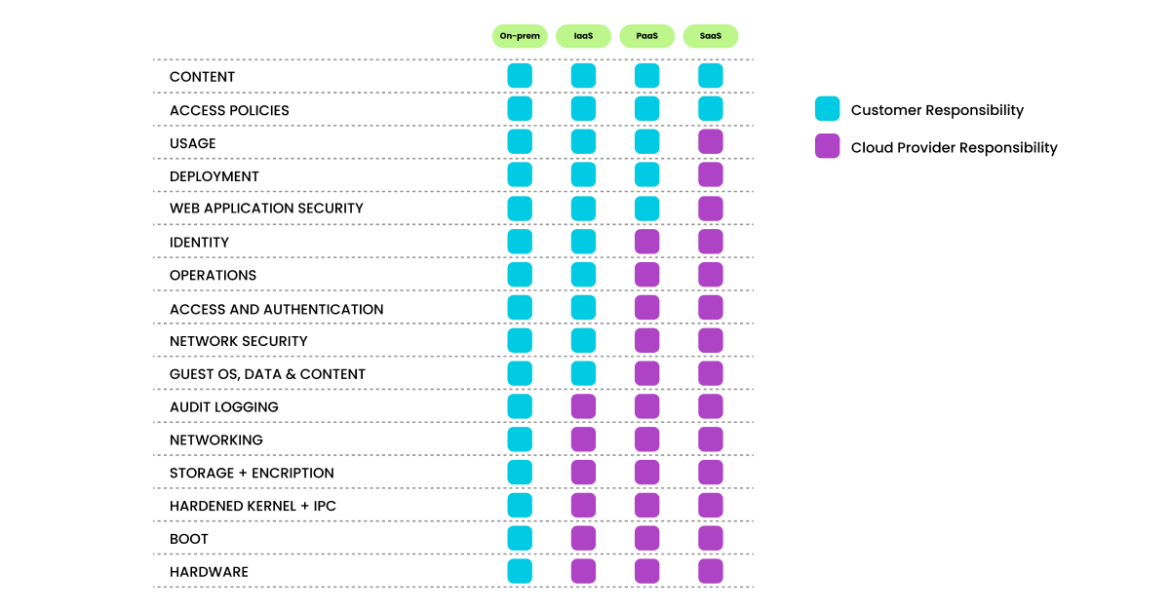
The monitoring, logging, and alerting insurance policies are necessary points of the shoppers’ accountability within the AWS shared accountability. These insurance policies allow the shoppers to enhance their possibilities of detecting malicious habits on methods and networks.
Monitoring is a crucial a part of sustaining the reliability, availability, and efficiency of AWS options. AWS supplies instruments and options that allow the shoppers to report and monitor cybersecurity-related occasions on a steady foundation throughout the AWS atmosphere.
Understanding cloud-native safety
As we coated in our weblog put up “Guess who in cloud security landscape,” about 50% of organizations acknowledge that they’ve a scarcity of inside data about cloud-native safety.
We wish to assist the reader be capable of perceive by themselves the “what and why” of every service. To take action we’ll contextualize safety providers leveraging two totally different strategies:
Safety approaches
Main ideas associated to cloud native safety take the type of a Cloud-native utility safety platform (CNAPP), which could be visualized as a mix of the next components:
- CAASM (Cyber Asset Assault Floor Administration) → Cyber asset assault floor administration. Uncover, stock, and monitor belongings (plain hosts, community units, S3 buckets, containers, and so forth.).
- Workloads (CWPP: Cloud Workload Safety Platform) → Runtime detection, system hardening, vulnerability administration, community safety, container compliance, and incident response.
- Posture and compliance (CSPM: Cloud Security Posture Administration) → Cloud controls airplane safety by verifying the static configuration, finest practices, frameworks, and benchmarks.
- Knowledge safety and DSPM (Knowledge Safety Posture Administration) → Knowledge safety and information consciousness methods allow enhanced safety of delicate information.
- Identification dangers (CIEM: Cloud Infrastructure Entitlement Administration) → Monitor and discover gaps in cloud permissions and insurance policies aimed to implement least privilege entry.
- Different areas can match into the CNAPP area, like Utility Safety Posture Administration (ASPM) for instance.
There are various different classifications and layers on the safety aspect of issues, however we wish to preserve this weblog put up so simple as doable.
AWS Effectively-Architected Framework method
Earlier than going into particulars, let’s classify AWS providers into two principal teams:
- Parts with implicit safety features: Foundational providers that incorporate some safety associated traits or have a direct impression on the general safety (AWS Artifact, IAM, EC2, and so forth.).
- Express safety providers: Parts aimed to deal with safety points like vulnerabilities, threats, and danger administration (e.g. AWS Safety Hub, Amazon Guard Obligation, Amazon Inspector, Amazon Macie, and so forth.).
This text is concentrated on the specific safety parts which might be native or third-party providers that assist your group meet finest practices throughout the shared accountability mannequin. As per AWS tips, the principle safety areas we’ll talk about embrace Detection, Infrastructure safety, Knowledge safety, and Reply.
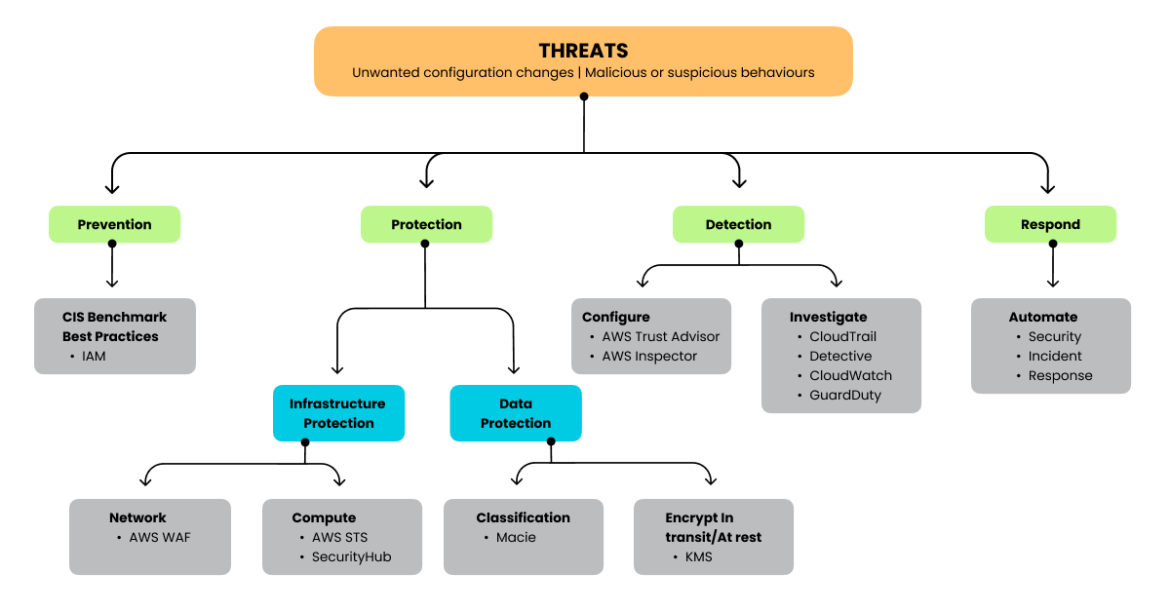
The vary of safety providers AWS presents is wealthy in choices and inter-connection prospects, though it generates some extra ranges of complexity that we are going to analyze later. Let’s take a look on the principal AWS native safety providers like AWS CloudTrail, Amazon GuardDuty, Amazon Inspector, AWS Config, AWS IAM service, AWS Safety Hub, and so forth.
Perceive AWS safety choices
After inspecting the big variety of safety instruments supplied by AWS, let’s deal with native options meant to deal with CNAPP and associated (CWPP, CSPM, CIEM) necessities utilizing the aforementioned AWS safety method as our lens:
| Service | Function | Focus | Sysdig |
| Amazon Inspector | Config detection and vulnerability administration | Appsec, CWPP, CSPM |
Extends vulnerability scanning capabilities for host cases and pictures additionally making use of runtime intelligence to supply danger highlight. Extends CSPM and Compliance options by combining dynamic and static checks into an unified expertise. |
| Amazon Guard Obligation | Cloud Security Monitoring and clever menace detection | Primarily CDR and CWPP | Wealthy OOTB algorithm and cloud safety monitoring. Deep runtime detection for workloads and cloud. Superior CWPP with multi-cloud and multi-vendor assist, together with Home windows nodes. |
| AWS Cloudtrail* | Audit logging | Allows detection | Native integration with CloudTrail |
| AWS IAM* | Identification, permissions, danger | Allows entry, CIEM | Simple utility of least privilege entry Superior CIEM, investigation, compromised identities. |
| AWS Safety Hub | Compliance and Knowledge Safety | Aggregation, CSPM, Standardization, React/Alert | Sysdig unifies Investigation and Steady Compliance for cloud and workloads with remediation capabilities |
| Amazon Macie | Monitor delicate Knowledge | DSPM | Sysdig reinforces Safe Posture and Compliance associated to information like GDPR and HITRUST |
| AWS Config* | Helps with Detection, Configuration Drifts, and Knowledge Safety | Helps with CSPM | Detect runtime threats and vulnerabilities resulting in response, remediation, and forensic evaluation |
| AWS Safety Lake | Analytics | Normalization, ingestion, long-term retention | Knowledge lakes will not be actual time, Sysdig is actual time and may feed and enrich Safety Lake information for additional investigation. |
| AWS Detective | Forensics investigation | Investigation | Superior captures, enriched cloud native context. |
* Companies marked with an asterisk will not be explicitly safe providers however have necessary implications associated to safety
Amazon Inspector
Safety and compliance for EC2 by way of vulnerability administration, configuration, community ports publicity, unsafe protocols, detection, and prioritization by severity score.
This answer is agent-based (Inspector traditional brokers have been switched with AWS Methods Supervisor brokers in Inspector v2).
Amazon Guard Obligation
This service helps to determine sudden and doubtlessly unauthorized or malicious actions like Malware, cryptomining, or assaults. GuardDuty ingests audit logs from a number of sources like CloudTrail occasion logs, VPC, EC2, S3, DNS, and EKS.
AWS Safety Hub
AWS Safety Hub supplies a complete view of the safety state of your AWS sources by ingesting actionable occasions from different sources and providers comparable to Amazon GuardDuty, Amazon Inspector, Amazon Macie, in addition to from Licensed Accomplice Options or some Open Supply Instruments. These safety alerts are standardized, aggregated, and prioritized. Actions based mostly on these findings could be triggered utilizing, as an example, Amazon Detective or Amazon CloudWatch Occasion guidelines. Moreover, Sysdig has an integration with Safety Hub.
AWS CloudTrail
AWS CloudTrail permits monitoring AWS deployments within the cloud by getting a historical past of AWS API calls to your account, together with API calls made through the use of the AWS Administration Console, the AWS SDKs, the command line instruments, and higher-level AWS providers. Sysdig consumes this service, amongst others, as a part of cloud safety and compliance steady suggestions.
AWS IAM
Safety in AWS begins with the inspiration of Identification, which is managed by the Identification and Entry Administration (IAM) service with fine-grained entry management insurance policies.
Amazon Macie
Amazon Macie is a totally managed information safety and information privateness service. Macie makes use of machine studying and sample matching to assist uncover, monitor, and shield your delicate information in Amazon S3 and obtain alerts about delicate information, uncovered info, and mental property. Mixed with different instruments, it might assist to fulfill rules like HIPAA, GDPR, and so forth.
AWS Config
AWS Config supplies an in depth view of the sources related together with your AWS account, together with how they’re configured, how they’re associated to at least one one other, and the way the configurations and their relationships have modified over time. It isn’t explicitly associated to safety however it has too many safety implications to not be listed on this article — steady monitoring/audit configuration, change administration, steady evaluation, and operational troubleshooting.
AWS Safety Lake
Launched as a totally managed information lake for safety, AWS Safety Lake centralizes safety information and makes use of the Open Cybersecurity Schema Framework (OCSF) for normalization. Sysdig can ahead findings to AWS Safety Lake.
The best way to safe and complement AWS providers with Sysdig
Sysdig enforces least privilege
Identification is (nearly) the brand new perimeter within the cloud.
Privilege escalation is a standard method attackers use to realize unauthorized entry to methods inside a safety perimeter. Insufficient safety controls, or failure to observe the precept of least privilege, with customers having extra privileges than they really want are simply a few of the methods they discover the “doors wide open” to cloud environments.
In different instances, attackers exploit serverless providers just like the Lambda perform, utilizing particular methods to raise privileges. As well as, it’s doable to have an effect on software program vulnerabilities to beat an working system’s permissions mechanism after which transfer to your infrastructure utilizing the Lateral Motion method.
Though we discover a good quantity of sources in AWS round the significance of making use of the Precept of Least Privilege entry to cloud identities, there isn’t a simple technique to accomplish that.
We talked concerning the totally different AWS safety providers that may assist us understand the permissions granted to identities (e.g., AWS IAM), the actions (e.g., AWS Config) that may be accomplished over a useful resource (e.g., Amazon Macie), and the data associated to the exercise the human and non-human identities carry out over a each day foundation (e.g., CloudTrail). Nonetheless, all that info is unfold throughout a number of AWS service choices.
The Sysdig CIEM providing is one thing totally different.
We complement AWS service providing relating to permissions and identities with a dashboard that unifies all of the configuration, insights, and the significant info from AWS so you possibly can carry out the required duties to actually implement this least privilege entry precept.
With a CIEM dashboard, you possibly can unveil the identities not working within the group, the roles, and the serverless identities you created for a POC that had granted approach too many permissions and are not wanted.
Keep in mind, attackers are there scanning no matter hints they might discover.
Many occasions, engineers get assigned to initiatives that have been to be accomplished by yesterday. For the sake of the challenge, we could find yourself granting extra permissions than wanted. We don’t wish to be those stopping the enterprise. If we analyze the habits of that cloud identification, we discover it’s utilizing only a outlined quantity of permissions over a restricted pool of sources.
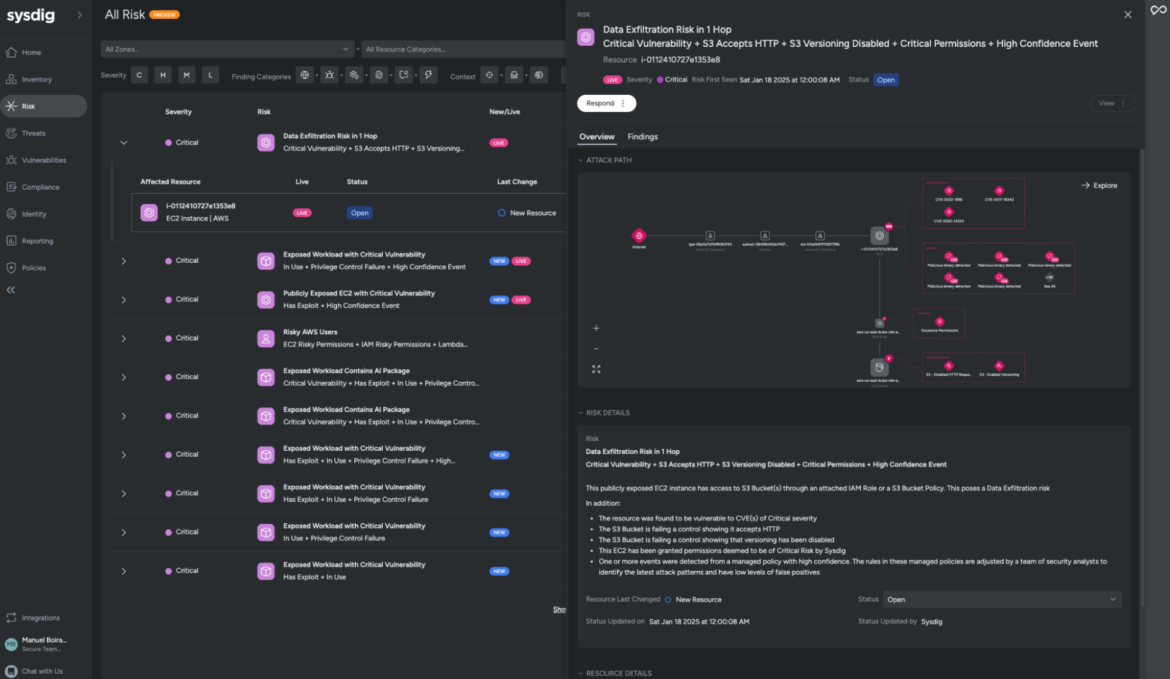
Sysdig will prevent and your crew a superb quantity of handbook investigation by way of AWS providers with auto-suggested insurance policies, analyzing what entitlements are granted versus what’s truly used/wanted.
Sysdig menace detection for cloud and containers
Amazon GuardDuty is the service AWS supplies as Risk Detection to its clients. It does an outstanding job detecting anomalies involving AWS sources like IAM entry keys, EC2 cases, S3 buckets, and Amazon EKS sources.
Sysdig is very well-known for its runtime detection capabilities, not solely round workload safety but additionally cloud safety monitoring (learn Falco for cloud for extra particulars) and its stream detection method.Sysdig Safe presents extra capabilities over Amazon GuardDuty.
Stream detection is a steady course of that collects, analyzes, and studies on information in movement. With a streaming detection course of, logs are inspected in actual time. This real-time detection lets you determine sudden adjustments to permissions and providers’ entry rights, in addition to uncommon exercise that may point out the presence of an intruder or an exfiltration of knowledge.
This fashion, Sysdig Risk Detection capabilities can now detect the identical cloud occasions as GuardDuty, together with the long-term current ones of the workload aspect like: spawning a shell in a container, writing under delicate folders, delete bash historical past…increasing the identical performance for Fargate duties since AWS launched platform model 1.4.0 of AWS Fargate.
In relation to sensible motion, relying on the dimensions of your cloud deployment, GuardDuty findings generally is a little overwhelming, You may get misplaced fairly simply with a lot info. If the crew wants to repair essentially the most important findings as quickly as doable, then you have to to filter out a few of the noise. Right here, Sysdig could be your ally.
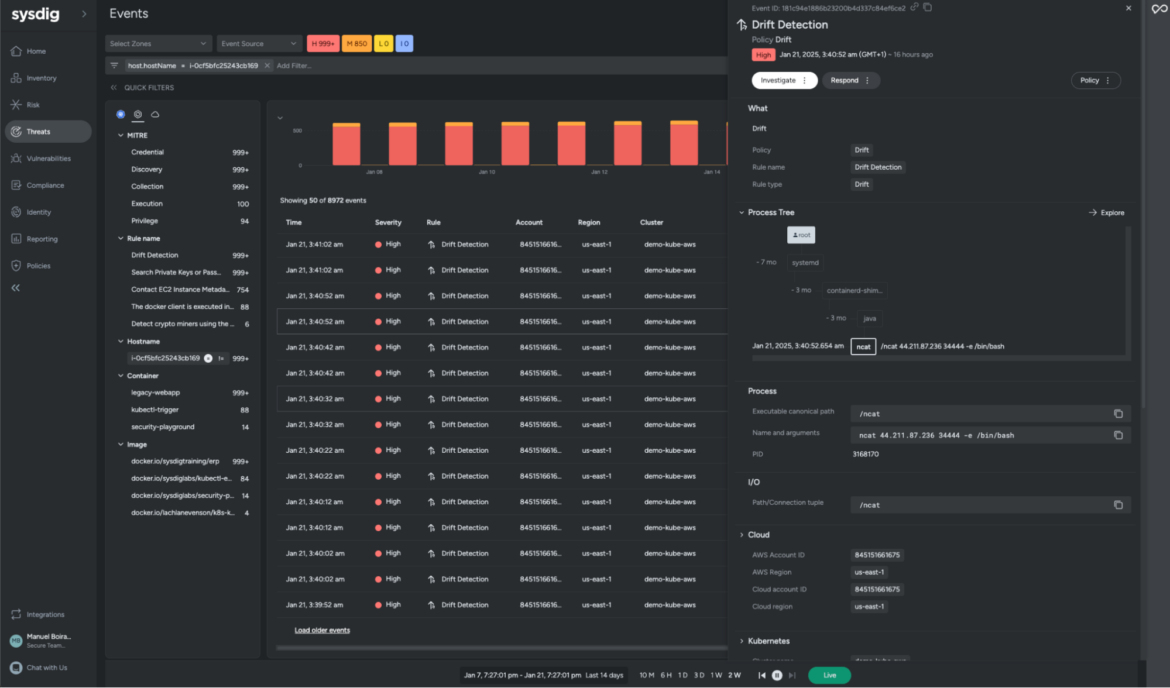
Sysdig’s menace detection engine makes use of the open supply challenge Falco below the hood, which suggests you get to make use of the Falco language to jot down guidelines and might make the most of the usage of an actual language with macros, lists, exceptions, and the Falco rule tuning to chop out undesirable noise.
Amazon GuardDuty service is completely accessible to AWS environments, which suggests you possibly can’t use the facility of its machine studying menace detection on every other cloud platform or on-prem deployment.
If you’re planning on going multi-cloud or utilizing hybrid cloud environments, Sysdig would pair properly with GuardDuty to guard your entire infrastructure and distributed workloads from a single place.
Sysdig steady Compliance/CSPM
Compliance revolves round being in accordance with established tips or specs, business led and authorities supported.
The 2 principal providers that relate to Compliance in AWS are AWS Artifact (not coated on this article) and AWS Safety Hub. However there are different providers additionally wanted to actually have steady compliance in AWS cloud: Amazon Inspector, AWS IAM, Amazon Macie, Listing Service, AWS Firewall Supervisor, AWS WAF, AWS Trusted Advisor, AWS Config, Amazon CloudWatch, AWS CloudTrail, AWS Management Tower, and extra.
In Sysdig, you will have your entire compliance controls in a single place: Posture.
There, you will discover fairly an extended record of safety compliance normal controls (SOC2, PCI, a number of NIST requirements, ISO-27001, HiTrust, HIPAA, FedRAMP, GDPR, and including extra requirements frequently) that we have now mapped for you, but additionally business finest practices that come from the CIS Benchmarks and cloud supplier recommendation, just like the AWS Effectively-Architectured Framework.
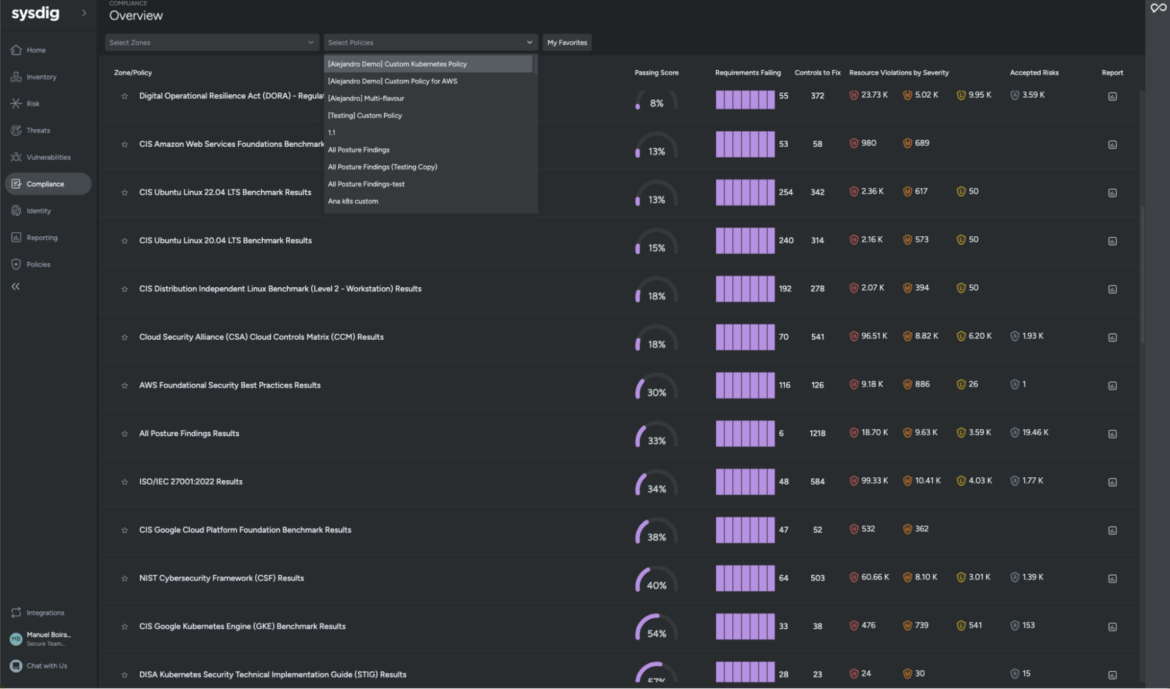
Whereas the AWS Safety Hub does an excellent job offering safety findings relating to the configuration of your cloud account and providers, it lacks deep visibility into the workloads and hybrid clouds.
Right here is the place Sysdig may help you.
Sysdig supplies an summary of your safety posture in each worlds, the general public cloud infrastructure, in addition to the workloads you will have in manufacturing (whether or not they’re on-premise or within the cloud). It is possible for you to to harden these to adjust to safety necessities, flagging violations once you haven’t configured AppArmor accurately in your cloud cases otherwise you don’t have a sudo suid set.
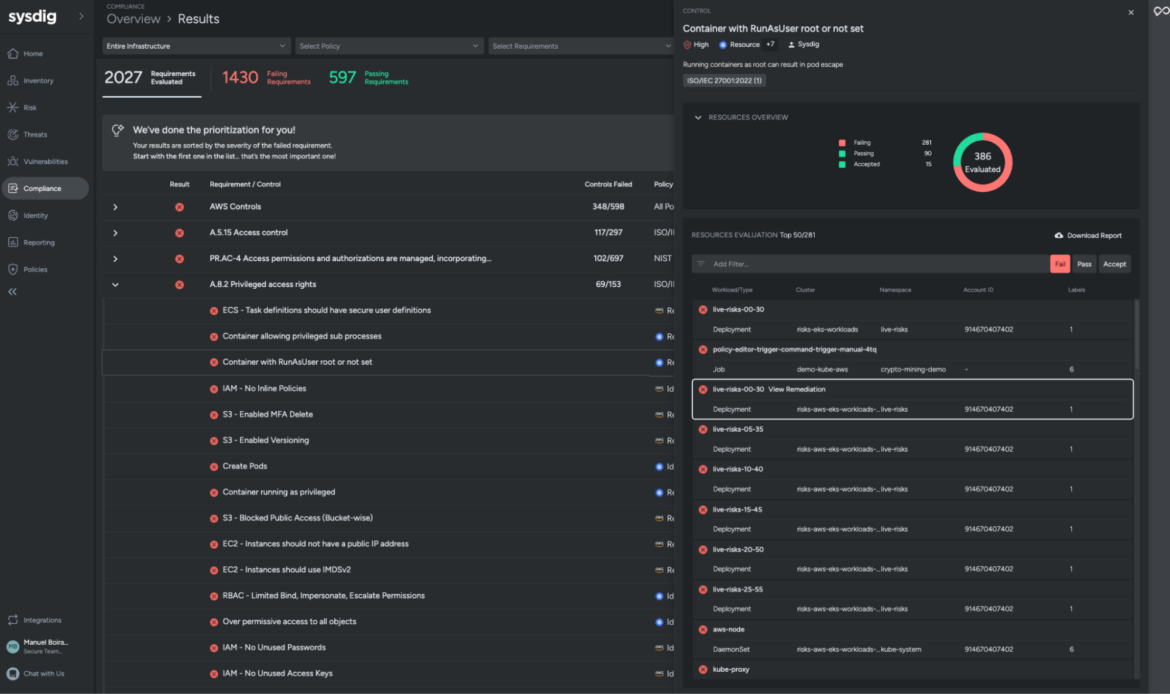
Additionally, should you occur to be working with on-prem information facilities, you want consistency between the 2 environments.
Sysdig is just not a substitute for AWS safety providers, however it’s complementary and strengthening of AWS Safety Hub, and is an answer to contemplate if you wish to simplify operations between the cloud and the on-prem infrastructure of your organization.
Conclusion
AWS safety providers are designed for particular security-related use instances and work very well. There are some gaps that might be coated by third-party instruments just like the Falco or Sysdig platform.
- This flexibility generates some extra technical complexity due to the necessity of deploying, configuring, and interconnecting a number of providers.
- With time, we are able to count on AWS to introduce extra of their specialised safety instruments whereas deprecating older ones. This additionally would possibly finally result in elevated complexity for Cloud Architects and Safety Specialists in integrating and managing these many sources of reality.
- It’s troublesome to hyperlink context and correlation coming from totally different AWS instruments for having one thing near a unified expertise.
Sysdig Safe strengthens AWS and multi-cloud safety by offering a robust however easy unified expertise with a predictable price mannequin, overlaying:
It is a refresh of a weblog initially revealed in 2022.