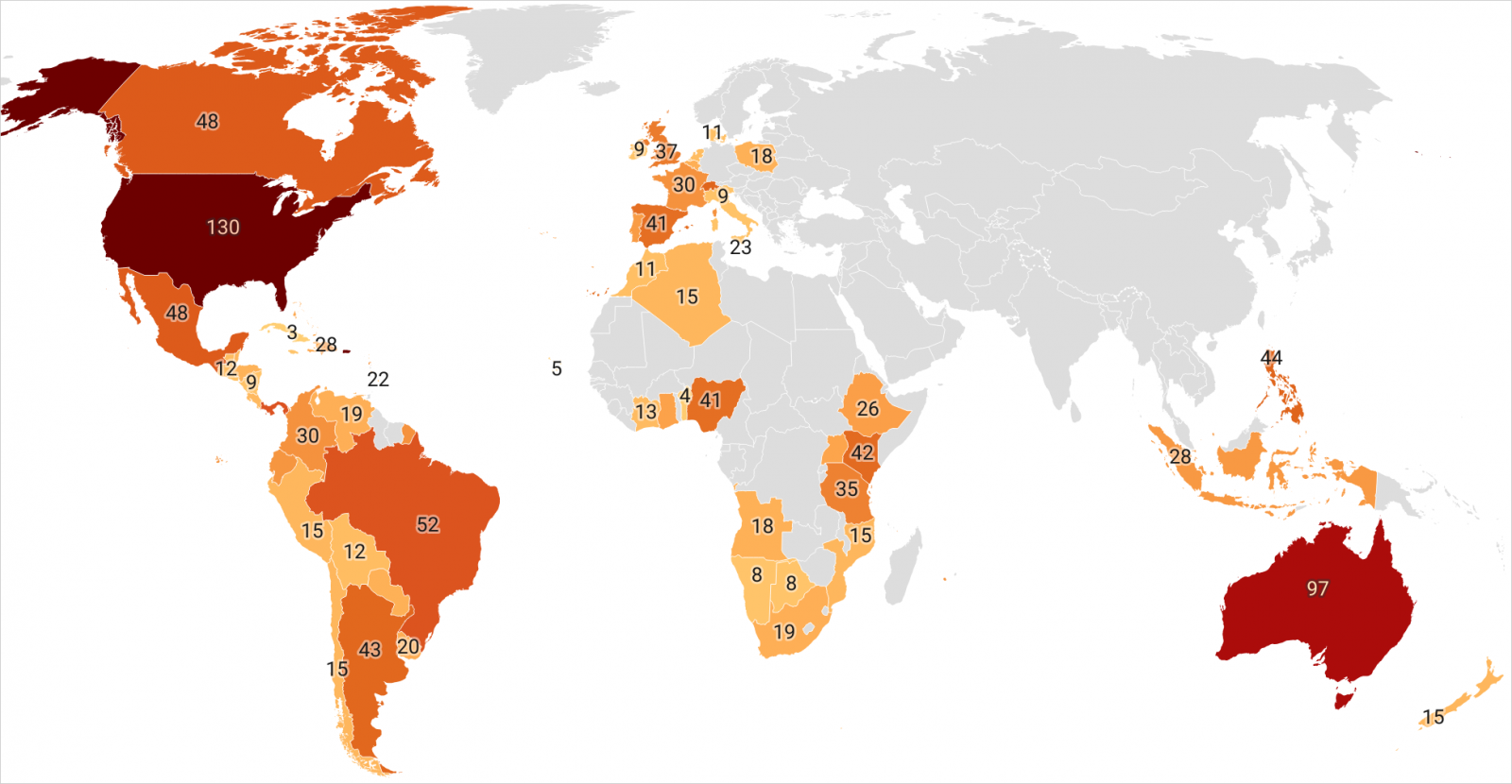
The Android banking trojan “Grandoreiro” is spreading in a large-scale phishing marketing campaign in over 60 international locations, concentrating on buyer accounts of roughly 1,500 banks.
In January 2024, a world legislation enforcement operation involving Brazil, Spain, Interpol, ESET, and Caixa Financial institution introduced the disruption of the malware operation, which had been concentrating on Spanish-speaking international locations since 2017 and precipitated $120 million in losses.
On the similar time, 5 arrests and 13 search and seizure actions occurred throughout Brazil. Nonetheless, no info was supplied on the arrested people’ roles within the operation.
IBM’s X-Drive group reviews that Grandoreiro seems to have returned to large-scale operations since March 2024, probably rented to cybercriminals by way of a Malware-as-a-Service (MaaS) mannequin, and now concentrating on English-speaking international locations too.
Supply: IBM
Moreover, the trojan itself has undergone a technical revamp that added many new highly effective options and enhancements, indicating that its creators evaded arrest and weren’t deterred by the earlier crackdown.
New phishing campaigns
Since a number of risk actors hire the malware, the phishing lures are various and crafted particularly for the organizations a specific cybercriminal is concentrating on.
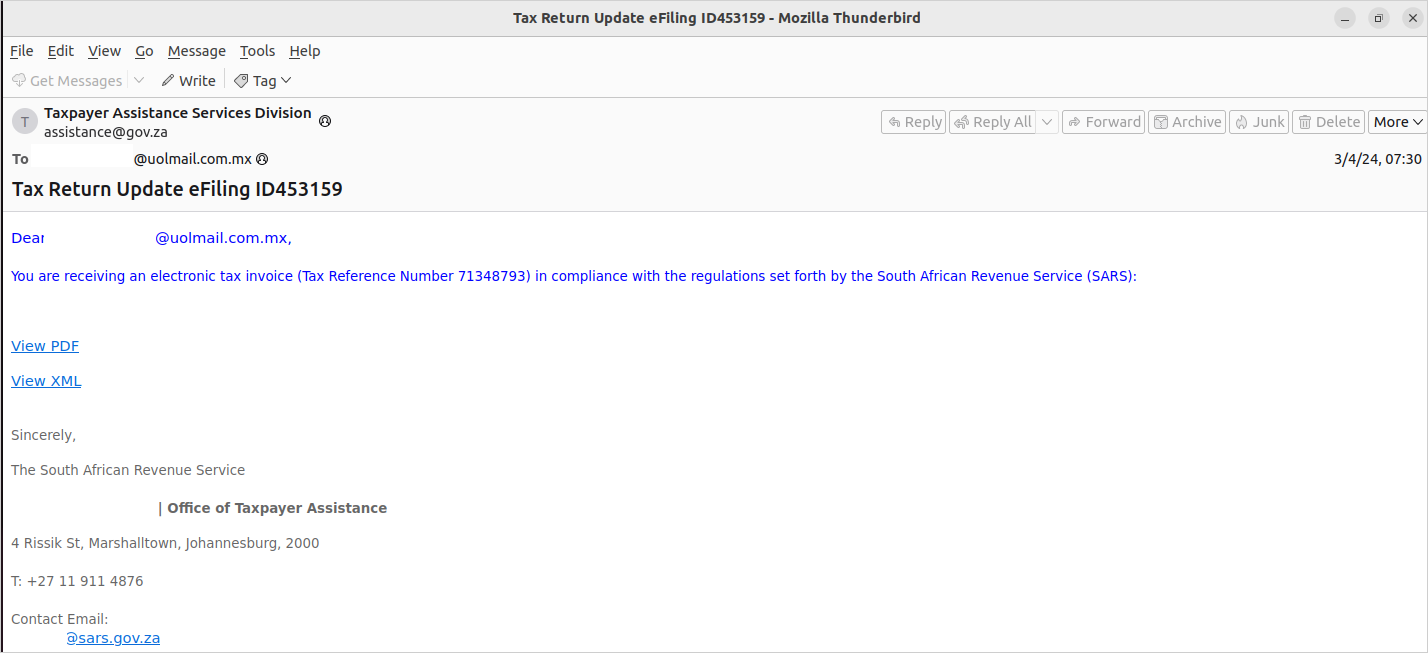
Phishing emails seen by IBM impersonate authorities entities in Mexico, Argentina, and South Africa, primarily tax administration organizations, income providers, and federal electrical energy commissions.
The emails are written within the recipient’s native language, incorporate official logos and codecs, and comprise a name to motion, resembling clicking hyperlinks to view invoices, account statements, or tax paperwork.
Supply: IBM
When recipients click on on these emails, they are redirected to a picture of a PDF that triggers the obtain of a ZIP file containing a bloated (100 MB) executable, which is the Grandoreiro loader.
New Grandoreiro options
IBM X-Drive seen a number of new options and important updates within the newest variant of the Grandoreiro banking trojan, making it a extra evasive and efficient risk.
These can be summarized within the following:
- Reworked and improved string decryption algorithm utilizing a mixture of AES CBC and customized decoder.
- Updates on the area era algorithm (DGA) which now contains a number of seeds to separate the command and management (C2) communications with operator duties.
- New mechanism that targets Microsoft Outlook shoppers, disabling safety alerts and utilizing them to ship phishing to new targets.
- New persistence mechanism counting on the creation of registry Run keys (‘HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun’ and ‘HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun’)
- Growth of concentrating on financial institution functions and inclusion of cryptocurrency wallets.
- Growth of the command set, now together with distant management, file add/obtain, keylogging, and browser manipulation by way of JavaScript instructions.
One other notable new characteristic is Grandoreiro’s skill to carry out detailed sufferer profiling and determine whether or not or not it should execute on the system, which provides operators higher management of their concentrating on scope.
IBM analysts report that the most recent model of the trojan avoids execution in particular international locations like Russia, Czechia, the Netherlands, and Poland, in addition to on Home windows 7 machines in the US the place no antivirus is energetic.
The above clearly signifies that regardless of the latest legislation enforcement motion, Grandoreiro is alive and kicking, and sadly, it seems to be stronger than ever.
