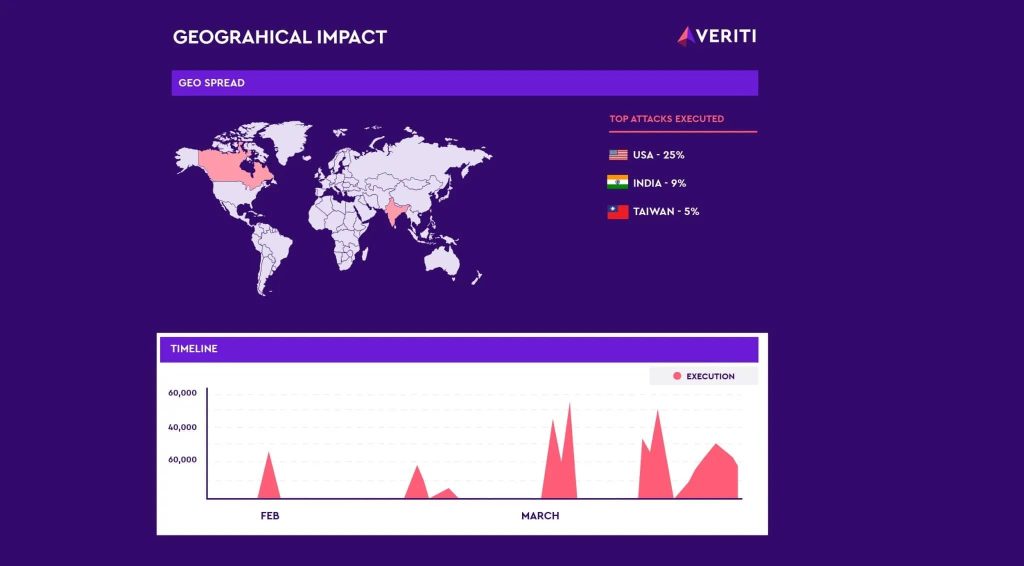
Veriti Analysis has found a surge in assaults from operators of the Androxgh0st malware household, uncovering over 600 servers compromised primarily within the U.S., India and Taiwan.
Based on Veriti’s weblog publish, the adversary behind Androxgh0st had their C2 server uncovered, which may permit for a counterstrike by revealing the impacted targets. The researchers then went on to alert the victims.
Additional analysis revealed that Androxgh0st operators are exploiting a number of CVEs, together with CVE-2021-3129 and CVE-2024-1709 to deploy an online shell on weak servers, granting distant management capabilities. Furthermore, proof suggests energetic net shells related to CVE-2019-2725.
Androxgh0st Menace Actor Ramps Up Exercise
Hackread.com has been monitoring Androxgh0st operations since was first observed in December 2022. The malware operator is understood for deploying Adhublika ransomware and was beforehand noticed speaking with an IP handle related to the Adhublika group.
Androxgh0st operators desire exploiting Laravel purposes to steal credentials for cloud-based providers like AWS, SendGrid, and Twilio. They exploit vulnerabilities in Apache net servers and PHP frameworks, deploying webshells for persistence.
Nevertheless. their latest focus appears to be constructing botnets to use extra methods. Not too long ago, the FBI and CISA issued a joint Cybersecurity Advisory (CSA) advisory, warning about Androxgh0st developing a botnet to hold out credential theft and set up backdoor entry.
Final yr, Cado Safety Ltd. revealed the main points of a Python-based credential harvester and a hacking instrument known as Legion, linked to the AndroxGh0st malware household. Legion is designed to use e mail providers for abuse.
The Method Ahead
Veriti’s analysis goes onto present the significance of proactive publicity administration and risk intelligence in cyber safety. Organizations should repeatedly replace their safety measures, together with patch administration for recognized vulnerabilities, robust net shell deployment monitoring, and behavioural evaluation instruments to stop breaches and defend in opposition to comparable vulnerabilities.
RELATED TOPICS
- Russian Hackers Hit Ubiquiti Routers for Botnet Creation
- ActiveMQ Flaw Exploited to Unfold GoTitan Botnet, PrCtrl Rat
- Mirai-based NoaBot Botnet Hit Linux Methods with Cryptominer
- Qakbot Botnet Disrupted, Contaminated 700,000 Computer systems Globally
- OracleIV DDoS Botnet Malware Targets Docker Engine API Situations