Key Factors
- In an ongoing marketing campaign, a menace actor is leveraging npm packages to focus on builders to steal supply code and secrets and techniques.
- The actor behind this marketing campaign is suspected to be associated to malicious exercise dated as early as 2021 undetected.
- On this report, we’ll share new packages and IOCs associated to this assault.
Introduction
Builders within the cryptocurrency sphere are being focused as soon as once more, as one more menace actor has been uncovered. This consumer has been publishing malicious NPM packages with the aim of exfiltrating delicate knowledge akin to supply code and configuration recordsdata from the sufferer’s machines.
The menace actor behind this marketing campaign has been linked to malicious exercise relationship again to 2021. Since then, they’ve repeatedly printed malicious code.
The most recent batch of exercise occurred in August, and was printed by Phylum.
On this report, we’ll present new packages and IOCs associated to this attacker. It is vital to notice that we do not simply have a malicious bundle downside; we’ve got an adversary downside. Solely by studying attacker ways, strategies, and procedures (TTPs), can we arrange correct defenses in opposition to future assaults.
A Deep Dive Into Code
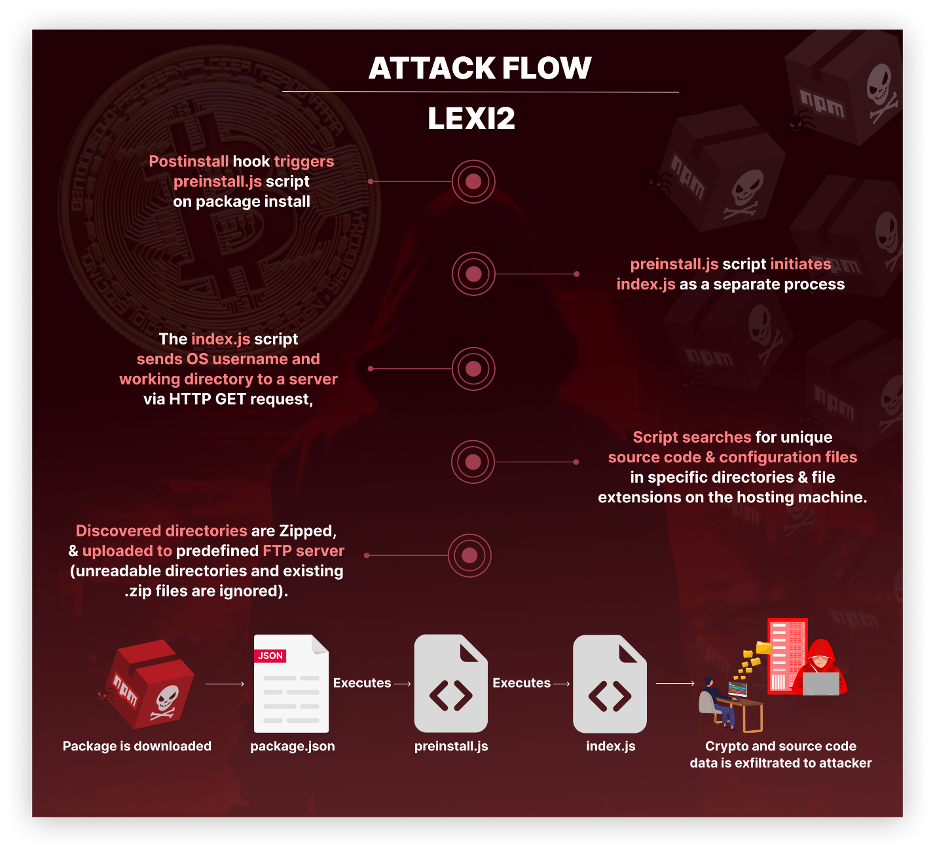
Every of the official packages utilized by this menace actor was designed to execute mechanically upon set up. Every bundle contained three recordsdata – bundle.json, preinstall.js, and index.js. The assault stream is as follows:
- Upon putting in the malicious bundle, a postinstall hook outlined within the bundle.json file triggers the preinstall.js script.
- The preinstall.js script makes use of a way known as ‘spawn’ to provoke one other file named index.js. Basically, it causes index.js to run as a separate course of, guaranteeing it continues to function independently even after the primary set up course of is full.
- The index.js script collects the present OS username and dealing listing and sends this data in an HTTP GET request to a predefined server.
- It then rakes via directories on the internet hosting machine, concentrating on particular directories like .env, .gitlab, and .github, and recordsdata with extensions akin to .asp, .js, and .php. focusing extra on distinctive supply code or configuration recordsdata.
- Subsequently, it ZIPs the found directories, intentionally avoiding unreadable directories or present .zip recordsdata.
- As a closing step, it makes an attempt to add these archives to a predefined FTP server.
The packages are tied to the cryptocurrency area additional solidifying their monetary motives, with clear references to entities like CryptoRocket and Binarium.
Searching down “lexi2” exercise
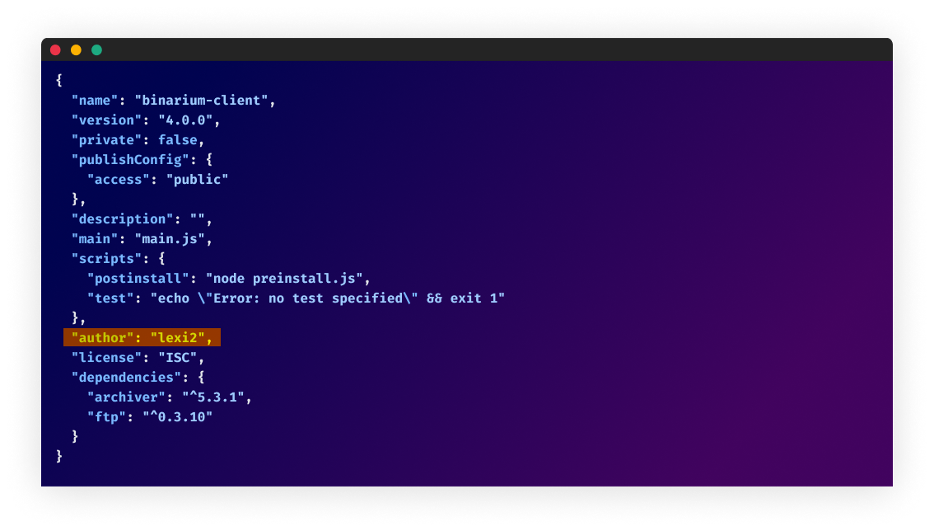
A deeper investigation revealed a constant metadata attribute: the “author” area within the bundle.json file citing “lexi2″ because the creator”lexi2” because the creator.
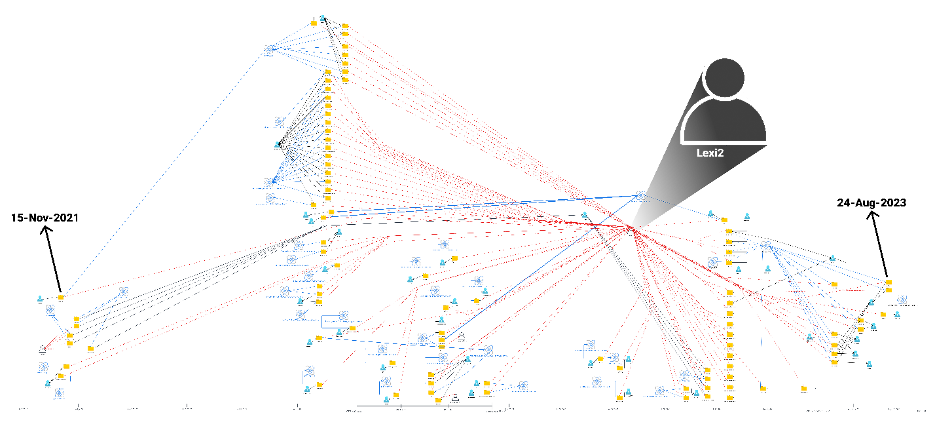
Sustaining a complete knowledge pool of all open-source packages that span totally different open-source repositories is important to understanding not solely the attacker, but in addition their evolving Ways, Strategies, and Procedures (TTPs). Leveraging this useful resource, we cross-referenced “lexi2” and different code-specific attributes in opposition to dozens of further malicious packages inside our database. Our database evaluation indicated that “lexi2” has been related to malicious packages relationship way back to 2021
Addressing the Adversary Downside
We have to perceive that when coping with menace actors and particularly APTs, simply reporting and eradicating packages gained’t be sufficient to cease them, we want as an trade to maneuver up the “Pyramid of pain” to cease APT attackers.
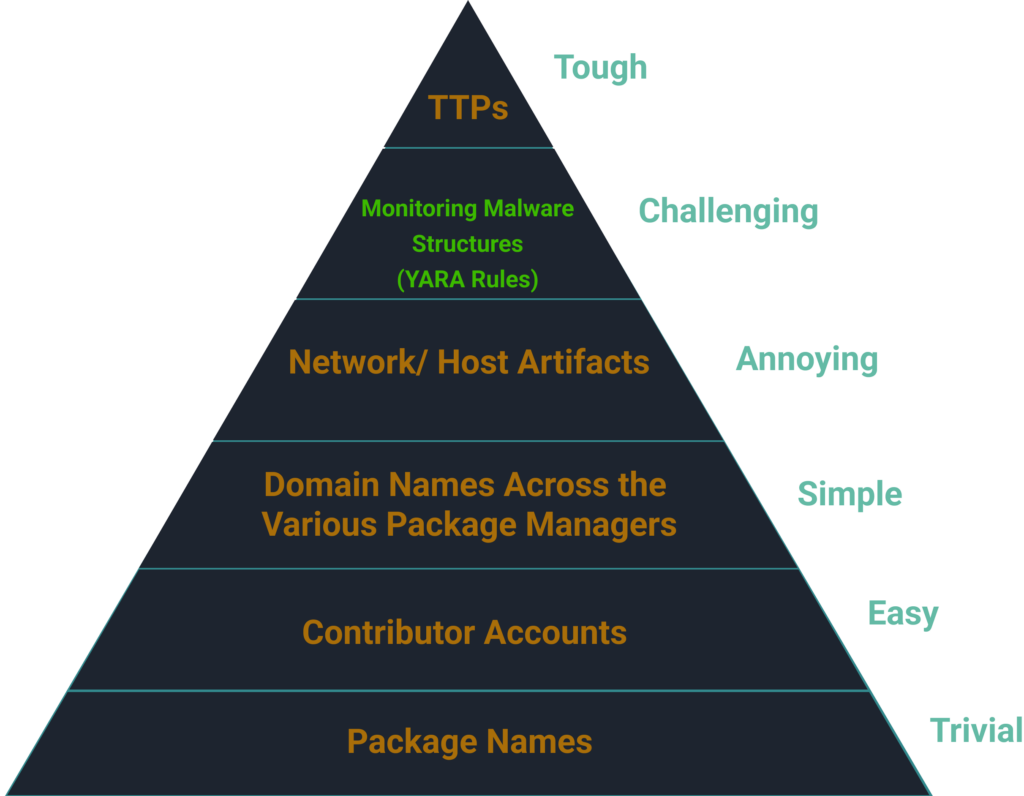
Now we have developed a YARA rule to help in figuring out, and stopping, the execution of the malicious scripts used on this infostealer marketing campaign.
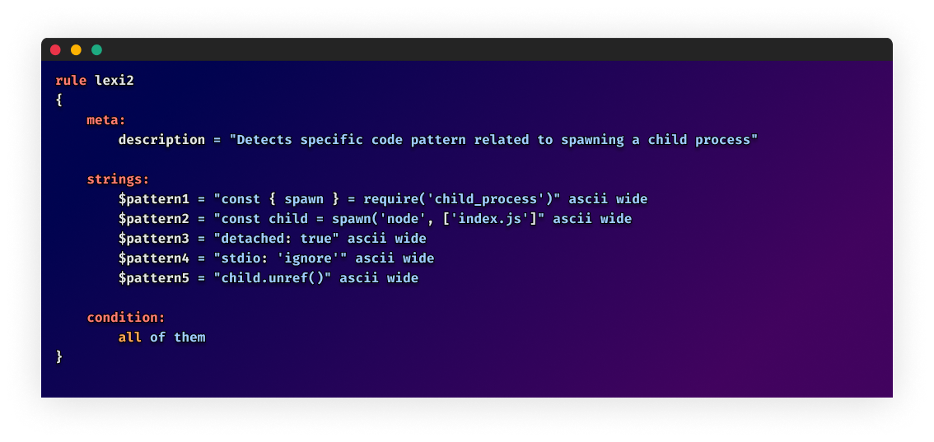
This rule, together with a repeatedly up to date assortment of menace detection signatures, may be present in our repository at os-scar/yara-signatures.
Conclusion
The cryptocurrency sector stays a sizzling goal, and it is vital to acknowledge that we’re not simply grappling with malicious packages ,but in addition persistent adversaries whose steady and meticulously deliberate assaults date again months and even years.
Reactive countermeasures of deleting the latest batch of malicious packages supply solely non permanent reduction and do not get to the foundation of the issue. Safety in opposition to these unrelenting threats requires a extra refined technique.
Sharing metadata and monitoring attackers is an integral part of this broader safety method. It goes past short-term fixes and delves into the continuing monitoring and evaluation of attacker conduct and patterns. Collaboration and intelligence sharing throughout the cybersecurity neighborhood can improve our defenses, making the ecosystem extra resilient to future assaults.
When you want any of those packages, be at liberty to contact us immediately at: [email protected].
Packages
The complete checklist of packages may be discovered within the following hyperlink:
https://gist.github.com/masteryoda101/01eee19e50054733dcde5b7364949550
IOCs
- 178[.]128[.]27[.]205
- 185[.]62[.]56[.]25
- 185[.]62[.]57[.]60
- 198[.]199[.]83[.]132
- 1wy3rk316x8qqy4fyxtvcs4kkbq2es2h[.]oastify[.]com
- 288utkkrohmp0nr8znflcp88nztrhg[.]oastify[.]com
- 4or5o5yn5lqzenk4[.]b[.]requestbin[.]internet
- 5[.]9[.]104[.]19
- 51[.]250[.]2[.]204
- 65[.]21[.]108[.]160
- 6wxd3v84nevku06dcgbqcxrmt[.]canarytokens[.]com
- bind9-or-callback-server[.]com
- bq5m9lnmalh9ktyi9wydockt9kfb32rr[.]oastify[.]com
- c7kxnys58daceezcxx0jjstn6ec50vok[.]oastify[.]com
- cczk46g2vtc0000k68dgggx31deyyyyyb[.]oast[.]enjoyable
- ck0r1hp2vtc00007c0zggjocy3ryyyyyb[.]oast[.]enjoyable
- cup1qnm56sdo4bdv[.]b[.]requestbin[.]internet
- efrva6[.]dnslog[.]cn
- fhg62xavat9jzyt6euwxi6sro[.]canarytokens[.]com