A brand new model of the FakeCall malware for Android hijacks outgoing calls from a person to their financial institution, redirecting them to the attacker’s cellphone quantity as a substitute.
The objective of the most recent model stays to steal individuals’s delicate data and cash from their financial institution accounts.
FakeCall (or FakeCalls) is a banking trojan with a give attention to voice phishing, through which victims are deceived by means of fraudulent calls impersonating banks, asking them to convey delicate data.
Kaspersky first reported the trojan in April 2022, that includes realistic-appearing calling interfaces to trick victims into believing they’re on a name with their financial institution.
A March 2023 report by CheckPoint warned that FakeCall was now impersonating over 20 monetary organizations, providing targets low-interest loans, and that includes new evasion mechanisms to decrease detection charges.
Along with vishing (voice phishing), FakeCall may additionally seize reside audio and video streams from the contaminated units, permitting attackers to steal delicate knowledge with out sufferer interplay.
Hijacking calls
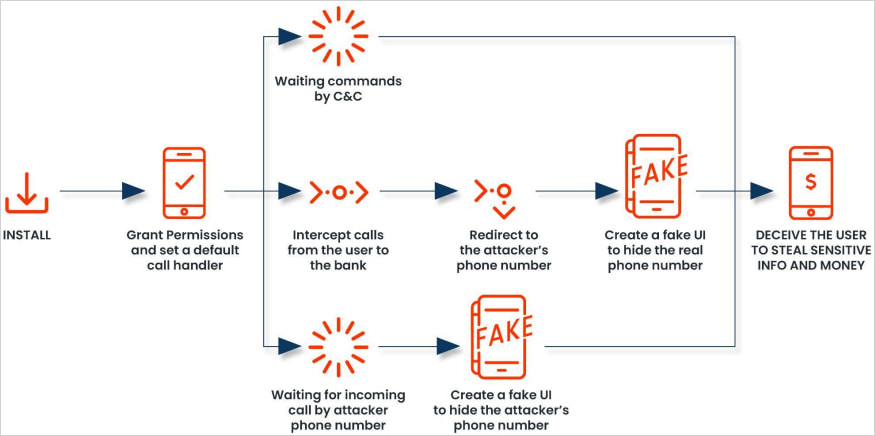
In earlier variations, FakeCall prompted customers to name the financial institution from inside an app, impersonating the monetary institute. Then, a pretend display was overlaid that displayed the financial institution’s precise quantity whereas the sufferer was related with the scammers.
Within the newest model analyzed by Zimperium, the malicious app units itself because the default name handler, asking the person to approve this motion upon putting in the applying by means of an Android APK.
The decision handler in Android manages incoming and outgoing calls, basically serving as the principle interface that processes dialing, connecting, and ending calls.
When the malware prompts the person to set it because the default name handler, it positive factors permission to intercept and manipulate each outgoing and incoming calls.
A pretend name interface mimics the precise Android dialer, displaying trusted contact data and names, elevating the extent of deception to some extent that is onerous for victims to understand.
What makes this malware so harmful is that when a person makes an attempt to name their monetary establishment, the malware secretly hijacks the decision and redirects it to an attacker’s cellphone quantity as a substitute.
“When the compromised individual attempts to contact their financial institution, the malware redirects the call to a fraudulent number controlled by the attacker,” explains the brand new Zimperium report.
“The malicious app will deceive the user, displaying a convincing fake UI that appears to be the legitimate Android’s call interface showing the real bank’s phone number.”
“The sufferer can be unaware of the manipulation, because the malware’s pretend UI will mimic the precise banking expertise, permitting the attacker to extract delicate data or acquire unauthorized entry to the sufferer’s monetary accounts.
Supply: Zimperium
New options and enhancements
Regardless of heavier code obfuscation, Zimperium additionally found that the most recent FakeCall variations add a number of enhancements and assault mechanisms, although some are nonetheless below improvement.
First, FakeCall added a Bluetooth listener and a display state monitor, each with out malicious performance but.
The malware now leverages Android’s Accessibility Service to realize in depth management over the person interface, permitting it to observe dialer exercise, mechanically grant itself permissions, and simulate person actions like clicks and gestures.
A brand new cellphone listener service establishes a communication channel with the attacker’s command and management (C2) server, permitting them to situation instructions to carry out varied actions, like get system location, delete apps, file audio or video, and edit contacts.
New instructions added on the most recent variant embrace:
- Configure the malware because the default name handler.
- Begin reside streaming of the system’s display content material.
- Take a screenshot of the system show.
- Unlock the system if it is locked and quickly flip off auto-lock.
- Use accessibility providers to imitate the press of the house button.
- Delete photographs specified by the C2 server.
- Entry, compress, and add photographs and thumbnails from storage, particularly concentrating on the DCIM folder for pictures.
These additions present that FakeCall is below energetic improvement, and its operators are working in direction of making it a extra evasive and formidable banking trojan.
Zimperium has revealed an inventory of indicators of compromise (IoC), together with app bundle names and APK checksums so customers can keep away from the malicious apps that carry the malware. Nevertheless, these are steadily modified by the menace actors.
As all the time, it’s recommended that customers keep away from manually putting in Android apps by means of APKs and as a substitute set up them from Google Play. Whereas malware can nonetheless make it onto Google’s service, when detected, it may be eliminated by Google Play Shield.
