Immediately, Google introduced new safety features coming to Android 15 and Google Play that may assist block scams, fraud, and malware apps on customers’ gadgets.
Introduced at Google I/O 2024, the brand new options are designed not solely to assist finish customers but in addition to warn builders when their apps have been tampered with.
“Today, we’re announcing more new fraud and scam protection features coming in Android 15 and Google Play services updates later this year to help better protect users around the world,” reads a Google weblog publish from Dave Kleidermacher, VP Engineering, Android Safety and Privateness.
“We’re also sharing new tools and policies to help developers build safer apps and keep their users safe.”
Defending in opposition to spyware and adware, banking malware
Google is introducing quite a few new options in Android 15 that are aimed at blocking banking trojans and spyware and adware from stealing your info.
Android banking trojans are used to steal customers banking credentials by displaying pretend login overlays, stealing MFA codes from notifications/messages, and permitting menace actors to remotely management gadgets.
Through the years, researchers have illustrated how Android malware generally steals one-time passcodes from messages and notifications. Final yr, a new model of the Xenomorph Android malware took it a step additional by permitting MFA codes to be stolen from Google Authenticator.
Google has introduced new safety features that trigger one-time passcodes to be hidden from notifications in order that malware can not steal them.
The corporate can also be increasing its restricted settings function to incorporate further permissions that customers should explicitly grant apps to forestall them from stealing knowledge.
Google says they’re additionally introducing new options that shield in opposition to screen-sharing assaults performed through social engineering.
When Android is in screen-sharing mode, the working system will robotically block delicate info from showing in notifications in order that it can’t be stolen by distant menace actors.
“During screen sharing, private notification content will be hidden, preventing remote viewers from seeing details in a user’s notifications,” explains Kleidermacher.
“Apps that post OTPs in notifications will be automatically protected from remote viewers when you’re screen sharing, helping thwart attempts to steal sensitive data.”
This new function can even stop your display screen from being proven to attackers when getting into credentials and bank card info throughout a screen-share session. A function rolling out later this yr will show extra outstanding indicators when display screen sharing is lively.
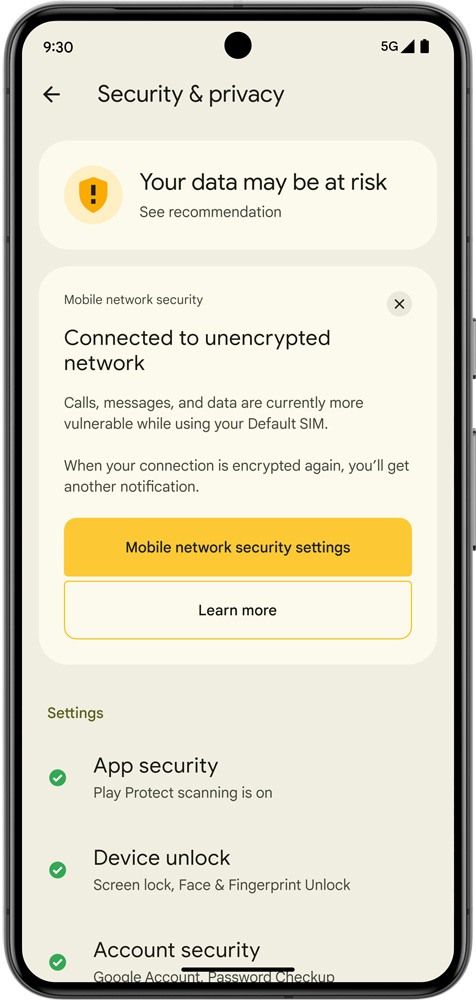
Lastly, Google is rolling out notifications alerting you when related to an unencrypted mobile community to dam Stingray assaults.
“We’ll notify you if your cellular network connection is unencrypted, potentially exposing voice and SMS traffic to radio interception, and potentially visible to others. This can help warn users if they’re being targeted by criminals who are trying to intercept their traffic or inject a fraud SMS message,” Kleidermacher additional shared.
“We’ll help at risk-users like journalists or dissidents by alerting them if a potential false cellular base station or surveillance tool is recording their location using a device identifier.”
Bringing AI to Google Play
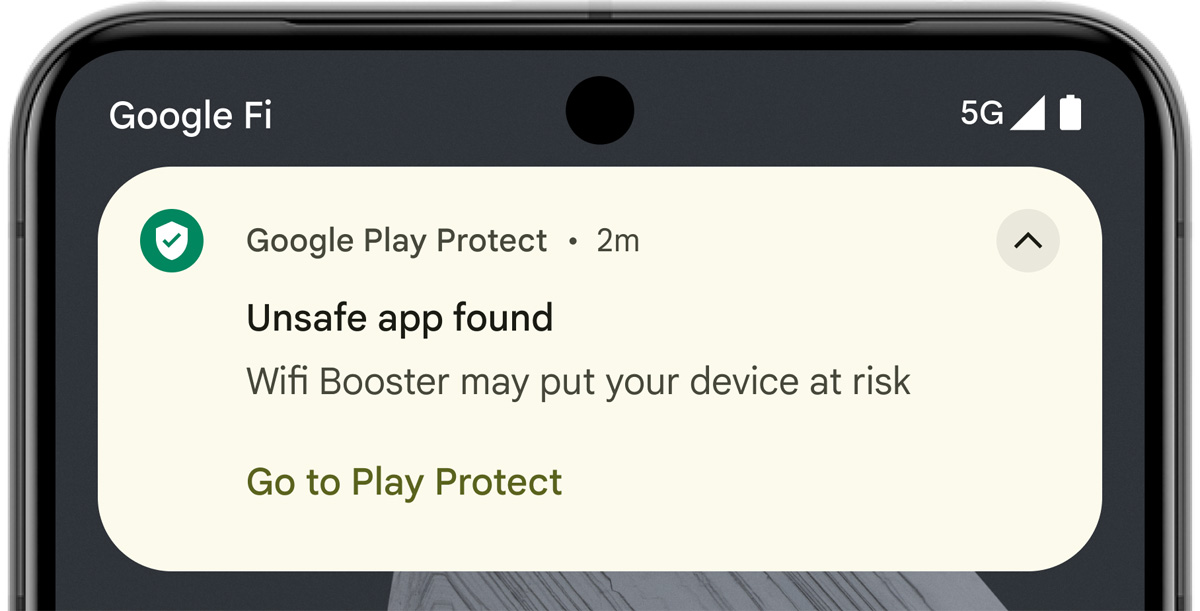
Google says they’re introducing a brand new function known as Google Play Defend stay menace detection, which makes use of on-device synthetic intelligence to detect when an Android app performs suspicious conduct.
The app is then despatched again to Google for evaluate, and customers are warned to disable it till it may be decided whether it is malicious.
For builders, Google has up to date its Play Integrity API to permit builders to test if apps are working in safe environments.
The API has now been up to date to permit dev to test the next in-app alerts:
- Threat From Display screen Capturing or Distant Entry: Builders can test if there are different apps working that could possibly be capturing the display screen, creating overlays, or controlling the system. That is useful for apps that need to cover delicate info from different apps and shield customers from scams.
- Threat From Identified Malware: Builders can test if Google Play Defend is lively and the consumer system is freed from recognized malware earlier than performing delicate actions or dealing with delicate knowledge. That is significantly precious for monetary and banking apps, including one other layer of safety to guard consumer info.
- Threat From Anomalous Gadgets: Builders also can opt-in to obtain current system exercise to test if a tool is making too many integrity checks, which could possibly be an indication of an assault.
Google says all these options will probably be rolling out to Google Play and Android 15 all year long.