Many customers are large followers of sensible home equipment and toys for his or her ease of use and integration into their sensible dwelling setups. It is vitally alluring to have the ability to pull up an app in your cellphone to activate the lights or warmth up your oven.
APIs typically energy these options that buyers have come to take pleasure in. Nevertheless, at any time when you possibly can remotely entry your sensible system, there’s all the time an opportunity that another person can too if the producer has not carried out correct safety measures. Tech-savvy customers may additionally work out learn how to tamper with their home equipment in methods the producer didn’t intend. Such tampering can lead to actual enterprise loss if the safety failure includes the alternate of cash.
One such incident has prompted a wave of media protection lately – a related/sensible laundry system created by CSC ServiceWorks could possibly be tricked into giving free laundry cycles. College students at UC Santa Cruz found API flaws to bypass the necessity for funds and even fill their laundry account with hundreds of thousands of {dollars}.
Checking pockets for any hidden goodies (or Swagger UI docs)
If you wish to probe an API for safety flaws, a standard first step is to try to discover documentation. For public APIs, a number of documentation is often obtainable and straightforward to seek out. For personal or inside APIs, documentation is nearly all the time by no means obtainable publicly as a result of the corporate didn’t intend for others to make use of the APIs. The provision of documentation may help safety researchers by saving them appreciable time.
As an alternative of reverse engineering binary recordsdata or JavaScript, an Open API spec can present every thing that’s wanted to probe an API for weak point, and generally even reveal inside APIs that unlock privileged entry.
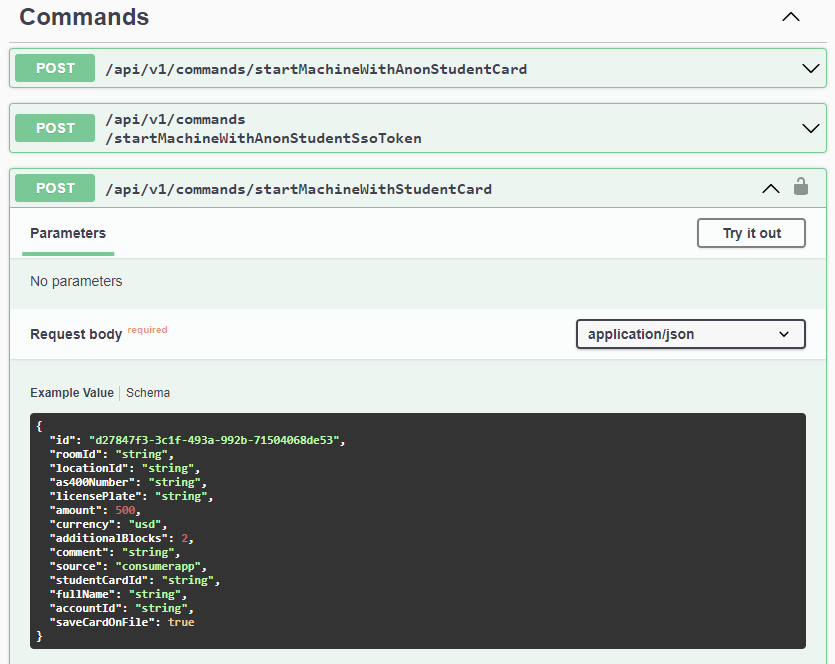
Swagger UI is a documentation platform designed for APIs. CSC ServiceWorks used it to doc their API. They by chance left it uncovered for anybody to view (in the event that they knew the place to look). This made it straightforward to work with the API and eliminated the necessity to reverse engineer something. Right here is an instance of an API name the place all request fields are clearly documented:
Beginning a load: Exploiting the API free of charge cycles
With the documentation in hand, it didn’t take lengthy to find some fascinating API requests with physique parameters that shouldn’t be there.
There have been at the very least 2 crucial vulnerabilities within the API that in the end allowed to start out a laundry machine free of charge. Each vulnerabilities are examples of Damaged Object Property Stage Authorization.
The primary vulnerability was with the startMachineWithPayment API. In the event you look intently, you’ll discover how there’s an quantity area:
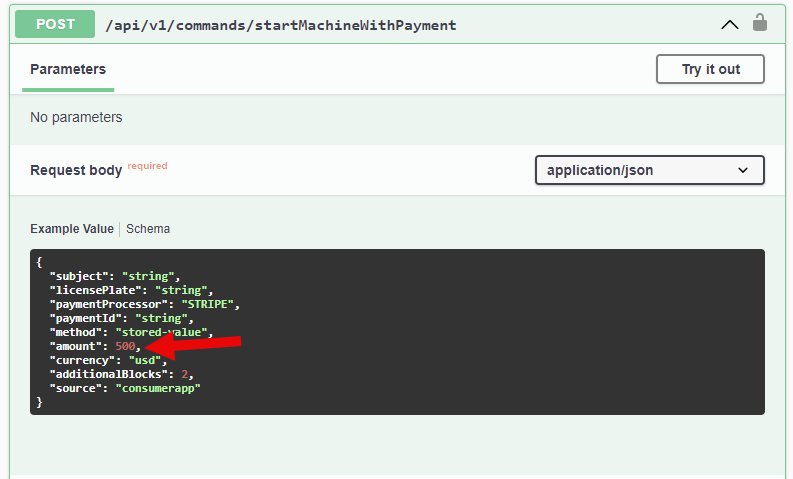
This was an vital discovery as a result of it indicated the consumer had management over how a lot they had been spending. As an alternative of the server deducting a set sum of money from the account, it relied on the consumer to inform them how a lot to deduct. When it was set to 0, no cash was deducted, however the laundry machine nonetheless began.
With this vulnerability, it was pointless so as to add any funds to your account, however to get any laundry accomplished, you would need to ship this API request manually every time, which might get tedious. Generally you simply wish to begin a load shortly and get again to finding out (or partying). Happily, the second vulnerability made issues even simpler.
The second vulnerability was with the deposit API itself. You purchase laundry credit score utilizing an exterior cost processor, after which the CSC API to truly add the funds can be referred to as with the quantity you paid:
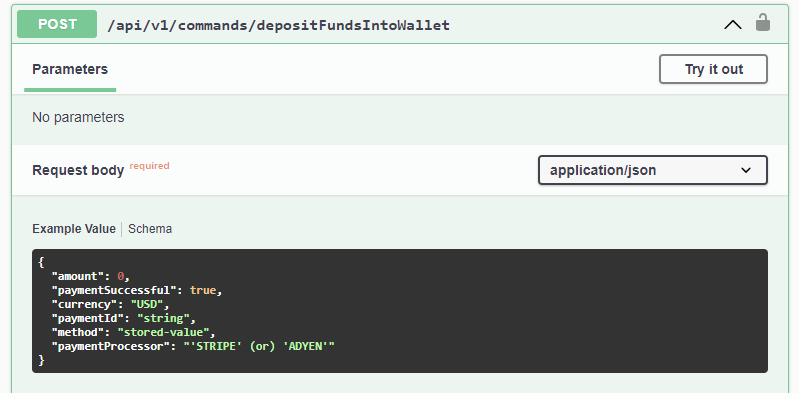
The difficulty was as soon as once more the API blindly accepting a client-provided quantity. The precise buy could possibly be bypassed fully. In the event you wished 1,000,000 {dollars} to your laundry, you’d put that within the quantity area and the API server would fortunately settle for it. It didn’t really test with the cost processor that you just really paid the quantity.
You’ll be free to do laundry for the remainder of your days with out having to fret about cash once more!
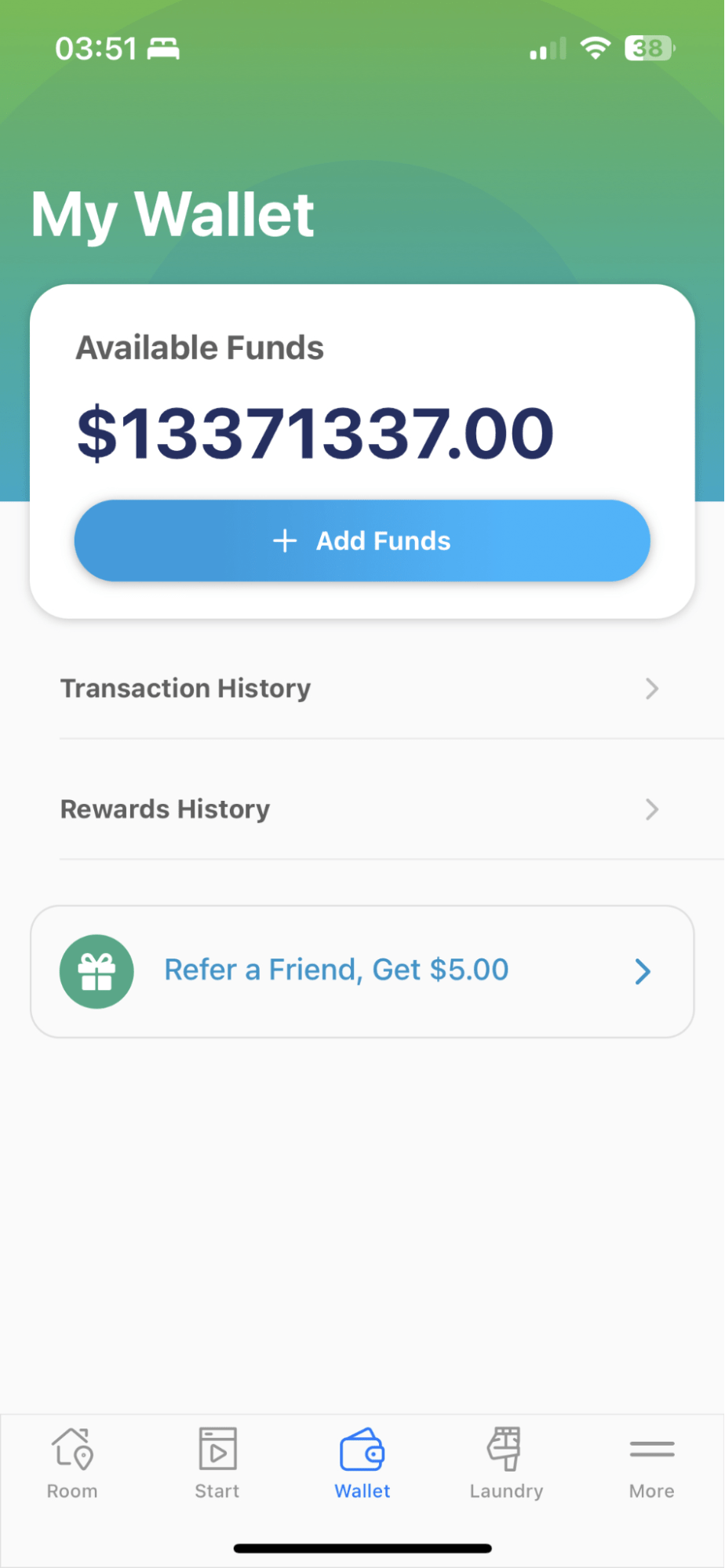
$13 million laundry credit must be sufficient for anyone, but it surely wouldn’t harm to refer a good friend to get just a little extra! Slug Safety/slugsec.ucsc.edu
Earlier hassle with scorching water
Again in 2022 there was one other eerily related incident involving a scorching water equipment: Jacuzzi SmartTubs. There was a crucial API flaw that allowed any logged in consumer to entry all of the admin features and consumer data. Lacking entry controls made this doable. The difficulty was ultimately resolved after a equally lengthy disclosure and serves as one other warning concerning the potential risks of “smart” platforms. You ought to be cautious about what knowledge you set into these platforms and the way deeply you combine them into your community. Many sensible system producers don’t dedicate a number of time to securing their merchandise, and these incidents clearly present that it wants to start out turning into extra of a precedence – particularly when cash is concerned.
Traceable ASPEN
Traceable ASPEN gives vendor impartial and risk pushed analysis in API safety, investigating the newest breaches with world main experience and evaluation. We imagine in securing the world’s APIs with actionable insights from throughout the business. We’re offensively minded, defensively pushed, and targeted in your safety.