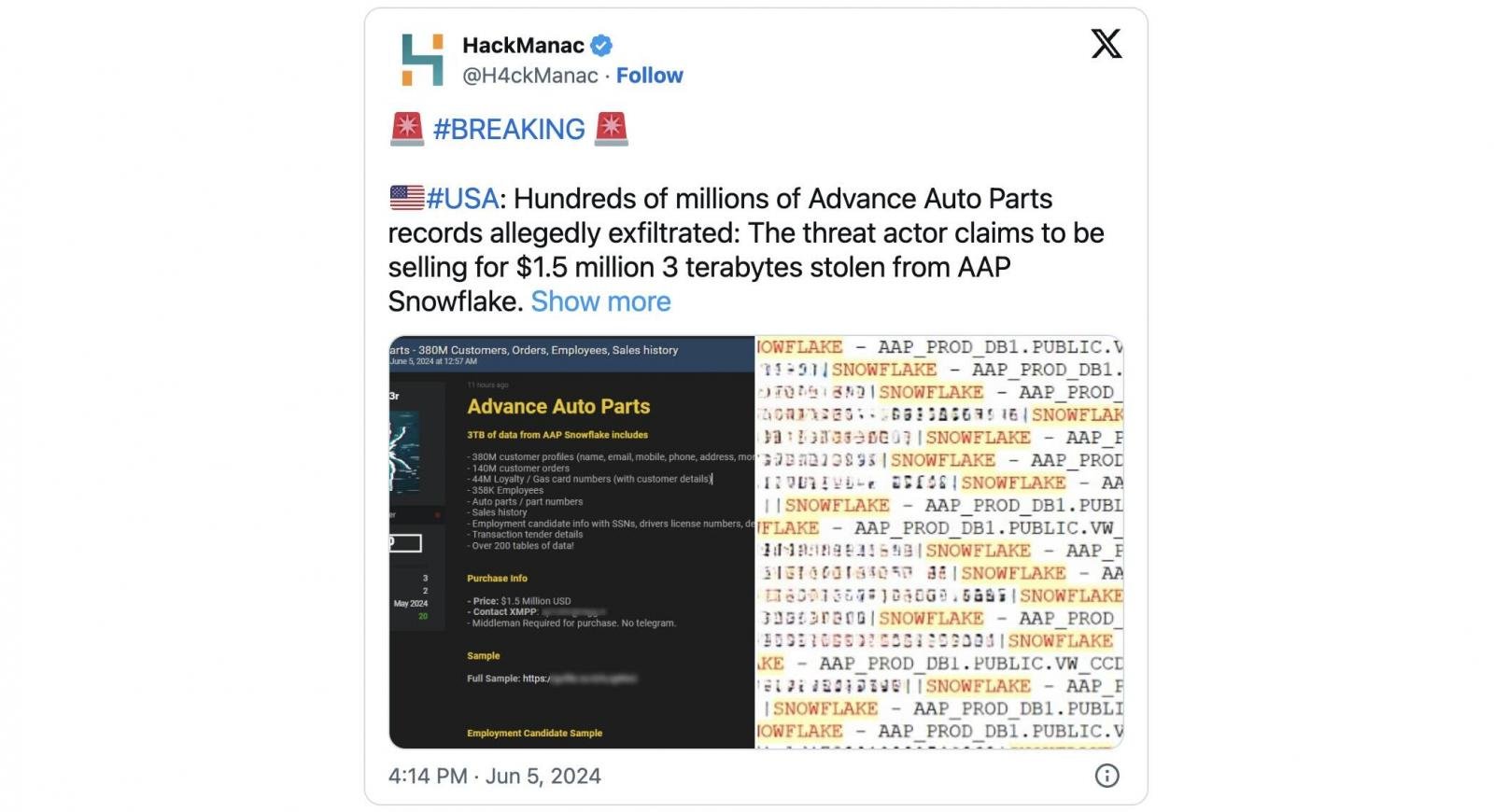
Risk actors declare to be promoting 3TB of knowledge from Advance Auto Elements, a number one automotive aftermarket components supplier, stolen after breaching the corporate’s Snowflake account.
Advance operates 4,777 shops and 320 Worldpac branches and serves 1,152 independently owned Carquest shops in the USA, Canada, Puerto Rico, the U.S. Virgin Islands, Mexico, and numerous Caribbean islands.
Because the menace actor (utilizing the Sp1d3r deal with) revealed as we speak, the huge archive of knowledge stolen from Advance’s Snowflake cloud storage surroundings consists of:
- 380 million buyer profiles (title, electronic mail, cell, telephone, tackle, and extra)
- 140 million buyer orders
- 44 million Loyalty / Gasoline card numbers (with buyer particulars)
- Auto components/half numbers
- Gross sales historical past
- Employment candidate information with SSNs, driver’s license numbers, and demographic particulars
- Transaction tender particulars
Whereas in addition they talked about they’re promoting the stolen info of 358,000 staff, the corporate presently has round 68,000. The distinction might be previous information belonging to former staff and associates.
BleepingComputer has been in a position to verify that a lot of Advance Auto Elements buyer data are respectable.
Advance has but to publicly disclose this breach and notify the U.S. Securities and Change Fee of the incident. BleepingComputer contacted an Advance Auto Elements spokesperson a number of occasions for affirmation and with questions in regards to the breach however didn’t obtain a reply.
Knowledge stolen from Advance’s Snowflake account
The menace actor promoting Advance’s information for $1.5 million on a hacking discussion board advised BleepingComputer that the information had been stolen in latest assaults focusing on cloud storage firm Snowflake prospects since at the very least mid-April 2024.
Snowflake’s cloud companies are utilized by 9,437 prospects, together with high-profile firms worldwide, similar to Adobe, AT&T, Kraft Heinz, Mastercard, Micron, Capital One, Doordash, HP, Nielsen, Novartis, Okta, PepsiCo, Siemens, Instacart, JetBlue, NBC Common, US Meals, Western Union, Yamaha, and plenty of others.
The menace actor additionally advised BleepingComputer that the automotive firm shouldn’t be the one Snowflake buyer whose information was exfiltrated. Some Snowflake prospects have additionally allegedly already paid to get their information again after being contacted by the attackers, in accordance with the menace actor, however BleepingComputer has not been in a position to independently verify if this was true.
As first shared by menace intel firm HackManac, the leaked information comprises quite a few references to ‘SNOWFLAKE,’ corroborating the menace actor’s declare that it was stolen within the latest Snowflake information theft assaults.
Latest Santander and Ticketmaster breaches have been additionally linked to those assaults. On Friday, TicketMaster’s father or mother firm, Stay Nation, confirmed that a knowledge breach hit the ticketing agency after its Snowflake account was compromised on Might 20.
The corporate confirmed in a joint advisory with CrowdStrike and Mandiant that attackers use stolen credentials to focus on prospects with multi-factor authentication disabled.
Snowflake added that whereas one worker’s demo account was compromised on this marketing campaign utilizing stolen credentials, this account did not present the menace actors entry to delicate information and manufacturing or company techniques.
“To date, we do not believe this activity is caused by any vulnerability, misconfiguration, or malicious activity within the Snowflake product,” Snowflake CISO Brad Jones mentioned.
“Throughout the course of our ongoing investigation, we have promptly informed the limited number of customers who we believe may have been impacted.”
Mandiant Consulting CTO Charles Carmakal has advised BleepingComputer that Mandiant has been aiding compromised Snowflake prospects over the previous few weeks. Mandiant’s investigations additionally point out that the attackers are possible utilizing credentials stolen by information-stealing malware to entry the victims’ Snowflake tenants and steal information.