The xz challenge, a software utilized by many Linux distributions for compressing recordsdata, was compromised by a malicious actor who steadily took over the challenge and inserted a backdoor.
The assault, found accidently on March 29, 2024, by a developer named Andres Freund, throughout efficiency testing, was carried out over a number of years by the GitHub account Jia Tan (JiaT75), who gained the belief of the long-time maintainer of the xz challenge and ultimately changed them as the primary level of contact.
The backdoor was added in variations 5.6.0 and 5.6.1 of xz Utils, a software program package deal that features the xz library. This backdoor permits attackers unauthorized entry on programs which have the compromised variations put in.
The impression of this backdoor is important due to xz’s use in lots of programs all over the world, together with standard Linux distributions like Crimson Hat and Debian.
On this weblog publish, we are going to present a timeline of the occasions, take a look at the important thing folks concerned, and focus on what this incident means for the open-source group and the significance of sustaining the safety and integrity of widely-used software program libraries.
Key Findings
- xz, a widely-used compression library, was compromised with a backdoor (CVE-2024-3094) that permits forunauthorized entry on programs with compromised variations (5.6.0 and 5.6.1) put in.
- The assault was carried out over a number of years by a consumer named Jia Tan (JiaT75), who steadily gained maintainer standing after steady stress from unknown accounts on the long-time maintainer, Lasse Collin, so as to add a brand new maintainer and approve Jia Tan’s patch.
- The widespread use of xz in Linux distributions makes the impression of the backdoor vital.
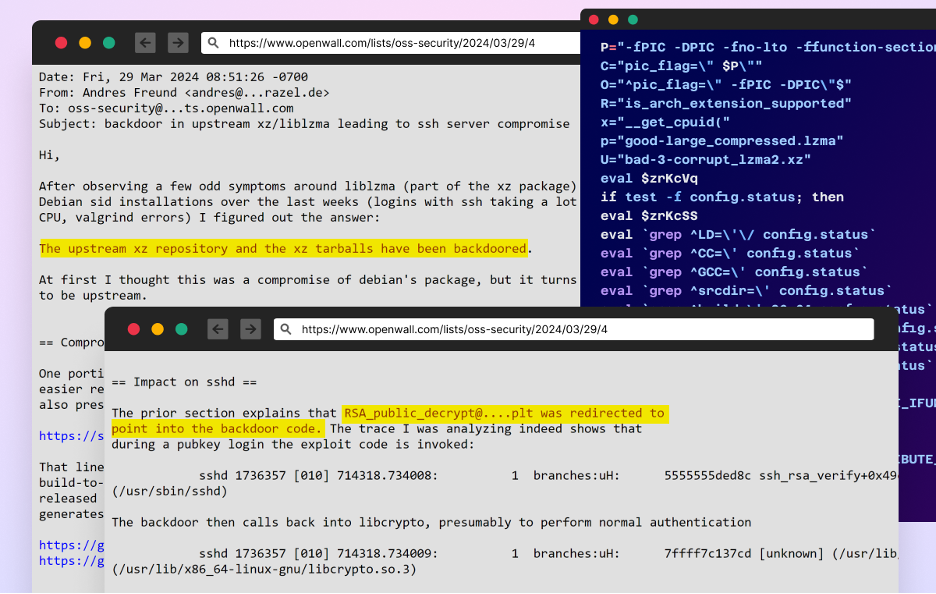
- The backdoor was by accident found on March 29, 2024, by the developer Andres Freund.
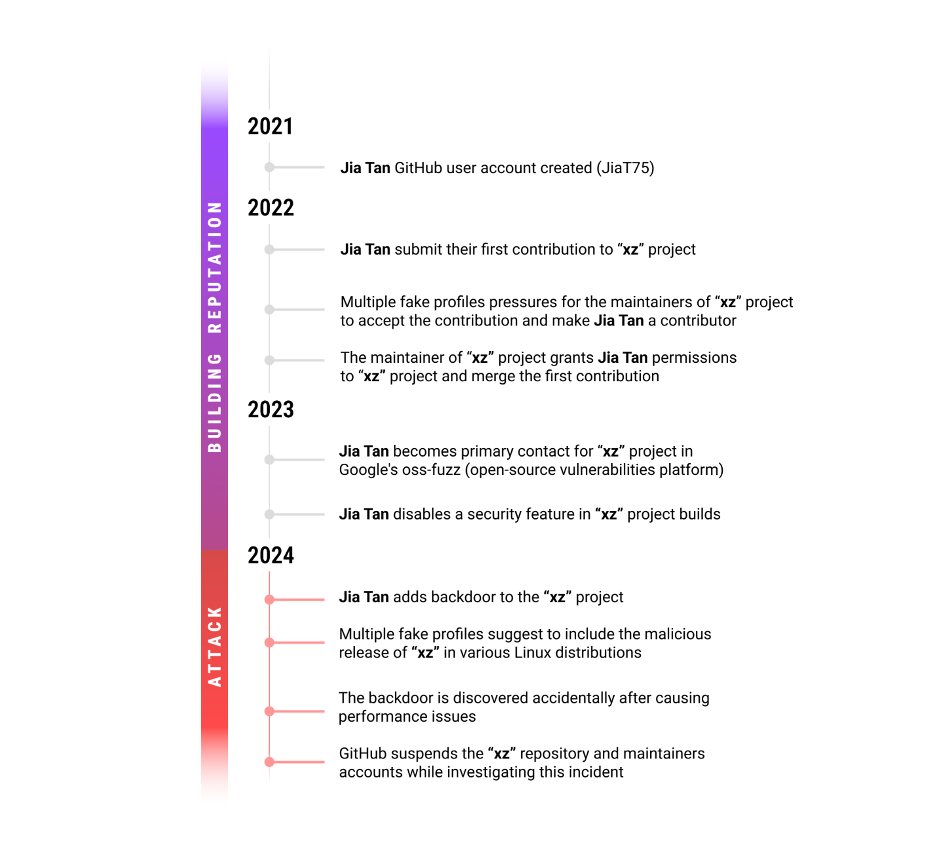
Gaining Popularity Over Time
The xz compression library, a widely-used software for compressing recordsdata, discovered throughout Linux distributions, group initiatives, and industrial merchandise, was compromised by a malicious actor named Jia Tan (JiaT75) who steadily and patiently gained maintainer standing as a way to pull off the assault, finally introducing a backdoor recognized as CVE-2024-3094.
The assault started in 2021 when Jia Tan created their GitHub account and commenced utilizing it for varied actions.
In April 2022, Jia Tan submitted a patch to the xz challenge by way of a mailing checklist. Quickly after, unknown accounts, together with one named Jigar Kumar and one other named Dennis Ens , started pressuring the long-time maintainer of xz, Lasse Collin, to merge the patch and add a brand new maintainer to the challenge. Lasse Collin, who had restricted availability to take look after the challenge, ultimately agreed so as to add Jia Tan as a maintainer. A choice that’s the truth is common within the open-source group, the place maintainers usually hand off initiatives to others as a result of varied causes.
Over the subsequent two years, Jia Tan turned a daily contributor to the xz challenge, gaining belief throughout the group.
By March 2023, Jia Tan had grow to be the first contact for xz in Google’s oss-fuzz, a platform for locating vulnerabilities in open-source software program.
Most Subtle Provide Chain Assault We Know
The backdoor itself was launched in variations 5.6.0 and 5.6.1 of xz Utils, a software program package deal that features the xz library. The malicious code permits attackers unauthorized entry by infecting the SSH on programs with the compromised variations put in, making it a major risk to customers of the library.
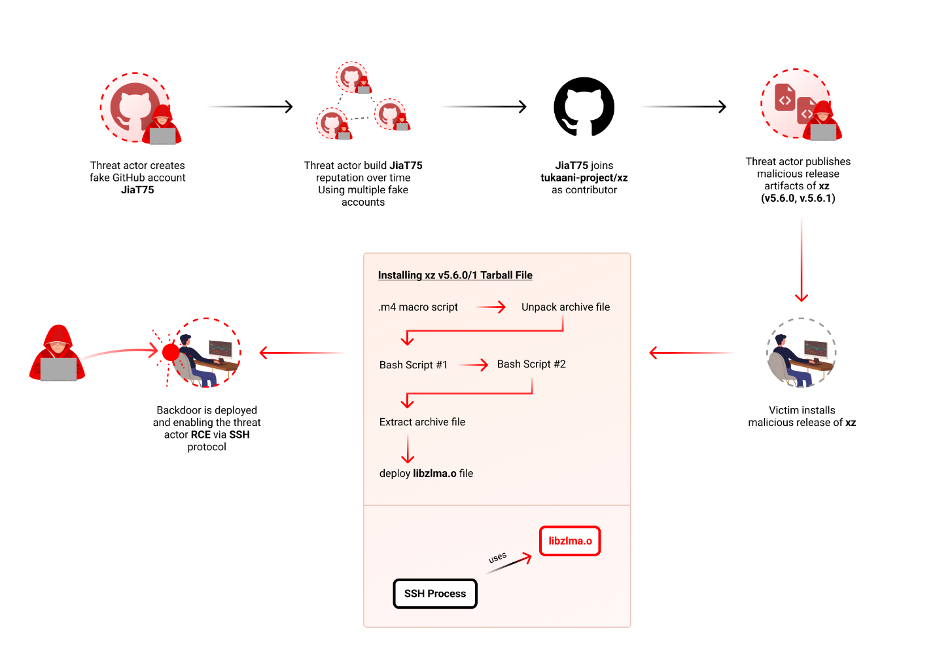
A Discovery
The backdoor was by accident found on March 29, 2024, by Andres Freund throughout routine efficiency testing. Freund observed uncommon CPU utilization within the sshd course of, which led him to analyze additional and uncover the malicious code. This unintended discovery, the backdoor might have gone unnoticed for an extended interval, effecting a big a part of the open supply ecosystem.
Affect
The impression of the backdoor might have had significantly extreme penalties because of the widespread use of xz in compressing important software program parts, together with standard Linux distributions like Crimson Hat and Debian. Many programs worldwide depend on xz for compressing and decompressing recordsdata, making the potential attain of the backdoor intensive.
Superior Persistent Menace
The involvement of a number of identities. The complexity of the payload, and the excessive stage of technical experience required, together with the persistence and persistence proven in steadily gaining belief throughout the xz group over a number of years earlier than introducing the backdoor. All these are per the capabilities of nation-state actors and are qualities of superior persistent threats (APTs).
This incident is a part of a rising and alarming pattern of superior persistent threats (APTs) concentrating on important open-source initiatives.
Conclusion
The xz compromise highlights the pressing want for the open-source group to enhance its safety practices and instruments to forestall comparable assaults sooner or later. Collaboration, transparency, and shared accountability are important to detecting and mitigating superior persistent threats (APTs) concentrating on important open-source initiatives.
We, the group should develop simpler methods, to strengthen the safety of open-source software program. By studying from this incident and taking proactive measures, the open-source group can construct a extra resilient and reliable ecosystem, guaranteeing the long-term success and integrity of open-source initiatives within the face of ever-evolving cybersecurity threats.
Working collectively to maintain the opensource ecosystem protected.