Assault floor administration (ASM) and vulnerability administration (VM) are sometimes confused, and whereas they overlap, they don’t seem to be the identical. The principle distinction between assault floor administration and vulnerability administration is of their scope: vulnerability administration checks a listing of recognized property, whereas assault floor administration assumes you may have unknown property and so begins with discovery. Let’s take a look at each in additional element.
What’s vulnerability administration?
Vulnerability administration is, on the easiest stage, the usage of automated instruments to establish, prioritize and report on safety points and vulnerabilities in your digital infrastructure.
Vulnerability administration makes use of automated scanners to run common, scheduled scans on property inside a recognized IP vary to detect established and new vulnerabilities, so you’ll be able to apply patches, take away vulnerabilities or mitigate any potential dangers. These vulnerabilities have a tendency to make use of a danger rating or scale – corresponding to CVSS – and danger calculations.
Vulnerability scanners typically have many 1000’s of automated checks at their disposal, and by probing and gathering details about your techniques, they’ll establish safety gaps which might be utilized by attackers to steal delicate data, achieve unauthorized entry to your techniques, or disrupt your enterprise. Armed with this data, you’ll be able to defend your group and forestall potential assaults.
 |
| A screenshot of the Intruder vulnerability administration platform, which is designed to carry out 1000’s of safety checks, figuring out vulnerabilities in internet apps, APIs, cloud techniques, and past. |
What’s the vulnerability administration course of?
- Performing a vulnerability scan
- Assessing your vulnerability danger
- Prioritizing and fixing vulnerabilities
- Monitoring repeatedly
What’s assault floor administration?
The principle distinction between vulnerability administration and assault floor administration is the scope. Assault floor administration (ASM) consists of asset discovery – serving to you to search out all of your digital property and companies after which lowering or minimizing their publicity to stop hackers from exploiting them.
With ASM, all recognized or unknown property (on-premises, cloud, subsidiary, third-party, or accomplice environments) are detected from the attacker’s perspective from exterior the group. If you do not know what you’ve got bought, how will you defend it?
Take the instance of an admin interface like cPanel or a firewall administration web page – these could also be safe towards all recognized present assaults right this moment, however a vulnerability might be found tomorrow – when it turns into a big danger. In case you monitor and scale back your assault floor, no matter vulnerabilities, you turn into more durable to assault.
So, a big a part of assault floor administration is lowering publicity to potential future vulnerabilities by eradicating pointless companies and property from the web. However to do that, first it’s essential to know what’s there.
What’s the assault floor administration course of?
- Uncover and map all of your digital property
- Guarantee visibility and create a file of what exists
- Run a vulnerability scan to establish any weaknesses
- Automate so everybody who creates infrastructure can accomplish that securely
- Constantly monitor as new infrastructure and companies are spun up
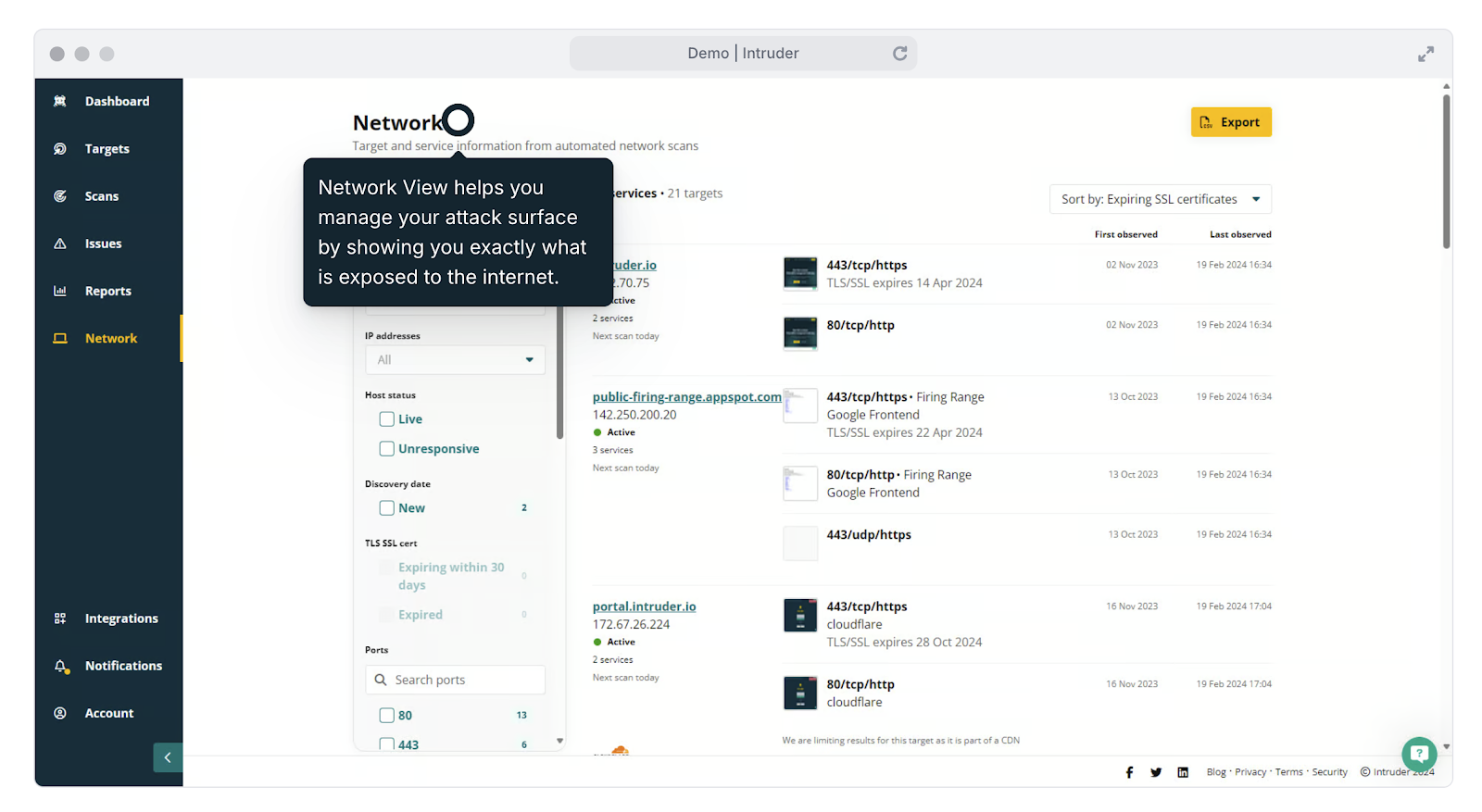 |
| Intruder’s assault floor administration options aid you to remain on prime of adjustments in your surroundings, corresponding to lately opened ports and companies. |
How does assault floor administration differ from vulnerability administration?
Vulnerability administration is the method of figuring out and prioritizing vulnerabilities in your IT infrastructure and purposes. Assault floor administration goes a step additional by figuring out and analyzing your assault floor – all of the gadgets, entry factors and uncovered companies that an attacker may probably use to realize entry to your techniques or knowledge.
Are you able to mix Assault Floor Administration and Vulnerability Administration?
Whereas ASM and VM could have totally different scopes and aims, they don’t seem to be mutually unique. Utilized in mixture, they create a way more holistic, sturdy and complete cyber safety posture. By figuring out your property and vulnerabilities, you’ll be able to prioritize your safety efforts and allocate sources extra successfully – which is able to aid you scale back the probability of a profitable assault and any potential affect.
How Intruder may also help with ASM and VM
In the end, you wish to go away no stone unturned in relation to cyber safety. Trendy VM and ASM options like Intruder can detect vulnerabilities affecting your group. It offers you better visibility and management over your assault floor, displays community adjustments and SSL/TLS certificates expiry dates, helps you keep on prime of your cloud infrastructure, and lets you pay just for energetic targets. Why not see for your self with a free 14-day trial?
