Amazon has seized domains utilized by the Russian APT29 hacking group in focused assaults in opposition to authorities and navy organizations to steal Home windows credentials and information utilizing malicious Distant Desktop Protocol connection information.
APT29, also called “Cozy Bear” and “Midnight Blizzard,” is a Russian state-sponsored cyber-espionage group linked to Russia’s Overseas Intelligence Service (SVR).
Amazon clarifies that though the phishing pages APT29 used have been made to seem as AWS domains, neither Amazon, nor credentials for its cloud platform have been the direct targets of those assaults.
“Some of the domain names they used tried to trick the targets into believing the domains were AWS domains (they were not), but Amazon wasn’t the target, nor was the group after AWS customer credentials,” reads the announcement.
“Rather, APT29 sought its targets’ Windows credentials through Microsoft Remote Desktop.”
“Upon learning of this activity, we immediately initiated the process of seizing the domains APT29 was abusing which impersonated AWS in order to interrupt the operation.”
The risk actors are recognized for extremely refined assaults concentrating on governments, suppose tanks, and analysis establishments globally, usually utilizing phishing and malware to steal delicate data.
Focusing on organizations worldwide
Though APT29’s current marketing campaign had a major impression in Ukraine, the place it was first found, it was broad in scope, concentrating on a number of nations thought-about Russian adversaries.
Amazon notes that on this specific marketing campaign, APT29 despatched phishing emails to a a lot bigger variety of targets than they often do, following the alternative strategy of their typical “narrow targeting” technique.
Ukraine’s Pc Emergency Response Staff (CERT-UA) revealed an advisory about these “Rogue RDP” attachments to warn concerning the mass e-mail exercise, which they observe beneath ‘UAC-0215.’
The messages used the subject of addressing ‘integration’ points with Amazon and Microsoft companies and implementing a ‘zero belief’ cybersecurity structure (Zero Belief Structure, ZTA).
The emails included RDP (Distant Desktop Protocol) connection information with names like “Zero Trust Security Environment Compliance Check.rdp” that robotically initiated connections to malicious servers when opened.
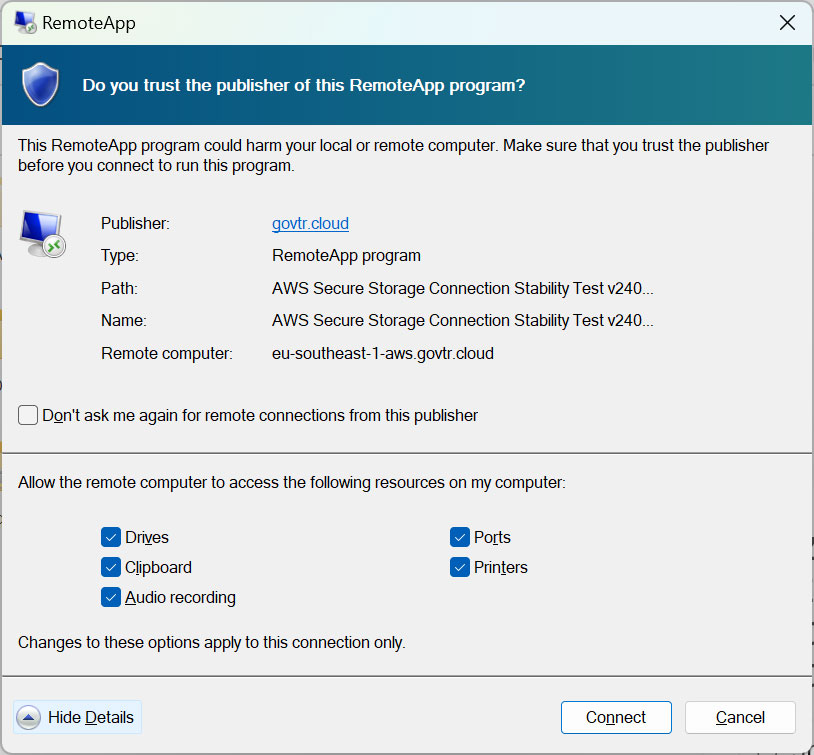
Supply: BleepingComputer
As will be seen from the picture of one in all these RDP connection profiles above, they shared all native sources with the attacker-controlled RDP server, together with:
- Native disks and information
- Community sources
- Printers
- COM ports
- Audio units
- Clipboard
Furthermore, UA-CERT says they will also be used to execute unauthorized packages or scripts on the compromised machine.
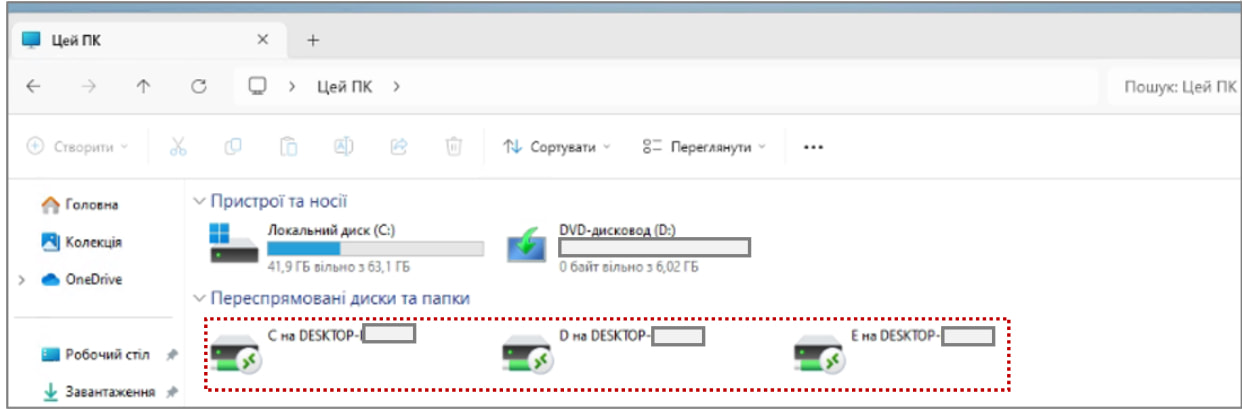
Supply: CERT-UA
Whereas Amazon says that this marketing campaign was utilized to steal Home windows credentials, because the goal’s native sources have been shared with the attacker’s RDP server, it could even have allowed the risk actors to steal information instantly from the shared units.
This consists of all information saved on the goal’s arduous drives, Home windows clipboard, and mapped community shares.
CERT-UA recommends scrutinizing community interplay logs for IP addresses shared within the IoC part of their bulletin to detect doable indicators of assaults or a breach.
Moreover, the under measures are beneficial for lowering the assault floor:
- Block’ .rdp’ information on the mail gateway.
- Forestall customers from launching any ‘.rdp’ information when not wanted.
- Configure firewall settings to limit RDP connections from the mstsc.exe program to exterior community sources.
- Configure group insurance policies to disable useful resource redirection through RDP (‘Distant Desktop Providers’ -> ‘Distant Desktop Session Host’ -> ‘Gadget and Useful resource Redirection’ -> ‘Don’t permit…’).
APT29 stays one in all Russia’s most succesful cyber threats, lately changing into recognized for utilizing exploits solely out there to spyware and adware distributors.
Up to now 12 months, it was revealed that the risk actors hacked necessary software program distributors like TeamViewer, Microsoft, and Hewlett Packard Enterprise.
Western intelligence companies warned earlier this month about APT29 leveraging Zimbra and JetBrains TeamCity servers flaws “en masse,” to breach necessary organizations worldwide.
